PowerShell 是一个微软开发的自动化任务和配置管理系统。它基于 .NET 框架,由命令行语言解释器(shell)和脚本语言组成。
PowerShell 提供对 COM (组件对象模型) 和 WMI (Windows 管理规范) 的完全访问,从而允许系统管理员在本地或远程 Windows 系统中 执行管理任务,以及对 WS-Management 和 CIM(公共信息模型)的访问,实现对远程 Linux 系统和网络设备的管理。
通过这个框架,管理任务基本上由称为 cmdlets(发音 command-lets)的 .NET 类执行。就像 Linux 的 shell 脚本一样,用户可以通过按照一定的规则将一组 cmdlets 写入文件来制作脚本或可执行文件。这些脚本可以用作独立的命令行程序或工具。
1.环境:kali linux 2018.1 , powershell_6.0.1-1.debian.9_amd64.deb
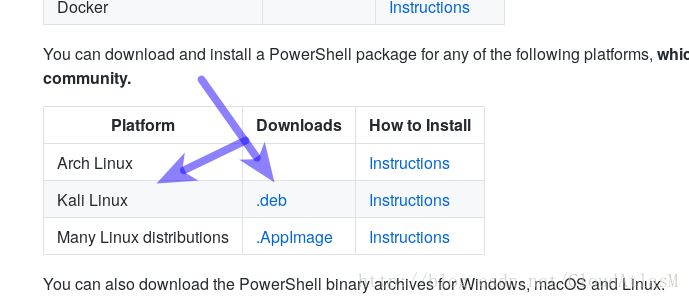
2.下载(科学上网):https://github.com/PowerShell/PowerShell
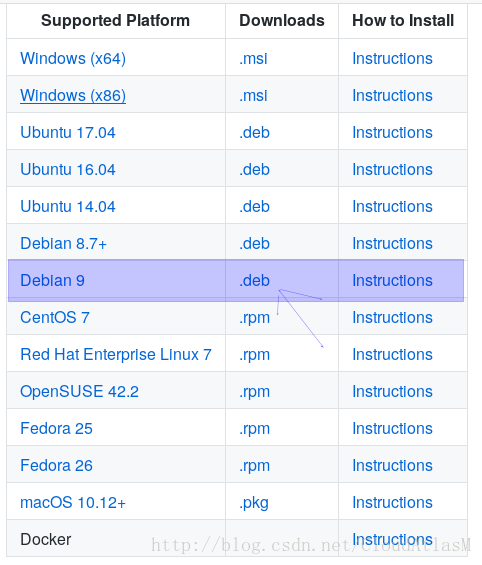
有kali版没测试过
3.安装:dpkg -i powershell_6.0.1-1.debian.9_amd64.deb
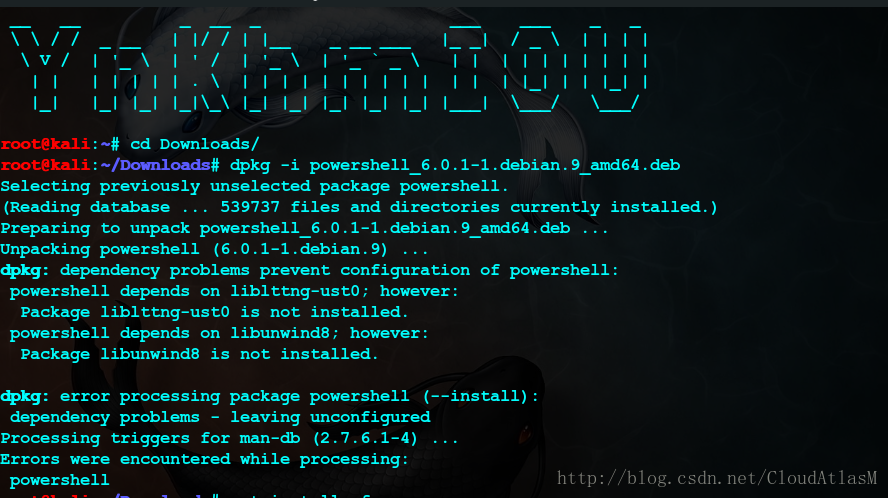
解决依赖关系:apt install -f
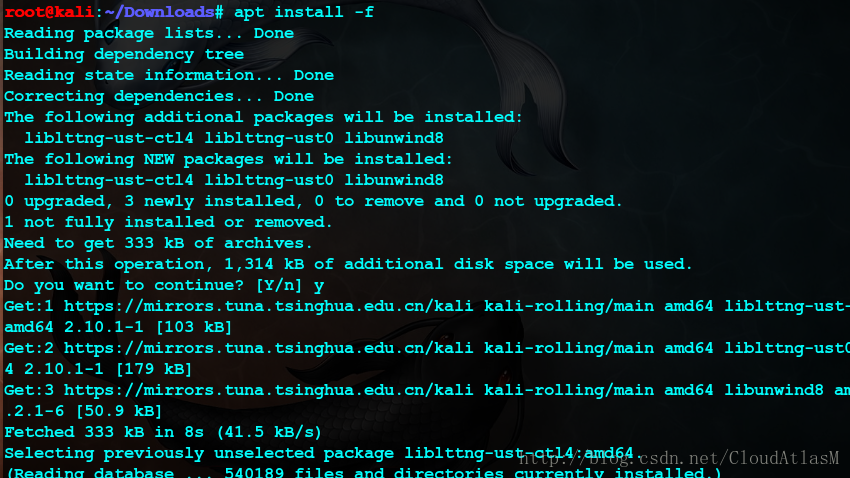
覆盖安装:dpkg -i powershell_6.0.1-1.debian.9_amd64.deb
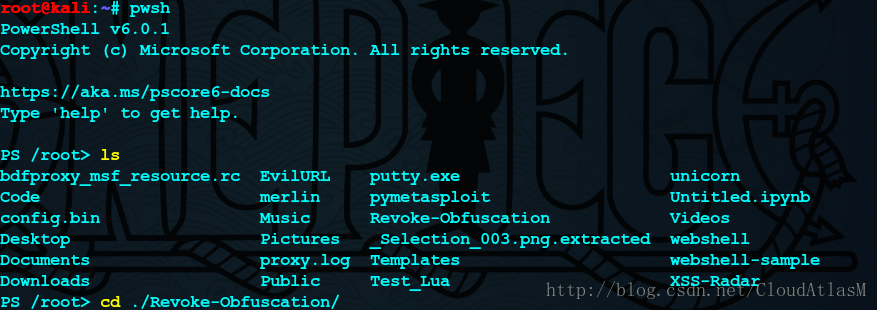
4.启动:启动命令并不是powershell 而是pwsh
5.测试一下:
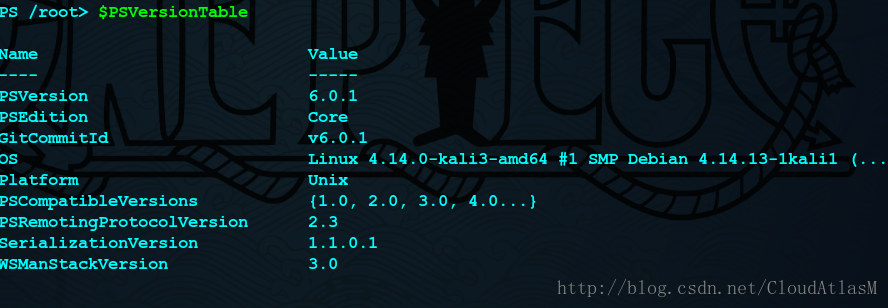
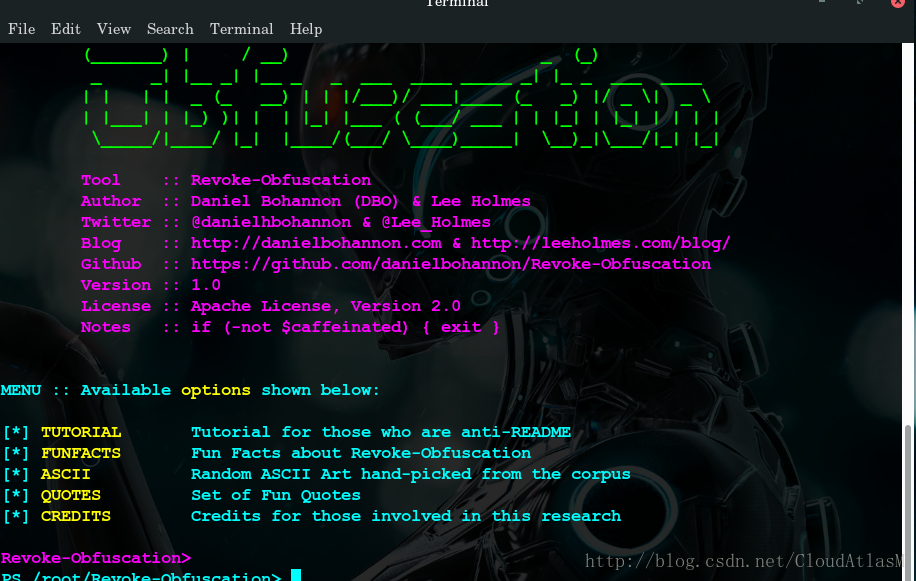
某powershell 脚本工具:
PS:最新版本kali 只能安装debian.9 版本才能正确解决依赖关系,debian.8是不可以的,并且只支持kali linux 64位





 本文介绍如何在Kali Linux 2018.1上安装PowerShell 6.0.1版本,并提供了详细的步骤指导,包括解决依赖问题的方法。此外,还介绍了PowerShell的基本概念及其在系统管理方面的应用。
本文介绍如何在Kali Linux 2018.1上安装PowerShell 6.0.1版本,并提供了详细的步骤指导,包括解决依赖问题的方法。此外,还介绍了PowerShell的基本概念及其在系统管理方面的应用。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








