rsa
e = 1
已知c,n,e且e=1爆破求值
m^1 mod n= c
m=k*n +c
import gmpy2 from Crypto.Util.number import * n = 86852141002447122652359289590048222078290272479429784699390143159809850622764995366174857656831774326418252758920004900401199143615586594447957990113364133299015845307213574314824735469132663035888652008111166877529344917641300929086286765037702038227706621339349983208784491420932326937356459917347756088903 e = 1 c = 5789891771182247663118797394223967432043383747559995111258322306735941755414199533224746114787130030399283853213179357492479237434954850004217757275686637243397309781146425188899498063745121936635373814428119010489926496514614187463963312475706520140518560450387486158638256652573234980999220291504908585681 m = '' for i in range(10 ** 500): m = n * i + c if b'flag'in long_to_bytes(m): break #也可以用while,此处用while更方便 ''' while b'flag'in long_to_bytes(m): m = n * i + c ''' print(long_to_bytes(m))
b"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAHere_is_your flag:---->flag{very_easy_to_solve_didn't_it??????}ZZZZZZZZZZZZZZBBBBBBBBBBBBBBBBBBBBBBB"
02
p+q : 0x1232fecb92adead91613e7d9ae5e36fe6bb765317d6ed38ad890b4073539a6231a6620584cea5730b5af83a3e80cf30141282c97be4400e33307573af6b25e2ea
(p+1)*(q+1) : 0x5248becef1d925d45705a7302700d6a0ffe5877fddf9451a9c1181c4d82365806085fd86fbaab08b6fc66a967b2566d743c626547203b34ea3fdb1bc06dd3bb765fd8b919e3bd2cb15bc175c9498f9d9a0e216c2dde64d81255fa4c05a1ee619fc1fc505285a239e7bc655ec6605d9693078b800ee80931a7a0c84f33c851740
e : 0xe6b1bee47bd63f615c7d0a43c529d219
d : 0x2dde7fbaed477f6d62838d55b0d0964868cf6efb2c282a5f13e6008ce7317a24cb57aec49ef0d738919f47cdcd9677cd52ac2293ec5938aa198f962678b5cd0da344453f521a69b2ac03647cdd8339f4e38cec452d54e60698833d67f9315c02ddaa4c79ebaa902c605d7bda32ce970541b2d9a17d62b52df813b2fb0c5ab1a5
enc_flag : 0x50ae00623211ba6089ddfae21e204ab616f6c9d294e913550af3d66e85d0c0693ed53ed55c46d8cca1d7c2ad44839030df26b70f22a8567171a759b76fe5f07b3c5a6ec89117ed0a36c0950956b9cde880c575737f779143f921d745ac3bb0e379c05d9a3cc6bf0bea8aa91e4d5e752c7eb46b2e023edbc07d24a7c460a34a9a
from Crypto.Util.number import *
import gmpy2
t = 0x1232fecb92adead91613e7d9ae5e36fe6bb765317d6ed38ad890b4073539a6231a6620584cea5730b5af83a3e80cf30141282c97be4400e33307573af6b25e2ea
s = 0x5248becef1d925d45705a7302700d6a0ffe5877fddf9451a9c1181c4d82365806085fd86fbaab08b6fc66a967b2566d743c626547203b34ea3fdb1bc06dd3bb765fd8b919e3bd2cb15bc175c9498f9d9a0e216c2dde64d81255fa4c05a1ee619fc1fc505285a239e7bc655ec6605d9693078b800ee80931a7a0c84f33c851740
e = 0xe6b1bee47bd63f615c7d0a43c529d219
d = 0x2dde7fbaed477f6d62838d55b0d0964868cf6efb2c282a5f13e6008ce7317a24cb57aec49ef0d738919f47cdcd9677cd52ac2293ec5938aa198f962678b5cd0da344453f521a69b2ac03647cdd8339f4e38cec452d54e60698833d67f9315c02ddaa4c79ebaa902c605d7bda32ce970541b2d9a17d62b52df813b2fb0c5ab1a5
c = 0x50ae00623211ba6089ddfae21e204ab616f6c9d294e913550af3d66e85d0c0693ed53ed55c46d8cca1d7c2ad44839030df26b70f22a8567171a759b76fe5f07b3c5a6ec89117ed0a36c0950956b9cde880c575737f779143f921d745ac3bb0e379c05d9a3cc6bf0bea8aa91e4d5e752c7eb46b2e023edbc07d24a7c460a34a9a
n = s - t - 1
print(long_to_bytes(pow(c, d, n)))
b'flag{cc7490e-78ab-11e9-b422-8ba97e5da1fd}'
03(已知n, e, dp, c)
from Crypto.Util.number import *
import gmpy2
n = 112175479714624818333695420235113121999253705121349034178095395776541578094363845388559590909361312410962099699881132411226346575237836053958453543906356619404909584589523034552316763130953004414064225313165485246176626930538343808535067926125049424274746489884590510228322575593062361327323956355018481606787
e = 65537
dp = 776332078153466902010331807629418087664139388392009242255833676093458381495736233562078206906276100477481877005559333154350072579336625440878501990952449
c = 29903204137287472183084078669621828153098745111154184308805918211775025708195435433119346070335075079723952901344436463613049125728645574344500681384720020052000458282929108115757637347220315188433383691840513855197665647546580597290143994943183285021863890508250103436224410969338201721816727848334445692915
t = e * dp
for i in range(1, t):
if (t - 1) % i == 0:
p = (t - 1) // i + 1
if n % p == 0:
m = pow(c, dp, p)
print(long_to_bytes(m))
# q = n // p
# phi = (q - 1) * (p - 1)
# d = gmpy2.invert(e, phi)
# m = pow(c, d, n)
# m = long_to_bytes(m)
# print(m)
04
题目:
from Crypto.Util.number import *
import gmpy2
from secret import flag
m = bytes_to_long(flag)
p = getPrime(256)
q = getPrime(256)
r = getPrime(256)
n1 = q*p
n2 = q*r
e = 65535
c1 = pow(m,e,n1)
c2 = pow(m,e,n2)
print("n1:"+str(n1))
print("n2:"+str(n2))
print("c1:"+str(c1))
print("c2:"+str(c2))
# n1:9116072673585619132111895403642168497263071691827949298017531396382827298782303749867264589825807183797020472968464660582686417921434431658511530041563901
# n2:9676471733476806363827533442570967957871359923261140318101161479170327996682930238809368950608051282208303548660410073403065643718187781752130771337383629
# c1:8824462894263393560944306775755201891143487603309462108944270494215822172733677936731309917183407096166230876035017809219712288813600390461631853255239986
# c2:5015105118262293349286521985688699702504989063271993070991789714282577934372078450119431649574609758836593485914932778436203219098204688867565801371889451题解:
注意先看已知,已知条件实在做不出来再看逻辑
import gmpy2
from Crypto.Util.number import *
n1 = 9116072673585619132111895403642168497263071691827949298017531396382827298782303749867264589825807183797020472968464660582686417921434431658511530041563901
n2 = 9676471733476806363827533442570967957871359923261140318101161479170327996682930238809368950608051282208303548660410073403065643718187781752130771337383629
c1 = 8824462894263393560944306775755201891143487603309462108944270494215822172733677936731309917183407096166230876035017809219712288813600390461631853255239986
c2 = 5015105118262293349286521985688699702504989063271993070991789714282577934372078450119431649574609758836593485914932778436203219098204688867565801371889451
e = 65535
q = gmpy2.gcd(n1, n2)
p = n1 // q
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c1, d, n1)
print(m)
print(long_to_bytes(m))
# r = n2 // q
# phi2 = (r - 1) * (q - 1)
# d2 = gmpy2.invert(e, phi2)#e, phi2不互素所以这种是错的
# m2 = pow(c2, d2, n2)
# print(m2)
# print(long_to_bytes(m2))b'DASCTF{09e6e620057c5df8bd6b95042f8ac11b}'
05(与04同类型)
题目:
from Crypto.Util.number import *
from random import choice, shuffle
import gmpy2
from math import sqrt
from secret import flag
def get_list(n):
my_list, cnt, st = [], 0, [False]*n*10
for i in range(2, n+1):
if not st[i]:
my_list.append(i)
cnt += 1
for j in range(n):
if my_list[j] * i > n:
break
st[my_list[j] * i] = True
if i % my_list[j] == 0:
break
return my_list
def get_prime(_, n1, n2, bound):
my_list = get_list(n1)
shuffle(my_list)
my_list = my_list[:n2]
while True:
p = 1
while True:
p *= choice(my_list)
if p.bit_length() > bound:
break
p += _
if isPrime(p):
return p
def start():
bound = 500
num1 = pow(10, 6)
num2 = num1//20
p1 = get_prime(1, num1, num2, bound)
q1 = getPrime(bound)
n1 = p1 * q1
q2 = get_prime(-1, round(sqrt(num1)), round(sqrt(num2)), bound)
p2 = getPrime(bound)
n2 = p2 * q2
r = getPrime(bound)
n = p1 * q2 * r
e = 65537
m = bytes_to_long(flag)
c = pow(m, e, n)
return (p1, q1, q2, p2, n1, n2, n, e, c)
p1, q1, q2, p2, n1, n2, n, e, c = start()
print(f"n1 = {n1}")
print(f"n2 = {n2}")
print(f"n = {n}")
print(f"e = {e}")
print(f"c = {c}")
# n1 = 32509937920108452706099222978031198053046977240732923211027190799808712561390169155364841105194594233029580635167477810369193036879340840248068937008881313273342215826772787212231135075968921423550014486660825365236823778400273212026560515936255396339715728338833037201922656923337487213841107397075109
# n2 = 217756212730007717890554673534036379275177917547723643270840770602902290982788533846026151243642123203368841503650943535194984352879255942349438336124321871462817622245239641040894724527645158421556848873893654612288130133028946952382061938109590350001187645000237098346579285177663299700021223291447809
# n = 1303560114489951493697516509057148146923068582040771113843750330756919107450213229633558065365345194729219444852720792530763214472377936067300874720520523005684541172840550215310671582342621150219685855499438258138549174096365852739825770183435917695991524687436832099301415241336313838164102830956407279
# e = 65537
# c = 918883620925282244187871610198318634655335345295801403926746762099044495103442395097077438644224283980575779027887445228375133305078827716605344834149133947176228968779226528965957353384807439927016614228197559016244781579825667932554040052318134689224265126254585084241072477528873133866090557928603209题解:
from Crypto.Util.number import *
from random import choice, shuffle
import gmpy2
from math import sqrt
from secret import *
n1 = 32509937920108452706099222978031198053046977240732923211027190799808712561390169155364841105194594233029580635167477810369193036879340840248068937008881313273342215826772787212231135075968921423550014486660825365236823778400273212026560515936255396339715728338833037201922656923337487213841107397075109
n2 = 217756212730007717890554673534036379275177917547723643270840770602902290982788533846026151243642123203368841503650943535194984352879255942349438336124321871462817622245239641040894724527645158421556848873893654612288130133028946952382061938109590350001187645000237098346579285177663299700021223291447809
n = 1303560114489951493697516509057148146923068582040771113843750330756919107450213229633558065365345194729219444852720792530763214472377936067300874720520523005684541172840550215310671582342621150219685855499438258138549174096365852739825770183435917695991524687436832099301415241336313838164102830956407279
e = 65537
c = 918883620925282244187871610198318634655335345295801403926746762099044495103442395097077438644224283980575779027887445228375133305078827716605344834149133947176228968779226528965957353384807439927016614228197559016244781579825667932554040052318134689224265126254585084241072477528873133866090557928603209
p1 = gmpy2.gcd(n, n1)
q2 = gmpy2.gcd(n, n2)
print(p1)
print(q2)
r = n // (p1 * q2)
print(r)
phi = (p1 - 1) * (q2 - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(m)
print(long_to_bytes(m))06(e, phi不互素)
import gmpy2
from Crypto.Util.number import *
# from flag import flag
from gmpy2 import iroot
e = 20
p = 89090419201867706773677116278097072719219629442258176901290128288852916511087
q = 104220742700548365653310196584523638658755653860418843622934901235800356935437
n = p*q
# m = bytes_to_long(flag)
# c = pow(m,e,n)
# print('c =', c)
c = 8526560700479785023678696814235746244655205264378920642471337039269088704511789828170943071682571641052151045423212433923261183650552543816419532887542668
phi = (p-1)*(q-1)
# t = gmpy2.gcd(e, phi)
# print(t)#t = 4
e = e//4
d = inverse(e,phi)
m4 = pow(c,d,n)
m = iroot(m4,4)[0]
flag = long_to_bytes(m)
print(flag)
#b'flag{this_flag}'哈希爆破
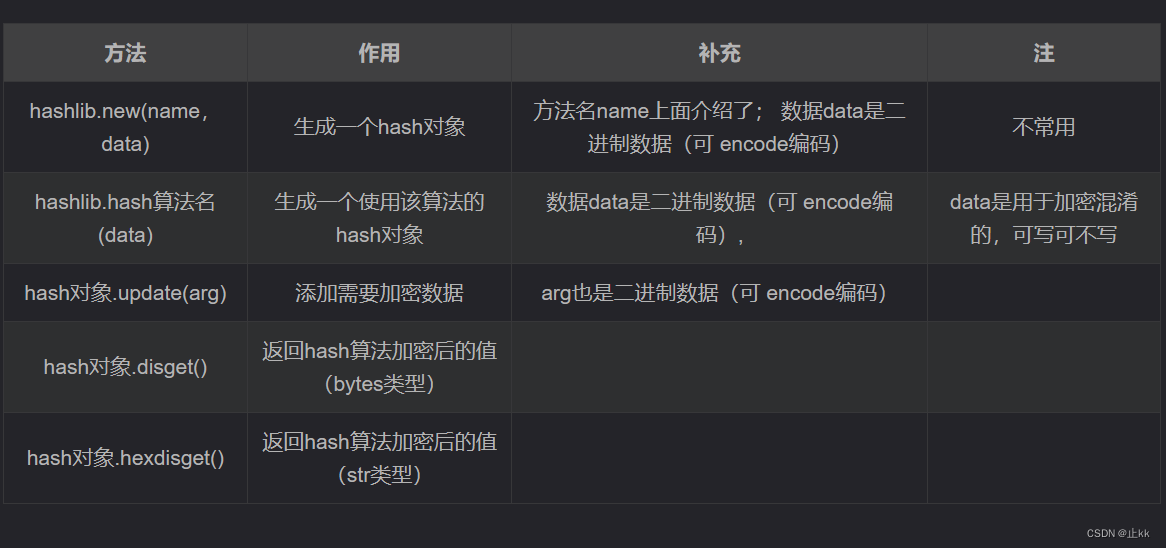
参考:7.hashlib模块与加密解密_hashlib.md5解密_py~豆腐的博客-CSDN博客
sha256
SHA-256是用32位字计算的哈希函数。
proof_of_work
题目链接:nc 59.110.20.54:5526 Build your own function to solve proof_of_work!
nc以后
sha256(XXXX+Ce7rw0H6wMVlj9Ze) == f27e597aa763e03eba65ff94e6adf150edc63caa0c24372c5d7e917b31b5a10f Give me XXXX:
``
import hashlib
import string
z = ''
tx = '' #dic = string.ascii_letters + string.digits (这里可以用dic会更加简便)
for i in string.ascii_letters + string.digits:
for j in string.ascii_letters + string.digits: #注意连个字符串用‘+’连接
for m in string.ascii_letters + string.digits:
for n in string.ascii_letters + string.digits:
tx = str(i) + str(j) + str(m) +str(n) + "Ce7rw0H6wMVlj9Ze"
sha256 = hashlib.sha256()
sha256.update(tx.encode('utf-8'))
z = sha256.hexdigest()
if z == "f27e597aa763e03eba65ff94e6adf150edc63caa0c24372c5d7e917b31b5a10f":
print(tx)
print(z)
4Ei3Ce7rw0H6wMVlj9Ze
f27e597aa763e03eba65ff94e6adf150edc63caa0c24372c5d7e917b31b5a10f
MD5
data='Boom_MD5' flag=MD5(data) print(flag) #0618ac93d4631df725bceea74d0’*‘**’ * *
``
import hashlib
import string
flag = ''
t = ''
for i in range(32, 128):
for j in range(32, 128):
for m in range(32, 128):
for n in range(32, 128):
t = 'Boom_MD5' + chr(i) + chr(j) + chr(m) +chr(n)
MD5 = hashlib.md5()
MD5.update(t.encode('utf-8'))
flag = MD5.hexdigest()
if flag[0:27] == "0618ac93d4631df725bceea74d0":
print(t)
print(flag)
Boom_MD5_NSS 0618ac93d4631df725bceea74d0fe071
异或运算
异或(xor)
异或(xor)是一个数学运算符。它应用于逻辑运算。异或的数学符号为“⊕”,计算机符号为“xor”。其运算法则为:
a⊕b = (¬a ∧ b) ∨ (a ∧¬b)
如果a、b两个值不相同,则异或结果为1。如果a、b两个值相同,异或结果为0。
异或也叫半加运算,其运算法则相当于不带进位的二进制加法:二进制下用1表示真,0表示假,则异或的运算法则为:0⊕0=0,1⊕0=1,0⊕1=1,1⊕1=0(同为0,异为1),这些法则与加法是相同的,只是不带进位,所以异或常被认作不进位加法。
注意,a^b^b=a
举例:
3⊕6= ?
3,6二进制分别为:0011,0110结果0101再转换为十进制为5,故结果为5
参考资料来源:异或_百度百科 (baidu.com)
01
题目
key = b"sourcecode" * 2023
for i in range(len(flag)):
print(flag[i] ^ key[i], end='0')
# 5904205403803703005903205400029012070110190170100001001200014025010120190602902901600010019070150240
对c手动去除0(有别的方法更好,但是我不会), 得到
c=[59,42,54,38,37,30,59,32,54,0,29,12,7,11,19,17,10,0,10,12,0,14,25,1,12,19,6,29,29,16,0,10,19,7,15,24]
解题
因为这里的字符是一个一个异或的,若用xor,这样得到的结果将会是这样b'H'b'E'b'C'b'T'b'F'b'{'b'X'b'O'b'R'b'e'b'n'b'c'b'r'b'y'b'p'b't'b'i'b'o'b'n'b'i'b's'b'a'b'l'b's'b'o'b'v'b'e'b'r'b'y'b'u'b's'b'e'b'f'b'u'b'l'b'}'
字符转ascii用的是 ord 不是 int
ascii转字符同理是用的 chr 而不是str
大整数里用long_to_bytes比较多
xor()是个pwn库写好的函数,^是python里自带的运算
c = [59,42,54,38,37,30,59,32,54,0,29,12,7,11,19,17,10,0,10,12,0,14,25,1,12,19,6,29,29,16,0,10,19,7,15,24]
key = b"sourcecode" * 2023
for i in range(len(c)):
print(chr(c[i] ^ key[i]),end='')HECTF{XORencryptionisalsoveryuseful}
OTPTwice
题目
from pwn import xor
from os import urandom
flag = b"SYC{Al3XEI_FAKE_FLAG}"
# step0: key generation & distribution
def s0(msg):
k1,k2 = [urandom(len(msg)) for _ in "__"]
return k1,k2
#
# step1: Alice encrypt M, and send it to Bob
def s1(msg,k1):
c1 = xor(msg,k1)
return c1
# step2: Bob encrypt c1, and send it to Alice
def s2(msg,k2):
c2 = xor(msg,k2)
return c2
# step3: Alice decrypt c2, and send it to Bob.
def s3(msg,k1):
c3 = xor(msg,k1)
return c3
# step4: Bob decrypt c3, get M.
def s4(msg,k2):
m_ = xor(msg,k2)
return m_
#代码解答 from pwn import xor c1 = b'\xdbi\xab\x8d\xfb0\xd3\xfe!\xf8Xpy\x80w\x8c\x87\xb9' #属于byte类型 c2 = b'o\xb0%\xfb\xdb\x0e\r\x04\xde\xd1\x9a\x08w\xda4\x0f\x0cR' c3 = b'\xe7\x80\xcd\ria\xb2\xca\x89\x1a\x9d;|#3\xf7\xbb\x96' k2 = xor(c1, c2) flag = xor(c3, k2)#xor使bytes类型直接异或,否则返回结果将是一个整数,需要多进行一步 chr() print(flag)
b'SYC{I_l0v3_Crypt0}'
中国剩余定理
原理
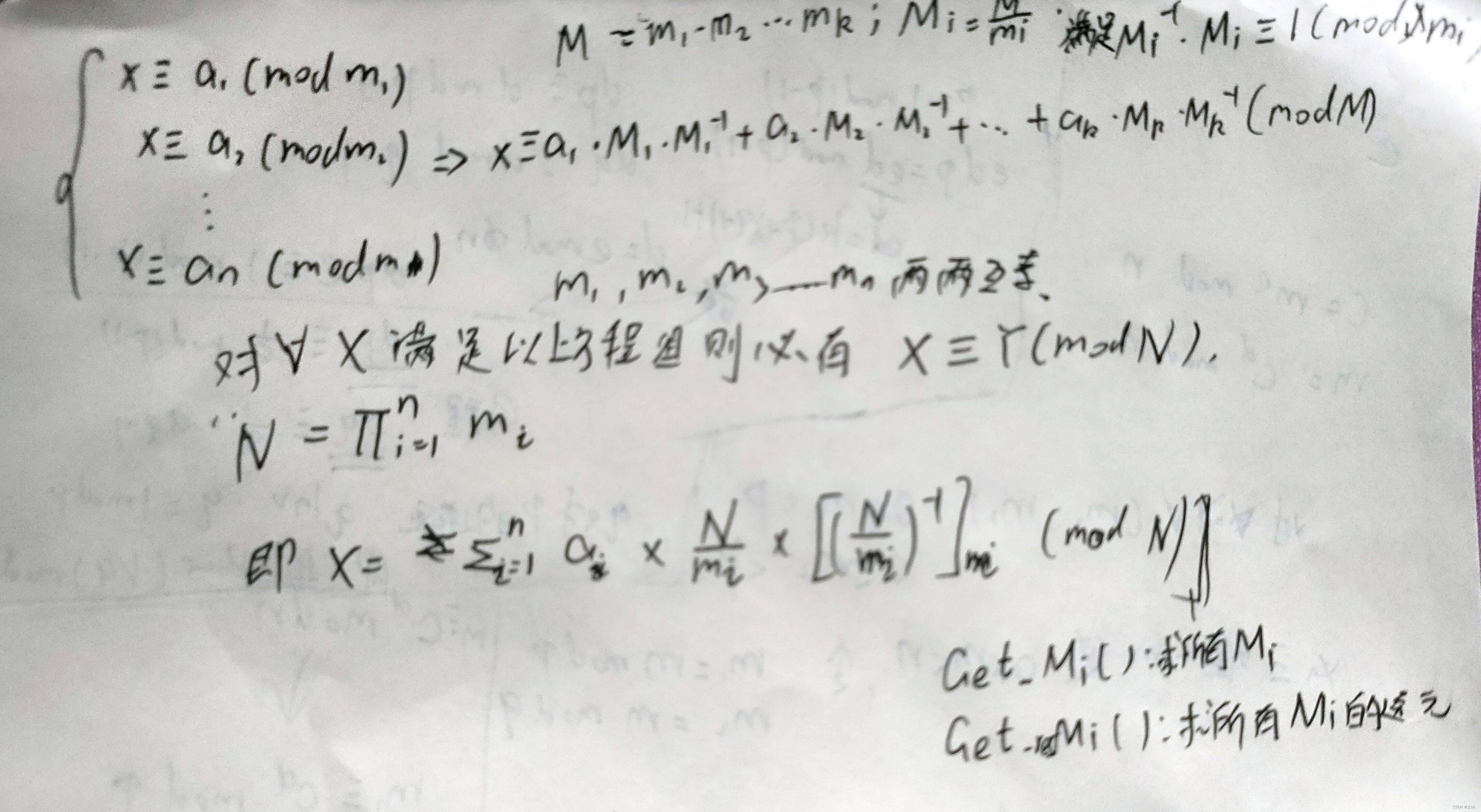
easy_classic
题目:
from Crypto.Util.number import *
import os
flag = b"SYC{Al3XEI_FAKE_FLAG}"
pad = lambda msg,padlen: msg+os.urandom(padlen-len(msg))
flag = pad(flag,32)
print(len(flag))
p = [getPrime(16) for _ in range(32)]
c = [bytes_to_long(flag)%i for i in p]
print('p=',p)
print('c=',c)
'''
p= [58657, 47093, 47963, 41213, 57653, 56923, 41809, 49639, 44417, 38639, 39857, 53609, 55621, 41729, 60497, 44647, 39703, 55117, 44111, 57131, 37747, 63419, 63703, 64007, 46349, 39241, 39313, 44909, 40763, 46727, 34057, 56333]
c= [36086, 4005, 3350, 23179, 34246, 5145, 32490, 16348, 13001, 13628, 7742, 46317, 50824, 23718, 32995, 7640, 10590, 46897, 39245, 16633, 31488, 36547, 42136, 52782, 31929, 34747, 29026, 18748, 6634, 9700, 8126, 5197]
'''
用到的相关函数:
lambda 函数特点:
- lambda 函数是匿名的,它们没有函数名称,只能通过赋值给变量或作为参数传递给其他函数来使用。
- lambda 函数通常只包含一行代码,这使得它们适用于编写简单的函数。
lambda 语法格式:
lambda arguments: expression
lambda是 Python 的关键字,用于定义 lambda 函数。arguments是参数列表,可以包含零个或多个参数,但必须在冒号(:)前指定。expression是一个表达式,用于计算并返回函数的结果。
index()方法语法:
str.index(substring, beg=0, end=len(string))
检测字符串中是否包含子字符串 str ,如果指定 beg(开始) 和 end(结束) 范围,则检查是否包含在指定范围内
index返回值
如果包含子字符串返回开始的索引值,否则抛出异常。
题解:
题解:
from functools import reduce
from Crypto.Util.number import *
import gmpy2
p = [58657, 47093, 47963, 41213, 57653, 56923, 41809, 49639, 44417, 38639, 39857, 53609, 55621, 41729, 60497, 44647, 39703, 55117, 44111, 57131, 37747, 63419, 63703, 64007, 46349, 39241, 39313, 44909, 40763, 46727, 34057, 56333]
c = [36086, 4005, 3350, 23179, 34246, 5145, 32490, 16348, 13001, 13628, 7742, 46317, 50824, 23718, 32995, 7640, 10590, 46897, 39245, 16633, 31488, 36547, 42136, 52782, 31929, 34747, 29026, 18748, 6634, 9700, 8126, 5197]
def CRT(moudle,a):
M = reduce((lambda x,y : x * y),moudle)#
result = 0
for mi in moudle:
Mi = M // mi
inv_Mi = gmpy2.invert(Mi,mi)
result = (result + a[moudle.index(mi)] * Mi * inv_Mi) % M
return result % M
m = 0
m = CRT(p, c)
print(long_to_bytes(m))b'SYC{CRT_1s_s0_ju1cy!}]mC\x9c\xf9C/\xfc\xb8t\x16'
中国剩余定理与rsa的结合使用
原理:
 .
.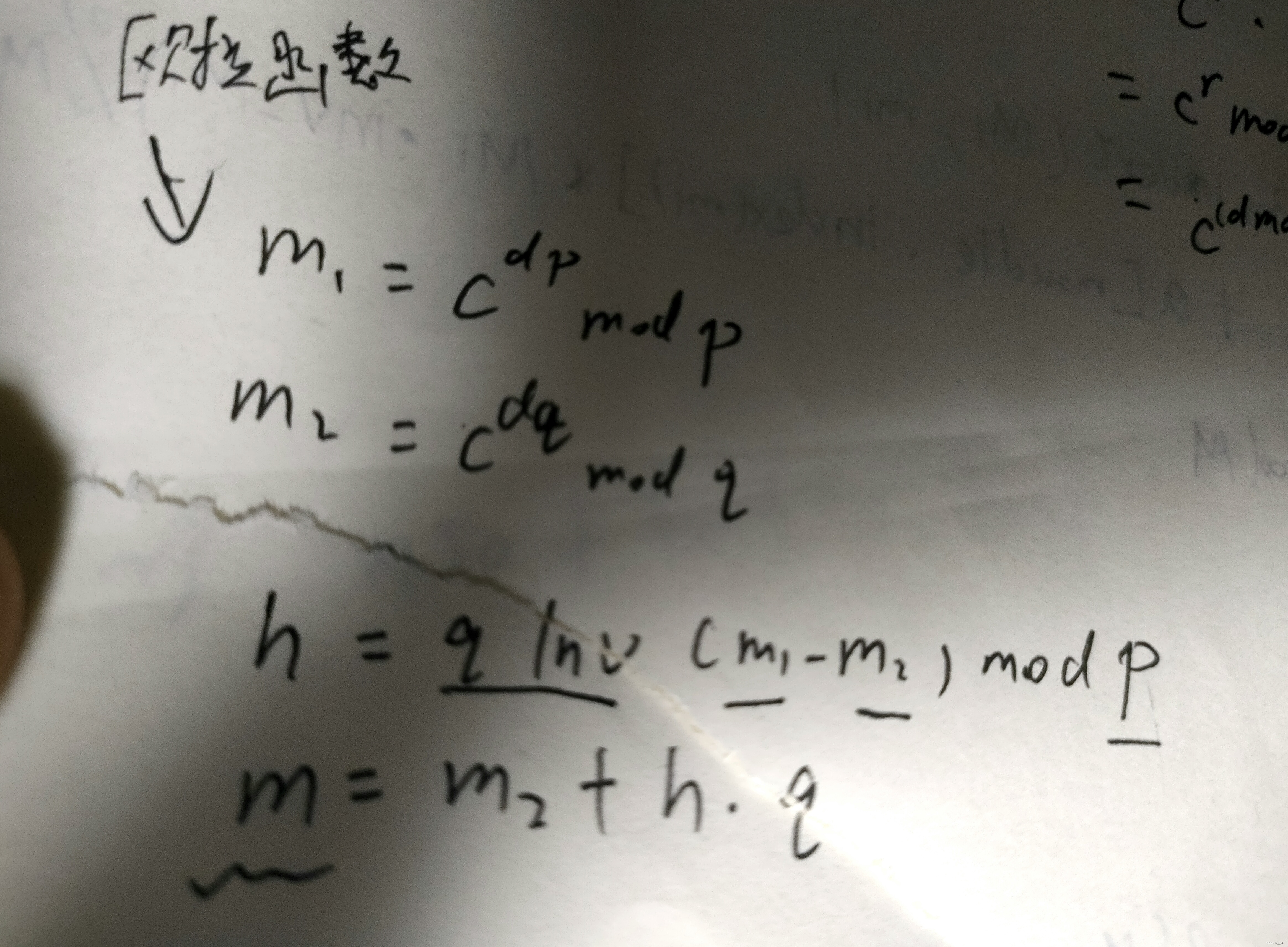





















 3206
3206











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








