[HGAME 2023 week2]stream

uncompyle6不支持该python脚本
改用pycdc
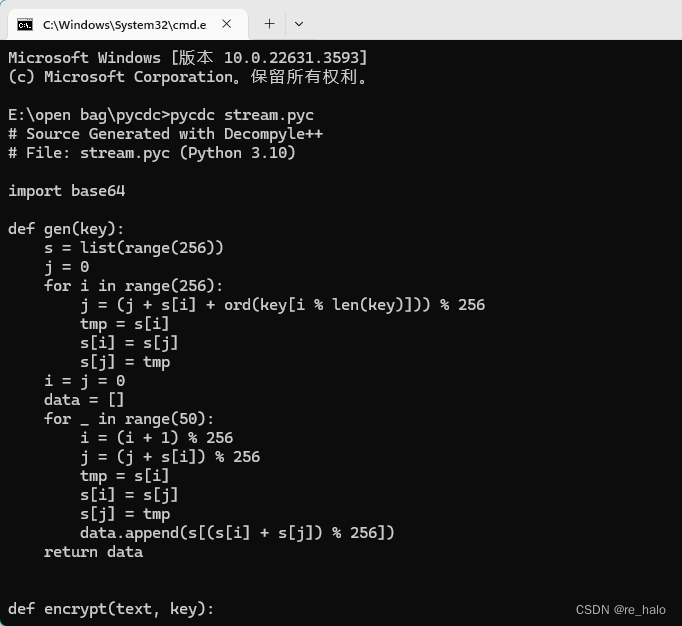
import base64
def gen(key):
s = list(range(256))
j = 0
for i in range(256):
j = (j + s[i] + ord(key[i % len(key)])) % 256
tmp = s[i]
s[i] = s[j]
s[j] = tmp
i = j = 0
data = []
for _ in range(50):
i = (i + 1) % 256
j = (j + s[i]) % 256
tmp = s[i]
s[i] = s[j]
s[j] = tmp
data.append(s[(s[i] + s[j]) % 256])
return data
def encrypt(text, key):
result = ''
for c, k in zip(text, gen(key)):
result += chr(ord(c) ^ k)
result = base64.b64encode(result.encode()).decode()
return result
text = input('Flag: ')
key = 'As_we_do_as_you_know'
enc = encrypt(text, key)
if enc == 'wr3ClVcSw7nCmMOcHcKgacOtMkvDjxZ6asKWw4nChMK8IsK7KMOOasOrdgbDlx3DqcKqwr0hw701Ly57w63CtcOl':
print('yes!')
return None
None('try again...')应该是RC4+base64
逆过来先base解码然后rc4解密

[SWPUCTF 2021 新生赛]PYRE
import hashlib
import base64
def init(OOOOO00O0OO00OO00, OOO00O0000OOO0O00):
OO00O000OOO0OOOOO = 0
OOO00O0000OOO0O00 = hashlib.md5(OOO00O0000OOO0O00.encode()).hexdigest()
OOO00OO0OOO00OOO0 = []
for O0O00OO00OOO0O000 in range(256):
OOOOO00O0OO00OO00.append(O0O00OO00OOO0O000)
OOO00OO0OOO00OOO0.append(OOO00O0000OOO0O00[O0O00OO00OOO0O000 % len(OOO00O0000OOO0O00)])
for O0O00OO00OOO0O000 in range(256):
OO00O000OOO0OOOOO = (OO00O000OOO0OOOOO + OOOOO00O0OO00OO00[O0O00OO00OOO0O000] + ord(OOO00OO0OOO00OOO0[O0O00OO00OOO0O000])) % 256
OOOOO00O0OO00OO00[O0O00OO00OOO0O000] = OOOOO00O0OO00OO00[OO00O000OOO0OOOOO]
OOOOO00O0OO00OO00[OO00O000OOO0OOOOO] = OOOOO00O0OO00OO00[O0O00OO00OOO0O000]
def Encrypt(O0000O0OO00OO00O0, OO0OO00O00O0O00O0):
OOOO0O00O00OOOOO0 = OO0O000O000O0O0O0 = 0
O00O00OOOO00O0000 = ''
for O0OO0O0O0OO0O0OOO in OO0OO00O00O0O00O0:
OOOO0O00O00OOOOO0 = (OOOO0O00O00OOOOO0 + 1) % 256
OO0O000O000O0O0O0 = (OO0O000O000O0O0O0 + O0000O0OO00OO00O0[OOOO0O00O00OOOOO0]) % 256
O0000O0OO00OO00O0[OOOO0O00O00OOOOO0] = O0000O0OO00OO00O0[OO0O000O000O0O0O0]
O0000O0OO00OO00O0[OO0O000O000O0O0O0] = O0000O0OO00OO00O0[OOOO0O00O00OOOOO0]
O0OO0O0OOO00O0O00 = (O0000O0OO00OO00O0[OOOO0O00O00OOOOO0] + O0000O0OO00OO00O0[OO0O000O000O0O0O0]) % 256
OOO000O0OOOOO00O0 = chr(ord(O0OO0O0O0OO0O0OOO) ^ O0000O0OO00OO00O0[(O0000O0OO00OO00O0[OOOO0O00O00OOOOO0] + O0000O0OO00OO00O0[OO0O000O000O0O0O0]) % 256])
O00O00OOOO00O0000 += OOO000O0OOOOO00O0
O00O00OOOO00O0000 = base64.b64encode(O00O00OOOO00O0000.encode())
return O00O00OOOO00O0000
input_str = input('input flag pls:')
s = []
init(s, 'bJLVFYw3WI5ncGez')
if Encrypt(s, input_str).decode() == 'w4s1PUYsJ8OYwpRXVjvDkVPCgzIEJ27Dt2I=':
print('good!')
continue
print('nonono!')
continue应该和上题一样
额,不对
对了,他引入了hashlib库,应该进行了哈希加密
在pycharm中 ctrl+F6 可以重构函数,重命名。vscode是shift+f2
然后就是先按照对加密的实现代码的理解先重命名
额,我先copy下大佬的:
import hashlib
import base64
def init(s2,enc):
a1 = 0
enc = hashlib.md5(enc.encode()).hexdigest()
a2 = []
for enc2 in range(256):
s2.append(enc2)
a2.append(enc[enc2%len(enc)])
for enc2 in range(256):
a1 = ((a1+s2[enc2])+ord(a2[enc2]))%256
s2[a1],s2[enc2] = s2[enc2],s2[a1]
def Encrypt(tmp6,flag):
tmp = 0
tmp2 = 0
tmp3 = ''
for tmp5 in flag:
tmp = (tmp+1)%256
tmp2 = (tmp2 + tmp6[tmp]) % 256
tmp6[tmp2],tmp6[tmp] = tmp6[tmp],tmp6[tmp2]
tmp7 = (tmp6[tmp] + tmp6[tmp2])%256
tmp8 = chr(ord(tmp5)^(tmp6[(tmp6[tmp]+tmp6[tmp2])%256]))
tmp3 += tmp8
tmp3 = base64.b64encode(tmp3.encode())
print(tmp3)
return tmp3
input_str = input('input flag pls:')
s = []
init(s,'bJLVFYw3WI5ncGez')
print(s)
if(Encrypt(s,input_str).decode() == 'w4s1PUYsJ8OYwpRXVjvDkVPCgzIEJ27Dt2I='):
print('good!')
else:
print('nonono!')
SWPU新生赛2021 Reverse部分WriteUp_[swpuctf 2021 新生赛] "astjs-CSDN博客

嗯,那个哈希函数只影响了S盒的初始化
先base解码,知道了flag长度
可以按照动调的思想,调出tmp6的值,中间插入一个print(tmp6[(tmp6[tmp]+tmp6[tmp2])%256],end=’,’)
tmp6[tmp7]
两者异或一下,得到flag。
关于chr函数输出无法显示的字符
[SWPUCTF 2021 新生赛]PYRE_spuwctf pyre-CSDN博客
[MoeCTF 2021]Realezpy

这一看应该python头坏了
额,好吧,是没有问题的
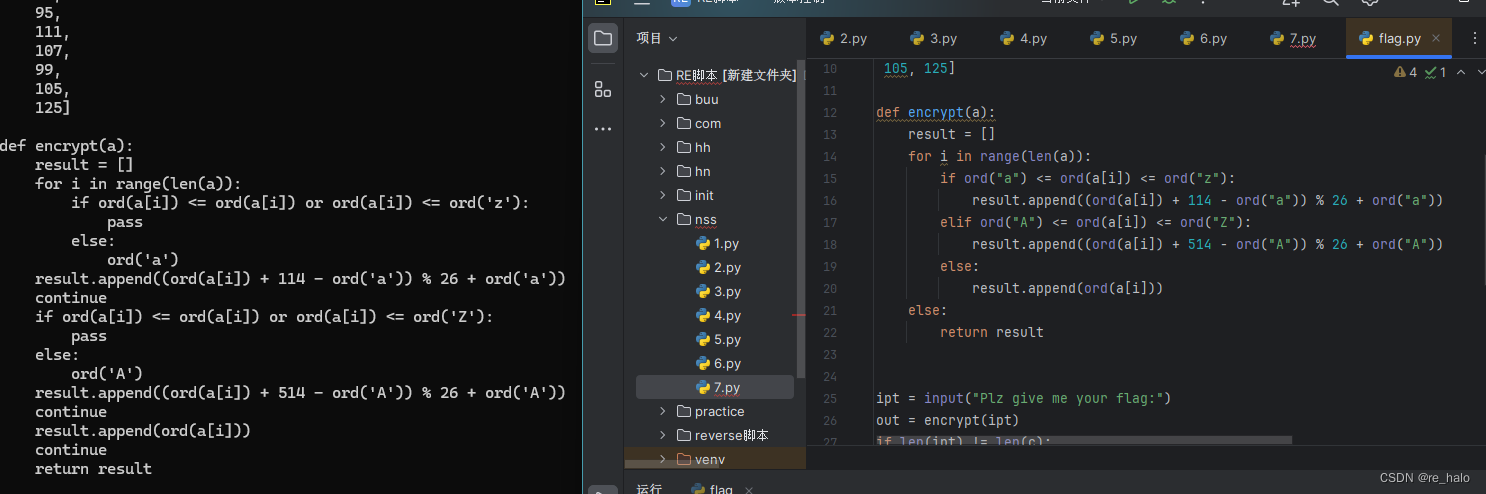
pycdc反编译的还是有点问题,尽量还是用uncompyle6
# uncompyle6 version 3.9.1
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 3.11.8 (tags/v3.11.8:db85d51, Feb 6 2024, 22:03:32) [MSC v.1937 64 bit (AMD64)]
# Embedded file name: Ezpython.py
# Compiled at: 2021-07-28 10:01:40
# Size of source mod 2**32: 931 bytes
import time
c = [119, 121, 111, 109, 100, 112, 123, 74, 105, 100, 114, 48, 120, 95, 49,
99, 95, 99, 121, 48, 121, 48, 121, 48, 121, 48, 95, 111, 107, 99,
105, 125]
def encrypt(a):
result = []
for i in range(len(a)):
if ord("a") <= ord(a[i]) <= ord("z"):
result.append((ord(a[i]) + 114 - ord("a")) % 26 + ord("a"))
elif ord("A") <= ord(a[i]) <= ord("Z"):
result.append((ord(a[i]) + 514 - ord("A")) % 26 + ord("A"))
else:
result.append(ord(a[i]))
else:
return result
ipt = input("Plz give me your flag:")
out = encrypt(ipt)
if len(ipt) != len(c):
print("Wrong lenth~")
exit()
else:
for i in range(len(c)):
if out[i] != c[i]:
print("Plz try again?")
exit()
else:
print("Congratulations!!!")
time.sleep(1)
print("enjoy the beauty of python ~~~ ")
import this
# okay decompiling Ezpython.pyc
类似凯撒的加密,直接写个小脚本
base64
import string
def encode(string,string2):
tmp_str = str()
ret = str()
bit_string_str = string.encode()
remain = len( string ) % 3
remain_str = str()
for char in bit_string_str:
b_char = (bin(char)[2:])
b_char = '0'*(8-len(b_char)) + b_char
tmp_str += b_char
for i in range(len(tmp_str)//6):
temp_nub = int(tmp_str[i*6:6*(i+1)],2)
ret += string2[temp_nub]
if remain==2:
remain_str = tmp_str[-4:] + '0'*2
temp_nub = int(remain_str,2)
ret += string2[temp_nub] + "="
elif remain==1:
remain_str = tmp_str[-2:] + '0'*4
temp_nub = int(remain_str,2)
ret += string2[temp_nub] + "="*2
return ret.replace("=","")
res = encode(input(),string.ascii_uppercase+string.ascii_lowercase+string.digits+'+/')
if res == "TlNTQ1RGe2Jhc2U2NCEhfQ":
print("good!")
else:
print("bad!")[HNCTF 2022 Week1]你知道什么是Py嘛?
s = str(input("please input your flag:"))
arr=[29, 0, 16, 23, 18, 61, 43, 41, 13, 28, 88, 94, 49, 110, 66, 44, 43, 28, 91, 108, 61, 7, 22, 7, 43, 51, 44, 46, 9, 18, 20, 6, 2, 24]
if(len(s)!=35 or s[0]!='N'):
print("error")
exit(0)
# s=NSSCTF{
for i in range(1,len(s)):
if(ord(s[i-1])^ord(s[i])!=arr[i-1]):
print("error!")
exit(0)
print("right!")
arr=[29, 0, 16, 23, 18, 61, 43, 41, 13, 28, 88, 94, 49, 110, 66, 44, 43, 28, 91, 108, 61, 7, 22, 7, 43, 51, 44, 46, 9, 18, 20, 6, 2, 24]
flag=[0]*35
flag[0]=ord('N')
for i in range(1,35):
flag[i]=(arr[i-1]^flag[i-1])
print(flag)
for i in range(len(flag)):
print(chr(flag[i]),end='')
# NSSCTF{Pyth0n_1s_th3_best_l@nguage}
# 也可以通过爆破
flag='N'
arr=[29, 0, 16, 23, 18, 61, 43, 41, 13, 28, 88, 94, 49, 110, 66, 44, 43, 28, 91, 108, 61, 7, 22, 7, 43, 51, 44, 46, 9, 18, 20, 6, 2, 24]
for i in range(34):
for j in range(128):
if (ord(flag[i])^j==arr[i]):
flag+=chr(j)
print(flag)看看能不能用pwntools爆破,但那是对可执行文件的爆破
[FSCTF 2023]ez_pycxor
都是好奇怪的文件头

flag = input('plz input your flag:')
encoded_flag = []
key = 'FUTURESTARS'
ciphertxt = [
168,
169,
185,
170,
160,
157,
197,
132,
226,
134,
134,
145,
255,
242,
130,
139,
234,
140,
180,
229,
179,
246,
243,
181,
183,
182,
249,
163,
254,
189,
246,
166]
for i in range(len(flag)):
encoded_flag.append((ord(flag[i]) ^ 168) + i)
for i in range(len(encoded_flag)):
if i % 2 == 0:
encoded_flag[i] ^= ord(key[i % 11])
if i % 2 == 1:
encoded_flag[i] ^= ord(key[i % 11])
if encoded_flag == ciphertxt:
print('OK! You have crack it!')enc=[
168,
169,
185,
170,
160,
157,
197,
132,
226,
134,
134,
145,
255,
242,
130,
139,
234,
140,
180,
229,
179,
246,
243,
181,
183,
182,
249,
163,
254,
189,
246,
166]
key='FUTURESTARS'
for i in range(len(enc)):
if i % 2 == 0:
enc[i] ^= ord(key[i % 11])
if i % 2 == 1:
enc[i] ^= ord(key[i % 11])
flag=''
for i in range(len(enc)):
flag+=chr((enc[i]-i)^168)
print(flag)
# FSCTF{8a3ccd61ab7ff9e87acb9c9d1}引入了别的库



使用不对应版本python解包好像这个文件夹就是空的
但那个库文件应该是在这个文件夹里面
所以需要切换到Python3.7去,要用到conda




















 1430
1430











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








