easyPY
这是一道python的反汇编题先下载文件发现是.exe
首先,我们先将pyinstxtractor.py工具与我们要反编译的.exe文件放入同一个工作目录下
 然后再黑框输入python pyinstxtractor.py +文件名.exe,回车运行,出现一个同名文件见夹再找同名文件,然后再用pycdc.exe
然后再黑框输入python pyinstxtractor.py +文件名.exe,回车运行,出现一个同名文件见夹再找同名文件,然后再用pycdc.exe
用pyc转成py就是如下,但是对于其中无法编译部分,需要对照字节码进行补全,将pyc文件转化为字节码需要使用pycdas工具
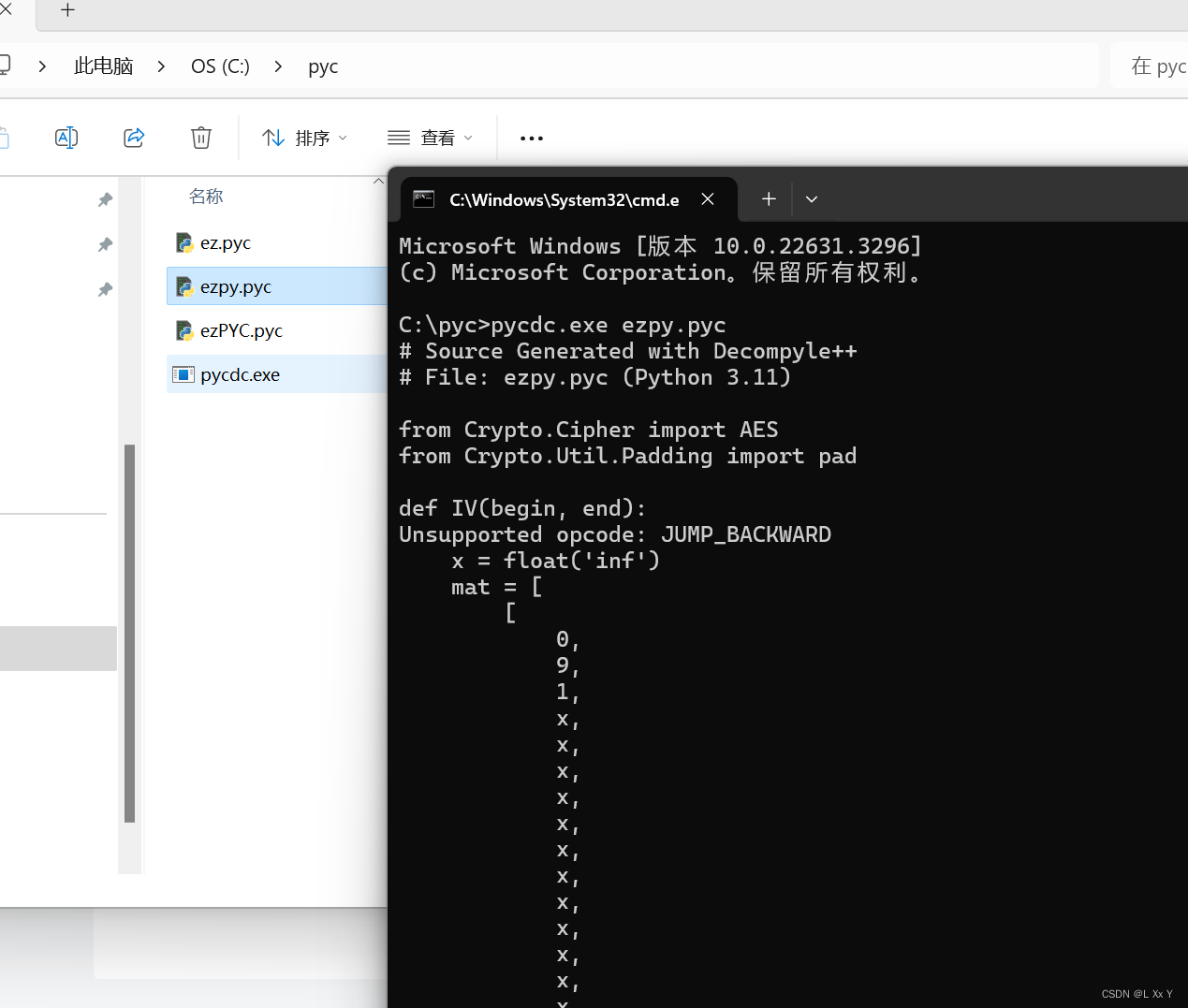
其实大致可以知道是一个aes加密然后主要就是找到iv和keyyongyong
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
def IV(begin, end):
Unsupported opcode: JUMP_BACKWARD
x = float('inf')
mat = [
[
0,
9,
1,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x],
[
1,
0,
x,
1,
x,
x,
x,
x,
0,
x,
x,
x,
x,
x,
x,
x],
[
1,
x,
0,
x,
1,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x],
[
x,
1,
x,
0,
x,
1,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x],
[
x,
x,
1,
x,
0,
x,
1,
x,
x,
x,
x,
x,
x,
x,
x,
x],
[
x,
x,
x,
1,
x,
0,
x,
1,
x,
x,
x,
x,
x,
x,
x,
x],
[
x,
x,
x,
x,
1,
x,
0,
x,
1,
x,
x,
x,
x,
x,
x,
x],
[
x,
x,
x,
x,
x,
1,
x,
0,
9,
1,
x,
x,
x,
x,
x,
x],
[
x,
1,
x,
x,
x,
x,
1,
9,
0,
x,
x,
x,
x,
x,
x,
50],
[
x,
x,
x,
x,
x,
x,
x,
1,
x,
0,
1,
x,
x,
x,
x,
x],
[
x,
x,
x,
x,
x,
x,
x,
x,
x,
1,
0,
1,
x,
x,
x,
x],
[
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
1,
0,
1,
x,
x,
x],
[
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
1,
0,
1,
x,
x],
[
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
1,
0,
1,
x],
[
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
x,
1,
0,
1],
[
x,
x,
x,
x,
x,
x,
x,
x,
50,
x,
x,
x,
x,
x,
1,
0]]
n = len(mat)
parent = []
collected = []
distTo = mat[begin]
path = []
# WARNING: Decompyle incomplete
def Key():
Unsupported opcode: JUMP_BACKWARD
key1 = [
55,
53,
55,
49,
53,
54,
55,
53]
key2 = [
59,
57,
59,
61,
57,
58,
58,
57]
key = ''
# WARNING: Decompyle incomplete
def encrypt(key, plaintext, iv = (None,)):
cipher = AES.new(key, AES.MODE_CBC, iv = iv) if iv else AES.new(key, AES.MODE_CBC)
ciphertext = cipher.encrypt(pad(plaintext, AES.block_size))
return ciphertext
def main():
flag = b'68fcb549ee313b964d5eea2d3dedea23e87e4e89a675ff46698ed29b191ffe19f5bac00e0eb5dedcc8be847356d93eb8'
print('please input your flag: ', end = '')
message = input()
plaintext = message.encode('utf-8')
key = Key().encode('utf-8')
iv = IV(0, 15).encode('utf-8')
ciphertext = encrypt(key, plaintext, iv)
if ciphertext.hex().encode('utf-8') == flag:
print('Right!!!')
return None
None('error!!!')用pycdas转成字符码,就可以更清晰的看见具体过程了
 然后key1和2异或得到key
然后key1和2异或得到key
key1 = (55, 53, 55, 49, 53, 54, 55, 53)
key2 = (59, 57, 59, 61, 57, 58, 58, 57)
result_key = ""
for i in range(len(key1)):
result_key += chr(key1[i] ^ 0x5)
for i in range(len(key2)):
result_key += chr(key2[i] ^ 0x9)
print(result_key)
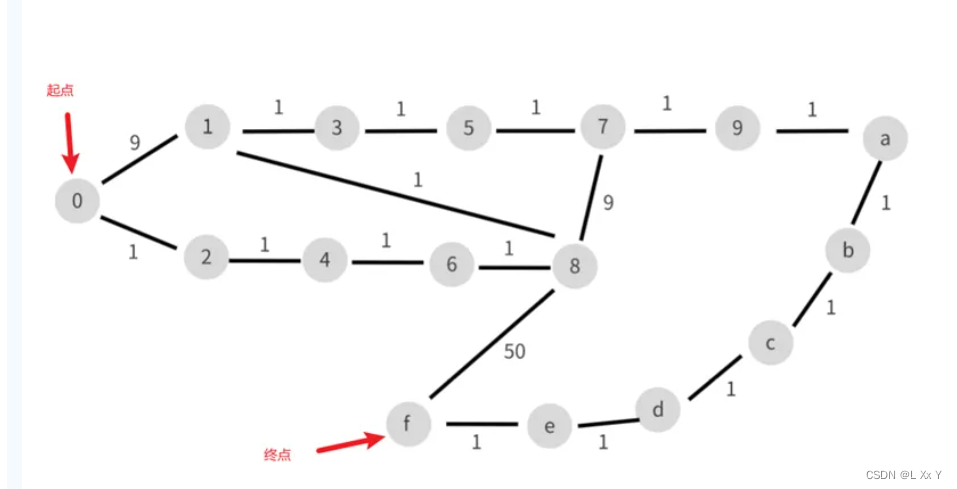
#2024032020240330关于iv先看一下这个16*16的矩阵,看的题解说是初始向量IV是通过dijkstra算法求得的最短路径
最短路径就是0246813579abcdef,然后就得到了key和iv放进赛博厨子
[0,9,1,x,x,x,x,x,x,x,x,x,x,x,x,x],
[9,0,x,1,x,x,x,x,1,x,x,x,x,x,x,x],
[1,x,0,x,1,x,x,x,x,x,x,x,x,x,x,x],
[x,1,x,0,x,1,x,x,x,x,x,x,x,x,x,x],
[x,x,1,x,0,x,1,x,x,x,x,x,x,x,x,x],
[x,x,x,1,x,0,x,1,x,x,x,x,x,x,x,x],
[x,x,x,x,1,x,0,x,1,x,x,x,x,x,x,x],
[x,x,x,x,x,1,x,0,9,1,x,x,x,x,x,x],
[x,1,x,x,x,x,1,9,0,x,x,x,x,x,x,50],
[x,x,x,x,x,x,x,1,x,0,1,x,x,x,x,x],
[x,x,x,x,x,x,x,x,x,1,0,1,x,x,x,x],
[x,x,x,x,x,x,x,x,x,x,1,0,1,x,x,x],
[x,x,x,x,x,x,x,x,x,x,x,1,0,1,x,x],
[x,x,x,x,x,x,x,x,x,x,x,x,1,0,1,x],
[x,x,x,x,x,x,x,x,x,x,x,x,x,1,0,1],
[x,x,x,x,x,x,x,x,50,x,x,x,x,x,1,0] HZNUCTF{w4wawa_Pyth0n_1s_To0_2_ea3y}
HZNUCTF{w4wawa_Pyth0n_1s_To0_2_ea3y}
运动的elf
本题考查的是动态调试和sm3加密
拖入exe发现是64字节然后拖入ida
babyAndroid
本题考查的是安卓逆向和aes加密
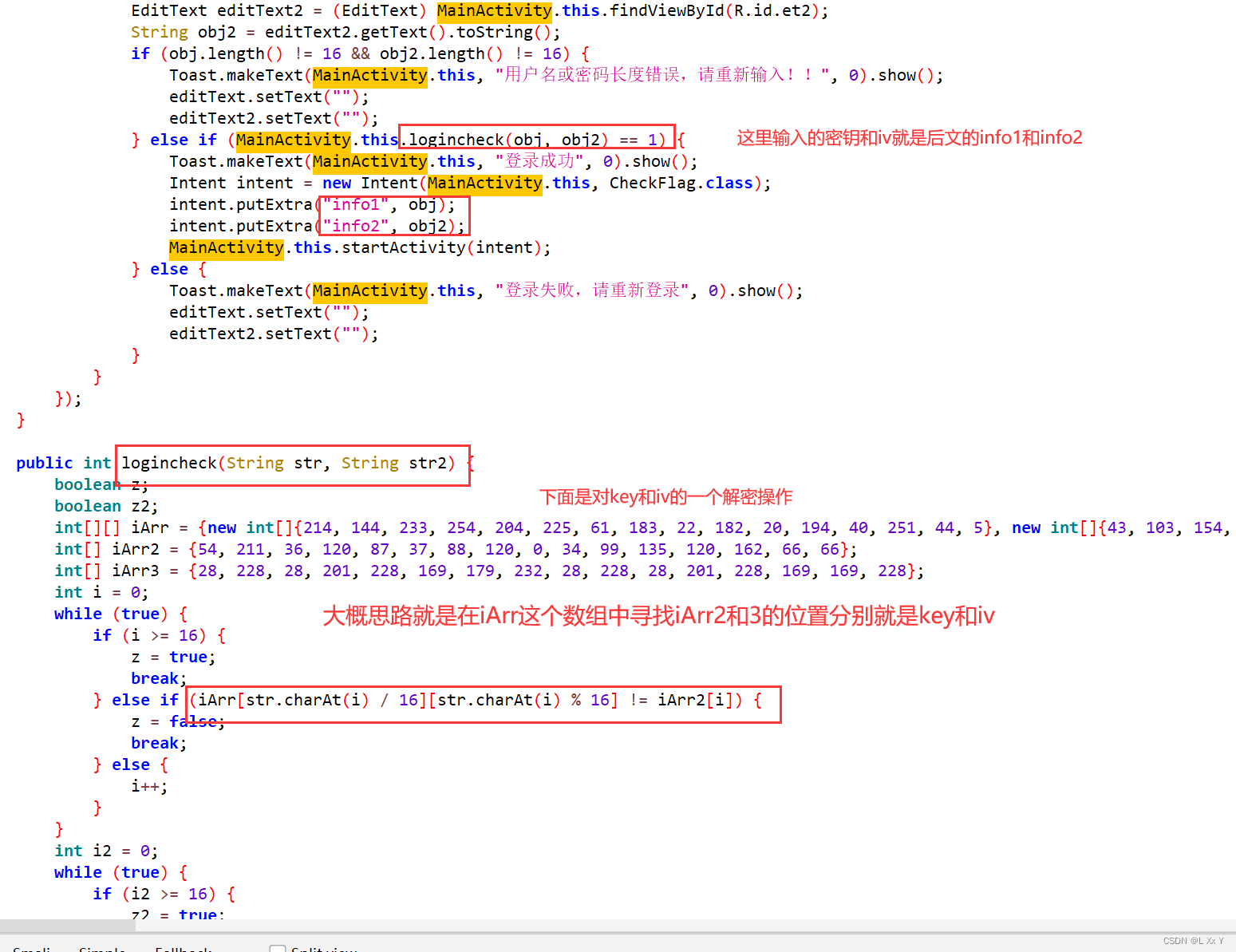
用jadx打开查看mainactivity然后分析
#include<stdio.h>
int main()
{
int iArr[16][16] =
{
{214, 144, 233, 254, 204, 225, 61, 183, 22, 182, 20, 194, 40, 251, 44, 5},
{43, 103, 154, 118, 42, 190, 4, 195, 170, 68, 19, 38, 73, 134, 6, 153},
{156, 66, 80, 244, 145, 239, 152, 122, 51, 84, 11, 67, 237, 207, 172, 98},
{228, 179, 28, 169, 201, 8, 232, 149, 128, 223, 148, 250, 117, 143, 63, 166},
{71, 7, 167, 252, 243, 115, 23, 186, 131, 89, 60, 25, 230, 133, 79, 168},
{104, 107, 129, 178, 113, 100, 218, 139, 248, 235, 15, 75, 112, 86, 157, 53},
{30, 36, 14, 94, 99, 88, 209, 162, 37, 34, 124, 59, 1, 33, 120, 135},
{212, 0, 70, 87, 159, 211, 39, 82, 76, 54, 2, 231, 160, 196, 200, 158},
{234, 191, 138, 210, 64, 199, 56, 181, 163, 247, 242, 206, 249, 97, 21, 161},
{224, 174, 93, 164, 155, 52, 26, 85, 173, 147, 50, 48, 245, 140, 177, 227},
{29, 246, 226, 46, 130, 102, 202, 96, 192, 41, 35, 171, 13, 83, 78, 111},
{213, 219, 55, 69, 222, 253, 142, 47, 3, 255, 106, 114, 109, 108, 91, 81},
{141, 27, 175, 146, 187, 221, 188, 127, 17, 217, 92, 65, 31, 16, 90, 216},
{10, 193, 49, 136, 165, 205, 123, 189, 45, 116, 208, 18, 184, 229, 180, 176},
{137, 105, 151, 74, 12, 150, 119, 126, 101, 185, 241, 9, 197, 110, 198, 132},
{24, 240, 125, 236, 58, 220, 77, 32, 121, 238, 95, 62, 215, 203, 57, 72}
};
int iArr1[] = {54, 211, 36, 120, 87, 37, 88, 120, 0, 34, 99, 135, 120, 162, 66, 66};
int iArr2[] = {28, 228, 28, 201, 228, 169, 179, 232, 28, 228, 28, 201, 228, 169, 169, 228};
int a[16];
int b[16];
int j, k, i;
for (i = 0; i < 16; i++)
{
for (j = 0; j < 16; j++)
{
for (k = 0; k < 16; k++)
{
if (iArr[j][k] == iArr1[i])
{
a[i] = 16 * j + k;
break; // 结束当前循环
}
}
}
}
for (i = 0; i < 16; i++)
{
for (j = 0; j < 16; j++)
{
for (k = 0; k < 16; k++)
{
if (iArr[j][k] == iArr2[i])
{
b[i] = 16 * j + k;
break; // 结束当前循环
}
}
}
}
printf("key:");
for (i = 0; i < 16; i++)
{
printf("%c", a[i]);
}
printf("\n");
printf("iv:");
for (i = 0; i < 16; i++)
{
printf("%c", b[i]);
}
printf("\n");
return 0;
}//key:yuanshenqidong!!
iv:2024031620240330
根据上述可以得到key和iv
用户名key:yuanshenqidong!!
password iv:2024031620240330
然后进入checkflag函数观察
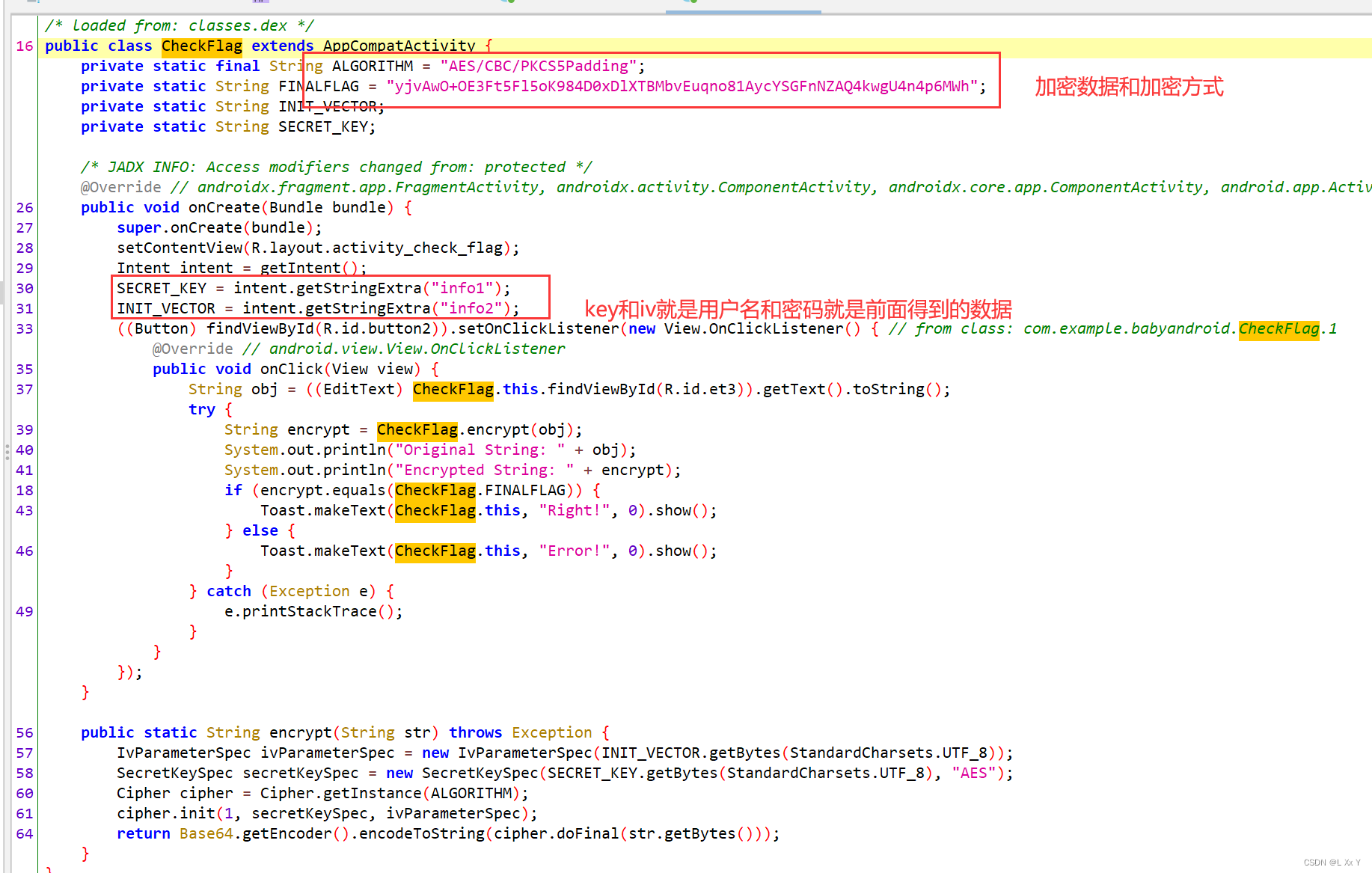
用赛博厨子HZNUCTF{welc0m3_2_4ndro1d_r3verse_?O.o_o.O?}






















 2662
2662











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








