详细描述:
远端WWW服务支持TRACE请求。RFC 2616介绍了TRACE请求,该请求典型地用于测试HTTP协议实现。攻击者利用TRACE请求,结合其它浏览器端漏洞,有可能进行跨站脚本攻击,获取敏感信息,比如cookie中的认证信息,这些敏感信息将被用于其它类型的攻击。
解决办法:
管理员应禁用WWW服务对TRACE请求的支持。
验证方法:
curl -v -X TRACE -I localhost:8081
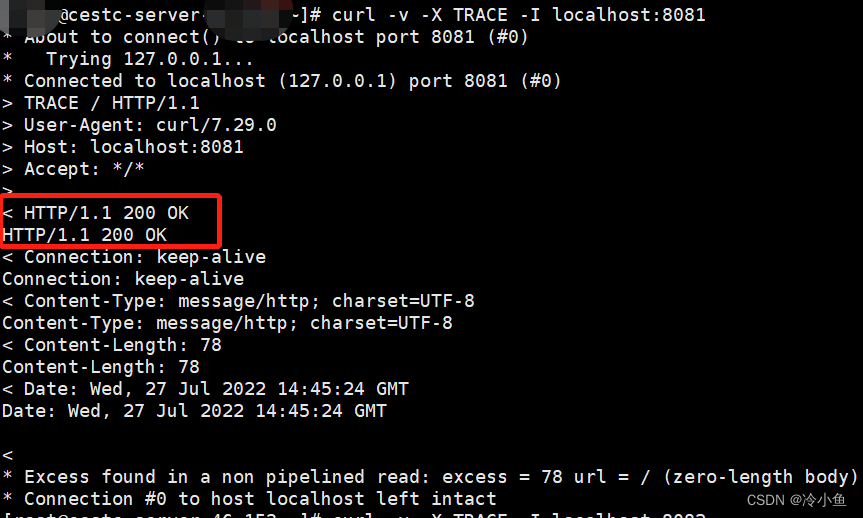
由于系统是Spring Boot 架构,因此加入配置类禁用 TRACE 请求。
package com.xxx.config;
import com.google.gson.Gson;
import lombok.extern.slf4j.Slf4j;
import org.apache.http.HttpStatus;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.context.WebApplicationContext;
import org.springframework.web.filter.OncePerRequestFilter;
import org.springframework.web.method.HandlerMethod;
import org.springframework.web.servlet.mvc.method.RequestMappingInfo;
import org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerMapping;
import javax.servlet.FilterChain;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
import java.util.ArrayList;
import java.util.List;
import java.util.Map;
import java.util.Set;
@Slf4j
@Configuration
public class SecurityFilterProxy extends OncePerRequestFilter {
@Value("${report.securityFilter:true}")
private boolean securityFilter;
@Autowired
WebApplicationContext applicationContext;
private static List<String> urlList=new ArrayList<>();
@Value("${access.control.notAllow.methods:trace}")
private String NOT_ALLOW_METHODS;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response,
FilterChain filterChain) throws ServletException, IOException {
String requestUrl = request.getServletPath();
log.info(requestUrl + "=requestUrl");
if(securityFilter) {
if((","+NOT_ALLOW_METHODS+",").indexOf(","+request.getMethod().toLowerCase()+",")>-1){
response.setStatus(HttpServletResponse.SC_METHOD_NOT_ALLOWED);
return ;
}
}
super.doFilter(request, response, filterChain);
return;
}
}
再次验证:


























 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










