openvpn安装配置
1、服务端安装
[root@openvpn ~]# curl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.aliyun.com/repo/Centos-7.repo && yum install epel-release -y [root@openvpn ~]# yum install -y openvpn [root@openvpn 3]# yum install -y easy-rsa && whereis easy-rsa && cd /usr/share/easy-rsa/3/ [root@openvpn 3]# cat vars export KEY_COUNTRY="CN" export KEY_PROVINCE="TianJin" export KEY_CITY="JinNan" export KEY_ORG="li" export KEY_EMAIL="li001157@163.com" export KEY_OU="My OpenVPN" [root@openvpn 3]# ./easyrsa init-pki #生成存放证书文件 [root@openvpn 3]# ./easyrsa build-ca Note: using Easy-RSA configuration from: /usr/share/easy-rsa/3.0.8/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Enter New CA Key Passphrase: 第一次根证书密码 Re-Enter New CA Key Passphrase: 第二次根证书密码 Generating RSA private key, 2048 bit long modulus ...............................+++ .................................+++ e is 65537 (0x10001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]:li 名字随意 CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /usr/share/easy-rsa/3/pki/ca.crt [root@openvpn 3]# ./easyrsa gen-req server nopass Note: using Easy-RSA configuration from: /usr/share/easy-rsa/3.0.8/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key ......................................+++ .................+++ writing new private key to '/usr/share/easy-rsa/3/pki/easy-rsa-4488.vN18r1/tmp.dfrp6F' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [server]:zhou server name 随意 Keypair and certificate request completed. Your files are: req: /usr/share/easy-rsa/3/pki/reqs/server.req key: /usr/share/easy-rsa/3/pki/private/server.key [root@openvpn 3]# ./easyrsa sign server server 签发server证书,属入yes 和 密码 Note: using Easy-RSA configuration from: /usr/share/easy-rsa/3.0.8/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a server certificate for 825 days: subject= commonName = zhou Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes Using configuration from /usr/share/easy-rsa/3/pki/easy-rsa-4560.oTwrQj/tmp.AJ8ykd Enter pass phrase for /usr/share/easy-rsa/3/pki/private/ca.key: Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'zhou' Certificate is to be certified until Oct 11 12:03:17 2025 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /usr/share/easy-rsa/3/pki/issued/server.crt [root@openvpn 3]# ./easyrsa gen-req client 生成客户端证书 Note: using Easy-RSA configuration from: /usr/share/easy-rsa/3.0.8/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 Generating a 2048 bit RSA private key ........................................................+++ ...........................................................+++ writing new private key to '/usr/share/easy-rsa/3/pki/easy-rsa-4703.3ovrws/tmp.49EtQf' Enter PEM pass phrase: 私钥密码 Verifying - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [client]:win10 #随意 Keypair and certificate request completed. Your files are: req: /usr/share/easy-rsa/3/pki/reqs/client.req key: /usr/share/easy-rsa/3/pki/private/client.key [root@openvpn 3]# ./easyrsa sign client client #yes 和根证书密码 签名client证书 Note: using Easy-RSA configuration from: /usr/share/easy-rsa/3.0.8/vars Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a client certificate for 825 days: subject= commonName = win10 Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes Using configuration from /usr/share/easy-rsa/3/pki/easy-rsa-4901.4iD2NE/tmp.Lw30Zt Enter pass phrase for /usr/share/easy-rsa/3/pki/private/ca.key: Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'win10' Certificate is to be certified until Oct 11 12:08:16 2025 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /usr/share/easy-rsa/3/pki/issued/client.crt [root@openvpn 3]# ./easyrsa gen-dh #创建Diffie-Hellman文件,秘钥交换时的Diffie-Hellman算法,确保key穿越不安全网络的命令,这里可能需要点时间才能执行完
2、服务端配置文件
cp -r /usr/share/easy-rsa/3/pki/ca.crt /etc/openvpn/ cp -r /usr/share/easy-rsa/3/pki/issued/server.crt /etc/openvpn/ cp -r /usr/share/easy-rsa/3/pki/private/server.key /etc/openvpn/ cp -r /usr/share/easy-rsa/3/pki/dh.pem /etc/openvpn/ port 1194 #服务端口 proto udp #协议(这里也可以采用tcp协议,相比于upd,tcp更加可靠,但是udp访问更快) dev tun #采用路由隧道模式tun ca ca.crt #ca证书文件位置(此处为ca.crt文件存放位置,如果不与server.conf文件在同一路径下,要标出文件位置),加载目录 cert server.crt #服务端公钥文件位置,加载目录 key server.key #服务端私钥文件位置,加载目录 dh dh.pem #秘钥交换交换证书文件位置,加载目录 server 10.0.2.0 255.255.255.0 #给客户端分配地址池,这里要区分openvpn服务器的其他网段 push "route 172.16.2.0 255.255.255.0" #允许客户端访问内网172.16.2.0网段,推送路由信息 ifconfig-pool-persist ipp.txt #地址池记录文件位置 keepalive 10 120 #存活时间,表示为10秒ping一次,120 如未收到响应则视为断线,默认配置即可 tls-auth ta.key 0 # This file is secret #拒绝dos攻击,提高VPN安全性,这里要在/etc/openvpn 下生成该文件,下文会生成该文件 cipher AES-256-GCM #这里是该服务使用的加密方式;默认为CBC,这里需要修改成GCM,v2.4版本以后客户端需要修改 max-clients 100 #最多允许100个客户端连接,默认配置即可 status openvpn-status.log #日志文件位置 verb 3 #指定日志文件的记录详细级别,可选0-9,等级越高日志内容越详细 client-to-client #客户端与客户端之间支持通信 log /var/log/openvpn.log #openvpn日志文件位置 persist-key #通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys。 persist-tun #检测超时后,重新启动VPN,一直保持tun是linkup的。否则网络会先linkdown然后再linkup echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf #开启路由转发功能 sysctl -p #激活内核中新增的配置文件信息使路由转发功能生效 [root@openvpn openvpn]# openvpn --genkey --secret ta.key #创建配置文件中抵御dos攻击的文件 openvpn --daemon --config server.conf #开启openvpn服务,--daemon参数表示后台运行,不加该参数前台会被占用,需要开新窗口 iptables -t nat -A POSTROUTING -s 10.0.2.0/24 -j MASQUERADE #实现内网转发
3、client配置
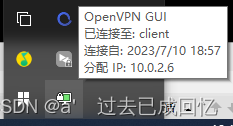
client #指定当前VPN是客户端 dev tun #使用tun隧道传输协议 proto udp #使用udp协议传输数据 remote frp_ip 1194 #openvpn服务器IP地址端口号 resolv-retry infinite #断线自动重新连接,在网络不稳定的情况下非常有用 nobind #不绑定本地特定的端口号 ca ca.crt #指定CA证书的文件路径 cert client.crt #指定当前客户端的证书文件路径 key client.key #指定当前客户端的私钥文件路径 verb 3 #指定日志文件的记录详细级别,0-9,等级越高日志内容越详细 persist-key #通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys persist-tun #检测超时后,重新启动VPN,一直保持tun是linkup的。否则网络会先linkdown然后再linkup tls-auth ta.key 1 将client.conf 生成转化为client.ovpn #将一下文件但如到win ***/openvpn/config文件下启动即可vpn即可,还要输入私钥密码。 cp -r /usr/share/easy-rsa/3/pki/private/client.key /etc/openvpn/client/ cp -r /usr/share/easy-rsa/3/pki/issued/client.crt /etc/openvpn/client/ cp -r /usr/share/easy-rsa/3/pki/ca.crt /etc/openvpn/client/ cp -r /etc/openvpn/ta.key /etc/openvpn/client/
4、frp实现
server端 [common] bind_port = 7000 dashboard_user = admin dashboard_pwd = admin dashboard_port = 8000 token = abc123 client端 [common] server_addr = ***** server_port = 7000 admin_addr = 127.0.0.1 log_file = ./frpc.log log_level = info token = abc123 # 通过 ssh 访问内网机器 # ssh -oPort=6000 用户名@x.x.x.x [ssh] type = tcp local_ip = 127.0.0.1 local_port = 22 remote_port = 6000 # 范围端口映射 [range:tcp] type = udp local_ip = 127.0.0.1 local_port = 1194 remote_port = 1194

qq: 870677314






















 1210
1210











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










