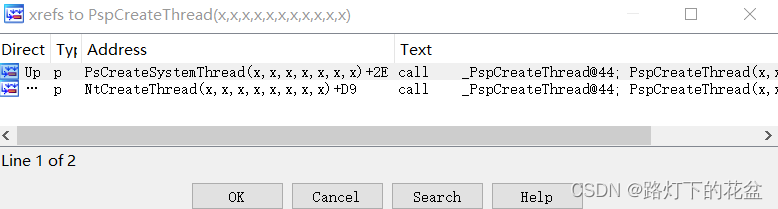
通过之前的分析NtCreateThread函数,可以看到线程的创建实际是在PspCreateThread中。在IDA交叉引用中可以看到仅仅被NtCreateThread 和PsCreateSystemThread 这两个函数调用,分别用于创建用户线程和系统线程对象。
PspCreateThread逆向分析
PAGE:004B710C 68 1C 01 00 00 push 11Ch
PAGE:004B7111 68 C8 19 42 00 push offset stru_4219C8
PAGE:004B7116 E8 20 43 F5 FF call __SEH_prolog
PAGE:004B7116
PAGE:004B711B 64 A1 24 01 00 00 mov eax, large fs:_KPCR.PrcbData.CurrentThread
PAGE:004B7121 89 45 C4 mov [ebp+Currentthread], eax
PAGE:004B7124 33 F6 xor esi, esi
PAGE:004B7126 39 75 2C cmp [ebp+arg_24], esi ; 如果为空则跳转
PAGE:004B7129 0F 84 FD 06 00 00 jz loc_4B782C ; 获取PreviousMode
PAGE:004B7129
PAGE:004B712F C6 45 D0 00 mov [ebp+AccessMode], 0
PAGE:004B712F
PAGE:004B7133
PAGE:004B7133 loc_4B7133: ; CODE XREF: MiFindEmptyAddressRangeDownTree(x,x,x,x,x)+7A↓j
PAGE:004B7133 89 75 E4 mov [ebp+var_1C], esi
PAGE:004B7136 33 DB xor ebx, ebx
PAGE:004B7138 89 5D A4 mov [ebp+var_5C], ebx
PAGE:004B713B 39 75 14 cmp [ebp+Handle], esi ; 判断进程句柄是否为空
PAGE:004B713E 0F 85 A9 DB FD FF jnz loc_494CED ; 如果句柄不为空则跳转
PAGE:004B713E
; 获取句柄进程对象
PAGE:00494CED loc_494CED:
PAGE:00494CED 56 push esi
PAGE:00494CEE 8D 85 6C FF FF FF lea eax, [ebp+Object]
PAGE:00494CF4 50 push eax ; Object
PAGE:00494CF5 FF 75 D0 push dword ptr [ebp+AccessMode] ; AccessMode
PAGE:00494CF8 FF 35 58 A4 48 00 push _PsProcessType ; ObjectType
PAGE:00494CFE 6A 02 push 2 ; DesiredAccess
PAGE:00494D00 FF 75 14 push [ebp+Handle] ; Handle
PAGE:00494D03 E8 E0 8E FF FF call _ObReferenceObjectByHandle@24 ; ObReferenceObjectByHandle(x,x,x,x,x,x)
PAGE:00494D03
PAGE:00494D08 8B 9D 6C FF FF FF mov ebx, [ebp+Object]
PAGE:00494D0E 89 5D A4 mov [ebp+ProcessObject], ebx
PAGE:00494D11 E9 46 24 02 00 jmp loc_4B715C
1.首先判断先前模式,然后判断进程句柄参数是否为空,并且获取对象
PAGE:004B7164 80 7D D0 00 cmp [ebp+AccessMode], 0 ; 判断先前模式
PAGE:004B7168 0F 85 AD 06 00 00 jnz loc_4B781B ; 判断是否是系统进程
PAGE:004B7168
PAGE:004B716E
PAGE:004B716E loc_4B716E: ; CODE XREF: MiFindEmptyAddressRangeDownTree(x,x,x,x,x)+66↓j
PAGE:004B716E 8D 45 B0 lea eax, [ebp+Thread_ETHREAD]
PAGE:004B7171 50 push eax ; int
PAGE:004B7172 56 push esi ; int
PAGE:004B7173 56 push esi ; int
PAGE:004B7174 68 58 02 00 00 push 258h ; int
PAGE:004B7179 56 push esi ; int
PAGE:004B717A FF 75 D0 push dword ptr [ebp+AccessMode] ; BackTraceHash
PAGE:004B717D FF 75 10 push [ebp+arg_8] ; int
PAGE:004B7180 FF 35 5C A4 48 00 push _PsThreadType ; int
PAGE:004B7186 FF 75 D0 push dword ptr [ebp+AccessMode] ; PreviousMode
PAGE:004B7189 E8 D8 73 FD FF call _ObCreateObject@36 ; 创建线程类型对象
PAGE:004B7189
PAGE:004B718E 3B C6 cmp eax, esi ; 判断是否执行成功
PAGE:004B7190 0F 8C C5 C0 06 00 jl loc_52325B
PAGE:004B7190
PAGE:004B7196 B9 96 00 00 00 mov ecx, 96h
PAGE:004B719B 33 C0 xor eax, eax
PAGE:004B719D 8B 75 B0 mov esi, [ebp+Thread_ETHREAD]
PAGE:004B71A0 8B FE mov edi, esi
PAGE:004B71A2 F3 AB rep stosd ; 清空整个Eprocess
2.判断先前模式是否是内核模式和系统线程,创建线程对象,并进行清空。
PAGE:004B7196 B9 96 00 00 00 mov ecx, 96h
PAGE:004B719B 33 C0 xor eax, eax
PAGE:004B719D 8B 75 B0 mov esi, [ebp+Thread_ETHREAD]
PAGE:004B71A0 8B FE mov edi, esi
PAGE:004B71A2 F3 AB rep stosd ; 初始化整个Eprocess
PAGE:004B71A4 21 86 34 02 00 00 and [esi+_ETHREAD.RundownProtect.___u0.Count], eax
PAGE:004B71AA 89 9E 20 02 00 00 mov [esi+_ETHREAD.ThreadsProcess], ebx
PAGE:004B71B0 8D BE EC 01 00 00 lea edi, [esi+_ETHREAD.Cid]
PAGE:004B71B6 8B 83 84 00 00 00 mov eax, [ebx+_EPROCESS.UniqueProcessId]
PAGE:004B71BC 89 07 mov [edi+_CLIENT_ID.UniqueProcess], eax
PAGE:004B71BE 89 75 B4 mov [ebp+ETHREAD0], esi
PAGE:004B71C1 83 65 B8 00 and [ebp+var_48], 0
PAGE:004B71C5 8D 45 B4 lea eax, [ebp+ETHREAD0]
PAGE:004B71C8 50 push eax
PAGE:004B71C9 FF 35 60 A4 48 00 push _PspCidTable
PAGE:004B71CF E8 78 99 FD FF call _ExCreateHandle@8 ; 创建线程句柄
PAGE:004B71CF
PAGE:004B71D4 89 86 F0 01 00 00 mov [esi+1F0h], eax
PAGE:004B71DA 85 C0 test eax, eax
PAGE:004B71DC 0F 84 89 C0 06 00 jz loc_52326B
3.初始化一些结构,并创建句柄
PAGE:004B71E2 A1 BC A4 47 00 mov eax, _MmReadClusterSize
PAGE:004B71E7 89 86 40 02 00 00 mov [esi+_ETHREAD.ReadClusterSize], eax
PAGE:004B71ED 6A 01 push 1 ; Limit
PAGE:004B71EF 6A 00 push 0 ; Count
PAGE:004B71F1 8D 86 F4 01 00 00 lea eax, [esi+_ETHREAD.___u9]
PAGE:004B71F7 50 push eax ; Semaphore
PAGE:004B71F8 E8 2D C1 F5 FF call _KeInitializeSemaphore@12 ; 初始化信号量
PAGE:004B71F8
PAGE:004B71FD 8D 86 C8 01 00 00 lea eax, [esi+_ETHREAD.___u2]
PAGE:004B7203 89 40 04 mov [eax+4], eax
PAGE:004B7206 89 00 mov [eax], eax
PAGE:004B7208 8D 86 10 02 00 00 lea eax, [esi+_ETHREAD.IrpList]
PAGE:004B720E 89 40 04 mov [eax+_LIST_ENTRY.Blink], eax
PAGE:004B7211 89 00 mov [eax], eax
PAGE:004B7213 8D 86 D4 01 00 00 lea eax, [esi+_ETHREAD.PostBlockList]
PAGE:004B7219 89 40 04 mov [eax+4], eax
PAGE:004B721C 89 00 mov [eax], eax
PAGE:004B721E 83 A6 38 02 00 00 00 and [esi+_ETHREAD.ThreadLock.___u0.__s0._bf_0], 0
PAGE:004B7225 8D 86 E0 01 00 00 lea eax, [esi+_ETHREAD.ActiveTimerListLock]
PAGE:004B722B 50 push eax ; SpinLock
PAGE:004B722C E8 93 C3 F4 FF call _KeInitializeSpinLock@4 ; 初始化自旋锁
PAGE:004B722C
PAGE:004B7231 8D 86 E4 01 00 00 lea eax, [esi+_ETHREAD.ActiveTimerListHead]
PAGE:004B7237 89 40 04 mov [eax+4], eax
PAGE:004B723A 89 00 mov [eax], eax
PAGE:004B723C 8D 8B 80 00 00 00 lea ecx, [ebx+_EPROCESS.RundownProtect] ; RunRef
PAGE:004B7242 89 8D 68 FF FF FF mov [ebp+var_98], ecx
PAGE:004B7248 E8 94 D6 FD FF call @ExAcquireRundownProtection@4 ;
4.继续初始化新线程对象ETHREAD 结构中的一些域
PAGE:004B7255 83 7D 20 00 cmp [ebp+context], 0 ; 判断环境是否为空
PAGE:004B7259 0F 85 DB 05 00 00 jnz loc_4B783A ; 创建TEB,并初始化
PAGE:004B7259
PAGE:004B725F 33 C9 xor ecx, ecx ; 如果不为空,则为系统线程
PAGE:004B7261 89 4D E4 mov [ebp+var_1C], ecx
PAGE:004B7264 6A 10 push 10h
PAGE:004B7266 58 pop eax
PAGE:004B7267 8D 96 48 02 00 00 lea edx, [esi+_ETHREAD.___u24]
PAGE:004B726D F0 09 02 lock or [edx], eax
PAGE:004B7270 8B 45 2C mov eax, [ebp+arg_24]
PAGE:004B7273 89 86 24 02 00 00 mov [esi+_ETHREAD.StartAddress], eax
PAGE:004B7279 53 push ebx
PAGE:004B727A 51 push ecx
PAGE:004B727B 51 push ecx
PAGE:004B727C FF 75 30 push [ebp+arg_28]
PAGE:004B727F 50 push eax
PAGE:004B7280 68 CB 3E 4A 00 push offset _PspSystemThreadStartup@8 ; 创建系统线程
PAGE:004B7285 51 push ecx
PAGE:004B7285
PAGE:004B7286
PAGE:004B7286 loc_4B7286: ; CODE XREF: MiFindEmptyAddressRangeDownTree(x,x,x,x,x)+D8↓j
PAGE:004B7286 56 push esi
PAGE:004B7287 E8 4D 02 00 00 call _KeInitThread@32 ; 初始化线程
PAGE:004B7287
PAGE:004B728C 8B F8 mov edi, eax ; 判断是否执行成功
PAGE:004B728E 85 FF test edi, edi
PAGE:004B7290 0F 8C 27 C0 06 00 jl loc_5232BD
PAGE:004B783A loc_4B783A: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+14D↑j
PAGE:004B783A 8D 45 E4 lea eax, [ebp+var_1C]
PAGE:004B783D 50 push eax ; int
PAGE:004B783E 57 push edi ; int
PAGE:004B783F FF 75 24 push [ebp+arg_1C] ; int
PAGE:004B7842 53 push ebx ; Process
PAGE:004B7843 E8 50 03 00 00 call _MmCreateTeb@16 ; 创建TEB
PAGE:004B7843
PAGE:004B7848 8B F8 mov edi, eax
PAGE:004B784A 85 FF test edi, edi
PAGE:004B784C 0F 8C 2D BA 06 00 jl loc_52327F
PAGE:004B784C
PAGE:004B7852 83 65 FC 00 and [ebp+var_4], 0
PAGE:004B7856 8B 45 20 mov eax, [ebp+arg_18]
PAGE:004B7859 8B 88 B8 00 00 00 mov ecx, [eax+0B8h]
PAGE:004B785F 89 8E 24 02 00 00 mov [esi+224h], ecx
PAGE:004B7865 8B 80 B0 00 00 00 mov eax, [eax+0B0h]
PAGE:004B786B 89 86 28 02 00 00 mov [esi+228h], eax
PAGE:004B7871 83 4D FC FF or [ebp+var_4], 0FFFFFFFFh
PAGE:004B7871
PAGE:004B7875
PAGE:004B7875 loc_4B7875: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C1AC↓j
PAGE:004B7875 85 FF test edi, edi
PAGE:004B7877 0F 8C 40 BA 06 00 jl loc_5232BD
PAGE:004B7877
PAGE:004B787D 53 push ebx
PAGE:004B787E FF 75 E4 push [ebp+var_1C]
PAGE:004B7881 FF 75 20 push [ebp+arg_18]
PAGE:004B7884 FF B6 24 02 00 00 push dword ptr [esi+224h]
PAGE:004B788A 6A 00 push 0
PAGE:004B788C 68 53 79 4B 00 push offset _PspUserThreadStartup@8 ; PspUserThreadStartup(x,x)
PAGE:004B7891 6A 00 push 0
PAGE:004B7893 E9 EE F9 FF FF jmp loc_4B7286
5.判断是否是系统线程,如果不是则创建PEB并初始化,如果是则初始化一些域,无论是执行哪种流程最后通过KeInitThread初始化线程
PAGE:004B7296 8B 7D C4 mov edi, [ebp+Currentthread]
PAGE:004B7299 FF 8F D4 00 00 00 dec [edi+_ETHREAD.Tcb.KernelApcDisable]
PAGE:004B729F 8D 43 6C lea eax, [ebx+_EPROCESS.ProcessLock]
PAGE:004B72A2 89 45 8C mov [ebp+ProcessLock], eax
PAGE:004B72A5 B8 00 00 00 00 mov eax, 0
PAGE:004B72AA 8B 4D 8C mov ecx, [ebp+ProcessLock]
PAGE:004B72AD BA 02 00 00 00 mov edx, 2
PAGE:004B72B2 0F B1 11 cmpxchg [ecx], edx
PAGE:004B72B5 85 C0 test eax, eax
PAGE:004B72B7 0F 85 15 C0 06 00 jnz loc_5232D2
PAGE:004B72B7
PAGE:004B72BD
PAGE:004B72BD loc_4B72BD: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C1CE↓j
PAGE:004B72BD F6 83 48 02 00 00 08 test byte ptr [ebx+_EPROCESS.___u70.Flags], 8
PAGE:004B72C4 0F 85 15 C0 06 00 jnz loc_5232DF
PAGE:004B72C4
PAGE:004B72CA 8D 83 A0 01 00 00 lea eax, [ebx+_EPROCESS.ActiveThreads]
PAGE:004B72D0 8B 38 mov edi, [eax]
PAGE:004B72D2 8D 4F 01 lea ecx, [edi+1]
PAGE:004B72D5 89 08 mov [eax], ecx
PAGE:004B72D7 8D 86 2C 02 00 00 lea eax, [esi+_ETHREAD.ThreadListEntry]
PAGE:004B72DD 8D 8B 90 01 00 00 lea ecx, [ebx+_EPROCESS.ThreadListHead]
PAGE:004B72E3 8B 51 04 mov edx, [ecx+_LIST_ENTRY.Blink]
PAGE:004B72E6 89 08 mov [eax], ecx
PAGE:004B72E8 89 50 04 mov [eax+_LIST_ENTRY.Blink], edx
PAGE:004B72EB 89 02 mov [edx], eax
PAGE:004B72ED 89 41 04 mov [ecx+_LIST_ENTRY.Blink], eax
PAGE:004B72F0 56 push esi
PAGE:004B72F1 E8 0C A6 F6 FF call _KeStartThread@4
6.锁住线程,然后将新线程加入到进程的线程链表中,调用KeStartThread初始化一些域
PAGE:004B731B loc_4B731B: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C24D↓j
PAGE:004B731B 8B 45 C4 mov eax, [ebp+Currentthread]
PAGE:004B731E FF 80 D4 00 00 00 inc [eax+_ETHREAD.Tcb.KernelApcDisable]
PAGE:004B7324 75 0B jnz short loc_4B7331
PAGE:004B7324
PAGE:004B7326 83 C0 34 add eax, 34h ; '4'
PAGE:004B7329 39 00 cmp [eax], eax
PAGE:004B732B 0F 85 2D C0 06 00 jnz loc_52335E
PAGE:004B732B
PAGE:004B7331
PAGE:004B7331 loc_4B7331: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+218↑j
PAGE:004B7331 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C261↓j
PAGE:004B7331 8D 8B 80 00 00 00 lea ecx, [ebx+_EPROCESS.RundownProtect] ; RunRef
PAGE:004B7337 E8 E5 D5 FD FF call @ExReleaseRundownProtection@4 ; ExReleaseRundownProtection(x)
PAGE:004B7337
PAGE:004B733C 85 FF test edi, edi
PAGE:004B733E 0F 84 26 1C FF FF jz loc_4A8F6A
PAGE:004B733E
PAGE:004B7344
PAGE:004B7344 loc_4B7344: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)-E193↑j
PAGE:004B7344 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C2A8↓j
PAGE:004B7344 8B BB 34 01 00 00 mov edi, [ebx+_EPROCESS.Job]
PAGE:004B734A 85 FF test edi, edi ; 判断进程是否处于JOB中
PAGE:004B734C 0F 85 03 FF 00 00 jnz loc_4C7255
PAGE:004B734C
PAGE:004B7352
PAGE:004B7352 loc_4B7352: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+10150↓j
PAGE:004B7352 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+1015F↓j
PAGE:004B7352 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C306↓j
PAGE:004B7352 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C311↓j
PAGE:004B7352 ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C323↓j
PAGE:004B7352 6A 01 push 1
PAGE:004B7354 FF 75 24 push [ebp+arg_1C]
PAGE:004B7357 56 push esi
PAGE:004B7358 E8 4B D6 FD FF call _WmiTraceThread@12 ; WmiTraceThread(x,x,x)
PAGE:004B7358
PAGE:004B735D 33 FF xor edi, edi
PAGE:004B735F 39 3D C0 A4 48 00 cmp _PspCreateThreadNotifyRoutineCount, edi
PAGE:004B7365 0F 85 C9 C0 06 00 jnz loc_523434
PAGE:004B7365
PAGE:004B736B
PAGE:004B736B loc_4B736B: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C373↓j
PAGE:004B736B 6A 02 push 2
PAGE:004B736D 5A pop edx
PAGE:004B736E 8B CE mov ecx, esi
PAGE:004B7370 E8 3D 52 F5 FF call @ObReferenceObjectEx@8 ; 线程对象的引用计数加2
PAGE:004B7370
PAGE:004B7375 39 7D 20 cmp [ebp+context], edi
PAGE:004B7378 0F 85 A7 03 00 00 jnz loc_4B7725
7.判断进程是否处在一个job中,如果是需要进行一些处理;通过ObReferenceObjectEx使线程对象的引用计数加2
PAGE:004B7393 loc_4B7393: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+66D↓j
PAGE:004B7393 8B 0D 5C A4 48 00 mov ecx, _PsThreadType
PAGE:004B7399 83 C1 68 add ecx, 68h ; 'h'
PAGE:004B739C 51 push ecx ; GenericMapping
PAGE:004B739D FF 75 0C push [ebp+DesiredAccess] ; AccessMask
PAGE:004B73A0 8D 8D 48 FF FF FF lea ecx, [ebp+var_B8]
PAGE:004B73A6 51 push ecx ; int
PAGE:004B73A7 8D 8D D4 FE FF FF lea ecx, [ebp+PassedAccessState]
PAGE:004B73AD 51 push ecx ; int
PAGE:004B73AE 50 push eax ; Process
PAGE:004B73AF 57 push edi ; Thread
PAGE:004B73B0 E8 82 5D FD FF call _SeCreateAccessStateEx@24 ; 创建ACCESS_STATE结构
PAGE:004B73B0
8.调用SeCreateAccessStateEx 函数创建一个访问状态结构
(ACCESS_STATE)
PAGE:004B73BA
PAGE:004B73C0 8D 45 E0 lea eax, [ebp+var_handle]
PAGE:004B73C3 50 push eax ; Handle
PAGE:004B73C4 57 push edi ; NewObject
PAGE:004B73C5 57 push edi ; ObjectPointerBias
PAGE:004B73C6 FF 75 0C push [ebp+DesiredAccess] ; DesiredAccess
PAGE:004B73C9 8D 85 D4 FE FF FF lea eax, [ebp+PassedAccessState]
PAGE:004B73CF 50 push eax ; PassedAccessState
PAGE:004B73D0 56 push esi ; Object
PAGE:004B73D1 E8 64 6C FD FF call _ObInsertObject@24 ; 将线程插入句柄表中
PAGE:004B73D1
PAGE:004B73D6 89 45 C8 mov [ebp+var_Ret], eax
PAGE:004B73D9 8D 85 D4 FE FF FF lea eax, [ebp+PassedAccessState]
PAGE:004B73DF 50 push eax
PAGE:004B73E0 E8 39 5E FD FF call _SeDeleteAccessState@4 ; 释放内存
PAGE:004B73E0
PAGE:004B73E5 39 7D C8 cmp [ebp+var_Ret], edi
PAGE:004B73E8 0F 8C 22 C1 06 00 jl loc_523510
9.调用ObInsertObject将线程插入句柄表中
PAGE:004B740C loc_4B740C: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C414↓j
PAGE:004B740C ; PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C420↓j
PAGE:004B740C 8D 45 BC lea eax, [ebp+CurrentTime]
PAGE:004B740F 50 push eax ; CurrentTime
PAGE:004B7410 E8 87 57 F5 FF call _KeQuerySystemTime@4 ; 设置创建时间
PAGE:004B7410
PAGE:004B7415 8B 45 BC mov eax, dword ptr [ebp+CurrentTime]
PAGE:004B7418 8B 4D C0 mov ecx, dword ptr [ebp+CurrentTime+4]
PAGE:004B741B 0F A4 C1 03 shld ecx, eax, 3
PAGE:004B741F C1 E0 03 shl eax, 3
PAGE:004B7422 89 86 C0 01 00 00 mov dword ptr [esi+_ETHREAD.___u1.CreateTime], eax
PAGE:004B7428 89 8E C4 01 00 00 mov [esi+_ETHREAD.___u1.CreateTime.__s0.HighPart], ecx
PAGE:004B742E 8D BE 48 02 00 00 lea edi, [esi+_ETHREAD.___u24]
PAGE:004B7434 F6 07 02 test byte ptr [edi], 2
PAGE:004B7437 0F 85 2B C1 06 00 jnz loc_523568
10.设置创建时间
PAGE:004B743D 8D 45 D8 lea eax, [ebp+MemoryAllocated]
PAGE:004B7440 50 push eax ; MemoryAllocated
PAGE:004B7441 8D 45 DC lea eax, [ebp+SecurityDescriptor]
PAGE:004B7444 50 push eax ; SecurityDescriptor
PAGE:004B7445 56 push esi ; Object
PAGE:004B7446 E8 E3 77 FD FF call _ObGetObjectSecurity@12 ; 获取线程的安全描述符
PAGE:004B7446
PAGE:004B744B 89 45 C8 mov [ebp+var_Ret], eax
PAGE:004B744E 85 C0 test eax, eax
PAGE:004B7450 0F 8C DB C0 06 00 jl loc_523531
PAGE:004B7450
PAGE:004B7456 89 5D 9C mov [ebp+SubjectSecurityContext.ProcessAuditId], ebx
PAGE:004B7459 53 push ebx ; Process
PAGE:004B745A E8 5C 5C FD FF call _PsReferencePrimaryToken@4 ; PsReferencePrimaryToken(x)
PAGE:004B745A
PAGE:004B745F 89 45 98 mov [ebp+SubjectSecurityContext.PrimaryToken], eax
PAGE:004B7462 83 65 90 00 and [ebp+SubjectSecurityContext.ClientToken], 0
PAGE:004B7466 8D BE 44 02 00 00 lea edi, [esi+_ETHREAD.GrantedAccess] ; 线程的访问权限
PAGE:004B746C 8D 45 D4 lea eax, [ebp+AccessStatus]
PAGE:004B746F 50 push eax ; AccessStatus
PAGE:004B7470 57 push edi ; GrantedAccess
PAGE:004B7471 FF 75 D0 push dword ptr [ebp+AccessMode] ; AccessMode
PAGE:004B7474 A1 5C A4 48 00 mov eax, _PsThreadType
PAGE:004B7479 83 C0 68 add eax, 68h ; 'h'
PAGE:004B747C 50 push eax ; GenericMapping
PAGE:004B747D 33 C0 xor eax, eax
PAGE:004B747F 50 push eax ; Privileges
PAGE:004B7480 50 push eax ; PreviouslyGrantedAccess
PAGE:004B7481 68 00 00 00 02 push 2000000h ; DesiredAccess
PAGE:004B7486 50 push eax ; SubjectContextLocked
PAGE:004B7487 8D 45 90 lea eax, [ebp+SubjectSecurityContext]
PAGE:004B748A 50 push eax ; SubjectSecurityContext
PAGE:004B748B FF 75 DC push [ebp+SecurityDescriptor] ; SecurityDescriptor
PAGE:004B748E E8 B5 64 FD FF call _SeAccessCheck@40 ; 设置线程的访问权限
11.通过SeAccessCheck设置线程的访问权限
PAGE:004B74BC loc_4B74BC: ; CODE XREF: PspCreateThread(x,x,x,x,x,x,x,x,x,x,x)+6C466↓j
PAGE:004B74BC 56 push esi
PAGE:004B74BD E8 D0 A4 F6 FF call _KeReadyThread@4 ; 使线程进入就绪态
PAGE:004B74BD
PAGE:004B74C2 8B CE mov ecx, esi ; Object
PAGE:004B74C4 E8 87 AB F4 FF call @ObfDereferenceObject@4 ; 给线程的引用计数减1
12.最后通过KeReadyThread使线程进入就绪态,通过ObfDereferenceObject使线程的引用计数减1。
至此PspCreateThread分析完成






















 524
524











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








