Communications model
- Source
- Generates data to be transmitted
- Transmitter
- Converts data into transmittable signals
- Transmission System
- Carries data
- Receiver
- Converts receive…d signal into data
- Destination
- Takes incoming data
Networking
-
Networking deals with the technology and architectures of the communication networks used to interconnect communication devices
-
Why in practice we do not use point to point communication?
为什么使用点对点的通信并不实用
- Devices too far apart
- large set of devices need impractical number of connections
Classification of communications networks
-
Local Area Network (LAN)
- Connects computers equipment and other terminals in a limited area, e.g. classroom, building, office
- Privately owned
-
Metropolitan Area Network (MAN)
-
connect number of LANs spread around. e.g. a cable television network
用于连接分布在整个城市中的多个 LAN
-
-
Wide Area Networks (WAN)
- Transmission of data over large geographical areas. e.g. a city, a state, a country, even globe.
- Circuit switching and packet switching
-
Personal Area Network (PAN)
- Provides transmission of data over short range.
- Requires low power for transmission
- 无线连接:蓝牙,红外,NFC
- 有线连接:USB电缆
Transmission Mode
-
Simplex
单工
- only one direction
-
Half-duplex
- each station can both transmit and receive, but one at a time
-
Full-duplex
- Both stations can transmit and receive simultaneously
Line Configuration
线路配置
-
The way two or more communication devices attach to a link.
两个或多个通信设备连接到一条链路的方式
- A link is a physical communication pathway that transfers data from one device to another.
- connections 线路配置也被称为连接
-
Point-to-Point line configuration
- dedicated link between two devices, use entire capacity of the channel.
-
Point-to-Multipoint line configuration
-
more than two specific devices share a single link. The capacity of the link is shared.
两个以上特定设备共享一条链路的配置
-
Topology
- Peer to peer / Primary - secondary(equal sharing)
- Mesh topology
- Every devices has a dedicated point to point link to every other device
- Eliminate traffic problem
- Robust and guarantees privacy
- Easy fault identification
- Star topology
- Each device has a dedicated point-to-point link only to a central controller called hub.
- Only one I/O port to connect hub
- If one link is disconnected, does not effect others.
- If the hub fails, all the connections are affected.
- Tree topology
- A variation of star as not all devices connect to central hub, but most devices connect to a secondary hub, which in turn connects to central hub.
- Central hub is mostly an active hub i.e. it repeats the signals.
- e.g. cable TV
- Bus topology
- Nodes are connected to a bus cable by drop lines and taps
- Has multipoint line configuration
- A fault in the cable will stop all transmission
- Ring topology
- Each device has a dedicated point-to-point line only with two devices on either side of it
- Signal is passed in one direction along the ring
- Ring length limits the maximum no. of devices
- Any break in ring will disable the entire network
- Hybrid topology
- A network may combine several topologies as subnetworks linked together in a larger topology.
Alternative Technologies
- Circuit switching 电路交换
- The communications between end devices (nodes) must be set up before they can communicate.
- Dedicated communication paths established between sender and receiver for the duration of the conversation.
- e.g. telephone network
- Packet switching 报文交换
- Data sent out of sequence
- Small chunks of data at a time
- Packets passed from node to node between source and destination
- Used for terminal to computer and computer to computer communications
- More efficient
Bit
- Smallest unit of data in a computer
Bandwidth
- Range between the lowest and highest frequencies used for a particular application.
- more data at one time for bigger bandwidth
Network Performance
- Data may be
- delayed
- lost
- mis-ordered
- duplicated
- Application’s Quality of Service requires:
- High data rate
- Delay 可能的原因:
- processing
- Packetisation分组
- Queuing队列
- Transmission传输
- Propagation传播
- IoT or wireless sensor networks
- Energy consumption能耗
- Network lifetime网络生命周期
Standardized Protocol Architectures
- Protocol
- Rules that both the sender and receiver and all intermediate devices need to follow for effective communication.
Open Systems Interconnection (OSI)(开放系统互连架构)
- Seven layers
- An Open System is a model that allows any two different systems to communicate regardless of their underlying architecture.
- Is a model, not a protocol.
- Each layer uses the services provided by its lower layer and provides service to its upper layer.
- it is a framework for developing protocol standards.
OSI layers
-
Layer Function Example Application Services that are used with end user applications SMTP Presentation 1. Formats the data so that it can be viewed by the user 2. Encrypt and decrypt JPG, GIF, HTTPS, SSL, TLS Session Establishes/ends connections between two hosts NetBIOS, PPTP Transport Responsible for the transport protocol and error handling TCP, UDP Network Reads the IP address form the packet Routers, Layer 3 Switches Data link Reads the MAC address from the data packet Swirched Physical Send data on to the physical wire Hubs, NICS, Cabl -
Application
- Enable users to access the network
- Means for applications to access OSI environment
- Everything at this layer is application-specific
- e.g. chrome
-
Presentation
- Data formats and coding
- Responsible for interoperability between these different encoding methods.
- Responsible for data Encryption/Decryption
- Data compression
-
Session
- Establishes, manages and terminates connections between applications
- Responsible for dialog control and synchronization.
- Recovery
-
Transport
- Provides end-to-end data delivery
- Error free transmission
- No losses
- Delivers data in sequence
- Include TCP and UDP
-
Network
- Responsible for the source-to-destination delivery of a packet
- Assigns sender’s and receiver’s IP address to each data segments to form a packet
- Routes the packets and determines the path of data according to unique device addresses
-
Data link
-
Means of activating, maintaining and deactivating the communication links
-
Frames data packets and prepares for transmission
将数据报封装成帧
-
Detects and corrects transmission errors
-
Provides hop-to-hop delivery in a closed network
hop到hop的传输
-
-
Physical
- Physical interface between devices.
- Signal -> physical media
- Binary sequence into electrical or electromagnetic signal and sends them over transmission medium
TCP/IP Protocol Architecture
- A suite of communication protocols used to interconnect network devices on the internet.
- 5 layers
TCP/IP Protocol Layers
-
Application layer
- 三合一
- Responsible for providing the channel for interaction between applications and end users.
- Generates the message and requests connections.
- HTTP / FTP / SSH(Secure Shell (SSH)) / DNS(Domain Name System (DNS))
-
Transport layer
- Responsible for maintaining end-to-end communications across the network
- Transport layer also arranges the packets to be sent, in sequence.
- Reliable delivery of data
- TCP & UDP
-
Internet layer
- Responsible for creating the packets that move across the network.
- Accepts and delivers packets with the
IPaddresses to identify the packet’s source and destination. - Routing functions across multiple networks
-
Network interface layer(datalink)
- Exchange of data between end system and network
- Adds the MAC address information and creates a frame.
- Provides services like priority.
-
Physical layer(Sometimes, Physical Layer is included in the Network Interface Layer)
TCP/IP layering
- Each layer only communicate with adjacent layers.
- 只和相邻的层通信,不用知道不相邻的层
- Each layer needs to add some control information to the data in order to do its job.
- Peer layer uses the control information
Transport Control Protocol (TCP)
- Connection Oriented Communication
- establish a connection before data exchanged
- requirement for an sending data
- Reliable Connection
- use ACK to ensure the data are right
- retransmit
- Segmentation and In-Sequence
- Error and Flow Control
- Weakness: Slower speed and higher overhead
User Datagram Protocol
- Connectionless
- Not guaranteed delivery
- No sequence
- No against duplication
- Faster
- Less overhead
- Better for online streaming / video games
Addressing in TCP/IP(协议栈用到的地址)
- Physical address
- used in data link layer
- link-layer address / MAC address
- MAC: 6 bytes
- used in data link layer
- Logical address
- Network layer
- IP
- IPv4 4 bytes
- Port address
- Transport layer differentiate between several programs running at the same time.
- Application-specific address
- user-friendly addresses
- email address / URL
Header and Encapsulation
PDU and Headers
- Protocol data unit (PDU) is a single unit of information transmitted among the peer layers of a network.
- Header and body
- Physical layer has no header
- Header contains protocol-specific control information.
- 上层的信息是本层的data,每层向data上加自己的header
- This process of preserving the data while attaching a new header is known as encapsulation.
IoT Introduction
- IoT refers to a system of connected objects that can
- collect and transfer data over a wireless network
- without human intervention.
- 潜在的物联网推动因素包括:RFID/Nanotechnology/Sensors/Smart Networks/Augmented Intelligence
Component
- Sensors
- measure a physical phenomenon
- Data centric creation of information without human intervention
- A sensor converts a non-electrical input into an electrical signal that can be sent to an electronic circuit.
- Actuator
/ˈæktʃueɪtər/ n. 执行机构;激励者- a device that converts an electrical signal into action
- An actuator requires a control signal and a source of energy
Factors driving the deployment of sensor tech
- Price
- Capability
- Size
Sensor Tech Challenges
- Power consumption
- Battery life, charging, and replacement, especially in remote areas, may represent significant issues
- Security of sensors
- Requires lightweight security algorithm. Data Integrity is a concern
- Interoperability
/ˌɪntərˌɒpərəˈbɪləti/n. [计] 互操作性;互用性- Most of the sensor systems currently in operation are designed for specific applications.
Networks in IoT
- Connect to networks using hubs/ gateways/ routers /network bridges /switches
Devices
- hubs
- Used to connect segments of a LAN.
- gateways
- A network point that acts as an entrance to another network.
- routers
- A device that forwards data packets along networks.
- network bridges
- A network device that connects multiple network segments
- switches
- A computer networking device that connects devices together by using packet switching to receive, process, and forward data to the destination device.
Internet Protocol
- IP was used to address computers before it began to be used to address other devices.
Network classified
-
wired
- USB ethernet fiber optics
-
wireless
- PAN LAN Wi-Fi WiMAX WAN
-
Data transfer rates and energy requirements are two key considerations
Bluetooth
- In PAN
- robustness, low power, low cost
- current bottleneck: interoperability
Characteristics of BLE(Bluetooth Low Energy)
- Short broadcast, small messages, battery life, simple, cheaper, same frequency
Wi-Fi
- high-speed data transfer rates
WiMax(Worldwide Interoperability for Microwave Access)
- 1 Gbps
- better compatibility
- Worldwide Interoperability for Microwave Access
LTE
- long term evolution
- 3G standard->LTE-A 4G standard
Weightless窄带物联网协议
- low power, wide area networks (LPWAN)
- 16 Mbps, 10 years
- 低速,低功耗,全双工,可
靠,安全的物联网解决方案
IoT Communication Setup
- Device to Device (D2D) setup
- Device to Server (D2S) setup
- Server to Server (S2S) setup
IoT Networks Challenges
-
Data Explosion
-
there are a large number of components and a massive amount of data transmission between users, IoT devices generate tremendous amount of data.
-
very costly to store data
-
proper information extraction mechanisms
必须使用适当的信息提取机制
-
-
Security
-
Easier to scoop up data transmitted from the IoT sensors and steal sensitive information
-
IoT devices are usually small and inexpensive with no or little physical security
-
Need effective Authentication and Access Control
需要有效的身份验证和访问控制
-
具体措施:
- strong data encryption
- strong authorization
- minimizing access points and gateways
-
-
Power Consumption
- Devices connected to a network consume power, and providing a continuous power source is a pressing concern for the IoT.
- power-aware routing and sleep-scheduling protocols
- Power-aware routing protocols 功耗感知路由determine the routing decision based on the most energy-efficient route for transmitting data packets.
- Sleep-scheduling protocols 睡眠调度协议define how devices can “sleep” and remain inactive for better energy efficiency without impacting the output.
Data Link Layer
Logical Link Control Sublayer (LLC)
-
Provides the link between the higher layers and the MAC sublayer.
-
service
- Unacknowledged connectionless service无确认无连接
- Connection oriented service有确认有连接
- Acknowledged connectionless service有确认无连接
连接的服务:通信前需要先建立连接 有连接一定有确认!!!
-
Responsible for flow control, sequencing, error control etc.
Media Access Control (MAC) Sublayer
- Access control to shared medium
- Reliable data transmission
Types of MAC protocol
- Reservation based protocols基于预先获得系统信息的协议
- Schedule for each end node
- Collision free
- Requires knowledge of network topology
- e.g. TDMA, Token Ring
- Contention based protocols
- No requirement for synchronization and topology knowledge
- Nodes compete for resources
- ALOHA and CSMA
MAC protocol
Reservation based protocols
Token Ring Concept
-
Access is controlled by gaining possession of a token, a special short frame.
-
Token circulates around a ring in sequence
-
Each node transmits its information in burst of maximum number of frames
-
Advantage: Doesn’t cause collision
-
Disadvantage: Failure of one node can crash the entire channel单点故障
Time Division Multiple Access (TDMA)
- All users share the same frequency spectrum
- Divided into time slots, each slot for only one user.
- 交替来,若本slot内传输没结束,等下一个周期
- 每一个时隙之间会加入一小段时间间隔
guard timeGuard time (每个time slot中间,避免overlap)
Advantages:
- Extended battery life, Cost effective, Interference free.
Disadvantages:
- Disconnection, Synchronization overheads.
Contention based protocols
Unslotted ALOHA
- Transmits data whenever there is a data to be transmitted.
- If frame is transmitted successfully, the next frame will be sent.
- Frames are destroyed if collision.
- If failed, resend
- Vulnerable time = 2 * frame transmission time
Slotted ALOHA
- Time of shared channel is divided into equal slots
- Transmit only at the beginning of a time slot
- If two or more transmit in same slot, collision
- If collision occurs, node retransmits frame in subsequent slots until successful transmission.
- Vulnerable time = Frame transmission time
CSMA/CD
-
Carrier Sense Multiple Access with Collision Detection
-
The stations will sense the channel or wire, shared by multiple stations, before trying to use it.
-
CSMA is based on the principal of ‘sense before transmit’
- If idle, transmit entire frame
- If busy, refrain from sending and wait
-
If collision
- retransmits the frame when the channel is free again
-
CD:
- If collision, the corrupt information reaches one of the nodes which is still transmitting, the node detects the information on the bus is not the same.
- Stop immediately enter Binary Exponential Back-off and then retry
-
Back-Off
- After the occurrence of collision, nodes wait a random time before attempting to retransmit data.
- This time depends on the number of attempted unsuccessful transmissions, N
- After a collision, a node waits X slot-times( round-trip time)
- [0, (2^N-1)] (0 <= N <= 10)
- [0, 1023] (11 <= N <= 16)
- After 16 attempts, a station gives up
Internetworking
Repeater中继器
- receives and retransmits an incoming electrical.
- Wi-Fi repeater
- physical layer device, do not have MAC/IP addresses
Bridge
- use bridge to avoid congestion
- Based on MAC address
- at layer 2 / link layer
- Divides LAN into multiple segments
- Maintain serval MAC tables
- Bridge recognizes whether MAC address of DEST is on the same side of the source, if so, it dose not transmit it through the bridge.
ETHERNET
- Connects devices in a wired LAN or WAN.
Pros and Cons
Pros
- Greater Speed than Wi-Fi
- Better signal stability
- Secured connection
- Excellent data transfer quality
- Backward compatibility
Cons
- Mobility is limited
- Higher Installation cost
- Longer cables can create crosstalk
- Port availability
Physical Topology
- Bus
- Star
- Active switch in center
- each dedicated line runs a separate Ethernet protocol (nodes do not collide with each other)
Frame structure
-
Data sent over Ethernet is carried by the ‘frame’.
-
Provides important information, such as addresses, control information, payload data, and checksums.
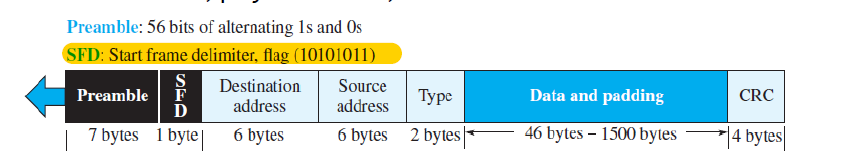
ˈpriːæmbl/前导码`七字节
-
Is used to synchronize receiver
-
SFD: Start Frame Delimiter
/dɪˈlɪmɪtər/(10101011)第一个不按规则出现的就是
以太网mac帧开始的定界符(此时有两个连续的1出现)- beginning of the frame
-
Address
- 6 bytes DEST & SRC MAC address
- If broadcast
- DEST address: FF:FF:FF:FF:FF:FF
-
Type
- Type of data within the frame. IPv4 / IPv6
-
Data
- 46 bytes ~ 1500 bytes
-
CRC
- Cyclic Redundancy Check
- Unique number calculated before the data is sent
- Added to the end of the data frame
- Recalculated by the receiver upon arrival
- Same, keep
- Diff, wrong
- Cyclic Redundancy Check
-
Interframe Gap
-
Space after a frame is sent
以太网帧与帧之间的间隔:12-96字节
-
Transmission pause of 12 bytes.
-
Standards
- Link & Physical layers
- address network devices by MAC address
- unslotted CSMA/CD with back off
- Places data in a ‘frame’.
Wireless
Elements of a wireless network
-
Wireless hosts
- Laptop, smartphone
- Run applications
- May be stationary or mobiles
-
Base station
- Typically connected to wired network
- Relay - responsible for sending packets between wired network and wireless host(s) in its “area”
-
Wireless link
- Typically used to connect host(s) to base station
- Multiple access protocol coordinates link access
- Also used as backbone link
- Various data rates, transmission distance
Network Mode
-
infrastructure mode(有基础设施支持的模式)
-
Devices communicate with each other through an access point; e.g. Router.
-
Handoff: Mobile changes base station providing connection into wired network.
切换:移动设备切换基站(提供接入有线网络)
-
-
Ad-hoc mode(自组织网络模式)
- Also known as “peer-to-peer” mode.
- No base stations required.
- Nodes create network and route among themselves.
- Nodes can only transmit to other nodes within link coverage.
- Easy and secured

Wireless vs Wired
-
No wire needed
-
Decreased signal strength (Path Loss)
- Radio signal attenuates as it propagates through space or other matter like buildings, trees, etc.
-
Interference from other sources
- Standardized wireless network frequencies (e.g., 2.4 GHz) shared by devices (e.g., phone, tablets, earbuds , etc) can interfere to each other.
-
Multipath propagation
- Radio reflects off objects walls, the ground, etc and arrives at the destination at slightly different times. This makes the signal less recognizable
Wireless Network Characteristics
Hidden terminal problem
-
B, A & B, C hear each other
-
A, C can not hear each other, unaware of their interference at B
A,C不知道他们会在B处产生干扰
隐藏终端:两个男人追一个女孩,你是其中一个男人,然后在对方两人约会时,你碰见了他们在约会,然后破坏了两人的约会,情敌遇见发生的事情
Signal attenuation
-
B, A hear each other
-
B, C hear each other
-
A, C can not hear each other, interfering at B
你是一个渣男,你吃着碗里的还想着锅里的,你觉得另一个女孩有可能也喜欢你,所以你很犹豫,脚踏两艘船
Wireless LAN WIFI
- 802.11
- All use CSMA/CA for multiple access
802.11 LAN Architecture
- Host communicates with base station (access point) (AP)
- Basic Service Set (BSS) contains
- wireless hosts
- AP
- AP 和 接入AP的设备
802.11 Channels
- 802.11b
- 2.4GHZ-2.485GHz divided into 11 channels at different frequencies
- Host: must associate with an AP
- Scan channels, listening for beacon frames
- Selects AP to associate with
802.11 Passive / Active Scanning
-
Passive scanning
被动:收到AP的信标
关联请求一致:host->AP
关联响应一致:AP->host- Beacons frames sent from APs
association request frame sent H1->AP后面两项两者一样sassociation response frame sent from selected AP
-
Active scanning
主动:发送探测请求帧
主动:AP回复探测请求帧
关联请求一致:host->AP
关联响应一致:AP->host- Probe request frame broadcast from H1
- Probe Response frames sent from APs
Association Request frame sent: H1 -> AP后面两项两者一样Association Response AP -> H1
Multiple Access
-
802.11: CSMA
-
no collision detection
-
Difficult to receive when transmitting due to weak received signals
可能由于信号的衰减,不能接受到冲突
-
can’t sense all collisions in any case: hidden terminal, fading
可能遇到hidden terminal/fading
-
Interframe Spacing
- SIFS - Short Interframe Spacing
- Control frame or next fragment
- PIFS - PCF Interframe Spacing (Point Coordination Function点协调功能,无竞争)
- PCF frames may be sent here
- DIFS - DCF Interframe Spacing (Distributed Coordination Function分布式协调功能,基于竞争)
- DCF frames may be sent here
- EIFS - Extended Interframe Spacing
- Bad frame recovery done here
802.11 MAC Protocol: CSMA/CA
Sender
在CSMA/CA中,发一个帧之前,都需要"等待"一个相应的帧间间隔,比如发送数据之前至少要等待DIFS时间,发送ACK之前需要等待SIFS时间
DCF包括两种介质访问模式:基本访问模式和可选的RTS/CTS((Request To Send/Clear To Send)访问模式
IEEE802.11协议中,有一个可设置的参数,这个参数叫RTS阈值,如果要传送的帧的大小比这个RTS阈值高,就会启动RTS/CTS机制,即使用RTS/CTS/DATA/ACK的传送方式;如果帧的大小比这个RTS阈值低,则只会使用DATA/ACK的传输方式
- if sense channel idle for DIFS, then transmit entire frame
媒介闲置时间 >DIFS,立即传输 - if sense channel busy then
- start random back-off time
- timer counts down while channel idle
- transmit when timer expires
- if no ACK, increase random backoff interval, repeat step 2
Receiver
- if frame received OK - return ACK after SIFS (ACK needed due to hidden terminal problem)
DCF包括两种介质访问模式:
- 基本访问模式
- 可选的RTS/CTS((Request ToSend/Clear To Send)访问模式。
下面为可选项:
Avoiding Collisions
- Sender first transmits request-to-send (RTS) packets to BS using CSMA
- BS broad casts clear-to-send CTS in response to RTS
- CTS hear by all nodes
- sender transmits data frame
- other stations defer推迟 transmissions
- 接收端收到数据后,用CRC来检验,正确则响应ACK帧
- handshaking can prevent collision
from a hidden station(通过广播CTS的方式实现) - handshaking cannot help with the exposed station problem

B对两边都发送了RTS,C本来可以发给D的,但是因为B所以不能发了
Frame Structure

- Address 1: MAC address of wireless host or AP to receive this frame接收方
-
Address 2: MAC address of wireless host or AP transmitting this frame发送方
-
Address 3: MAC address of router interface to which AP is attached.AP所属的路由器网卡地址
-
Address 4: Used only in ad hoc mode.
-
Duration of reserved transmission time
-
2字节frame control中的2bit表示type Type: RTS / CTS / ACK / data
Advanced Capabilities
- Rate adaptation
- 传输速率(transmission rate)随着距离的变化而改变,SNR也会变
802.15 PAN
- Less than 10 m diameter
- Master / slaved:
- slaves request permission to send
- master grants requests
Drawbacks of the MAC protocols
- Collisions
- Two or more nodes simultaneously transmit on a shared medium.
- Overhearing
- Node drains energy receiving irrelevant packets e.g. unicast packets or redundant broadcast packets.
- Overhead
- Useless data that results energy waste when transmitting or receiving.
- Idle listening
- Node keeps turn on the radio while waiting for the receiving data.
Wireless Technologies for IoT
WSN / IoT Protocol Stack
- Wireless sensor network

-
Data Link Layer - LLC Sublayer
-
LLC is on the top of the MAC sub-layer and is in-charge of achieving good utilization and providing a reliable service to the layers above it.
-
Framing组装成帧
- Data units must be encapsulated into LLC sub-layer frames to add necessary information to perform the sub-layer function.
- The frame size must be kept to minimum to save energy
-
Error Control
- Error detection and error correction mechanism must be embedded to detect, and correct bit errors introduced in the media.
-
Flow Control
- In Low data rate WSNs, flow control is not important and is embedded in error control mechanism.
-
Link Management
- Neighbor discovery, link setup, maintenance and tear down, and link quality estimation
MAC protocols in WSN
- In WSN, MAC protocols are different, because fairness is not as important as in other networks, rarely compete for the channel.
- **Energy is the most important issue**因此,吞吐量和其他的一些因素被牺牲,换取能耗
Energy Problems
-
Collision
-
Overhearing
-
Protocol overhead
-
Idle listening
-
Over emitting
-
Waste of energy when transmitting a message but the destination node is not ready.
接收节点还没有准备好就发送了
-
Communication Patterns
- Broadcast(广播)
- Transmit some information to all sensor nodes of the network.
- Local Gossip(本地闲聊)
- The sensors that detect a change in the environment or sense something and communicate locally.
- Convergecast(收敛广播)
- The sensors that detect something then send what they perceive to the information center
Different MAC protocols
-
Centralized Medium Access(中心节点控制的)
- A central station controls
-
Distributed Medium Access(分布式节点控制的)
-
Schedule based protocols
-
Provides a schedule regulating which participant may use which resource at which time
提供一个时间表,规定哪个参与者可以在哪个时间使用哪个资源
-
Collisions, overhearing and Idle listening are no issues; but time-synchronization is needed
不会产生collision, overhear, idle listening但是需要维持时间同步
-
-
Contention based protocols
-
Risk of colliding
有着方式碰撞的风险
-
Avoid/reduce collisions requires
需要避免/减少碰撞
-
-
Contention-based MAC protocols
Multiple Access with Collision Avoidance (MACA)具有冲突避免的多路访问(即CSMA/CA)
- Sender asks receiver - Request to Send (RTS)
- Receiver sends out a Clear to Send (CTS)
- Other nodes know how long they will transmission and wait.
- Sender sends data, receiver ACKs.
Problem
- 因为 low data rate, idle listening, wastes energy unnecessarily
- Solution
- Use rendezvous
[ˈrɑːndɪvuː]会合mechanism- Turn off nodes and neighboring nodes turn on simultaneously to allow packet exchange
- Use rendezvous
Sensor MAC / S-MAC
-
Solves the energy consumption related problems of Idle listening, collision and overhearing
-
Nodes turns off and on periodically
通过将时间分成两部分来周期性地关闭和开启来减少空闲侦听问题
- Listen & Sleep
-
During sleep, node set a timer and switch its radio off
- timer expires, wake up and listen
-
In order to synchronize, nodes broadcast their schedule to all neighbors with the help of SYNC frame.
- Form virtual clusters(形成虚拟集群)
-
RTS / CTS
Timeout MAC / T-MAC
- S-MAC listen period is fixed length
- 太多 不够 太少 浪费
- Prematurely go back to sleep mode when there is no traffic for a certain time
- Return to the sleep mode when no communication
- Adaptive duty cycle自适应占空比
- Nodes wake up during the beginning of a slot
Preamble Sampling(前导采样)
-
Regularly sample the medium to check for activity, rest of the time change to sleep mode
-
Uses long preambles to alert the receiver node
使用长前导码来提醒接收器节点。
-
Nodes go to sleep and wake up independently (NO SYN)
-
Stay awake until the channel is idle如果信道空闲,则保持清醒
WiseMAC
a preamble of size equal to the sampling period
前导码的长度等于采样周期
Berkeley MAC / B-MAC
Clear Channel Assessment
对渠道是否畅通进行评估
- Sampling of the medium to estimate the noise floor. 首先获得媒介medium的噪声等级
- When a node wants to transmit, it takes the sample of the channel and compares it with noise floor.节点想要发送时,对信道采样,并和noise floor进行比较
- If the sample energy level is below the noise floor then channel is assumed to be clear.
实际应用中的实际:
-
For actual assessment when sending a packet, looks at five channel samples看5份信道采样
- Channel is assumed as free, when even a single sample is significantly below noise; transmits哪怕只有一个信道样本低于noise floor,信道都被认定为free,发送
- If channel is found busy, Random back-off如果busy,随机回退
-
Employs an adaptive preamble sampling scheme to reduce duty cycle and minimize idle listening.
采用自适应前导采样方案来减少占空比并最大限度地减少空闲侦听
-
发消息之前发preambles,时间要大于duty cycle,怕receiver sleep,收不到

Advantages of B-MAC
-
Low Power Listening采用前导采样,不用一直监听了
-
Uses the clear channel assessment techniques to decide whether there is packet arriving when node wakes up使用clear channel assessment来检测是否有packet到达
-
Timeout puts node back to sleep if no packet arrived如果没有packet到达,timeout使得节点回到sleep状态
-
No synchronization or control packets like RTS/CTS
-
clean and simple interface
Default MAC protocol for WSN
Schedule-based MAC protocols - LEACH
-
low-energy Adaptive Clustering Hierarchy
-
Dense network of sensor nodes reporting to a central sink
大量的传感器网络节点向
中心节点sink报道 -
Each node can reach the sink or base station directly
每个节点都能直接连接到
中心节点sink
Idea
- Nodes are clusters, controlled by a cluster-head(CH)
- CDMA for all members of the cluster
- TDMA is used within the cluster
Operates
Setup phase
- CHs advertise themselves; other nodes join the CH with the strongest signal
- broadcast schedule is distributed by the CH
Steady-state phase
- CH collects and aggregates data from all cluster members using TDMA-style frames and time slot
- CH reports aggregated data to the base station
- CH must remain awake at all times to receive sensor data from its cluster members
ZIGBEE / 802.15.4
- PHY layer and MAC layer
Features
- Extremely low cost
- Ease of installation
- Reliable data transfer
- Short range operation
- Lower duty cycle
PHY
从硬件的角度看,以太网接口电路主要由MAC(Media Access Control)控制器和物理层接口PHY(Physical Layer,PHY)两大部分构成

PHY Packet Fields
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Tt7cuwkI-1640632529934)(D:\photo\photolibrary\image-20211209012243520.png)]
- Preamble (4 bytes)
- Start of packet delimiter (1 byte)
- PHY header (1 byte)
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-sO3Ytczx-1640632529935)(C:\Users\Yubo\AppData\Roaming\Typora\typora-user-images\image-20201210151453028.png)]
-
27 channels total
Zigbee技术是一种极低复杂度、低成本、低功耗、低速率的无线连接技术,应用低速率无线个人区域网(LR-WPAN)LR-WPAN中设备的分类:
LR-WPAN中包含两种不同类型的设备:全功能设备(FFD)和简单功能设备(RFD)。
FFD:全功能设备可作为整个PAN中的网络协调器、路由器或终端。FFD可以和RFD或者FFD通信,而RFD只能与FFD通信。
RFD:简单功能设备在PAN中主要是一个终端,不能传输大规模的数据,同一时刻只能和一个FFD联系。
Device classes
Full function device (FFD)
- Any topology
- PAN coordinator capable
PAN中的网络协调器 - Talks to any other device
FFD可以和RFD或者FFD通信 - Implements complete protocol set
实现全协议的设备
Reduced function device (RFD)
- Limited to star topology or end-device in a peer-to-peer network.
只能为星形/端设备 - Cannot become a PAN coordinator
RFD只能与FFD通信 - Very simple implementation
- Reduced protocol set
IEEE802.15.4定义了物理层(PHY层)和MAC层。Zigbee联盟提供网络层和应用层结构。
Definitions
-
Network devices: RFD or FFD containing IEEE 802.15.4 MAC and PHY interface
-
Coordinator: An FFD with network device functionality provides coordination and other services to the network.
网络协调器: 具有网络设备功能的 FFD,可为网络提供协调和其他服务
-
PAN coordinator: It acts as a cluster head through which all the communication takes place. Talk to any other device and controls the overall functions of a PAN.
- A network has exactly one PAN coordinator
PAN 协调器:它充当
cluster head,所有通信都通过它进行。它可以与任何其他设备通信并控制 PAN 的整体功能。一个网络只有一个 PAN 协调器
Topology
- Star topology
- FFD建立自己的network, RFD 不能是PAN coordinator
- Peer-Peer topology
- 大部分是
FFD, 且RFD一定是leave node(没有连接其他,随时可能断开的节点)
- 大部分是
- Combined
Optional superframe structure

- Network Beacon: Transmitted by network coordinator. Contains network information, frame structure and notification of pending node messages.
- CAP 11 slots
- CFP 5 slots: reserved nodes
Guaranteed Time Slot (GTS)
- Time slot dedicated exclusively to a device
- Can be allocated only by the PAN coordinator
- GTS has to be allocated before it is used
- Allocated on a first-come-first-serve basis
- Completely managed by the PAN coordinator even after allocation
- Takes one or more Time-Slots of contention free period.
MAC Frame Format




Data Service
- Data transfer to neighboring devices
- ACK or UNACK
- Direct or indirect
- Using GTS service
IEEE 802.11ah
- Enhancements to the IEEE802.11 MAC to support this PHY.
- Transmission rate up to 1 km
- Lower Energy Consumption
- Data rates > 100kbps
- Support up to 8196 connected devices
- Advantages of transmitting in sub 1 GHz
- Spectrum characteristics
- Reliability
- Battery operation
Features
- Short Beacons
- Beacons are sent frequently at the lowest rate
- short (more frequent)
- full beacons (less frequent)
- Beacons are sent frequently at the lowest rate
- Implicit acknowledgment (no ACK needed)
- support thousands of associated devices (increases coverage → increases reachable STAs)
Long Range Radio (LoRa)
- Range-2.5 Km in dense urban and 15 km in suburban areas.
- Pros
- Supports thousands of nodes.
-serve basis
- Supports thousands of nodes.
- Completely managed by the PAN coordinator even after allocation
- Takes one or more Time-Slots of contention free period.






















 1704
1704











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








