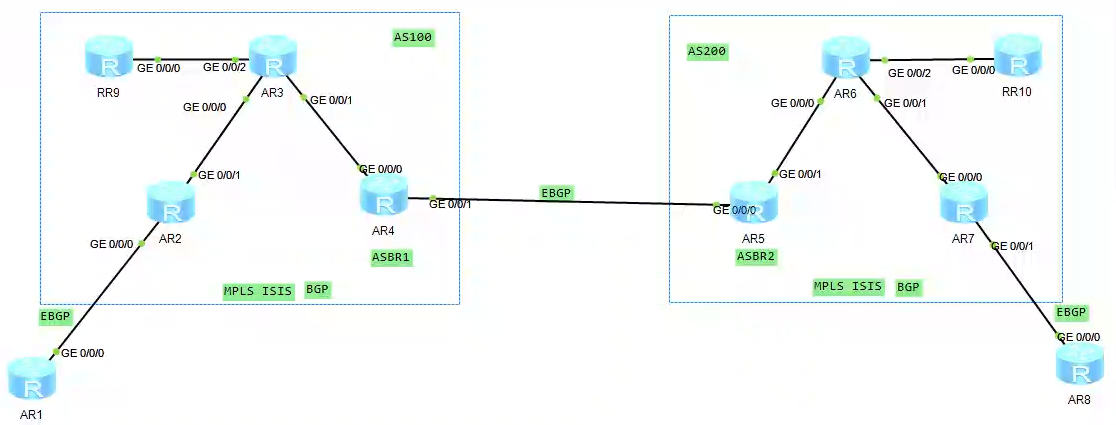
用OptionC的第一种方式说明:(在OptionC的第一种方式配置基础上做出一些修改)
在AS100中加入AR9(即反射器RR),mpls和isis底层配置需要补上。
AR2和AR4之间的邻居断开,让AR9分别和AR2、AR4建立公网邻居。(label-route-capability这个能力同样需要开启)
在AS200中加入AR10,配置参考AS100。
此时2、9、4、5、10、7构成了一条公网路由 。
此时AR9与AR10可以建立私网邻居了,同时AR9与AR2、AR10与AR7也建立私网邻居 .
此时2、9、10、7构成了一条私网路由。

红色笔迹为公网路由,黄色笔迹为私网路由。
在私网路由线路中,配置next-hop-invariable ,不改变路由的下一跳,达到优化路由的目的。
具体配置如下:
[AR2]DIS CU
[V200R003C00]
#
sysname AR2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
ip vpn-instance 2
ipv4-family
route-distinguisher 2:2
vpn-target 1:8 export-extcommunity
vpn-target 8:1 import-extcommunity
#
mpls lsr-id 2.2.2.2
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 1
is-level level-2
network-entity 49.0002.0000.0000.0002.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip binding vpn-instance 2
ip address 12.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 23.1.1.2 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
isis enable 1
#
bgp 100
router-id 2.2.2.2
undo default ipv4-unicast
peer 9.9.9.9 as-number 100
peer 9.9.9.9 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 9.9.9.9 enable
peer 9.9.9.9 next-hop-local
peer 9.9.9.9 label-route-capability
#
ipv4-family vpnv4
policy vpn-target
peer 9.9.9.9 enable
peer 9.9.9.9 next-hop-invariable
#
ipv4-family vpn-instance 2
peer 12.1.1.1 as-number 1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return<AR3>dis cu
[V200R003C00]
#
sysname AR3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
mpls lsr-id 3.3.3.3
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 1
is-level level-2
network-entity 49.0003.0000.0000.0003.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
ip address 34.1.1.3 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface GigabitEthernet0/0/2
ip address 39.1.1.3 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface NULL0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
isis enable 1
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR4>dis cu
[V200R003C00]
#
sysname AR4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
mpls lsr-id 4.4.4.4
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 1
is-level level-2
network-entity 49.0004.0000.0000.0004.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 34.1.1.4 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
ip address 45.1.1.4 255.255.255.0
mpls
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
isis enable 1
#
bgp 100
router-id 4.4.4.4
undo default ipv4-unicast
peer 9.9.9.9 as-number 100
peer 9.9.9.9 connect-interface LoopBack0
peer 45.1.1.5 as-number 200
#
ipv4-family unicast
undo synchronization
network 2.2.2.2 255.255.255.255
network 9.9.9.9 255.255.255.255
peer 9.9.9.9 enable
peer 9.9.9.9 route-policy p2 export
peer 9.9.9.9 next-hop-local
peer 9.9.9.9 label-route-capability
peer 45.1.1.5 enable
peer 45.1.1.5 route-policy p1 export
peer 45.1.1.5 label-route-capability
#
ipv4-family vpnv4
undo policy vpn-target
#
route-policy p1 permit node 10
apply mpls-label
#
route-policy p2 permit node 10
if-match mpls-label
apply mpls-label
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<RR9>dis cu
[V200R003C00]
#
sysname RR9
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
mpls lsr-id 9.9.9.9
mpls
#
mpls ldp
#
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
isis 1
is-level level-2
network-entity 49.0009.0000.0000.0009.00
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 39.1.1.9 255.255.255.0
isis enable 1
mpls
mpls ldp
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 9.9.9.9 255.255.255.255
isis enable 1
#
bgp 100
router-id 9.9.9.9
undo default ipv4-unicast
peer 2.2.2.2 as-number 100
peer 2.2.2.2 connect-interface LoopBack0
peer 4.4.4.4 as-number 100
peer 4.4.4.4 connect-interface LoopBack0
peer 10.10.10.10 as-number 200
peer 10.10.10.10 ebgp-max-hop 255
peer 10.10.10.10 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 2.2.2.2 enable
peer 2.2.2.2 reflect-client
peer 2.2.2.2 label-route-capability
peer 4.4.4.4 enable
peer 4.4.4.4 reflect-client
peer 4.4.4.4 label-route-capability
undo peer 10.10.10.10 enable
#
ipv4-family vpnv4
undo policy vpn-target
peer 2.2.2.2 enable
peer 2.2.2.2 next-hop-invariable
peer 10.10.10.10 enable
peer 10.10.10.10 next-hop-invariable
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








