引言
无
together
附件有两个 公钥,pem 和 flag(base64编码) 文件
联想题目,容易猜想是 RSA 共模攻击
编写代码验证:
from Crypto.PublicKey import RSA
with open("pubkey1.pem", "r") as f:
key = RSA.import_key(f.read())
print(key.n)
print(key.e)
with open("pubkey2.pem", "r") as f:
key = RSA.import_key(f.read())
print(key.n)
print(key.e)
输出结果:
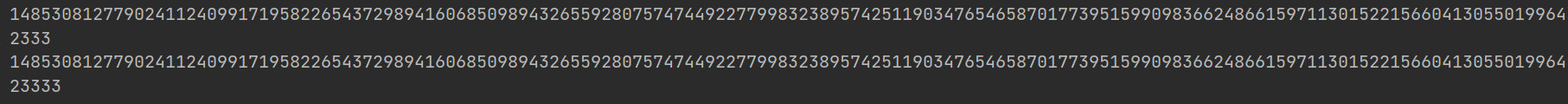
猜想成立
然后进行共模攻击
完整代码如下:
from Crypto.PublicKey import RSA
import base64
from Crypto.Util.number import *
import gmpy2
with open("pubkey1.pem", "r") as f:
key = RSA.import_key(f.read())
n1 = key.n
e1 = key.e
with open("pubkey2.pem", "r") as f:
key = RSA.import_key(f.read())
n2 = key.n
e2 = key.e
assert n1 == n2
n = n1
with open('myflag1', 'r') as f:
c1 = int(base64.b64decode(f.read()).hex(), 16)
print(c1)
with open('myflag2', 'r') as f:
c2 = int(base64.b64decode(f.read()).hex(), 16)
print(c2)
g, u, v = gmpy2.gcdext(e1, e2)
if u < 0:
u = -u
c1 = inverse(c1, n)
if v < 0:
v = -v
c2 = inverse(c2, n)
m = (pow(c1, u, n) * pow(c2, v, n)) % n
print(long_to_bytes(m))
结果为:flag{23re_SDxF_y78hu_5rFgS}
babyRSA
加密代码如下:
import sympy
import random
from gmpy2 import gcd, invert
from Crypto.Util.number import getPrime, isPrime, getRandomNBitInteger, bytes_to_long, long_to_bytes
from z3 import *
flag = b"MRCTF{xxxx}"
base = 65537
def gen_p():
P = [0 for i in range(17)]
P[0] = getPrime(128)
for i in range(1, 17):
P[i] = sympy.nextprime(P[i-1])
print("P_p :", P[9])
n = 1
for i in range(17):
n *= P[i]
p = getPrime(1024)
factor = pow(p, base, n)
print("P_factor :", factor)
return sympy.nextprime(p)
def gen_q():
sub_Q = getPrime(1024)
Q_1 = getPrime(1024)
Q_2 = getPrime(1024)
Q = sub_Q ** Q_2 % Q_1
print("Q_1: ", Q_1)
print("Q_2: ", Q_2)
print("sub_Q: ", sub_Q)
return sympy.nextprime(Q)
if __name__ == "__main__":
_E = base
_P = gen_p()
_Q = gen_q()
assert (gcd(_E, (_P - 1) * (_Q - 1)) == 1)
_M = bytes_to_long(flag)
_C = pow(_M, _E, _P * _Q)
print("Ciphertext = ", _C)
'''
P_p : 206027926847308612719677572554991143421
P_factor : 213671742765908980787116579976289600595864704574134469173111790965233629909513884704158446946409910475727584342641848597858942209151114627306286393390259700239698869487469080881267182803062488043469138252786381822646126962323295676431679988602406971858136496624861228526070581338082202663895710929460596143281673761666804565161435963957655012011051936180536581488499059517946308650135300428672486819645279969693519039407892941672784362868653243632727928279698588177694171797254644864554162848696210763681197279758130811723700154618280764123396312330032986093579531909363210692564988076206283296967165522152288770019720928264542910922693728918198338839
Q_1: 103766439849465588084625049495793857634556517064563488433148224524638105971161051763127718438062862548184814747601299494052813662851459740127499557785398714481909461631996020048315790167967699932967974484481209879664173009585231469785141628982021847883945871201430155071257803163523612863113967495969578605521
Q_2: 151010734276916939790591461278981486442548035032350797306496105136358723586953123484087860176438629843688462671681777513652947555325607414858514566053513243083627810686084890261120641161987614435114887565491866120507844566210561620503961205851409386041194326728437073995372322433035153519757017396063066469743
sub_Q: 168992529793593315757895995101430241994953638330919314800130536809801824971112039572562389449584350643924391984800978193707795909956472992631004290479273525116959461856227262232600089176950810729475058260332177626961286009876630340945093629959302803189668904123890991069113826241497783666995751391361028949651
Ciphertext = 1709187240516367141460862187749451047644094885791761673574674330840842792189795049968394122216854491757922647656430908587059997070488674220330847871811836724541907666983042376216411561826640060734307013458794925025684062804589439843027290282034999617915124231838524593607080377300985152179828199569474241678651559771763395596697140206072537688129790126472053987391538280007082203006348029125729650207661362371936196789562658458778312533505938858959644541233578654340925901963957980047639114170033936570060250438906130591377904182111622236567507022711176457301476543461600524993045300728432815672077399879668276471832
'''
其实他原附件给的代码里面定义的 GCD() 函数根本没有用到,我把它删了
分析代码,p 和 q 分别由 gen_p() 和 gen_q() 两个自定义函数获取
其中 q 很容易求,而且把需要用到的数据都给了
需要注意的就是 用原代码的 sympy.nextprime(sub_Q ** Q_2 % Q_1) 求 q 会非常慢,我们用 sympy.nextprime(pow(sub_Q, Q_2, Q_1)) 的方式求解
代码如下:
import sympy
# 求 q
Q_1 = 103766439849465588084625049495793857634556517064563488433148224524638105971161051763127718438062862548184814747601299494052813662851459740127499557785398714481909461631996020048315790167967699932967974484481209879664173009585231469785141628982021847883945871201430155071257803163523612863113967495969578605521
Q_2 = 151010734276916939790591461278981486442548035032350797306496105136358723586953123484087860176438629843688462671681777513652947555325607414858514566053513243083627810686084890261120641161987614435114887565491866120507844566210561620503961205851409386041194326728437073995372322433035153519757017396063066469743
sub_Q = 168992529793593315757895995101430241994953638330919314800130536809801824971112039572562389449584350643924391984800978193707795909956472992631004290479273525116959461856227262232600089176950810729475058260332177626961286009876630340945093629959302803189668904123890991069113826241497783666995751391361028949651
q = sympy.nextprime(pow(sub_Q, Q_2, Q_1))
然后求 p
发现 gen_p() 函数和 RSA 加密算法很相似,只不过 n 是 17 个素数相乘
告诉我们 P[9] 容易求得其他 16 个相邻的素数
最后类似于 RSA 解密即可
代码如下:
import sympy
from Crypto.Util.number import *
# 求 p
P_p = 206027926847308612719677572554991143421
P_factor = 213671742765908980787116579976289600595864704574134469173111790965233629909513884704158446946409910475727584342641848597858942209151114627306286393390259700239698869487469080881267182803062488043469138252786381822646126962323295676431679988602406971858136496624861228526070581338082202663895710929460596143281673761666804565161435963957655012011051936180536581488499059517946308650135300428672486819645279969693519039407892941672784362868653243632727928279698588177694171797254644864554162848696210763681197279758130811723700154618280764123396312330032986093579531909363210692564988076206283296967165522152288770019720928264542910922693728918198338839
list_P = [P_p]
P = P_p
for i in range(9):
P = sympy.prevprime(P)
list_P.append(P)
P = P_p
for i in range(7):
P = sympy.nextprime(P)
list_P.append(P)
phi_p = 1
n_p = 1
for i in range(len(list_P)):
n_p *= list_P[i]
phi_p *= (list_P[i]-1)
d_p = inverse(e, phi_p)
p = sympy.nextprime(pow(P_factor, d_p, n_p))
最后就是最基础的 RSA 解密算法了
完整代码如下:
import sympy
from Crypto.Util.number import *
e = 65537
c = 1709187240516367141460862187749451047644094885791761673574674330840842792189795049968394122216854491757922647656430908587059997070488674220330847871811836724541907666983042376216411561826640060734307013458794925025684062804589439843027290282034999617915124231838524593607080377300985152179828199569474241678651559771763395596697140206072537688129790126472053987391538280007082203006348029125729650207661362371936196789562658458778312533505938858959644541233578654340925901963957980047639114170033936570060250438906130591377904182111622236567507022711176457301476543461600524993045300728432815672077399879668276471832
# 求 q
Q_1 = 103766439849465588084625049495793857634556517064563488433148224524638105971161051763127718438062862548184814747601299494052813662851459740127499557785398714481909461631996020048315790167967699932967974484481209879664173009585231469785141628982021847883945871201430155071257803163523612863113967495969578605521
Q_2 = 151010734276916939790591461278981486442548035032350797306496105136358723586953123484087860176438629843688462671681777513652947555325607414858514566053513243083627810686084890261120641161987614435114887565491866120507844566210561620503961205851409386041194326728437073995372322433035153519757017396063066469743
sub_Q = 168992529793593315757895995101430241994953638330919314800130536809801824971112039572562389449584350643924391984800978193707795909956472992631004290479273525116959461856227262232600089176950810729475058260332177626961286009876630340945093629959302803189668904123890991069113826241497783666995751391361028949651
q = sympy.nextprime(pow(sub_Q, Q_2, Q_1))
# 求 p
P_p = 206027926847308612719677572554991143421
P_factor = 213671742765908980787116579976289600595864704574134469173111790965233629909513884704158446946409910475727584342641848597858942209151114627306286393390259700239698869487469080881267182803062488043469138252786381822646126962323295676431679988602406971858136496624861228526070581338082202663895710929460596143281673761666804565161435963957655012011051936180536581488499059517946308650135300428672486819645279969693519039407892941672784362868653243632727928279698588177694171797254644864554162848696210763681197279758130811723700154618280764123396312330032986093579531909363210692564988076206283296967165522152288770019720928264542910922693728918198338839
list_P = [P_p]
P = P_p
for i in range(9):
P = sympy.prevprime(P)
list_P.append(P)
P = P_p
for i in range(7):
P = sympy.nextprime(P)
list_P.append(P)
phi_p = 1
n_p = 1
for i in range(len(list_P)):
n_p *= list_P[i]
phi_p *= (list_P[i]-1)
d_p = inverse(e, phi_p)
p = sympy.nextprime(pow(P_factor, d_p, n_p))
# 求 c
n = p*q
phi = (p-1)*(q-1)
d = inverse(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
结果:MRCTF{sti11_@_b@by_qu3st10n}
结语
希望继续坚持






















 1443
1443











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








