下载附件解压后看到easy_rsa.py文件:
from Crypto.Util.number import *
from flag import flag
import gmpy2
def gen_prime(nbits, gamma):
g = getPrime(int(nbits * gamma))
alpha = 0.5 - gamma
while True:
a = getRandomNBitInteger(int(alpha * nbits))
p = 2 * g * a + 1
if isPrime(p):
b = getRandomNBitInteger(int(alpha * nbits))
q = 2 * g * b + 1
h = 2 * g * a * b + a + b
while not isPrime(q) or isPrime(h) or gmpy2.gcd(a, b) != 1:
b = getRandomNBitInteger(int(alpha * nbits))
q = 2 * g * b + 1
return p, q
def encrypt(nbits, gamma):
p, q = gen_prime(nbits, gamma)
n = p * q
e = getPrime(16)
while gmpy2.gcd(e, gmpy2.lcm(p-1,q-1)) != 1:
e = getPrime(16)
m = bytes_to_long(flag)
c = pow(m, e, n)
return n, e, c
n, e, c = encrypt(1024, 0.48)
print 'n =', n
print 'e =', e
print 'c =', c
# n = 84236796025318186855187782611491334781897277899439717384242559751095347166978304126358295609924321812851255222430530001043539925782811895605398187299748256080526691975084042025794113521587064616352833904856626744098904922117855866813505228134381046907659080078950018430266048447119221001098505107823645953039
# e = 58337
# c = 13646200911032594651110040891135783560995665642049282201695300382255436792102048169200570930229947213493204600006876822744757042959653203573780257603577712302687497959686258542388622714078571068849217323703865310256200818493894194213812410547780002879351619924848073893321472704218227047519748394961963394668代码大致意思如下:
定义生成大素数的函数gen_prime
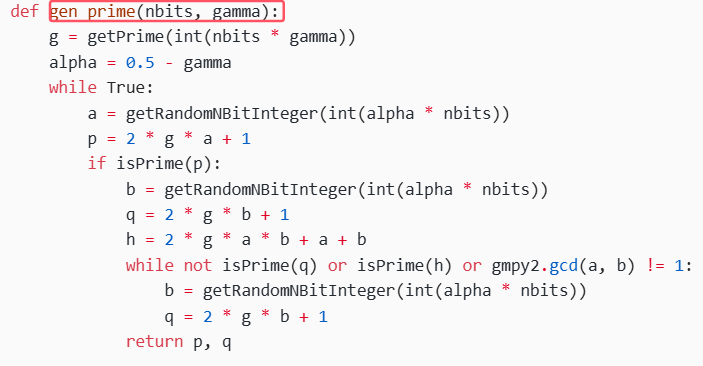
先生成大素数 g,然后生成随机数a,b,计算p = 2 * g * a + 1和q = 2 * g * b + 1,接着检查 q 是否为素数,且 p 和 q 的乘积的因数 h 不是素数,同时 a 和 b 互质,这样生成的 p 和 q 用于构建RSA密钥对
定义加密函数encrypt
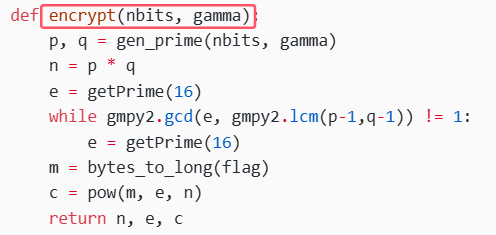
生成的 p 和 q 来计算 n = p * q,并生成一个16位的大素数 e 作为公钥的指数。然后将 flag 字符串转换为大整数 m,使用模幂运算计算密文 c
调用加密函数encrypt
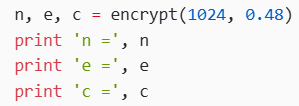
生成密钥对,并计算密文 c,参数 1024 表示密钥对的位数,0.48 是生成素数时的随机性调整参数
用easy_rsa0.py脚本进行解密:
from Crypto.Util.number import *
import gmpy2
def f(x, n):
return (pow(x, n - 1, n) + 3) % n
def rho(n):
i = 1
while True:
a = getRandomRange(2, n)
b = f(a, n)
j = 1
while True:
p = GCD(abs(a - b), n)
print('{} in {} circle'.format(j, i))
if p == n:
break
elif p > 1:
return (p, n // p)
else:
a = f(a, n)
b = f(f(b, n), n)
j += 1
i += 1
n = 84236796025318186855187782611491334781897277899439717384242559751095347166978304126358295609924321812851255222430530001043539925782811895605398187299748256080526691975084042025794113521587064616352833904856626744098904922117855866813505228134381046907659080078950018430266048447119221001098505107823645953039
e = 58337
c = 13646200911032594651110040891135783560995665642049282201695300382255436792102048169200570930229947213493204600006876822744757042959653203573780257603577712302687497959686258542388622714078571068849217323703865310256200818493894194213812410547780002879351619924848073893321472704218227047519748394961963394668
p, q = rho(n)
d = gmpy2.invert(e, (p-1)*(q-1))
m = pow(c, d, n)
print(bytes.fromhex(hex(m)[2:]))

变成NSSCTF{}的格式:
NSSCTF{0a8c2220-4c1b-32c8-e8c1-adf92ec7678b}

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








