__int64 __fastcall main(int a1, char **a2, char **a3)
{
__int64 v3; // rdx
bool v4; // bl
__int64 v5; // rax
__int64 v6; // rdx
__int64 v7; // rax
__int64 v8; // rdx
__int64 v9; // rax
__int64 v10; // rsi
__int64 v11; // rdx
__int64 v12; // rax
char v14; // [rsp+Fh] [rbp-1E1h] BYREF
char v15[32]; // [rsp+10h] [rbp-1E0h] BYREF
char v16[32]; // [rsp+30h] [rbp-1C0h] BYREF
int v17[8]; // [rsp+50h] [rbp-1A0h] BYREF
char v18[32]; // [rsp+70h] [rbp-180h] BYREF
char v19[32]; // [rsp+90h] [rbp-160h] BYREF
char v20[32]; // [rsp+B0h] [rbp-140h] BYREF
char v21[32]; // [rsp+D0h] [rbp-120h] BYREF
char v22[32]; // [rsp+F0h] [rbp-100h] BYREF
char v23[32]; // [rsp+110h] [rbp-E0h] BYREF
char v24[32]; // [rsp+130h] [rbp-C0h] BYREF
char v25[136]; // [rsp+150h] [rbp-A0h] BYREF
unsigned __int64 v26; // [rsp+1D8h] [rbp-18h]
v26 = __readfsqword(0x28u);
v17[0] = 1;
v17[1] = 2;
v17[2] = 3;
v17[3] = 4;
v17[4] = 5;
v17[5] = 6;
v17[6] = 7;
std::allocator<char>::allocator(v16, a2, a3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v18, "ISCCYES", v16);
std::allocator<char>::~allocator(v16);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v19);
std::operator<<<std::char_traits<char>>(&std::cout, "id: ");
std::operator>><char>(&std::cin, v19);
std::istream::get((std::istream *)&std::cin);
sub_4A5A(v25, v19);
std::allocator<char>::allocator(v16, v19, v3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(
v20,
"cfe6902ba6404626f1bcabc81e72767b",
v16);
std::allocator<char>::~allocator(v16);
sub_4CE4(v24, v25);
v4 = (unsigned int)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::compare(v24, v20) == 0;
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v24);
if ( v4 )
{
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v21);
v5 = std::operator<<<std::char_traits<char>>(&std::cout, "Please give me the flag:");
std::ostream::operator<<(v5, &std::endl<char,std::char_traits<char>>);
std::operator>><char>(&std::cin, v21);
std::allocator<char>::allocator(v16, v21, v6);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v24, "{", v16);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v23, v21);
sub_2A5F(v15, v23, v24);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v23);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v24);
std::allocator<char>::~allocator(v16);
v7 = sub_38CA(v15);
if ( (unsigned __int8)sub_38F4(v7, "ISCC") )
{
std::allocator<char>::allocator(&v14, "ISCC", v8);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v24, "}", &v14);
v9 = sub_391E(v15);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v23, v9);
sub_2A5F(v16, v23, v24);
v10 = sub_38CA(v16);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator=(v21, v10);
sub_3704(v16);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v23);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v24);
std::allocator<char>::~allocator(&v14);
std::allocator<char>::allocator(&v14, v10, v11);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v23, "4", &v14);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(v22, v19);
sub_2A5F(v16, v22, v23);
v12 = sub_38CA(v16);
std::operator+<char>(v24, v21, v12);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator=(v21, v24);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v24);
sub_3704(v16);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v22);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v23);
std::allocator<char>::~allocator(&v14);
sub_2914(v21, v17);
sub_29C9(v24, v21, v18);
if ( (unsigned int)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::compare(
v24,
"rJFsLqVyFKZFEJvgerWvFpMkdmHBs5RX1ummCrv=") )
std::operator<<<std::char_traits<char>>(&std::cout, "Wrong!");
else
std::operator<<<std::char_traits<char>>(&std::cout, "Correct!");
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v24);
}
else
{
std::operator<<<std::char_traits<char>>(&std::cout, "head! head! head!");
}
sub_3704(v15);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v21);
}
else
{
std::operator<<<std::char_traits<char>>(&std::cout, "You don't have permission to acess the file!");
}
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v20);
sub_3636(v25);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v19);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v18);
return 0LL;
}逆向后得到的伪C代码,发现乱乱的
先打开string的的窗口检查一下
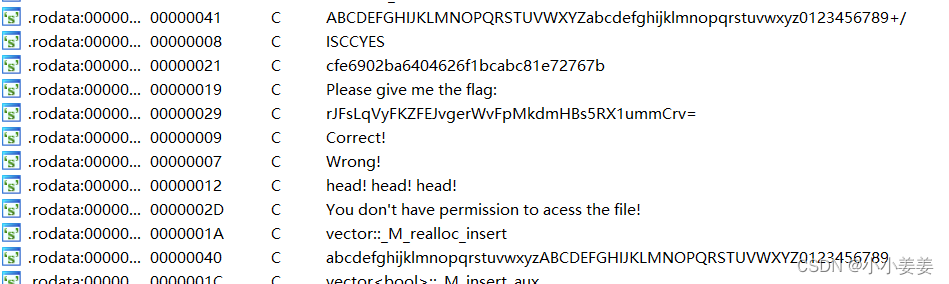
而且有一处
"rJFsLqVyFKZFEJvgerWvFpMkdmHBs5RX1ummCrv="
推测存在base64
从
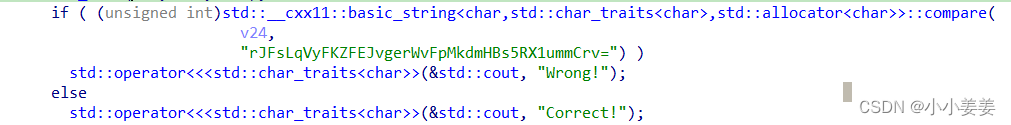
开始逆向分析
打开sub_29c9函数,v24为函数执行结果,也就是"rJFsLqVyFKZFEJvgerWvFpMkdmHBs5RX1ummCrv=",v18是上面的"ISCCKEY",v21是sub_2914的执行结果,那么逆向就是要推出v21
__int64 __fastcall sub_29C9(__int64 a1, __int64 a2, __int64 a3)
{
char v5[40]; // [rsp+20h] [rbp-40h] BYREF
unsigned __int64 v6; // [rsp+48h] [rbp-18h]
v6 = __readfsqword(0x28u);
sub_27C6(v5, a2);
sub_2569(a1, v5, a3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v5);
return a1;
}先把v21作为a2传入sub_27c6中
然后将执行结果和v18一起传入sub_2569
27c6和2569分别分析
__int64 __fastcall sub_27C6(__int64 a1, __int64 a2)
{
int v3; // [rsp+14h] [rbp-1Ch]
int v4; // [rsp+18h] [rbp-18h]
int i; // [rsp+1Ch] [rbp-14h]
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(a1);
v3 = 0;
v4 = -6;
for ( i = 0;
i < (unsigned __int64)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a2);
++i )
{
v3 = (v3 << 8)
+ *(char *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a2, i);
for ( v4 += 8; v4 >= 0; v4 -= 6 )
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::push_back(
a1,
(unsigned int)aAbcdefghijklmn[(v3 >> v4) & 0x3F]);
}
if ( v4 >= -5 )
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::push_back(
a1,
(unsigned int)aAbcdefghijklmn[(v3 << 8 >> (v4 + 8)) & 0x3F]);
while ( (std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a1) & 3) != 0 )
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::push_back(a1, 61LL);
return a1;
}可以推测出这是base64
看看2569
__int64 __fastcall sub_2569(__int64 a1, __int64 a2, __int64 a3)
{
__int64 v3; // rdx
char *v4; // rax
char *v6; // rax
int v7; // ebx
char *v8; // rax
unsigned __int64 v9; // rbx
unsigned __int64 v10; // rax
_BYTE *v11; // rbx
char v14; // [rsp+23h] [rbp-4Dh] BYREF
int i; // [rsp+24h] [rbp-4Ch]
int v16; // [rsp+28h] [rbp-48h]
int v17; // [rsp+2Ch] [rbp-44h]
char v18[40]; // [rsp+30h] [rbp-40h] BYREF
unsigned __int64 v19; // [rsp+58h] [rbp-18h]
v19 = __readfsqword(0x28u);
v16 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a2);
v17 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a3);
std::allocator<char>::allocator(&v14, a2, v3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(a1, v16, 120LL, &v14);
std::allocator<char>::~allocator(&v14);
sub_2447(v18, a2, a3);
for ( i = 0; i < v16; ++i )
{
v4 = (char *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a2, i);
if ( isalnum(*v4)
|| *(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a2, i) == 32 )
{
v6 = (char *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a2, i);
v7 = sub_23D9((unsigned int)*v6);
v8 = (char *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](v18, i);
v9 = (int)(v7 + sub_23D9((unsigned int)*v8));
v10 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(&unk_10280);
v11 = (_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](
&unk_10280,
v9 % v10);
}
else
{
v11 = (_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a2, i);
}
*(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, i) = *v11;
}
*(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, i) = 0;
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(v18);
return a1;
}sub_2447
__int64 __fastcall sub_2447(__int64 a1, __int64 a2, __int64 a3)
{
__int64 v3; // rdx
_BYTE *v4; // rbx
char v7; // [rsp+2Fh] [rbp-21h] BYREF
int v8; // [rsp+30h] [rbp-20h]
int v9; // [rsp+34h] [rbp-1Ch]
int v10; // [rsp+38h] [rbp-18h]
int v11; // [rsp+3Ch] [rbp-14h]
v10 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a2);
std::allocator<char>::allocator(&v7, a2, v3);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(a1, v10, 120LL, &v7);
std::allocator<char>::~allocator(&v7);
v11 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a3);
v8 = 0;
v9 = 0;
while ( v8 < v10 )
{
if ( v9 == v11 )
v9 = 0;
v4 = (_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a3, v9);
*(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, v8++) = *v4;
++v9;
}
*(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, v8) = 0;
return a1;
}发现这个函数将字符串"ISCCKEY"循环延长到与"rJFsLqVyFKZFEJvgerWvFpMkdmHBs5RX1ummCrv="长度一样
sub_23D9
__int64 __fastcall sub_23D9(char a1)
{
unsigned int i; // [rsp+1Ch] [rbp-14h]
for ( i = 0;
(int)i < (unsigned __int64)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(&unk_10280);
++i )
{
if ( a1 == *(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](
&unk_10280,
(int)i) )
return i;
}
return 0xFFFFFFFFLL;
}其中&unk_10280我们需要用交叉引用
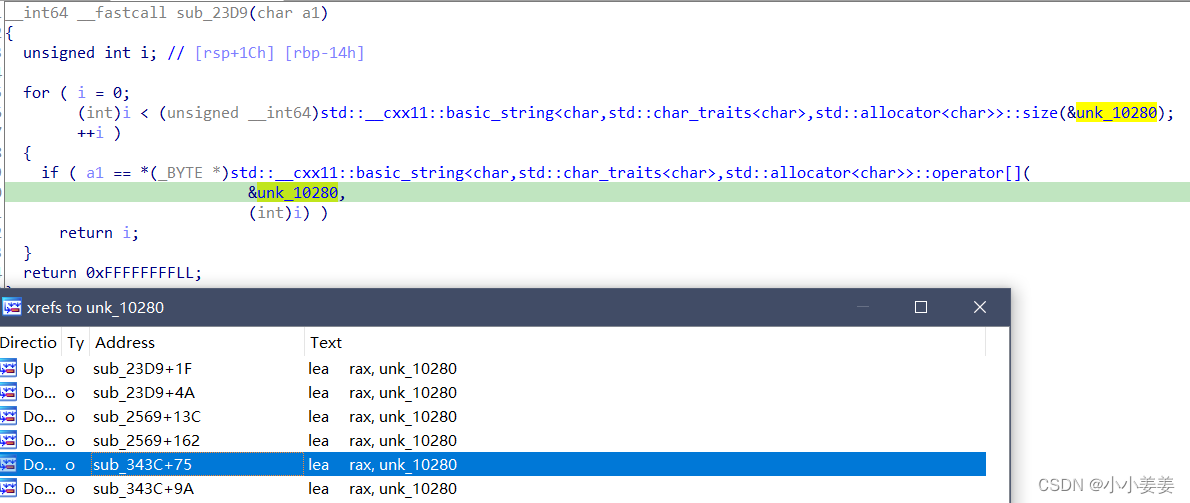
int __fastcall sub_343C(int a1, int a2)
{
__int64 v2; // rdx
int result; // eax
char v4[9]; // [rsp+1Fh] [rbp-11h] BYREF
if ( a1 == 1 && a2 == 0xFFFF )
{
std::ios_base::Init::Init((std::ios_base::Init *)&unk_102A0);
__cxa_atexit((void (__fastcall *)(void *))&std::ios_base::Init::~Init, &unk_102A0, &dso_handle);
std::allocator<char>::allocator(v4, &unk_102A0, v2);
std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(
&unk_10280,
"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 ",
v4);
std::allocator<char>::~allocator(v4);
result = __cxa_atexit(
(void (__fastcall *)(void *))&std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string,
&unk_10280,
&dso_handle);
}
return result;
}发现这里有个函数是把"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 "
赋值到&unk_10280
说明sub_23D9中
就是查找a1在
"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 "
中的位置,并返回下标
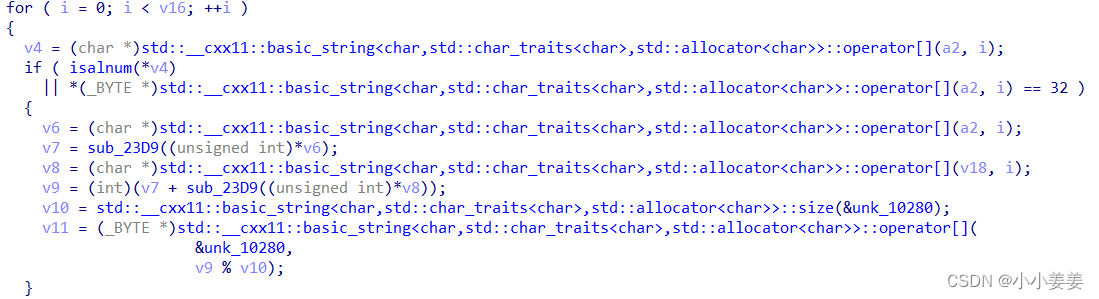
分析
其实是对base64加密后的的那个字符串和"ISCCKEY"那个字符串进行遍历
得到的两个字符分别在"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 "
中查找下标,并相加
得到的数字和strlen("abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 ")
取余
当做下标从&unk_10280里进行取值
赋给v24
再看2914
__int64 __fastcall sub_2914(__int64 a1, __int64 a2)
{
char v2; // bl
int v3; // er12
__int64 result; // rax
signed int i; // [rsp+18h] [rbp-18h]
signed int v6; // [rsp+1Ch] [rbp-14h]
v6 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::size(a1);
for ( i = 0; ; ++i )
{
result = (unsigned int)i;
if ( i >= v6 )
break;
v2 = *(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, i);
v3 = *(_DWORD *)(4LL * (i % 7) + a2);
*(_BYTE *)std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::operator[](a1, i) = v3 ^ v2;
}
return result;
}一个简单的取余和异或
编写脚本解密
import base64
a = "ISCCYES"
b = ''
c = "rJFsLqVyFKZFEJvgerWvFpMkdmHBs5RX1ummCrv="
d = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 '
f = ''
for i in range(len(c)):
b += a[i % len(a)]
print(b)
for i in range(len(c)-1):
f += d[(d.find(c[i]) - d.find(b[i]) + 63) % 63]
print(base64.b64decode(f))
f='Sguawub,Rkf37Ova.S37TVzowQOWN'
g=[1,2,3,4,5,6,7]
h=''
for i in range(len(f)):
h+=chr(ord(f[i])^(g[i%7]))
print(h)




















 932
932











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








