crypto
RSA_e_n
维纳攻击
from RSAwienerHacker import hack_RSA
import binascii,gmpy2
e=0x14b367bf01efd4dc667b8e62975479c612c96e78f7f1f55242b2973c882ddcb33a65c52174d8ae1273764ce429054ea3f2fdc38ff205443c92ef4198739f05aa11fc10d3fc6ff30c8f5f05a04f43e3d8fc9bfffe916b2e0360560a162729e91b7775bda70177e0f875626e0a81bd4eacea9948b02232a82659f8d9aa9b4c754f
n=0x75be564267f8bf6c2038dd0cadfeecbc3158acfc27e679dd0bdb0db0e90bd5198a0a7edc0626f357a2d75f3c37ede045b7f7ca6bda79e5bf6fc0aea0aa7beda587388599d2b77b538fc3e666784493ffaf731e2ae232e8e9e9f9f2a4df25c19b7680f5bf6c485bd87923f01c17d8ec35438772c28e361774e6e7681d67ecbe19
d=hack_RSA(e,n)
c=10127659956533419108589656976567211166527205183773088147543122705230809548550336271584049969380709512046523116316965506372940655242616078713681678662841367955124154879878984026023241163358487655249424233120021240245459984899558747887087199609289148343740081670749999484769650710161617077523656215330005636913
m=pow(c ,d ,n)
print(hex(m))
print(binascii.unhexlify(hex(m)[2:].strip("L")))
#Hacked!
#0x48454354467b5253415f4c4c4c5f31735f73305f7573656675312121217d
#b'HECTF{RSA_LLL_1s_s0_usefu1!!!}'
re-rsa
基本面

exe文件 64位 无壳
静态分析

发现py字符串 加上题目名称提示我们可以猜测应该是pyinstaller打包之后的rsa解密
提取文件 pyc转py
# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: 123456.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
import math
print('please input you flag:')
s = input()
e1 = 65537
e2 = 72613
n = 95525425639268618904242122073026771652646935213019341295993735437526311434723595304323184458026403667135481765527601691276167501123468272392153875706450309539988975293150023714062357483846051629494980532347703161226570915424953846206752605423302029528621365549138045079620953801043515344814417917150911967549
c1 = 50016380988825140771789180404368584321245554683013673243046447860755867497534086012885574115002127671925300478433415755560263795098483437759149032753639933337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
c2 = 26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
h = ''
for i in range(len(s)):
x = hex(ord(s[i]))[2:]
if len(x) < 2:
x = '0' + x
h = h + x
else:
m = int(h, 16)
if pow(m, e1, n) == c1 and pow(m, e2, n) == c2:
print('Successful!')
else:
print('Wrong flag!')
# okay decompiling E:\��������\python-exe-unpacker-master\123456.pyc
解密脚本1(2e2c1n)
from Crypto.Util.number import long_to_bytes, bytes_to_long
from gmpy2 import gcdext,invert
n=95525425639268618904242122073026771652646935213019341295993735437526311434723595304323184458026403667135481765527601691276167501123468272392153875706450309539988975293150023714062357483846051629494980532347703161226570915424953846206752605423302029528621365549138045079620953801043515344814417917150911967549
e1=65537
e2=72613
c1=50016380988825140771789180404368584321245554683013673243046447860755867497534086012885574115002127671925300478433415755560263795098483437759149032753639933337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
c2=26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
print(c1)
print(c2)
(tmp,s1,s2)=gcdext(e1,e2)
if s1<0:
s1=-s1
c1=invert(c1,n)
else:
s2=-s2
c2=invert(c2,n)
m=(pow(c1,s1,n)*pow(c2,s2,n))%n
print(long_to_bytes(m))
#50016380988825140771789180404368584321245554683013673243046447860755867497534086012885574115002127671925300478433415755560263795098483437759149032753639933337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
#26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
#b'HECTF{RSA_and_PyInstaller_1s_ve7y_ea$y!!!}'
解密脚本2(共模)
import sys
import binascii
sys.setrecursionlimit(1000000)
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
c1=50016380988825140771789180404368584321245554683013673243046447860755867497534086012885574115002127671925300478433415755560263795098483437759149032753639933337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
n=95525425639268618904242122073026771652646935213019341295993735437526311434723595304323184458026403667135481765527601691276167501123468272392153875706450309539988975293150023714062357483846051629494980532347703161226570915424953846206752605423302029528621365549138045079620953801043515344814417917150911967549
e1=65537
c2=26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
e2=72613
s = egcd(e1, e2)
s1 = s[1]
s2 = s[2]
if s1<0:
s1 = - s1
c1 = modinv(c1, n)
elif s2<0:
s2 = - s2
c2 = modinv(c2, n)
m=(pow(c1,s1,n)*pow(c2,s2,n)) % n
print(m)
print (binascii.unhexlify(hex(m)[2:].strip("L")))
LittleRSA
import random
import hashlib
import string
import sympy
import gmpy2
from Crypto.Util.number import *
se = random.randint(1,1000)
random.seed(se)
STR = list(string.ascii_letters+string.digits)
proof = ''.join([STR[random.randint(1, 62)-1] for _ in range(20)])
digest = hashlib.sha256(proof.encode()).hexdigest()
print(proof[4:])
print(digest)
e = sympy.nextprime(int(bytes(proof[:4],'utf-8').hex(),16))
p = sympy.nextprime(random.randint(pow(2,1023),pow(2,1024)))
q = sympy.nextprime(random.randint(pow(2,1023),pow(2,1024)))
flag = b'HECTF{XXXXXXXXXXXXXXX}'
m = bytes_to_long(flag)
n = p*q
c = pow(m,e,n)
print(c)
'''
NYAdQidL59lHklvI
1c92e2001540854eb03a06aa37b7bdc76b41a42d315c6dafb02bb339de9a3f25
12424425564383219080490551209643464847620938168930079127681706857658268732506553762185733232174616369346638607986790966147165572856020333466266950817761290120789562282899235194115801039977159247279287016533562522176851376987246778559325369725945217698449887185588509259585902043152698222880550864805704835462119046093822533459389519887750590547895454677651757127860660687183857783014508127001807318860919181678041597391665738436983340807978924856116264434249926664228272176813107767851582594893815624629540970573254201006817388643737600565142486019783712277126799182049309476758941334813964777650021632346392783087599
'''
看着挺复杂的一道rsa 不要慌其实只要知道它
其实难点就是猜测他的种子
他已经给了我们校验位
所以我们只需要写个简单的脚本
爆破出它的种子就可以了
import random
import string
for se in range(0,1000):
random.seed(se)
STR = list(string.ascii_letters+string.digits)
proof = ''.join([STR[random.randint(1, 62)-1] for _ in range(20)])
flag = 'NYAdQidL59lHklvI'
if proof[4:] == flag:
print(se)
#571
我们将爆破出的种子带入我们的rsa脚本中
运行后可以得到我们想要的所有的数值e p q n c
import random
import hashlib
import string
import sympy
import gmpy2
from Crypto.Util.number import *
random.seed(571)
STR = list(string.ascii_letters+string.digits)
proof = ''.join([STR[random.randint(1, 62)-1] for _ in range(20)])
digest = hashlib.sha256(proof.encode()).hexdigest()
e = sympy.nextprime(int(bytes(proof[:4],'utf-8').hex(),16))
print(e)
p = sympy.nextprime(random.randint(pow(2,1023),pow(2,1024)))
print(p)
q = sympy.nextprime(random.randint(pow(2,1023),pow(2,1024)))
print(q)
flag = b'HECTF{XXXXXXXXXXXXXXX}'
m = bytes_to_long(flag)
n = p*q
print(n)
c = pow(m,e,n)
print(c)
'''
NYAdQidL59lHklvI
1c92e2001540854eb03a06aa37b7bdc76b41a42d315c6dafb02bb339de9a3f25
12424425564383219080490551209643464847620938168930079127681706857658268732506553762185733232174616369346638607986790966147165572856020333466266950817761290120789562282899235194115801039977159247279287016533562522176851376987246778559325369725945217698449887185588509259585902043152698222880550864805704835462119046093822533459389519887750590547895454677651757127860660687183857783014508127001807318860919181678041597391665738436983340807978924856116264434249926664228272176813107767851582594893815624629540970573254201006817388643737600565142486019783712277126799182049309476758941334813964777650021632346392783087599
'''
#1785803627
#145761905930263138706936874952287989451163740801768124316638194142053136728482823176175006571074964544663304793459554206652959217189535730286200684386647465283995296122915022195050319604559741051002366944416141348676197874185262201649841435463619858083016023221897609700155299995358787406738947679758978398079
#91536557984668704700241147674513341431163262522271166024774731241046009089878244315861936297361116478818372387622618452092967843503795947991656539912625954357511406372314568099344007331186921707503763242814545509139824084213975728811966334411984509916811665096919194290285039049454829579869446244711563361247
#13342543154141356928237037014835662778253580667782108942569184904965289043128597806773614650021113373976693739380228024957362608294586683189481439958652548773879112702665177133083028025373319763201541205132676693787014198267385918391685536223655448390543553734735764017234993237167620400766820574691092303878050425083500151337247013764395756976500432514102466791323279875149999093398122104519412533229094658809423590134371192653476346624983151023383782409665927965094170518538732848716031270835255344934456063035577156958220080623245389718106934469954850798774165827963729082580605168695584722304893781039956847844513
#3563950014312812669732328924672310602497103750296851566716046900480862207774871793098361097565057964574977166251841619016016766524352728059103489917294454241234238311885220119844106777348853355269118917520276873957967185852513396520094551756497556734205429207486551831989837273187621600536966569074784654048462264419905813068211446715153051078546356314484223673999033848204191955340203070409621642570105695375836205779490219026932562133958372727024848802331650916775500283273859295065476074459093778093373234034514742505603296217229217116003533167192617451435209289167518504103542547898573481462127526348806418685069
但是注意c的值经过了pow加密 加密之后的数值显然不是我们想要的
真正的值为最一开始题目给我们的注释值
知道了我们所需要的大部分数值直接套基础解密脚本就行了
import binascii
import gmpy2
n=13342543154141356928237037014835662778253580667782108942569184904965289043128597806773614650021113373976693739380228024957362608294586683189481439958652548773879112702665177133083028025373319763201541205132676693787014198267385918391685536223655448390543553734735764017234993237167620400766820574691092303878050425083500151337247013764395756976500432514102466791323279875149999093398122104519412533229094658809423590134371192653476346624983151023383782409665927965094170518538732848716031270835255344934456063035577156958220080623245389718106934469954850798774165827963729082580605168695584722304893781039956847844513
p=145761905930263138706936874952287989451163740801768124316638194142053136728482823176175006571074964544663304793459554206652959217189535730286200684386647465283995296122915022195050319604559741051002366944416141348676197874185262201649841435463619858083016023221897609700155299995358787406738947679758978398079
q=91536557984668704700241147674513341431163262522271166024774731241046009089878244315861936297361116478818372387622618452092967843503795947991656539912625954357511406372314568099344007331186921707503763242814545509139824084213975728811966334411984509916811665096919194290285039049454829579869446244711563361247
e=1785803627
c=12424425564383219080490551209643464847620938168930079127681706857658268732506553762185733232174616369346638607986790966147165572856020333466266950817761290120789562282899235194115801039977159247279287016533562522176851376987246778559325369725945217698449887185588509259585902043152698222880550864805704835462119046093822533459389519887750590547895454677651757127860660687183857783014508127001807318860919181678041597391665738436983340807978924856116264434249926664228272176813107767851582594893815624629540970573254201006817388643737600565142486019783712277126799182049309476758941334813964777650021632346392783087599
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(hex(m))
print(binascii.unhexlify(hex(m)[2:].strip("L")))
#0x48454354467b79756a6e626734726473773378646676726667797274677663647d
#b'HECTF{yujnbg4rdsw3xdfvrfgyrtgvcd}'
encode
附件 010查看为zip类型 改后缀解压

解压后为md文档
明显emoji密码

你好呀,送你串字符吧:ɯlxɹƃluʌ‾ʌdɹo‾ɟlq‾lʍ : dǝʇs ʇsɐl
感觉为倒序的字母 正过来

last step : wl_blf_orpv_vnlgrxlm
根据题目提示我们可以找到埃特巴什密码
进行解密

HECTF{do_you_like_emoticon}
misc
snake
贪吃蛇小游戏
exe文件但是看logo明显是经过了pyinstaller打包之后的
直接提取文件

修复一下snake的文件结构

修复完后的snake是pyc文件 转成py文件
查看源码
# uncompyle6 version 3.7.4
# Python bytecode 3.7 (3394)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: snake.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
import pygame, sys, random
SCREEN_X = 700
SCREEN_Y = 700
class Snake(object):
def __init__(self):
self.dirction = pygame.K_RIGHT
self.body = []
for x in range(5):
self.addnode()
def addnode(self):
left, top = (0, 0)
if self.body:
left, top = self.body[0].left, self.body[0].top
else:
node = pygame.Rect(left, top, 20, 20)
if self.dirction == pygame.K_LEFT:
node.left -= 20
else:
if self.dirction == pygame.K_RIGHT:
node.left += 20
else:
if self.dirction == pygame.K_UP:
node.top -= 20
else:
if self.dirction == pygame.K_DOWN:
node.top += 20
self.body.insert(0, node)
def delnode(self):
self.body.pop()
def isdead(self):
if self.body[0].x not in range(SCREEN_X):
return True
if self.body[0].y not in range(SCREEN_Y):
return True
if self.body[0] in self.body[1:]:
return True
return False
def move(self):
self.addnode()
self.delnode()
def changedirection(self, curkey):
LR = [
pygame.K_LEFT, pygame.K_RIGHT]
UD = [pygame.K_UP, pygame.K_DOWN]
if curkey in LR + UD:
if curkey in LR:
if self.dirction in LR:
return
if curkey in UD:
if self.dirction in UD:
return
self.dirction = curkey
class Food:
def __init__(self):
self.rect = pygame.Rect(-20, 0, 20, 20)
def remove(self):
self.rect.x = -20
def set(self):
if self.rect.x == -20:
allpos = [
(220, 620), (140, 580), (380, 280), (320, 260), (440, 500), (320, 100), (420, 240), (380, 260), (160, 280), (480, 460), (340, 260), (420, 580), (140, 460), (180, 380), (60, 160), (200, 100), (320, 620), (120, 540), (360, 480), (420, 460), (100, 40), (280, 100), (60, 60), (100, 480), (20, 60), (100, 80), (500, 320), (300, 500), (60, 320), (560, 220), (400, 100), (360, 20), (460, 380), (100, 400), (100, 500), (400, 60), (520, 320), (160, 60), (480, 440), (360, 600), (140, 540), (520, 220), (500, 220), (80, 60), (520, 280), (260, 60), (320, 320), (320, 240), (460, 280), (580, 20), (140, 80), (40, 240), (420, 420), (100, 440), (180, 60), (140, 420), (220, 400), (440, 300), (240, 380), (420, 480), (360, 260), (460, 320), (160, 100), (260, 80), (520, 40), (200, 260), (360, 580), (100, 380), (80, 620), (360, 620), (340, 440), (200, 60), (200, 300), (20, 500), (400, 20), (120, 620), (540, 220), (240, 420), (320, 200), (60, 300), (260, 320), (300, 580), (160, 480), (140, 200), (100, 420), (420, 20), (360, 500), (240, 500), (140, 620), (260, 620), (100, 100), (540, 60), (420, 380), (240, 400), (60, 180), (480, 380), (40, 500), (560, 320), (320, 280), (260, 280), (160, 540), (300, 440), (60, 200), (560, 280), (240, 260), (200, 280), (180, 500), (100, 20), (540, 20), (320, 300), (80, 600), (380, 200), (20, 40), (440, 580), (580, 60), (420, 400), (140, 60), (120, 440), (520, 20), (260, 40), (320, 220), (360, 560), (100, 460), (200, 20), (80, 520), (60, 500), (300, 600), (520, 60), (420, 260), (260, 260), (140, 100), (380, 240), (160, 300), (500, 260), (400, 540), (560, 60), (480, 400), (380, 320), (400, 80), (580, 500), (240, 480), (160, 600), (440, 380), (540, 280), (160, 620), (380, 20), (460, 440), (400, 620), (400, 40), (300, 480), (420, 560), (20, 20), (500, 280), (300, 100), (60, 280), (360, 200), (240, 460), (520, 100), (340, 200), (500, 300), (440, 20), (420, 300), (240, 620), (140, 20), (300, 20), (420, 280), (20, 80), (220, 500), (320, 20), (60, 260), (300, 460), (200, 320), (520, 80), (140, 40), (420, 440), (60, 220), (480, 480), (180, 20), (180, 100), (320, 440), (160, 580), (80, 560), (360, 460), (100, 60), (120, 580), (420, 320), (560, 20), (300, 620), (40, 60), (360, 440), (420, 500), (60, 240), (100, 240), (240, 440), (260, 300), (260, 500), (120, 260), (140, 320), (480, 500), (20, 100), (500, 240), (120, 560), (380, 300), (80, 580), (420, 600), (140, 260), (80, 140), (300, 560), (120, 200), (220, 260), (160, 400), (280, 20), (160, 20), (100, 220), (540, 500), (380, 220), (460, 500), (560, 500), (120, 320), (540, 320), (80, 340), (340, 620)]
random.shuffle(allpos)
self.rect.left, self.rect.top = random.choice(allpos)
def show_text(screen, pos, text, color, font_bold=False, font_size=30, font_italic=False):
cur_font = pygame.font.SysFont('宋体', font_size)
cur_font.set_bold(font_bold)
cur_font.set_italic(font_italic)
text_fmt = cur_font.render(text, 1, color)
screen.blit(text_fmt, pos)
def main():
pygame.init()
screen_size = (SCREEN_X, SCREEN_Y)
screen = pygame.display.set_mode(screen_size)
pygame.display.set_caption('Welcome to HECTF,enjoy!')
clock = pygame.time.Clock()
scores = 0
isdead = False
snake = Snake()
food = Food()
while True:
for event in pygame.event.get():
if event.type == pygame.QUIT:
sys.exit()
if event.type == pygame.KEYDOWN:
snake.changedirection(event.key)
if event.key == pygame.K_SPACE and isdead:
return main()
screen.fill((205, 205, 205))
if not isdead:
snake.move()
for rect in snake.body:
pygame.draw.rect(screen, (0, 220, 0), rect, 0)
isdead = snake.isdead()
if isdead:
show_text(screen, (100, 200), 'You lose :(', (227, 29, 18), False, 100)
show_text(screen, (150, 260), 'press SAPCE to try again...', (0, 0, 22), False, 30)
if food.rect == snake.body[0]:
scores += 100
food.remove()
snake.addnode()
food.set()
pygame.draw.rect(screen, (136, 0, 21), food.rect, 0)
show_text(screen, (50, 600), 'Scores: ' + str(scores), (223, 0, 0))
if scores > 400:
show_text(screen, (100, 650), 'f', (223, 223, 0))
if scores > 500:
show_text(screen, (110, 650), 'l', (223, 223, 0))
if scores > 600:
show_text(screen, (120, 650), 'a', (223, 223, 0))
if scores > 700:
show_text(screen, (130, 650), 'g', (223, 223, 0))
if scores > 800:
show_text(screen, (150, 650), 'i', (223, 223, 0))
if scores > 900:
show_text(screen, (160, 650), 's', (223, 223, 0))
show_text(screen, (450, 650), 'Try to get 6000 points', (223, 223, 223))
if scores >= 6000:
show_text(screen, (100, 670), 'wtf,you really got 6000 points?check the source code', (223,
223,
223))
show_text(screen, (100, 470), 'the original author is codetask from', (223,
223,
223))
show_text(screen, (100, 490), 'https://gitee.com/codetimer,thanks to him', (223,
223,
223))
pygame.display.update()
clock.tick(10)
if __name__ == '__main__':
main()
# okay decompiling snake.pyc
提取出的py文件就是游戏的源码
出题人给了提示去观察源码
看了源码发现与出题人的源码唯一的不同在于食物的坐标不同
我们猜测食物的坐标是有问题的
取出食物的所有坐标转为字符串
f = open("123.txt","w")
key = [(220, 620), (140, 580), (380, 280), (320, 260), (440, 500), (320, 100), (420, 240), (380, 260), (160, 280), (
480, 460), (340, 260), (420, 580), (140, 460), (180, 380), (60, 160), (200, 100), (320, 620), (120, 540), (360, 480), (
420, 460), (100, 40), (280, 100), (60, 60), (100, 480), (20, 60), (100, 80), (500, 320), (300, 500), (60, 320), (
560, 220), (400, 100), (360, 20), (460, 380), (100, 400), (100, 500), (400, 60), (520, 320), (160, 60), (480, 440), (
360, 600), (140, 540), (520, 220), (500, 220), (80, 60), (520, 280), (260, 60), (320, 320), (320, 240), (460, 280), (
580, 20), (140, 80), (40, 240), (420, 420), (100, 440), (180, 60), (140, 420), (220, 400), (440, 300), (240, 380), (
420, 480), (360, 260), (460, 320), (160, 100), (260, 80), (520, 40), (200, 260), (360, 580), (100, 380), (80, 620), (
360, 620), (340, 440), (200, 60), (200, 300), (20, 500), (400, 20), (120, 620), (540, 220), (240, 420), (320, 200), (
60, 300), (260, 320), (300, 580), (160, 480), (140, 200), (100, 420), (420, 20), (360, 500), (240, 500), (140, 620), (
260, 620), (100, 100), (540, 60), (420, 380), (240, 400), (60, 180), (480, 380), (40, 500), (560, 320), (320, 280), (
260, 280), (160, 540), (300, 440), (60, 200), (560, 280), (240, 260), (200, 280), (180, 500), (100, 20), (540, 20), (
320, 300), (80, 600), (380, 200), (20, 40), (440, 580), (580, 60), (420, 400), (140, 60), (120, 440), (520, 20), (
260, 40), (320, 220), (360, 560), (100, 460), (200, 20), (80, 520), (60, 500), (300, 600), (520, 60), (420, 260), (
260, 260), (140, 100), (380, 240), (160, 300), (500, 260), (400, 540), (560, 60), (480, 400), (380, 320), (400, 80), (
580, 500), (240, 480), (160, 600), (440, 380), (540, 280), (160, 620), (380, 20), (460, 440), (400, 620), (400, 40), (
300, 480), (420, 560), (20, 20), (500, 280), (300, 100), (60, 280), (360, 200), (240, 460), (520, 100), (340, 200), (
500, 300), (440, 20), (420, 300), (240, 620), (140, 20), (300, 20), (420, 280), (20, 80), (220, 500), (320, 20), (
60, 260), (300, 460), (200, 320), (520, 80), (140, 40), (420, 440), (60, 220), (480, 480), (180, 20), (180, 100), (
320, 440), (160, 580), (80, 560), (360, 460), (100, 60), (120, 580), (420, 320), (560, 20), (300, 620), (40, 60), (
360, 440), (420, 500), (60, 240), (100, 240), (240, 440), (260, 300), (260, 500), (120, 260), (140, 320), (480, 500), (
20, 100), (500, 240), (120, 560), (380, 300), (80, 580), (420, 600), (140, 260), (80, 140), (300, 560), (120, 200), (
220, 260), (160, 400), (280, 20), (160, 20), (100, 220), (540, 500), (380, 220), (460, 500), (560, 500), (120, 320), (
540, 320), (80, 340), (340, 620)]
key = [str(i) for i in key]
key = '\n'.join(key)
key = key.replace("(","")
key = key.replace(")","")
f.write(key)
使用Gunplot进行画图
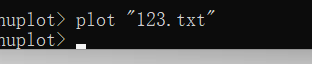


使用画图工具 可以看出flag
JamesHarden
解压后打开发现PK头可以猜测是 压缩文件

解压后打开发现是class文件 用jd-gui或者luyten打开可以看到
明显的凯撒密码
13位位移
hectf{we1c0me_t0_h3ct6_!}
捉迷藏
打开为doc文件

常见的就是零宽和隐藏
解除字体隐藏后
出现了作文的分割线?
不对我们放大看一下

jsfuck编码
解码

HECTF{dfdfj234kflfj3fadfdsv}
迷途的狗狗


有加密 无法爆破
拖到010中查看下

修改一下版本号
还是无法爆破 用WinRAR修复一下

再次进行爆破

取出文件为一张jpg图片
分离图片即可拿到flag

re
hard

签到题直接搜字符串即可
Baby_pp
易语言
看下基本面

64位 无壳
静态分析

又是pyinstaller打包之后的易语言?
用样的操作 提取一下文件
# uncompyle6 version 3.7.4
# Python bytecode 3.8 (3413)
# Decompiled from: Python 3.8.5 (tags/v3.8.5:580fbb0, Jul 20 2020, 15:57:54) [MSC v.1924 64 bit (AMD64)]
# Embedded file name: main.py
# Compiled at: 1995-09-28 00:18:56
# Size of source mod 2**32: 272 bytes
import random
ens = '742641edefb6770733ab5932325106b3a5fa75222791d09e451161c46f15504402b32737362443d4df7d136145cd970b54116669c230'
def encode(s, nuum):
step = len(s) // nuum
ens = ''
for i in range(step):
ens += s[i::step]
else:
return ens
def main():
random.seed(10085)
u_input = input(': ')
t = ''
for i in u_input:
t += '%02x' % (ord(i) ^ random.randint(0, 127))
else:
eni = encode(t, 6)
if eni == ens:
print('Success!')
else:
print('Failed!')
if __name__ == '__main__':
main()
# okay decompiling main.pyc
先分析一下这个函数
ens = '742641edefb6770733ab5932325106b3a5fa75222791d09e451161c46f15504402b32737362443d4df7d136145cd970b54116669c230'
def encode(s, nuum):
step = len(s) // nuum
ens = ''
for i in range(step):
ens += s[i::step]
else:
return ens
其实就是将字符串s按照步长依次取出 每取完一组就相当于进行了一个循环
然后将每一组依次按照顺序放到ens中
所以解密脚本就很容易写了
key = ''
ens = '742641edefb6770733ab5932325106b3a5fa75222791d09e451161c46f15504402b32737362443d4df7d136145cd970b54116669c230'
for i in range(6):
key += ens[i::6]
#7e7a3b794c5b3d1c564d7b23515403643d492e055a2d16422d691c6f7915201f474f17124b330f29610347406316326a7e15273d5b60
第二部分
def main():
random.seed(10085)
u_input = input(': ')
t = ''
for i in u_input:
t += '%02x' % (ord(i) ^ random.randint(0, 127))
else:
eni = encode(t, 6)
if eni == ens:
print('Success!')
else:
print('Failed!')
既然已经有了种子那么random生成的随意的数就是确定的
只需要知道for i in u_input循环想表达的意思是啥就可以了
其实可以看到就是一个简单的异或算法我们只需要按照原来的顺序异或回去就可以了
import random
key1 = [0x7e,0x7a,0x3b,0x79,0x4c,0x5b,0x3d,0x1c,0x56,0x4d,0x7b,0x23,0x51,0x54,0x03,0x64,0x3d,0x49,0x2e,0x05,0x5a,0x2d,0x16,0x42,0x2d,0x69,0x1c,0x6f,0x79,0x15,0x20,0x1f,0x47,0x4f,0x17,0x12,0x4b,0x33,0x0f,0x29,0x61,0x03,0x47,0x40,0x63,0x16,0x32,0x6a,0x7e,0x15,0x27,0x3d,0x5b,0x60]
random.seed(10085)
y = ''
print(key1)
for i in range(len(key1)):
y += chr(key1[i] ^ random.randint(0,127))
print(y)
#HECTF{decrypt(80410840840842108808881088408084210842)}
只含有0148 可以猜测云影密码
def de_code(c):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
flag = []
c2 = [i for i in c.split("0")]
for i in c2:
c3 = 0
for j in i:
c3 += int(j)
flag.append(dic[c3 - 1])
return flag
def encode(plaintext):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
m = [i for i in plaintext]
tmp = [];flag = []
for i in range(len(m)):
for j in range(len(dic)):
if m[i] == dic[j]:
tmp.append(j + 1)
for i in tmp:
res = ""
if i >= 8:
res += int(i/8)*"8"
if i%8 >=4:
res += int(i%8/4)*"4"
if i%4 >=2:
res += int(i%4/2)*"2"
if i%2 >= 1:
res += int(i%2/1)*"1"
flag.append(res + "0")
print ("".join(flag)[:-1])
c = input("输入要解密的数字串:")
print(de_code(c))
#m_code = input("请输入要加密的数字串:")
#encode(m_code)
#['H', 'E', 'L', 'L', 'O', 'P', 'Y', 'T', 'H', 'O', 'N']
HECTF{HELLOPYTHON}





















 1664
1664











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








