TupEAx
脱壳+tea加密
拖进exe发现有壳然后是32字节
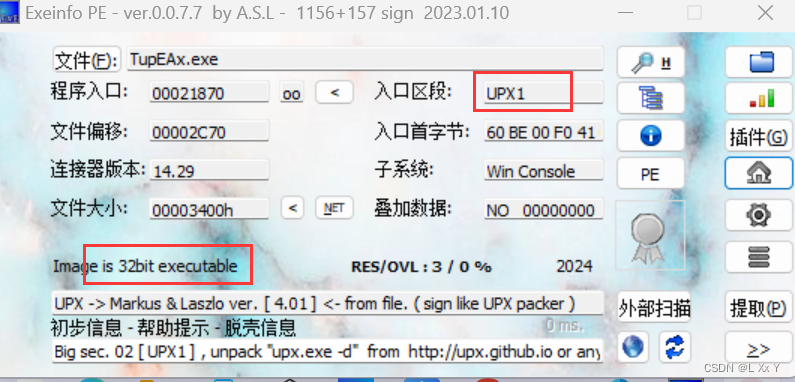
脱壳
进入ida32分析
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char v4; // [esp+0h] [ebp-1B8h]
char v5; // [esp+0h] [ebp-1B8h]
int m; // [esp+D0h] [ebp-E8h]
int k; // [esp+DCh] [ebp-DCh]
int j; // [esp+E8h] [ebp-D0h]
int v9[4]; // [esp+F4h] [ebp-C4h] BYREF
int i; // [esp+104h] [ebp-B4h]
int v11; // [esp+110h] [ebp-A8h]
char v12[4]; // [esp+11Ch] [ebp-9Ch] BYREF
int v13[7]; // [esp+120h] [ebp-98h] BYREF
char v14; // [esp+13Ch] [ebp-7Ch]
char v15[44]; // [esp+148h] [ebp-70h]
int v16[6]; // [esp+174h] [ebp-44h] BYREF
char v17[31]; // [esp+18Ch] [ebp-2Ch]
char v18[4]; // [esp+1ABh] [ebp-Dh] BYREF
__CheckForDebuggerJustMyCode(&unk_41C003);
v17[0] = 74;
v17[1] = -100;
v17[2] = 22;
v17[3] = -29;
v17[4] = -23;
v17[5] = -112;
v17[6] = -79;
v17[7] = 73;
v17[8] = 84;
v17[9] = -95;
v17[10] = -126;
v17[11] = -98;
v17[12] = 62;
v17[13] = 63;
v17[14] = -60;
v17[15] = -82;
v17[16] = 12;
v17[17] = -127;
v17[18] = 32;
v17[19] = 95;
v17[20] = 64;
v17[21] = -50;
v17[22] = 81;
v17[23] = -82;
v17[24] = 59;
v17[25] = 82;
v17[26] = -101;
v17[27] = -80;
v17[28] = -86;
v17[29] = -63;
v17[30] = -11;
strcpy(v18, "S");
v16[0] = 2;
v16[1] = 0;
v16[2] = 2;
v16[3] = 4;
*(_DWORD *)v12 = 0;
memset(v13, 0, sizeof(v13));
v14 = 0;
sub_4110DC("please input your flag: ", v4);
sub_41103C("%32s", (char)v12);
v11 = 0;
for ( i = 0; i < 32; i += 8 )
{
v9[0] = *(_DWORD *)&v12[i];
v9[1] = v13[i / 4u];
sub_41100A(v9, v16);//tea加密改了sum和delta
for ( j = 0; j < 2; ++j )
{
for ( k = 0; k < 4; ++k )
{
v15[v11] = v9[j];
v9[j] = (unsigned int)v9[j] >> 8;
++v11;
}
}
}
for ( m = 0; m < 32; ++m )
{
if ( v17[m] != v15[m] )
{
sub_4110DC("error!!!\n", v5);
return 0;
}
}
sub_4110DC(aRight, v5);
return 0;
}sub_41100A(v9, v16)函数
int __cdecl sub_411790(unsigned int *a1, _DWORD *a2)
{
int result; // eax
int i; // [esp+D0h] [ebp-38h]
int v4; // [esp+E8h] [ebp-20h]
unsigned int v5; // [esp+F4h] [ebp-14h]
unsigned int v6; // [esp+100h] [ebp-8h]
__CheckForDebuggerJustMyCode(&unk_41C003);
v6 = *a1;
v5 = a1[1];
v4 = 0;
for ( i = 0; i < 32; ++i )
{
v4 += 221492336;
v6 += (a2[1] + (v5 >> 5)) ^ (v4 + v5) ^ (*a2 + 16 * v5);
v5 += (a2[3] + (v6 >> 5)) ^ (v4 + v6) ^ (a2[2] + 16 * v6);
}
*a1 = v6;
result = 4;
a1[1] = v5;
return result;
}
写个脚本得到,其实就是常规tea加密
#include <stdio.h>
#include <stdint.h>
//加密函数
void encrypt (uint32_t* v, uint32_t* k) {
uint32_t v0=v[0], v1=v[1], sum=0, i; //v0,v1分别为字符串的低字节高字节
uint32_t delta=0xdeadbeef;
uint32_t k0=k[0], k1=k[1], k2=k[2], k3=k[3];
for (i=0; i < 32; i++) { //加密32轮
sum += delta;
v0 += ((v1<<4) + k0) ^ (v1 + sum) ^ ((v1>>5) + k1);
v1 += ((v0<<4) + k2) ^ (v0 + sum) ^ ((v0>>5) + k3);
}
v[0]=v0;
v[1]=v1;//加密后再重新赋值
}
//解密函数
void decrypt (uint32_t* v, uint32_t* k) {
uint32_t v0=v[0], v1=v[1], sum=0xD33B470*32, i;
uint32_t delta=0xD33B470;
uint32_t k0=k[0], k1=k[1], k2=k[2], k3=k[3];
for (i=0; i<32; i++)
{ //解密时将加密算法的顺序倒过来,还有+=变为-=
v1 -= ((v0<<4) + k2) ^ (v0 + sum) ^ ((v0>>5) + k3);
v0 -= ((v1<<4) + k0) ^ (v1 + sum) ^ ((v1>>5) + k1);
sum -= delta;
}
v[0]=v0;
v[1]=v1;//解密后再重新赋值
}
int main()
{
unsigned int key[4] = {2,0,2,4};
unsigned char data[] =
{
0x4A,0x9C, 0x16, 0xE3, 0xE9, 0x90, 0xB1, 0x49,
0x54, 0xA1,0x82, 0x9E, 0x3E, 0x3F, 0xC4, 0xAE,
0x0C,0x81, 0x20, 0x5F, 0x40, 0xCE, 0x51, 0xAE,
0x3B,0x52, 0x9B, 0xB0, 0xAA, 0xC1, 0xF5, 'S'
};
for (int i = 0; i < 5; i++)
decrypt((unsigned int*)data + i * 2, key);
for (int i = 0; i < 32; i++)
{
printf("%c", data[i]);
}
return 0;
}//HZNUCTF{EnjOy_th1s_cuP_0f_t3@@@}IDA
拖入exe,然后进入ida64
根据提示找到一二部分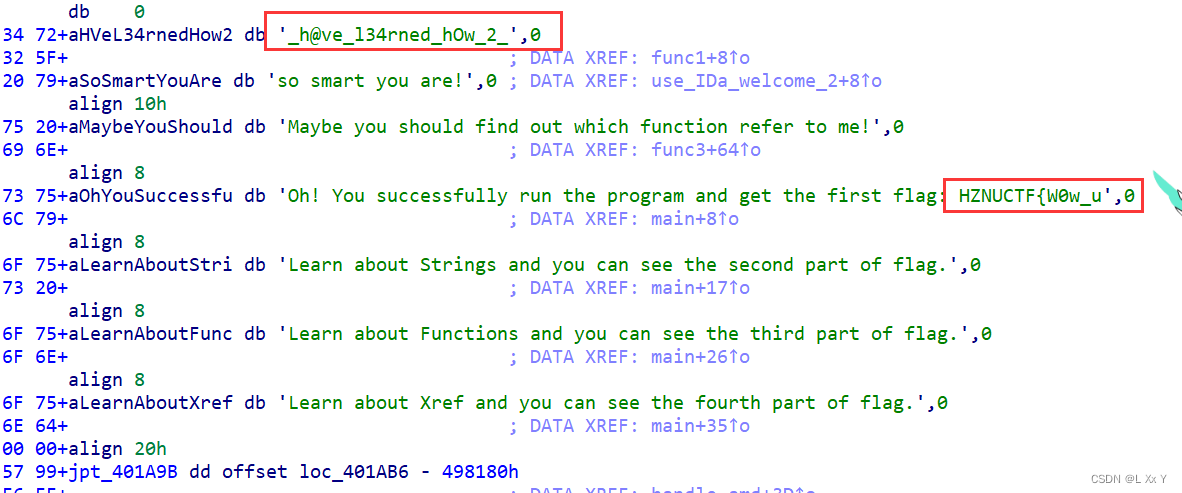
第三部分是函数名称
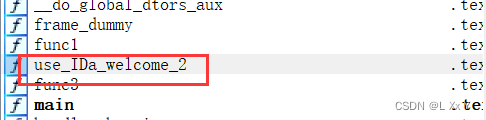
第四部分对函数交叉应用(X)
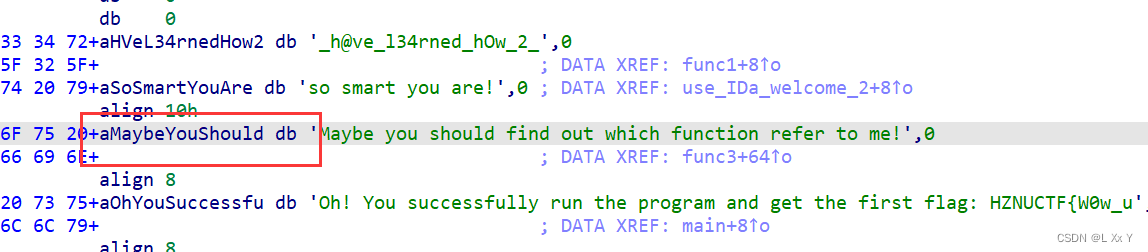
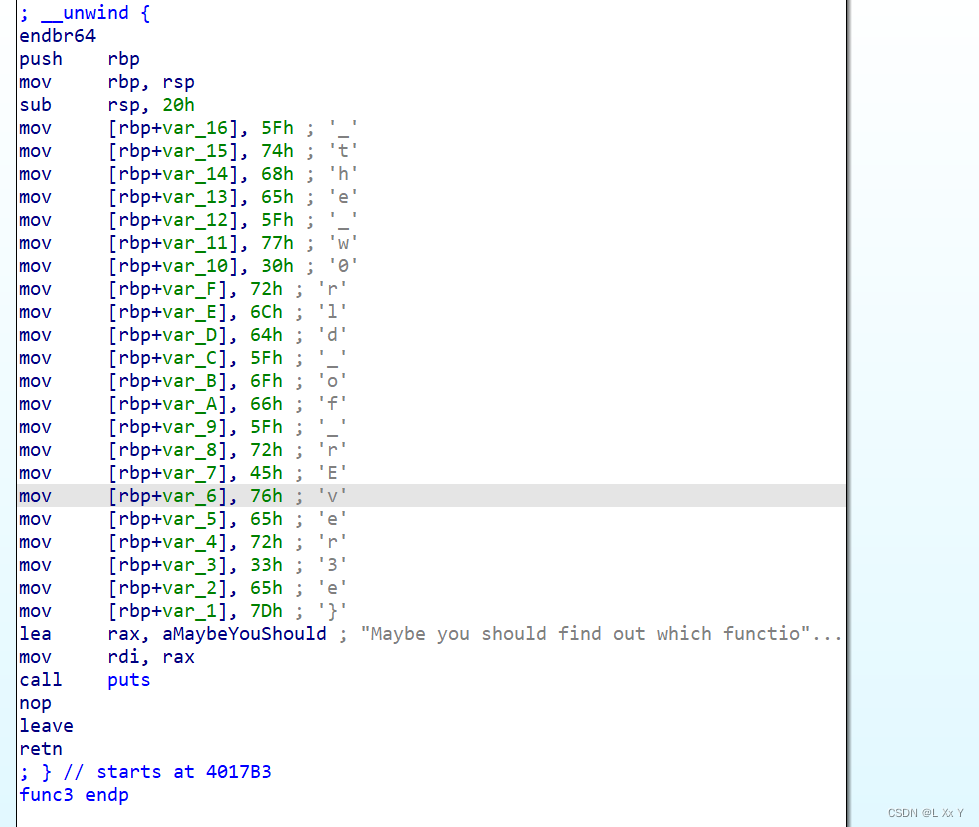 HZNUCTF{W0w_u_h@ve_l34rned_hOw_2_use_IDa_welcome_2_the_w0rld_of_rEver3e}
HZNUCTF{W0w_u_h@ve_l34rned_hOw_2_use_IDa_welcome_2_the_w0rld_of_rEver3e}
babyre
拖入exe,然后拖入ida32分析
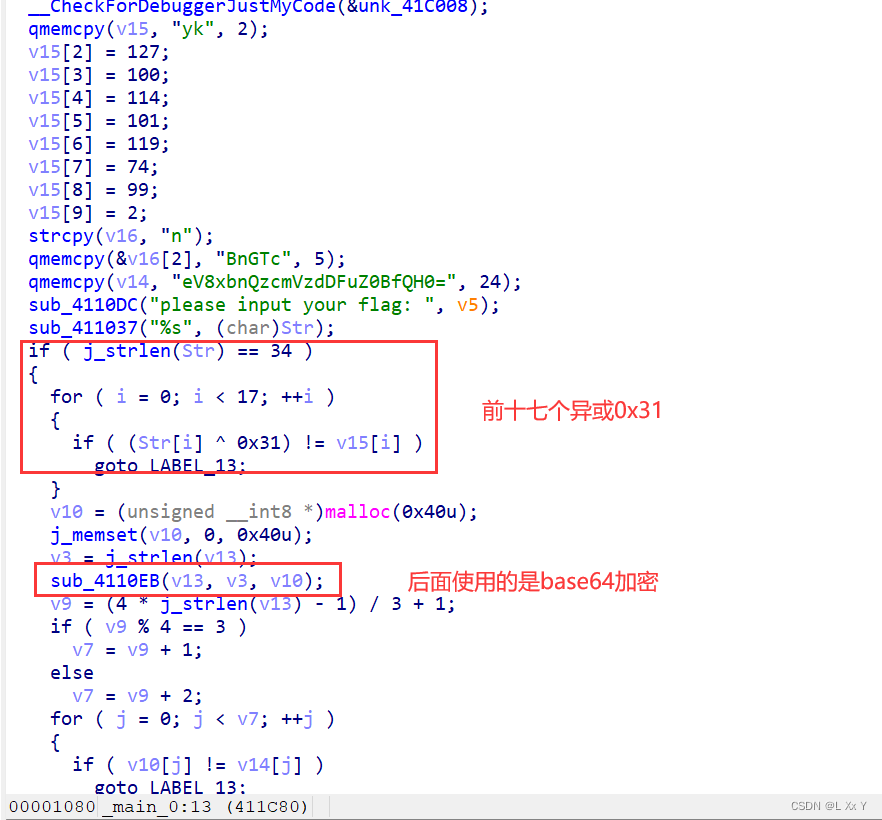
写出脚本 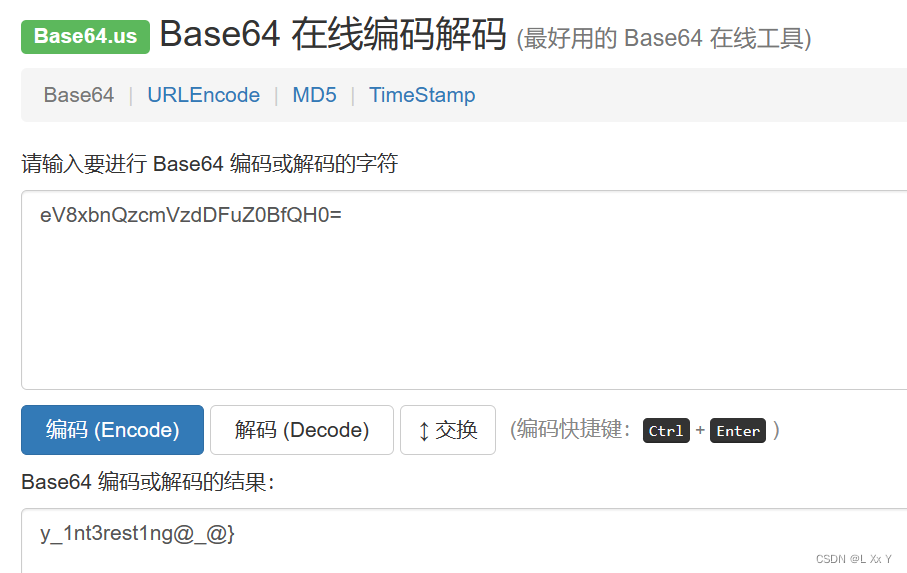
#include <stdio.h>
#include <stdint.h>
int main()
{
char enc[]={'y','k',127,100,114,101,119,74,99,2,'n','B'
,'n','G','T','c'};
int i;
for(i=0;i<17;i++)
{
enc[i]^=0x31;
printf("%c",enc[i]);
}
printf("y_1nt3rest1ng@_@}");
return 0;
}//HZNUCTF{R3_1s_veRy_1nt3rest1ng@_@}少了一个1
但是应该看得出来吧





















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








