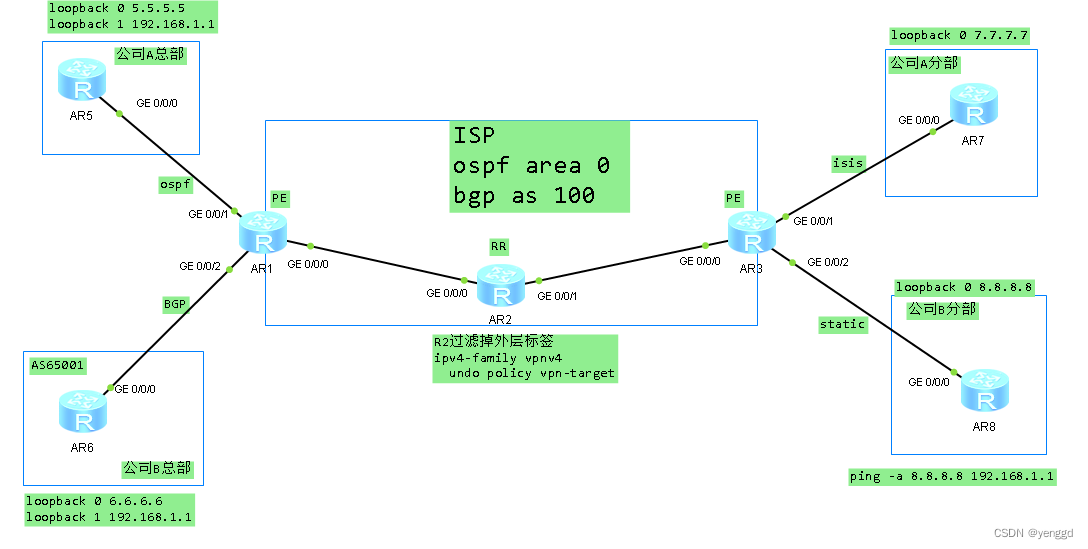
通信原理:
例:公司A总部到公司A分部:
1、R1把与R5建立ospf实例路由邻居:
ip vpn-instance vpna
ipv4-family
route-distinguisher 1:1
vpn-target 100:100 export-extcommunity
vpn-target 100:100 import-extcommunity
interface GigabitEthernet0/0/1
ip binding vpn-instance vpna
ip address 15.1.1.1 255.255.255.0
ospf 2 vpn-instance vpna
area 0.0.0.0
network 15.1.1.1 0.0.0.0
2、R1将收到的路由R5学到的ospf路由引入到vpn实例BGP表中去:
ipv4-family vpn-instance vpna
import-route ospf 2
注意:如果pe和ce是建立的ebgp邻居,那就不用导入这个动作了,直接在bgp的vpn实例中中直接建立邻居就可以了,而且next-hop local也不用,R1的vpnv4路由在传给R3时会自动修改下一调:
ipv4-family vpn-instance vpna
peer xxx as 200
3、bgp中的vpn实例路由会自动导入到bgp中的vpnv4路由表中去
4、配置bgp设置:
R1和R3分别与R2建立Ibgp邻居及vpnv4邻居,R2为普通bgp和vpnv4的RR路由反射器
注意:R2上面没有建立vpn-instance实例,所以默认R2的bgp里的vpnv4 会过滤掉vpnv4传递过来的路由,要把那个过滤功能关掉:undo policy vpn-traget
ipv4-family vpnv4
policy vpn-target
peer 2.2.2.2 enable
5、然后通过bgp vpnv4路由把vpnv4路由传给R3的vpnv4路由表中去
6、R3再把vpnv4路由表经根据RT规则进行过滤后导入到bgp vpn实例路由表中去
ip vpn-instance vpna
ipv4-family
route-distinguisher 1:1
vpn-target 100:100 export-extcommunity
vpn-target 100:100 import-extcommunity
7、最后导入到isis实例路由中去,AR7就学到了
isis 1 vpn-instance vpna
network-entity 49.0001.0000.0000.0003.00
import-route bgp
8、回包原理相同就省略了。。。。。。
注意:总部和分公司两个站点如果用ospf两边一定要用相同的区域,不然会因为ospf防环原则会出现问题,ISP如果igp用ospf就会看成一个opsf骨干网,两边如果用不同的区域那就会因为ospf算法出现问题,再者包括如果各分支下面再加其它区域的ospf,肯定会出问题。
r1:
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
ip vpn-instance vpna
ipv4-family
route-distinguisher 1:1
vpn-target 100:100 export-extcommunity
vpn-target 100:100 import-extcommunity
ip vpn-instance vpnb
ipv4-family
route-distinguisher 2:2
vpn-target 200:200 export-extcommunity
vpn-target 200:200 import-extcommunity
mpls lsr-id 1.1.1.1
mpls
mpls ldp
interface GigabitEthernet0/0/0
ip address 12.1.1.1 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/1
ip binding vpn-instance vpna
ip address 15.1.1.1 255.255.255.0
interface GigabitEthernet0/0/2
ip binding vpn-instance vpnb
ip address 16.1.1.1 255.255.255.0
interface NULL0
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
bgp 100
peer 2.2.2.2 as-number 100
peer 2.2.2.2 connect-interface LoopBack0
ipv4-family unicast
undo synchronization
peer 2.2.2.2 enable
ipv4-family vpnv4
policy vpn-target
peer 2.2.2.2 enable
ipv4-family vpn-instance vpna
import-route ospf 2
ipv4-family vpn-instance vpnb
peer 16.1.1.6 as-number 65001
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255
ospf 2 vpn-instance vpna
import-route bgp
area 0.0.0.0
network 15.1.1.1 0.0.0.0
R2:
[Huawei]dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
mpls lsr-id 2.2.2.2
mpls
mpls ldp
interface GigabitEthernet0/0/0
ip address 12.1.1.2 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/1
ip address 23.1.1.2 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
bgp 100
peer 1.1.1.1 as-number 100
peer 1.1.1.1 connect-interface LoopBack0
peer 3.3.3.3 as-number 100
peer 3.3.3.3 connect-interface LoopBack0
ipv4-family unicast
undo synchronization
peer 1.1.1.1 enable
peer 1.1.1.1 reflect-client
peer 3.3.3.3 enable
peer 3.3.3.3 reflect-client
ipv4-family vpnv4
undo policy vpn-target
peer 1.1.1.1 enable
peer 1.1.1.1 reflect-client
peer 3.3.3.3 enable
peer 3.3.3.3 reflect-client
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255
R3:
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
ip vpn-instance vpna
ipv4-family
route-distinguisher 1:1
vpn-target 100:100 export-extcommunity
vpn-target 100:100 import-extcommunity
ip vpn-instance vpnb
ipv4-family
route-distinguisher 2:2
vpn-target 200:200 export-extcommunity
vpn-target 200:200 import-extcommunity
mpls lsr-id 3.3.3.3
mpls
mpls ldp
isis 1 vpn-instance vpna
network-entity 49.0001.0000.0000.0003.00
import-route bgp
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/1
ip binding vpn-instance vpna
ip address 37.1.1.3 255.255.255.0
isis enable 1
interface GigabitEthernet0/0/2
ip binding vpn-instance vpnb
ip address 38.1.1.3 255.255.255.0
interface NULL0
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
bgp 100
peer 2.2.2.2 as-number 100
peer 2.2.2.2 connect-interface LoopBack0
ipv4-family unicast
undo synchronization
peer 2.2.2.2 enable
ipv4-family vpnv4
policy vpn-target
peer 2.2.2.2 enable
ipv4-family vpn-instance vpna
import-route isis 1
ipv4-family vpn-instance vpnb
import-route static
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255
ip route-static vpn-instance vpnb 8.8.8.8 255.255.255.255 38.1.1.8
R5:
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
set cpu-usage threshold 80 restore 75
interface GigabitEthernet0/0/0
ip address 15.1.1.5 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
interface LoopBack1
ip address 192.168.1.1 255.255.255.0
ospf enable 1 area 0.0.0.0
ospf 1
area 0.0.0.0
network 5.5.5.5 0.0.0.0
network 15.1.1.5 0.0.0.0
R6:
dis cu
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
set cpu-usage threshold 80 restore 75
interface GigabitEthernet0/0/0
ip address 16.1.1.6 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
interface LoopBack1
ip address 192.168.1.1 255.255.255.0
bgp 65001
peer 16.1.1.1 as-number 100
ipv4-family unicast
undo synchronization
network 6.6.6.6 255.255.255.255
network 192.168.1.0
peer 16.1.1.1 enable
R7:
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
set cpu-usage threshold 80 restore 75
isis 1
network-entity 49.0001.0000.0000.0007.00
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 37.1.1.7 255.255.255.0
isis enable 1
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack0
ip address 7.7.7.7 255.255.255.255
isis enable 1
R8:
dis cu
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
set cpu-usage threshold 80 restore 75
interface GigabitEthernet0/0/0
ip address 38.1.1.8 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack0
ip address 8.8.8.8 255.255.255.255
ip route-static 0.0.0.0 0.0.0.0 38.1.1.3
























 383
383











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










