实验拓扑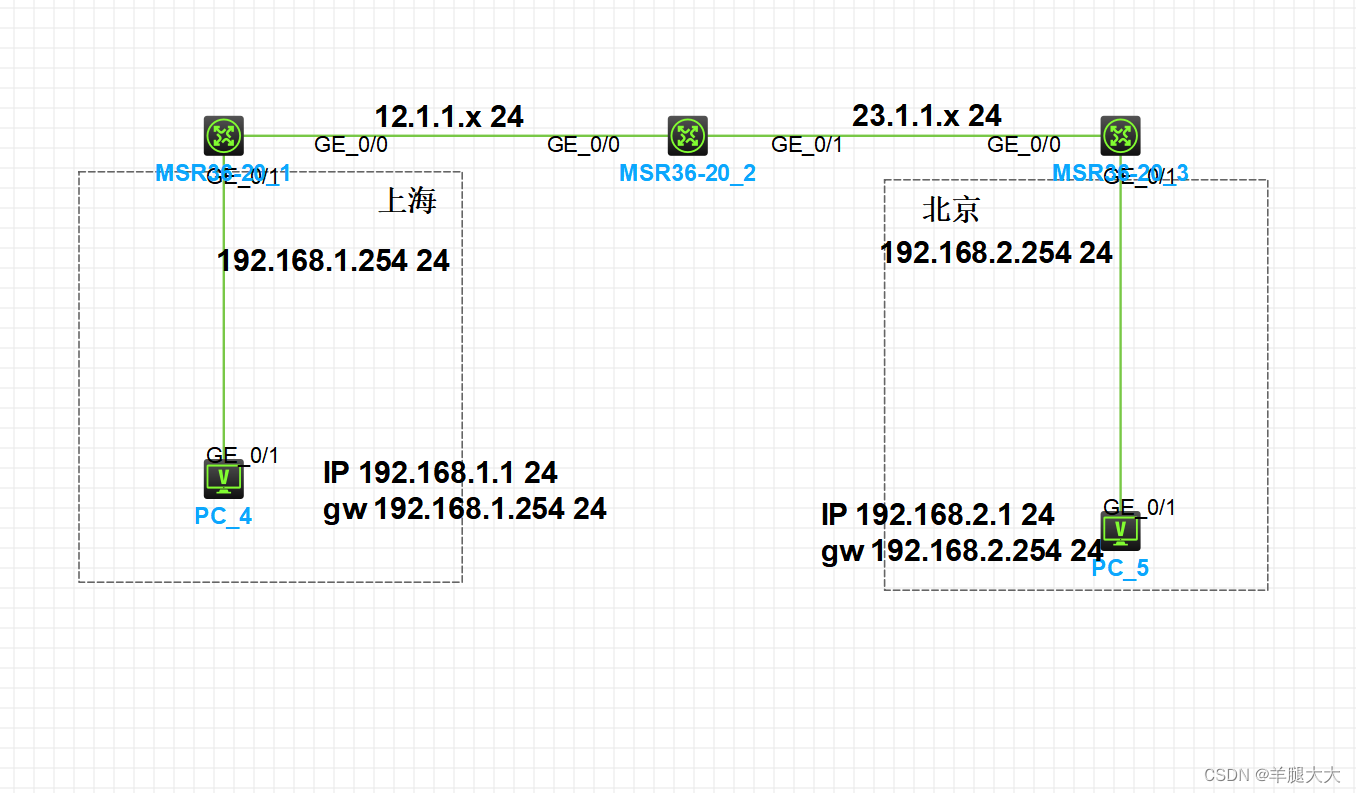
实验需求
- 按照拓扑配置 IP 地址。
- AR1 与 AR3 部署静态路由。
- 对 192.168.1.0/24 和 192.168.2.0/24 的流量进行数据 IPSCE 加密处理。
- 部署 GRE 隧道和静态路由实现 PC1 与 PC2 通过加密 GRE 隧道实现互通。
实验配置之及其验证
(1)根据拓扑配置IP地址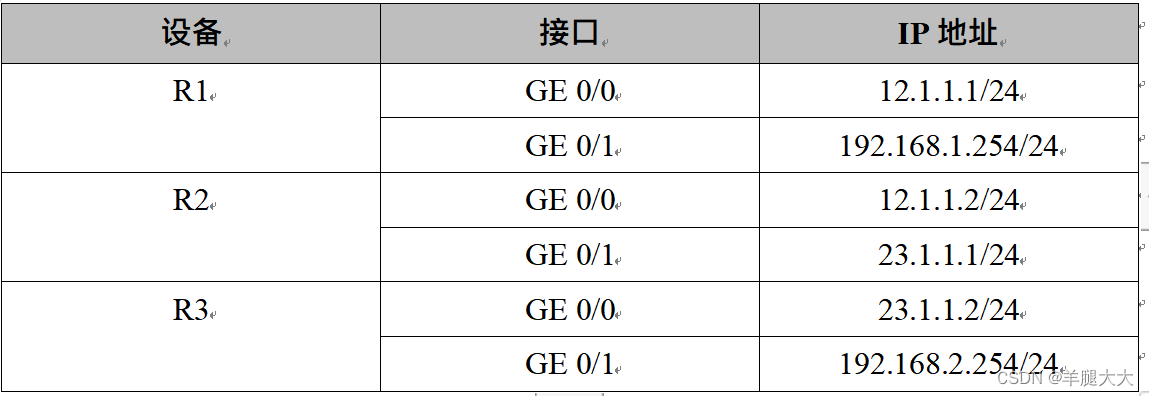
(2)实现需求 2:部署静态路由
#R1
[R1]ip route-static 23.1.1.0 255.255.255.0 12.1.1.2
//配置一条目的地址是网络 A 外网出口的静态路由
#R3
[R3]ip route-static 12.1.1.0 255.255.255.0 23.1.1.1(3)部署 GRE 隧道和静态路由实现 PC1 与 PC2 通过加密 GRE 隧道实现互通。
#R1
[R1] interface Tunnel 0 mode gre
[R1-Tunnel0] ip address 25.25.25.1 24
[R1-Tunnel0] source 12.1.1.1
[R1-Tunnel0] destination 23.1.1.2
#R3
[R3] interface Tunnel 0 mode gre
[R3-Tunnel0] ip address 25.25.25.2 24
[R3-Tunnel0] source 23.1.1.2
[R3-Tunnel0] destination 12.1.1.1
#R1
[R1] ip route-static 192.168.2.0 24 Tunnel 0
#R3
[R3] ip route-static 192.168.1.0 24 Tunnel 0(4)对 192.168.1.0/24 和 192.168.2.0/24 的流量进行数据 IPSCE 加密处理
1>部署acl
#R1
[R1]acl advanced 3000
[R1-acl-ipv4-adv-3000]rule 5 permit ip source 192.168.1.0 0.0.0.255 destination
192.168.2.0 0.0.0.255
#R3
[R3]acl advanced 3000
[R3-acl-ipv4-adv-3000]rule 5 permit ip source 192.168.2.0 0.0.0.255 destination
192.168.1.0 0.0.0.2552>部署 IKE 提议
#R1
[R1]ike proposal 1
[R1-ike-proposal-1]authentication-method pre-share//身份验证方法采用预共享密钥
[R1-ike-proposal-1]dh group2 //采用非对称算法 DH 组交换 key
[R1-ike-proposal-1]encryption-algorithm aes-cbc-128 //加密算法 aes-cbc-128
[R1-ike-proposal-1]authentication-algorithm sha //验证算法 sha1
#R3
[R3] ike proposal 1
[R3-ike-proposal-1] authentication-method pre-share
[R3-ike-proposal-1] dh group2
[R3-ike-proposal-1] encryption-algorithm aes-cbc-128
[R3-ike-proposal-1] authentication-algorithm sha3>部署ike keychain
#R1
[R1]ike keychain k //配置预共享密钥为 123456
[R1-ike-keychain-k]pre-shared-key address 25.25.25.2 key simple 123456
#R3
[R3]ike keychain k
[R3-ike-keychain-k]pre-shared-key address 25.25.25.1 key simple 1234564>部署IKE对等体
#R1
[R1] ike profile 1
[R1-ike-profile-1] exchange-mode aggressive //协商模式为野蛮模式
[R1-ike-profile-1] local-identity address 25.25.25.1 //采用 IP 地址标识本端身份信息
[R1-ike-profile-1] match remote identity address 25.25.25.2 //匹配对端身份
[R1-ike-profile-1] proposal 1
[R1-ike-profile-1] keychain k
#R3
[R3] ike profile 1
[R3-ike-profile-1] exchange-mode aggressive
[R3-ike-profile-1] local-identity address 25.25.25.2
[R3-ike-profile-1] match remote identity address 25.25.25.1
[R3-ike-profile-1] proposal 1
[R3-ike-profile-1] keychain k5>部署 IPSEC 提议
#R1
[R1] ipsec transform-set 1
[R1-ipsec-transform-set-1] esp encryption-algorithm aes-cbc-128
[R1-ipsec-transform-set-1] esp authentication-algorithm sha256
#R3
[R3] ipsec transform-set 1
[R3-ipsec-transform-set-1] esp encryption-algorithm aes-cbc-128
[R3-ipsec-transform-set-1] esp authentication-algorithm sha2566>部署IPSEC策略
#R1
[R1] ipsec policy map1 10 isakmp
[R1-ipsec-policy-isakmp-map1-10] security acl 3000
[R1-ipsec-policy-isakmp-map1-10] remote-address 25.25.25.2
[R1-ipsec-policy-isakmp-map1-10] transform-set 1
[R1-ipsec-policy-isakmp-map1-10] ike-profile 1
#R3
[R3] ipsec policy map1 10 isakmp
[R3-ipsec-policy-isakmp-map1-10] security acl 3000
[R3-ipsec-policy-isakmp-map1-10] remote-address 25.25.25.1
[R3-ipsec-policy-isakmp-map1-10] transform-set 1
[R3-ipsec-policy-isakmp-map1-10] ike-profile 17>应用IPSEC策略
#R1
[R1] interface Tunnel 0 mode gre
[R1-Tunnel0] ipsec apply policy map1
#R3
[R3] interface Tunnel 0 mode gre
[R3-Tunnel0] ipsec apply policy map1验证:
(1)实现外网通信
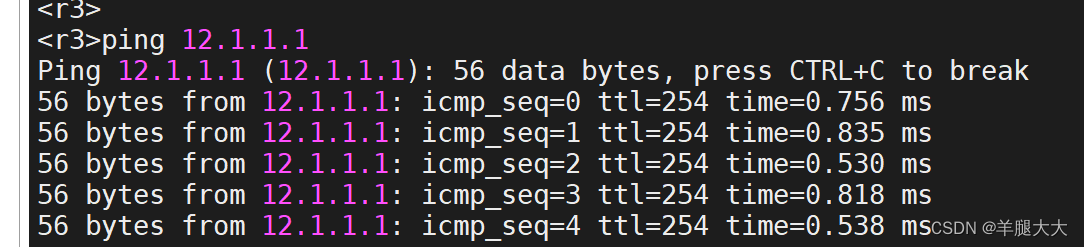
(2)PC1与PC2通信

(3)IPSEC加密


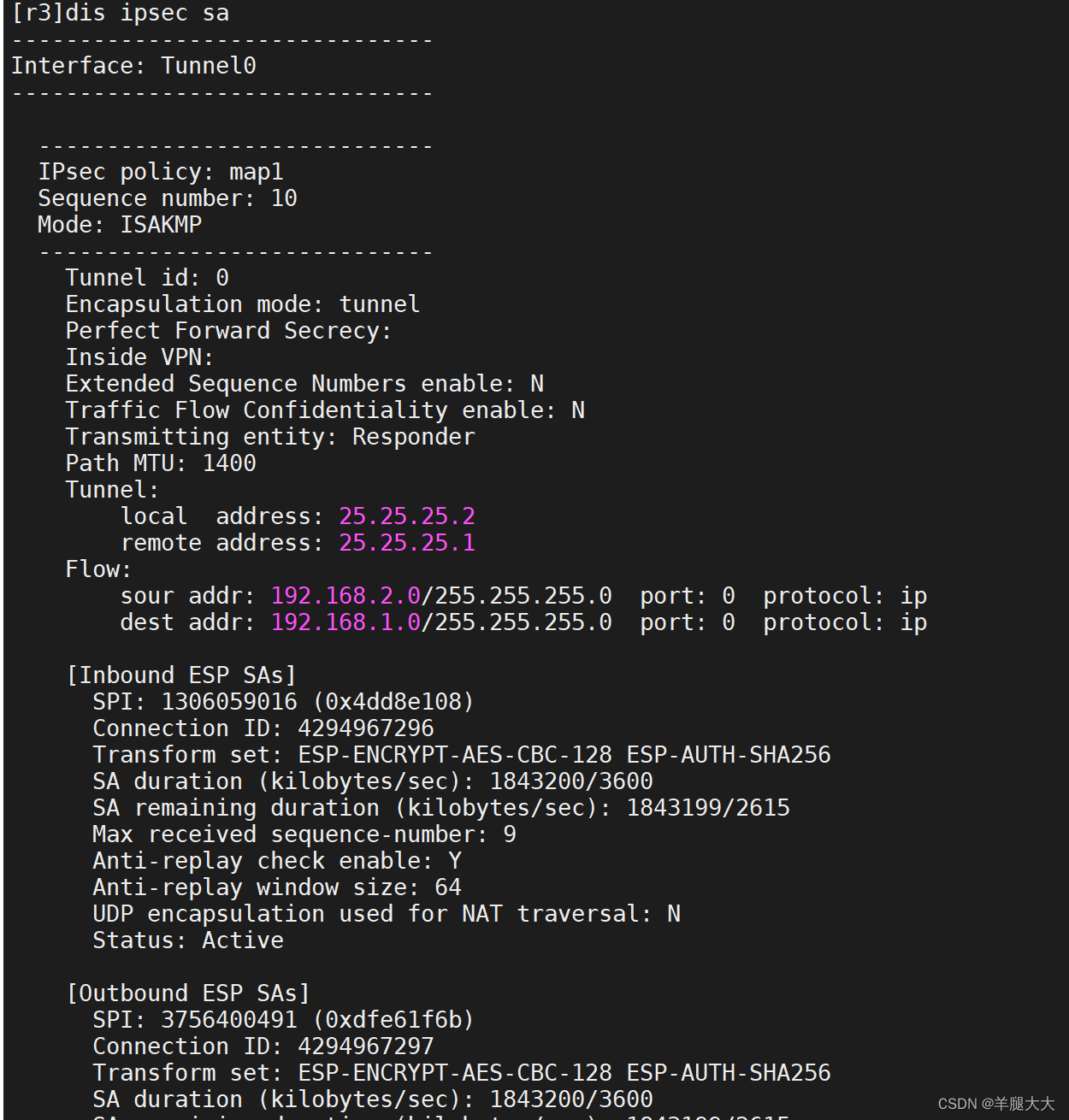




















 2533
2533











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








