HZNUCTF
babyre
exe检查是32位,拖入ida32
本题考查动态调试
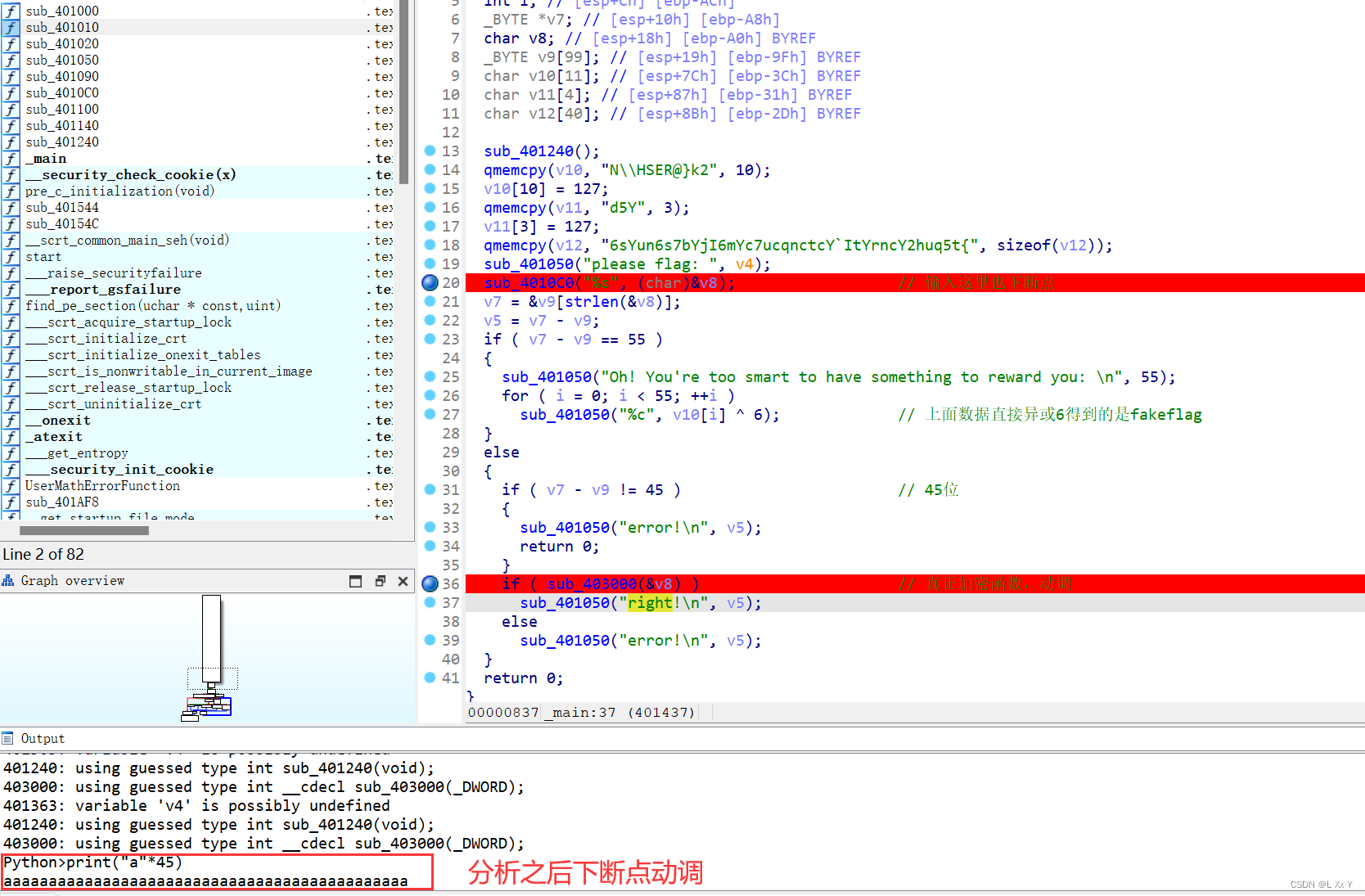
F5生成伪代码,先F8执行然后传参
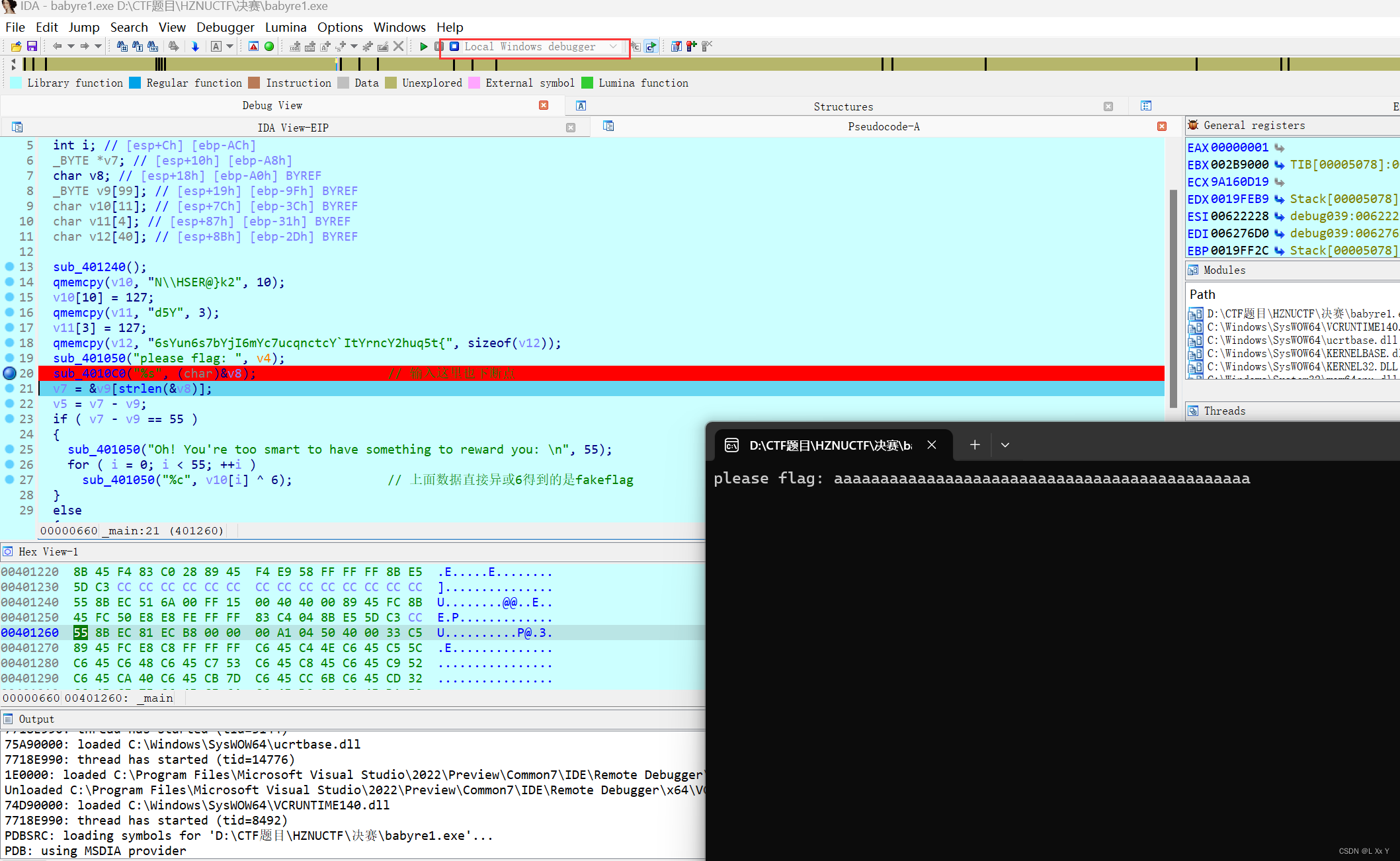
然后F9跳到加密函数 tab+空格进入汇编层
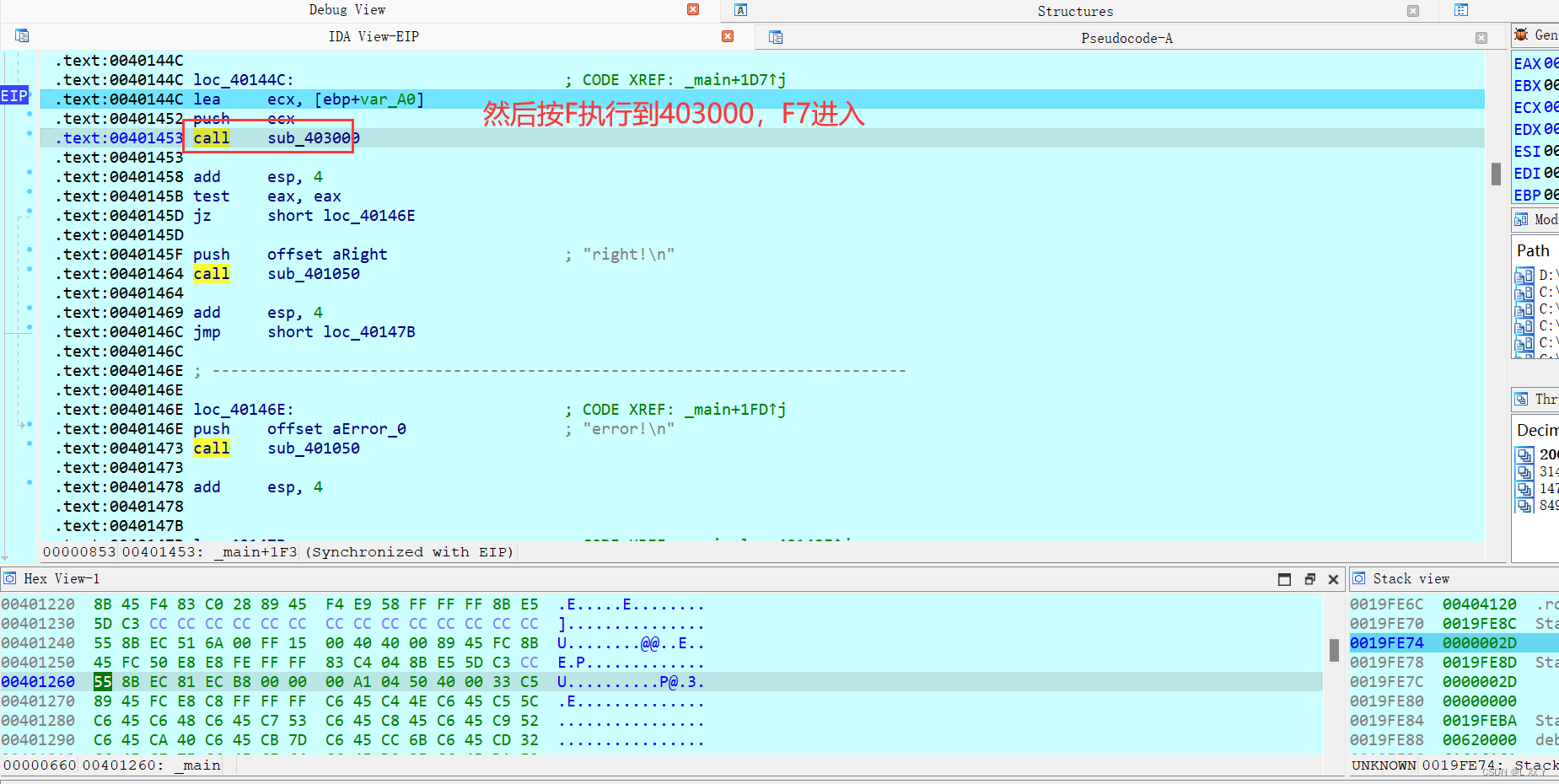
进入之后一直F8,然后U(取消识别)C(识别成代码)P(创建函数)在这期间可以ALT+L:标记 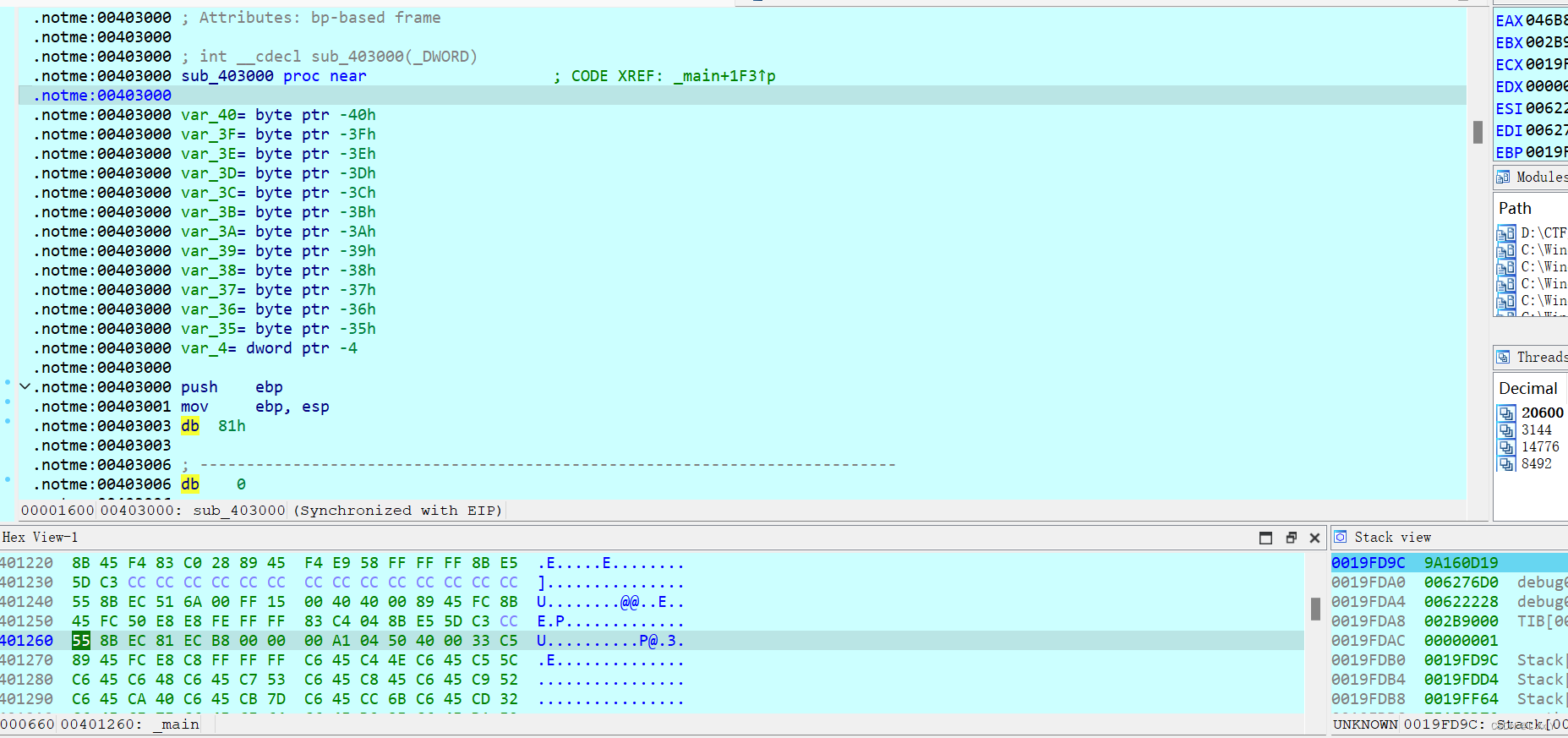
之后就是这样然后按空格分析
就是base64改表
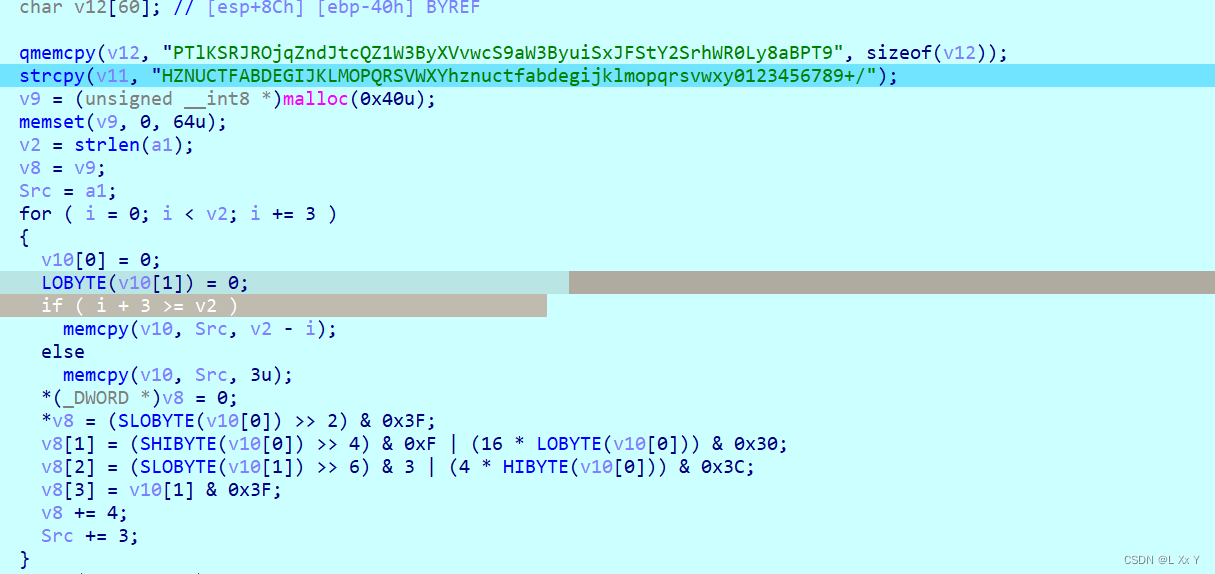
int __cdecl sub_403000(const char *a1)
{
signed int v2; // [esp+Ch] [ebp-C0h]
const char *Src; // [esp+18h] [ebp-B4h]
unsigned int k; // [esp+20h] [ebp-ACh]
int j; // [esp+28h] [ebp-A4h]
signed int i; // [esp+2Ch] [ebp-A0h]
int v7; // [esp+34h] [ebp-98h]
unsigned __int8 *v8; // [esp+38h] [ebp-94h]
unsigned __int8 *v9; // [esp+40h] [ebp-8Ch]
__int16 v10[2]; // [esp+44h] [ebp-88h] BYREF
char v11[68]; // [esp+48h] [ebp-84h] BYREF
char v12[60]; // [esp+8Ch] [ebp-40h] BYREF
qmemcpy(v12, "PTlKSRJROjqZndJtcQZ1W3ByXVvwcS9aW3ByuiSxJFStY2SrhWR0Ly8aBPT9", sizeof(v12));
strcpy(v11, "HZNUCTFABDEGIJKLMOPQRSVWXYhznuctfabdegijklmopqrsvwxy0123456789+/");
v9 = (unsigned __int8 *)malloc(0x40u);
memset(v9, 0, 64u);
v2 = strlen(a1);
v8 = v9;
Src = a1;
for ( i = 0; i < v2; i += 3 )
{
v10[0] = 0;
LOBYTE(v10[1]) = 0;
if ( i + 3 >= v2 )
memcpy(v10, Src, v2 - i);
else
memcpy(v10, Src, 3u);
*(_DWORD *)v8 = 0;
*v8 = (SLOBYTE(v10[0]) >> 2) & 0x3F;
v8[1] = (SHIBYTE(v10[0]) >> 4) & 0xF | (16 * LOBYTE(v10[0])) & 0x30;
v8[2] = (SLOBYTE(v10[1]) >> 6) & 3 | (4 * HIBYTE(v10[0])) & 0x3C;
v8[3] = v10[1] & 0x3F;
v8 += 4;
Src += 3;
}
v7 = (4 * v2 - 1) / 3 + 1;
for ( j = 0; j < v7; ++j )
v9[j] = v11[v9[j]];
if ( v7 % 4 == 3 )
{
v9[v7] = 61;
}
else if ( v7 % 4 == 2 )
{
v9[v7 + 1] = 61;
v9[v7] = 61;
}
for ( k = 0; k < strlen((const char *)v9); ++k )
{
if ( v9[k] != v12[k] )
return 0;
}
return 1;
}脚本
import base64
str1 = "PTlKSRJROjqZndJtcQZ1W3ByXVvwcS9aW3ByuiSxJFStY2SrhWR0Ly8aBPT9"
# str1是要解密的代码
string1 = "HZNUCTFABDEGIJKLMOPQRSVWXYhznuctfabdegijklmopqrsvwxy0123456789+/"
# string1是改过之后的base64表
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print(base64.b64decode(str1.translate(str.maketrans(string1, string2))))
#HZNUCTF{Ar3_y0u_r3al1y_a_r3ver4e_geniu4??!!!}XYCTF
ez_cube
放入exe,然后拖入ida64分析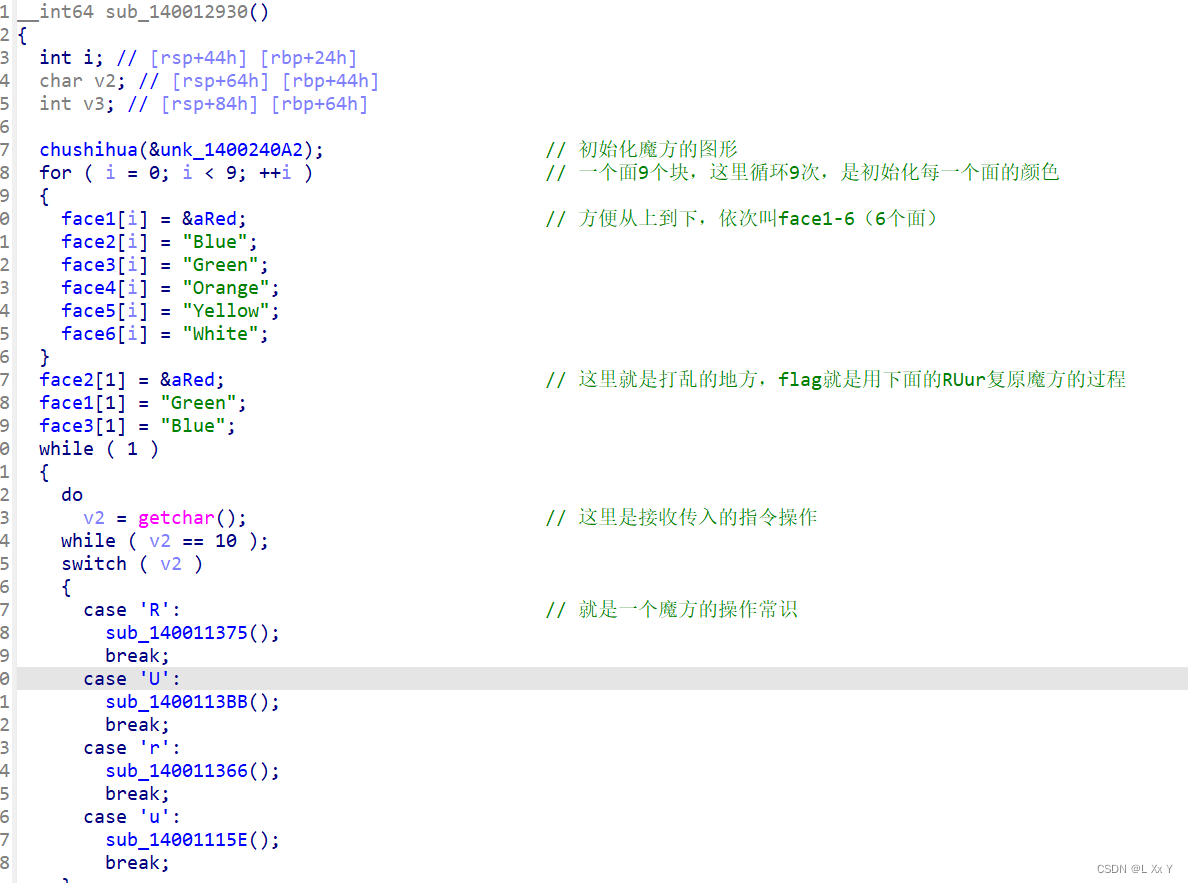
网上找的魔方模拟器
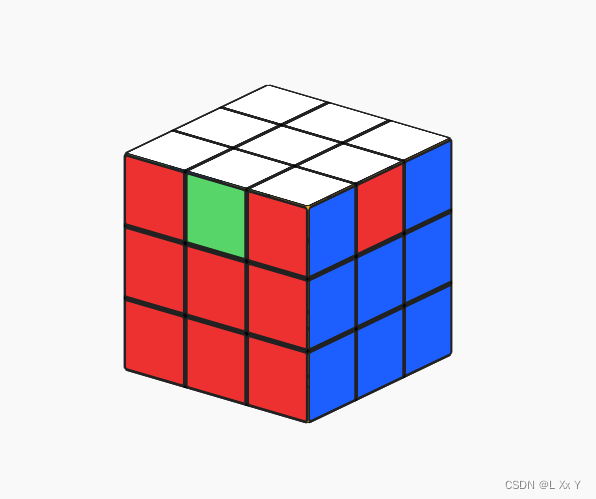
flag{RuRURURuruRR}
砸核桃
先用nspack解包,然后就是一个简单的异或(没有附件)主要就是使用nspack
ezmath
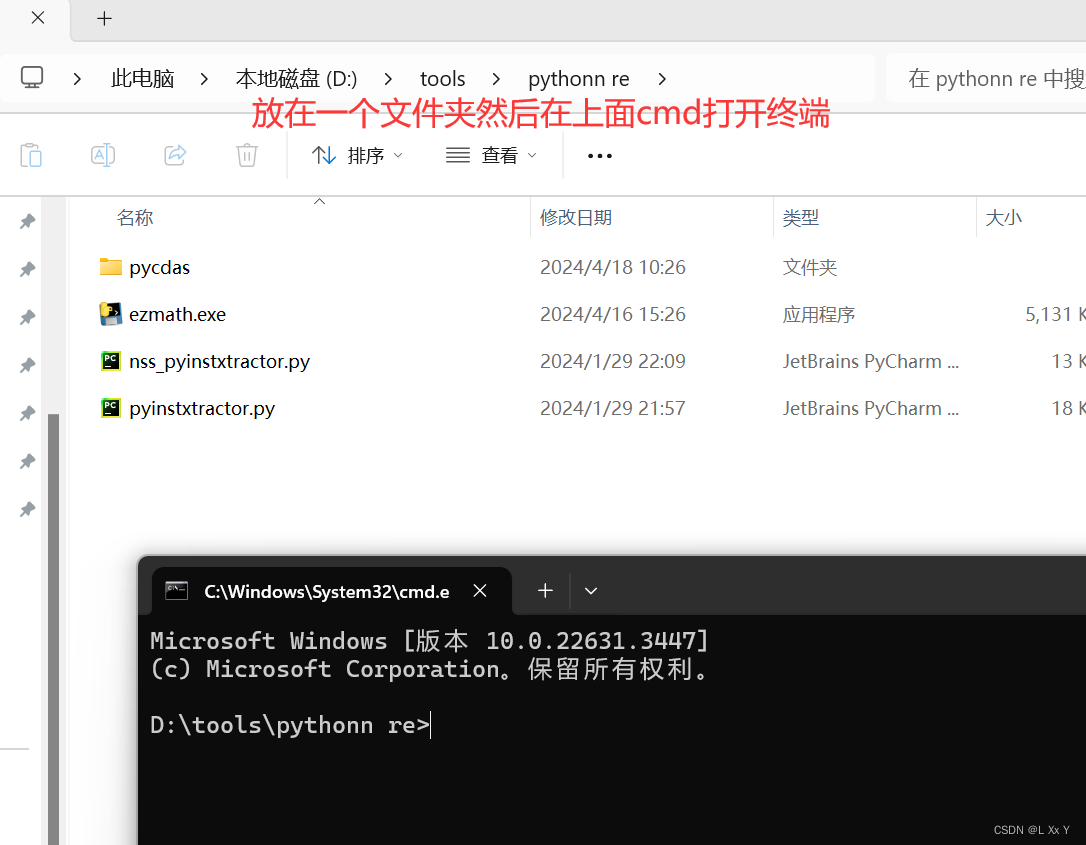
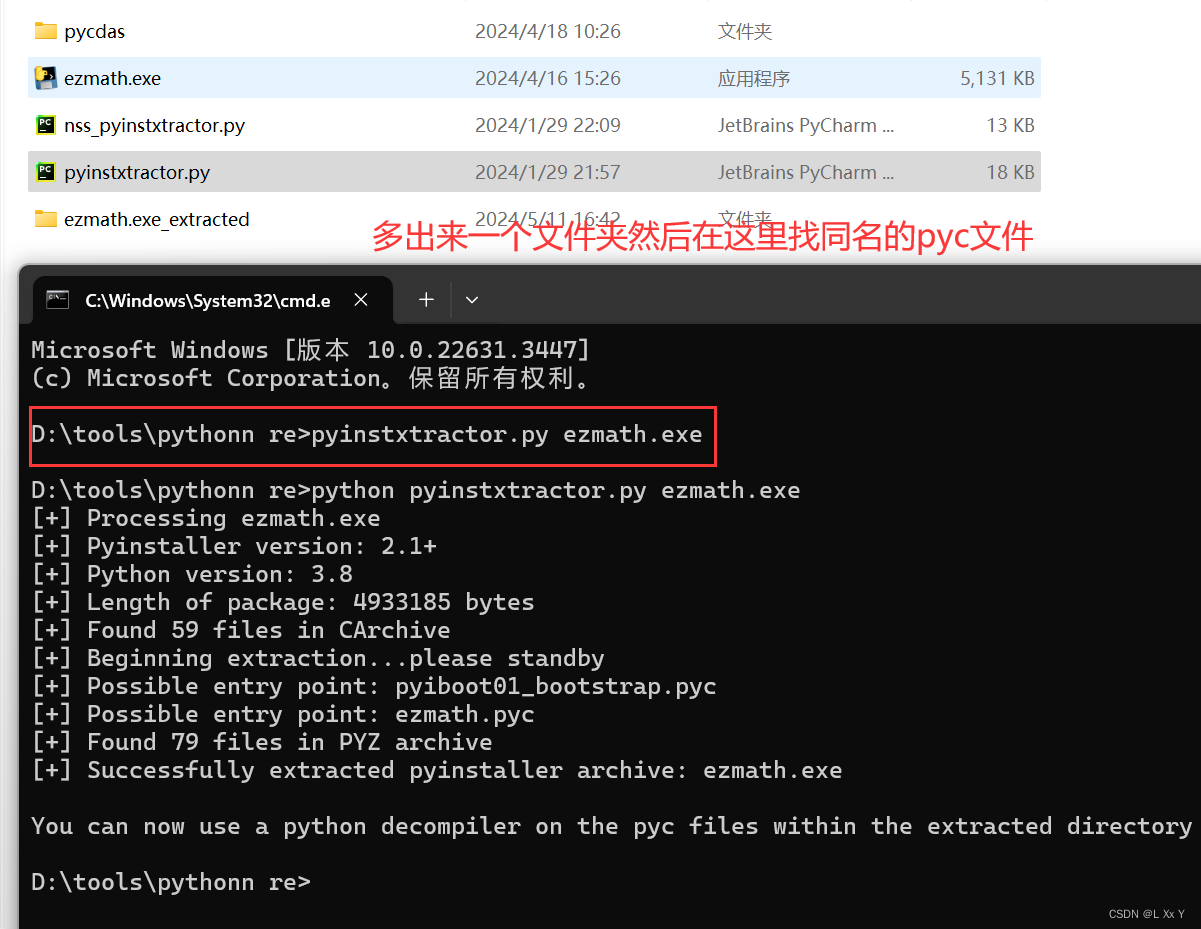
然后再打开pyc文件就是一堆z3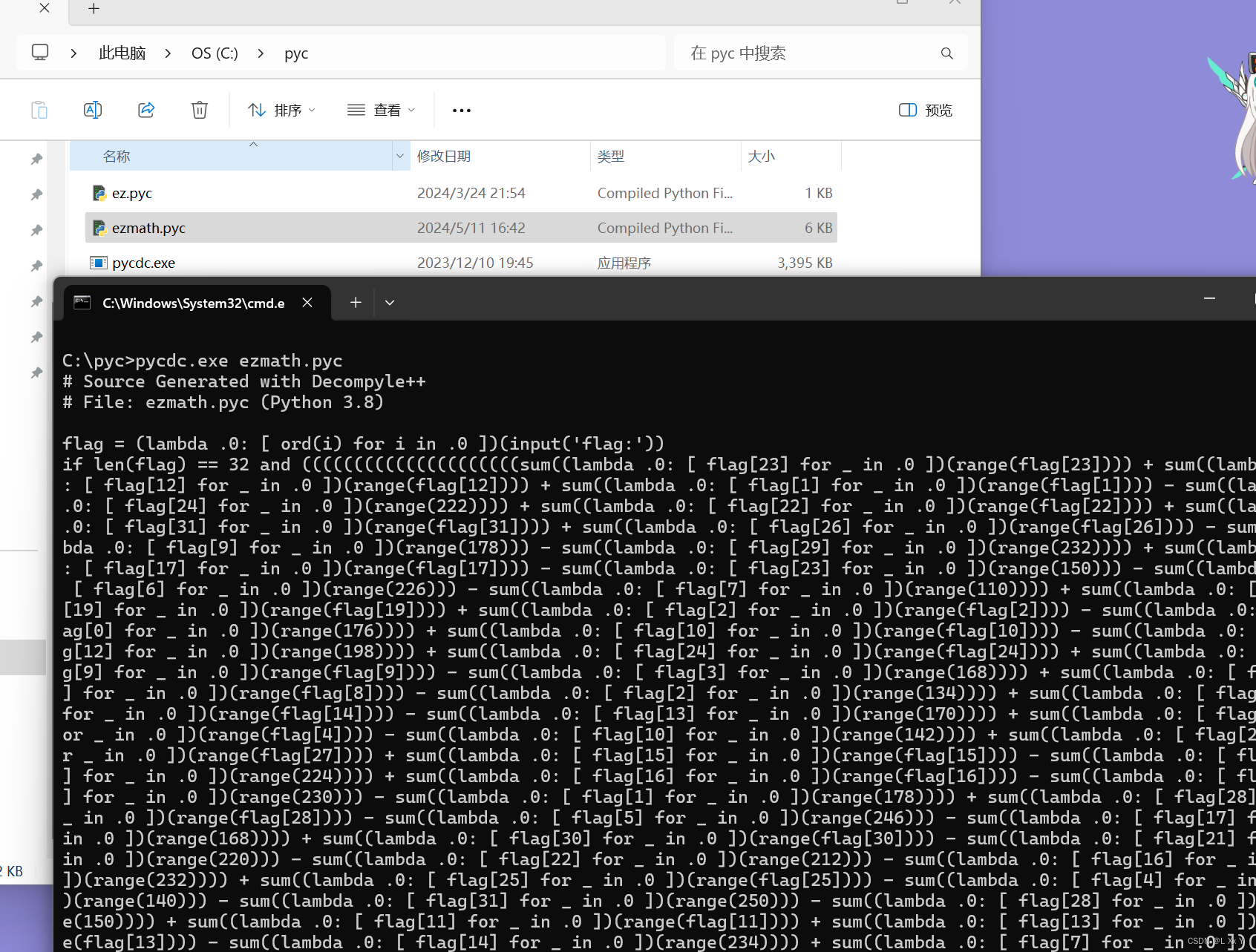 丢给gpt但是我跑不出来
丢给gpt但是我跑不出来
from z3.z3 import Int, Solver, sat
flag = [Int(f"flag[{i}]") for i in range(32)]
solver = Solver()
solver.add(
flag[23] * (flag[23]) +
flag[12] * (flag[12]) +
flag[1] * (flag[1]) -
flag[24] * 222 +
flag[22] * (flag[22]) +
flag[31] * (flag[31]) +
flag[26] * (flag[26]) -
flag[9] * 178 -
flag[29] * 232 +
flag[17] * (flag[17]) -
flag[23] * 150 -
flag[6] * 226 -
flag[7] * 110 +
flag[19] * (flag[19]) +
flag[2] * (flag[2]) -
flag[0] * 176 +
flag[10] * (flag[10]) -
flag[12] * 198 +
flag[24] * (flag[24]) +
flag[9] * (flag[9]) -
flag[3] * 168 +
flag[8] * (flag[8]) -
flag[2] * 134 +
flag[14] * (flag[14]) -
flag[13] * 170 +
flag[4] * (flag[4]) -
flag[10] * 142 +
flag[27] * (flag[27]) +
flag[15] * (flag[15]) -
flag[15] * 224 +
flag[16] * (flag[16]) -
flag[11] * 230 -
flag[1] * 178 +
flag[28] * (flag[28]) -
flag[5] * 246 -
flag[17] * 168 +
flag[30] * (flag[30]) -
flag[21] * 220 -
flag[22] * 212 -
flag[16] * 232 +
flag[25] * (flag[25]) -
flag[4] * 140 -
flag[31] * 250 -
flag[28] * 150 +
flag[11] * (flag[11]) +
flag[13] * (flag[13]) -
flag[14] * 234 +
flag[7] * (flag[7]) -
flag[8] * 174 +
flag[3] * (flag[3]) -
flag[25] * 242 +
flag[29] * (flag[29]) +
flag[5] * (flag[5]) -
flag[30] * 142 -
flag[26] * 170 -
flag[19] * 176 +
flag[0] * (flag[0]) -
flag[27] * 168 +
flag[20] * (flag[20]) -
flag[20] * 212 +
flag[21] * (flag[21]) +
flag[6] * (flag[6]) +
flag[18] * (flag[18]) -
flag[18] * 178 +
297412 == 0
)
if solver.check() == sat:
model = solver.model()
print(model)
solution = [model.evaluate(flag[i] for i in range(32))]
print("Solution found:")
print(solution)
for i in range(32):
print(chr(int(str(model[flag[i]]))), end="")
else:
print("No solution found.")XYCT{Fq7WYGscpuYtTXjnjKoyUTK}
what's this
exe查是lua编译的在线工具https://www.luatool.cn/index.php
直接反编译然后开始处理 ,直接滑倒最后
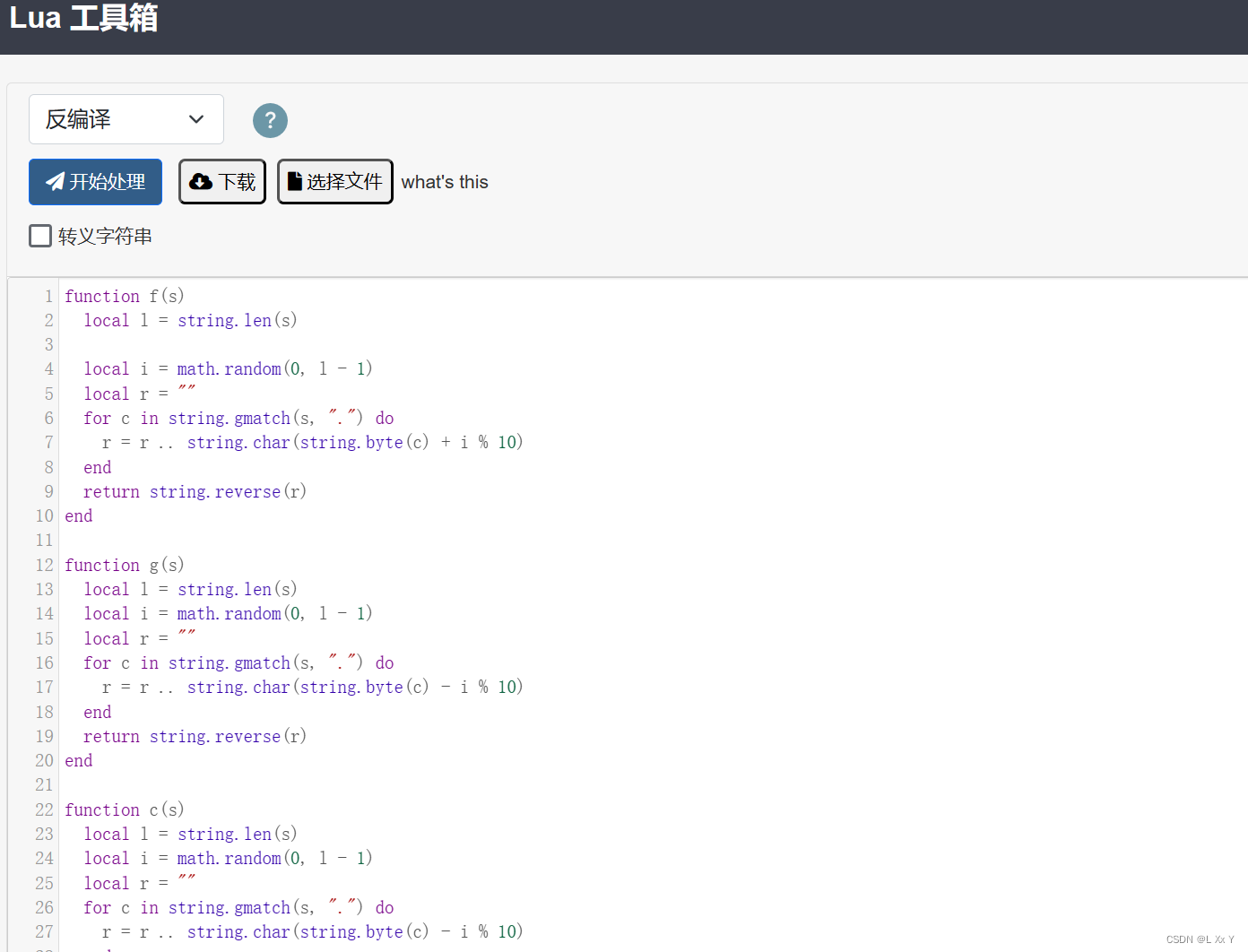
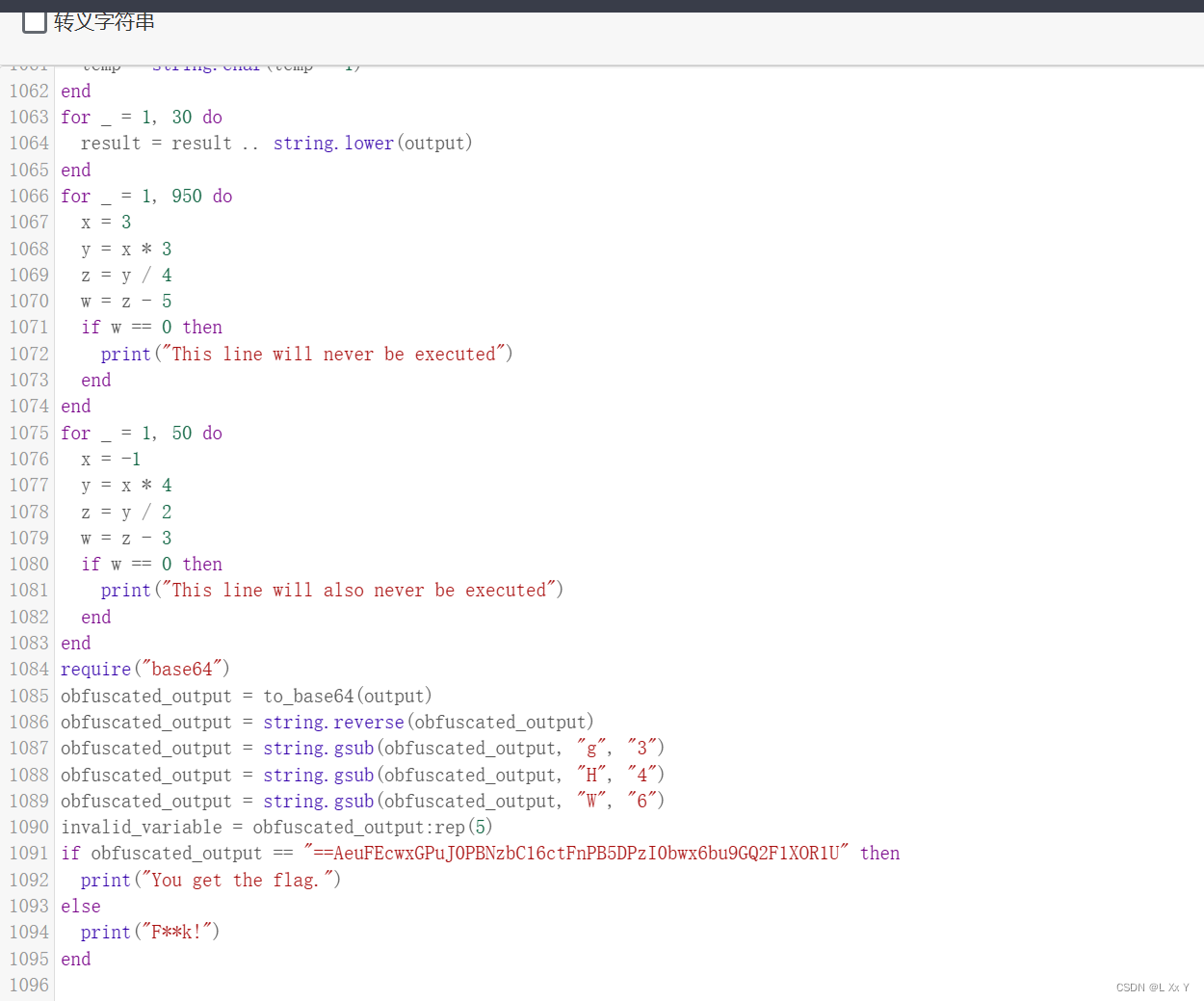
function Xor(num1, num2)
local tmp1 = num1
local tmp2 = num2
local str = ""
repeat
local s1 = tmp1 % 2
local s2 = tmp2 % 2
if s1 == s2 then
str = "0" .. str
else
str = "1" .. str
end
tmp1 = math.modf(tmp1 / 2)
tmp2 = math.modf(tmp2 / 2)
until tmp1 == 0 and tmp2 == 0
return tonumber(str, 2)
end
value = ""
output = ""
i = 1
while true do
local temp = string.byte(flag, i)
temp = string.char(Xor(temp, 8) % 256) //异或8
value = value .. temp
i = i + 1
if i > string.len(flag) then
break
end
end
for _ = 1, 1000 do
x = 3
y = x * 3
z = y / 4
w = z - 5
if w == 0 then
print("This line will never be executed")
end
end
for i = 1, string.len(flag) do
temp = string.byte(value, i)
temp = string.char(temp + 3) //加三
output = output .. temp
end
result = output:rep(10)
invalid_list = {
1,
2,
3
}
for _ = 1, 20 do
table.insert(invalid_list, 4)
end
for _ = 1, 50 do
result = result .. "A"
table.insert(invalid_list, 4)
end
for i = 1, string.len(output) do
temp = string.byte(output, i)
temp = string.char(temp - 1)
end
for _ = 1, 30 do
result = result .. string.lower(output)
end
for _ = 1, 950 do
x = 3
y = x * 3
z = y / 4
w = z - 5
if w == 0 then
print("This line will never be executed")
end
end
for _ = 1, 50 do
x = -1
y = x * 4
z = y / 2
w = z - 3
if w == 0 then
print("This line will also never be executed")
end
end
require("base64")
obfuscated_output = to_base64(output)
obfuscated_output = string.reverse(obfuscated_output)
obfuscated_output = string.gsub(obfuscated_output, "g", "3")
obfuscated_output = string.gsub(obfuscated_output, "H", "4")
obfuscated_output = string.gsub(obfuscated_output, "W", "6")
invalid_variable = obfuscated_output:rep(5)
if obfuscated_output == "==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U" then
print("You get the flag.")
else
print("F**k!")
end
使用xor函数然后对字符串异或8再加3,然后替换
import base64
cipher = "==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U"
new_cipher = cipher[::-1]
new_cipher = new_cipher.replace("3", "g")
new_cipher = new_cipher.replace("4", "H")
new_cipher = new_cipher.replace("6", "W")
def Xor(num1, num2):
tmp1 = num1
tmp2 = num2
str_result = ""
while tmp1 != 0 or tmp2 != 0:
s1 = tmp1 % 2
s2 = tmp2 % 2
if s1 == s2:
str_result = "0" + str_result
else:
str_result = "1" + str_result
tmp1 = tmp1 // 2
tmp2 = tmp2 // 2
return int(str_result, 2)
d_cipher = base64.b64decode(new_cipher)
flag = ""
for char in d_cipher:
flag += chr(Xor(char - 3, 8))
print(flag)





















 607
607











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








