第五周
一、openssh服务安全加固总结
-
禁止root用户远程登录
为了增加系统的安全性,可以设置系统禁用root远程登录,Ubuntu系统默认禁止root用户进行远程登录。centos系统可以修改/etc/ssh/sshd_config文件实现。设置PermitRootLogin的值为no,如图。

-
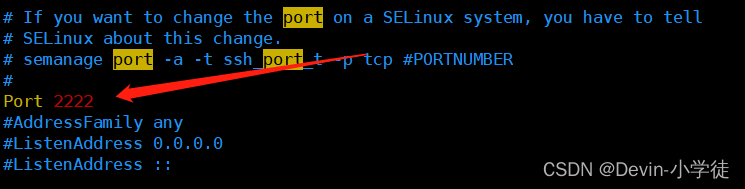
修改SSH默认端口
将SHH默认端口22修改为其他的端口,通过/etc/ssh/sshd_config文件来实现。在该文件中,将Port的值设置为其他端口即可。如图
-
使用SSH密钥进行登录可以提高系统安全性
[root@rocky8 ~]#ssh-keygen //客户端生成SSH密钥对
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:9gg/UwXKgBt4HpLF0U6ec9n99XMLhKkQK/3NX5/L1dY root@rocky8.5
The key's randomart image is:
+---[RSA 3072]----+
| =o+. . |
| + * o+ . . |
| + B..=o .+ |
| o.=+o .+.. .|
| ooS = .. ..|
| + * o ..o=|
| = . . o E|
| o ..+o|
| o.|
+----[SHA256]-----+
[root@rocky8 ~]#ssh-copy-id 10.0.0.111 //将生成的密钥对拷贝到服务器中
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '10.0.0.111 (10.0.0.111)' can't be established.
ECDSA key fingerprint is SHA256:cOVZCFv60WiniZBsuP6bnhp0ry+EWx8pR2iIAsAizEs.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@10.0.0.111's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '10.0.0.111'"
and check to make sure that only the key(s) you wanted were added.
实现免密登录
[root@rocky8 ~]#cat .ssh/
id_rsa id_rsa.pub known_hosts
[root@XWD-C7 ~]# ll .ssh/ //服务器查看密钥对是否已完成拷贝
total 4
-rw------- 1 root root 567 Jun 25 23:24 authorized_keys
[root@XWD-C7 ~]#
[root@rocky8 ~]#ssh 10.0.0.111 //实现免密远程登录
Last login: Sun Jun 25 23:22:39 2023 from 10.0.0.1
[root@XWD-C7 ~]#
二、 总结sudo配置文件格式,总结相关示例。
- 格式:
who where=(whom) what - 允许用户“xu”在本地可以执行所有命令:
xu ALL=(ALL) ALL - 允许用户devin在本地执行/etc/init.d/httpd脚本:
devin ALL=(ALL) /etc/init.d/httpd - 允许用户devin在本地执行
/usr/bin/apt-get命令:devin ALL=(ALL) /usr/bin/apt-get - 允许用户xu在本地以root身份执行所有命令:
xu ALL=(root) ALL - 允许用户devin在本地执行
/usr/bin/apt-get命令,但需要输入密码:
devin ALL=(ALL) /usr/bin/apt-get, /usr/bin/aptitude, /usr/sbin/synaptic
三、实现私有时间服务器
在公司内部搭建时间同步服务器,使其可以与互联网进行时间同步,再将本地其他的服务器与服务器服务端进行同步;
在本地使用两台虚拟机进行配置测试
服务器配置
yum insatll -y chrony //安装chrony
vim /etc/chronyd.conf //修改配置文件,添加时间同步服务器
//设置允许内部所有网段服务器均可与服务器同步连接
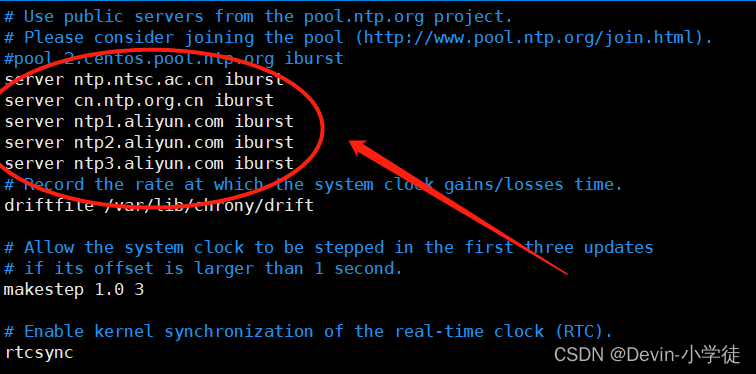

systemctl restart chronyd //修改配置文件之后重新启动服务
[root@rocky8 ~]#chronyc sources
MS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^- 114.118.7.161 1 6 65 28 +21ms[ +21ms] +/- 30ms
^? 223.113.120.195 0 7 0 - +0ns[ +0ns] +/- 0ns
^* 120.25.115.20 2 6 17 32 +3222us[+1652ms] +/- 27ms
^- 203.107.6.88 2 6 17 32 +51us[ +51us] +/- 14ms
[root@rocky8 ~]#
//*显表示已经与配置的其中某个时间同步服务器连接
内部服务器实现与服务器服务端同步
内部服务器安装chrony,并修改配置文件;
# Use public servers from the pool.ntp.org project.
# Please consider joining the pool (http://www.pool.ntp.org/join.html).
server 10.0.0.115 iburst //设置同步时间服务器地址
#server 0.centos.pool.ntp.org iburst
#server 1.centos.pool.ntp.org iburst
#server 2.centos.pool.ntp.org iburst
#server 3.centos.pool.ntp.org iburst
保存配置文件之后重启服务,测试是否已于时间同步服务器完成同步
[root@XWD-C7 ~]# chronyc sources -v
210 Number of sources = 1
.-- Source mode '^' = server, '=' = peer, '#' = local clock.
/ .- Source state '*' = current synced, '+' = combined , '-' = not combined,
| / '?' = unreachable, 'x' = time may be in error, '~' = time too variable.
|| .- xxxx [ yyyy ] +/- zzzz
|| Reachability register (octal) -. | xxxx = adjusted offset,
|| Log2(Polling interval) --. | | yyyy = measured offset,
|| \ | | zzzz = estimated error.
|| | | \
MS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^* 10.0.0.115 3 6 17 0 +3209ns[ +52us] +/- 23ms
[root@XWD-C7 ~]#
//完成与上游时间服务器同步
四、总结DNS域名三级结构
1、顶级域名:是DNS层次结构的最高级别,在整个域名的最后边,例如 .com 、.net、.org、.edu等。用于表示域名的分类或者国家/地区。.com用于商业网站、.edu用于教育机构、.cn用于中国等。
2、二级域名:在顶级域名之后的部分,可以由组织或者个人自定义的名称,用于识别特定的网站或服务,如www.magedu.com。“magedu”就是二级域名。
3、子域名:在二级域名之前的部分,可用于进一步细分组织网站的内容或者服务,如mail.qq.com。“mail”就是子域名,表示指定的邮箱服务。
在系统中可以修改/etc/hosts文件管理域名解析,可以在文件中配置域名和IP地址之间的映射关系。
五、总结DNS服务工作原理,涉及递归和迭代查询原理
递归查询:当客户端需要解析一个域名时,它会向本地DNS解析器发送一个DNS查询请求。
- 本地DNS解析器首先会检查自己的缓存,如果找到了对应的域名解析结果,则直接返回给客户端。
- 如果本地DNS解析器的缓存中没有找到对应的解析结果,它将作为一个DNS客户端,向根DNS服务器发送一个递归查询请求。
- 根DNS服务器收到递归查询请求后,会根据请求的域名后缀(例如,.com、.org等)返回一个指向对应顶级域名服务器的IP地址。
- 本地DNS解析器继续向顶级域名服务器发送递归查询请求。
- 顶级域名服务器返回下一级域名服务器的IP地址,本地DNS解析器再向该域名服务器发送递归查询请求。
- 这个过程会一直重复,直到找到负责该域名的权威域名服务器。
权威域名服务器将域名解析结果返回给本地DNS解析器,本地DNS解析器再将结果返回给客户端,并将结果保存在缓存中,以备将来使用。
迭代查询:由DNS客户端发起。
- DNS客户端向DNS服务器发送一个查询请求,而DNS服务器只返回一个指向下一个查询的DNS服务器的IP地址。
- DNS客户端继续向下一个DNS服务器发送查询请求,直到找到负责该域名的权威域名服务器。
- 权威域名服务器将域名解析结果返回给最后一个DNS服务器,最后一个DNS服务器再将结果返回给DNS客户端。
该条件查询的源不变,但查询的目标不断变化,为查询结果一般需要发起多次查询。
总结:递归查询是DNS解析过程中的主要查询方式,客户端向本地DNS解析器发送递归查询请求,本地DNS解析器负责向根DNS服务器和其他级别的DNS服务器发送查询请求,直到找到域名的解析结果。
迭代查询是DNS解析过程中的备选查询方式,DNS客户端直接向DNS服务器发送查询请求,并按照服务器返回的IP地址逐级查询,直到找到域名的解析结果。
递归查询和迭代查询共同构成了DNS服务的工作原理,确保了域名的解析能够高效准确地完成。
六、实现本地私有DNS,供本地网络主机作DNS递归查询
测试功能实现我本地准备了3台虚拟机,其中10.0.0.119为master服务器,10.0.0.123为DB,10.0.0.113为www从主机;
服务端配置 //安装bind、bind-utils软件
[root@C8M-1 ~]# yum install -y bind bind-utils
[root@C8M-1 ~]# systemctl enable --now named //设置开机启动服务
Created symlink /etc/systemd/system/multi-user.target.wants/named.service → /usr/lib/systemd/system/named.service.
//修改配置文件/etc/named.conf文件
options {
// listen-on port 53 { 127.0.0.1; }; //注释监听端口
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
// allow-query { localhost; }; //注释掉请求连接限制,可以添加某一网段或者直接干掉
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable no; //默认为yes,将该选项关闭
dnssec-validation no;
managed-keys-directory "/var/named/dynamic";
[root@C8M-1 ~]# vim /etc/named.conf
[root@C8M-1 ~]# rndc reload //修改完配置文件后重新加载,也可以用命令:nmcli connection reload + nmcli connection up eth0
server reload successful
//修改网卡信息,将dns1改为本主机127.0.0.1
[root@C8M-1 ~]# vim /etc/sysconfig/network-scripts/ifcfg-eth0
[root@C8M-1 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth0
DEVICE=eth0
NAME=eth0
BOOTPROTO=none
ONBOOT=yes
IPADDR=10.0.0.119
PREFIX=24
GATEWAY=10.0.0.2
DNS=127.0.0.1
#DNS1=223.5.5.5
#DNS2=223.6.6.6
vim /etc/named.rfc1912.zones
添加以下内容,设置域名,类型为主服务器
zone "xuweidong.org" {
type master;
file "/etc/named/zones/xuweidong.org.zone";
};
创建相关文件夹及文件
[root@C8M-1 ~]# mkdir /etc/named/zones
root@C8M-1 ~]# vim /etc/named/zones/xuweidong.org.zone
[root@C8M-1 ~]# cat /var/named/xuweidong.org.zone
$TTL 1D
@ IN SOA master admin.xuweidong.org ( 20230627 3H 10M 1D 6H )
NS master
master A 10.0.0.119
www A 10.0.0.113
db A 10.0.0.123
node1 A 1.1.1.1
[root@C8M-1 ~]# nmcli connection reload //启动相关服务
[root@C8M-1 ~]# nmcli connection up eth0
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2)
[root@C8M-1 ~]# cat /etc/resolv.conf //查看已经设置的dns地址
# Generated by NetworkManager
nameserver 127.0.0.1
[root@C8M-1 ~]# host www.baidu.com //解析成功
www.baidu.com is an alias for www.a.shifen.com.
www.a.shifen.com has address 220.181.38.150
www.a.shifen.com has address 220.181.38.149
服务端配置完成,该服务端可对互联网进行域名解析
本地客户端配置
/安装服务端软件,bind-utils;
修改网卡信息
[root@XWD-C7M-1 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth0
DEVICE=eth0
NAME=eth0
BOOTPROTO=static
ONBOOT=yes
IPADDR=10.0.0.113
PREFIX=24
GATEWAY=10.0.0.2
DNS1=10.0.0.119 //将dns地址修改为服务端地址
#DNS1=223.5.5.5
#DNS2=223.6.6.6
[root@XWD-C7M-1 ~]# cat /etc/resolv.conf //查看dns地址
# Generated by NetworkManager
nameserver 10.0.0.119
[root@XWD-C7M-1 ~]# host www.baidu.com //测试解析是否成功
www.baidu.com is an alias for www.a.shifen.com.
www.a.shifen.com has address 220.181.38.150
www.a.shifen.com has address 220.181.38.149
[root@XWD-C7M-1 ~]# host www.xuweidong.org
www.xuweidong.org has address 10.0.0.113
[root@XWD-C7M-1 ~]# host db.xuweidong.org
db.xuweidong.org has address 10.0.0.123
[root@XWD-C7M-1 ~]# host master.xuweidong.org
master.xuweidong.org has address 10.0.0.119
[root@XWD-C7M-1 ~]#
// 10.0.0.123客户端测试
[root@Rocky8 ~]# host db.xuweidong.org
db.xuweidong.org has address 10.0.0.123
[root@Rocky8 ~]# host www.xuweidong.org
www.xuweidong.org has address 10.0.0.113
[root@Rocky8 ~]# host master.xuweidong.org
master.xuweidong.org has address 10.0.0.119
udp端口作用为dns解析服务,对外提供查询支持的主要端口
七、总结iptables5表5链,基本使用,扩展模块。
iptables是用于系统中配置和管理防火墙规则的工具,使用表(tables)和链(chains)来组织和处理网络数据包。
1、5表包括:filter、nat、mangle、rew、security。优先级从高到底为:security—>raw—>mangle—>nat—>filter
- 1)filter:过滤规则表,可以根据定义的规则过滤符合条件的数据包和默认表;
- 2)nat:地址转换规则表;
-
- mangle:修改数据标记位规则表;
- 4)rew:可以关闭启用的连接跟踪机制,加快封包穿过防火墙速度;
- 5)security:用于强制访问控制(MAC)网络规则
2、5链包括:INPUT、OUTPUT、PORWARD、PREROUTING、POSTROUTING。
3、基本使用语法
- 1)拒绝某个主机进行访问
iptables -A INPUT -s 10.0.0.111 -j DROP/REJECT(拒绝) //将10.0.0.111主机拒绝访问 -
表示追加 限制主机地址 (跳过)
[root@rocky8 ~]#iptables -A INPUT -s 10.0.0.111 -j DROP
[root@rocky8 ~]#tcpdump -i eth0 -nn icmp //抓包查看
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:39:32.702655 IP 10.0.0.111 > 10.0.0.115: ICMP echo request, id 2104, seq 151, length 64 //只有请求没有回复
13:39:33.702718 IP 10.0.0.111 > 10.0.0.115: ICMP echo request, id 2104, seq 152, length 64
13:39:34.702451 IP 10.0.0.111 > 10.0.0.115: ICMP echo request, id 2104, seq 153, length 64
13:39:35.702404 IP 10.0.0.111 > 10.0.0.115: ICMP echo request, id 2104, seq 154, length 64
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 175 14596 DROP all -- * * 10.0.0.111 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
- 2)添加允许某个主机访问策略
[root@rocky8 ~]#iptables -I INPUT 1 -s 10.0.0.111 -j ACCEPT //允许IP进行访问 -I
// -I表示在第几行添加规则 表示同意访问
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT all -- * * 10.0.0.111 0.0.0.0/0 添加成功,已允许该地址进行访问
2 233 19452 DROP all -- * * 10.0.0.111 0.0.0.0/0
3 62 5208 DROP all -- * * 10.0.0.117 0.0.0.0/0
4 190 11124 ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
- 3)删除第2行拒绝10.0.0.111主句访问规则;
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT all -- * * 10.0.0.111 0.0.0.0/0
2 233 19452 DROP all -- * * 10.0.0.111 0.0.0.0/0 //删除该行规则
3 62 5208 DROP all -- * * 10.0.0.117 0.0.0.0/0
4 190 11124 ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
[root@rocky8 ~]#iptables -D INPUT 2 // -D表示删除
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 5 396 ACCEPT all -- * * 10.0.0.111 0.0.0.0/0
2 62 5208 DROP all -- * * 10.0.0.117 0.0.0.0/0
3 272 16337 ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
- 4)添加允许访问协议规则
[root@rocky8 ~]#iptables -I INPUT 3 -p icmp -j ACCEPT //允许ICMP协议访问规则
-p 添加协议规则
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 11 852 ACCEPT all -- * * 10.0.0.111 0.0.0.0/0
2 62 5208 DROP all -- * * 10.0.0.117 0.0.0.0/0
3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
4 556 33556 ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
- 5)添加协议允许的端口
iptables -I INPUT 3 -p tcp --dprot 80 -j ACCEPT
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 29 2220 ACCEPT all -- * * 10.0.0.111 0.0.0.0/0
2 62 5208 DROP all -- * * 10.0.0.117 0.0.0.0/0
3 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
- 6)实现主机之间的单向通讯
[root@rocky8 ~]#iptables -A INPUT -s 10.0.0.0/24 -j REJECT
[2]+ Stopped ping 10.0.0.117
[root@rocky8 ~]#iptables -I INPUT 4 -p icmp --icmp-type 0 -j ACCEPT
[root@rocky8 ~]#iptables -vnL --line-number
Chain INPUT (policy ACCEPT 158 packets, 10897 bytes)
num pkts bytes target prot opt in out source destination
1 1180 73026 ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 4 788 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 12 976 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
[root@rocky8 ~]#ping 10.0.0.117
PING 10.0.0.117 (10.0.0.117) 56(84) bytes of data.
64 bytes from 10.0.0.117: icmp_seq=1 ttl=64 time=0.513 ms
64 bytes from 10.0.0.117: icmp_seq=2 ttl=64 time=1.63 ms
[root@localhost ~]#ping 10.0.0.115
PING 10.0.0.115 (10.0.0.115) 56(84) bytes of data.
From 10.0.0.115 icmp_seq=1 Destination Port Unreachable
From 10.0.0.115 icmp_seq=2 Destination Port Unreachable
From 10.0.0.115 icmp_seq=3 Destination Port Unreachable
- 7)端口替换命令,合并80端口与443端口;
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 1619 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 2619 166K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 7 552 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
6 25 1964 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 2721 packets, 269K bytes)
num pkts bytes target prot opt in out source destination
[root@rocky8 ~]#iptables -R INPUT 3 -p tcp -m multiport --dports 80,443 -j ACCEPT
[root@rocky8 ~]#iptables -R INPUT 3 -p tcp -m muvnL --line-numbers
Chain INPUT (policy ACCEPT 1619 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 2776 175K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 7 552 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
6 25 1964 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 2811 packets, 277K bytes)
num pkts bytes target prot opt in out source destination
[root@rocky8 ~]#
- 8)自定义链的增加删除,并实现允许HTTP和HTTPS访问;
[root@rocky8 ~]#iptables -N WEB //增加自定义链
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 1621 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 3220 202K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 10 904 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 27 2116 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3089 packets, 305K bytes)
num pkts bytes target prot opt in out source destination
Chain WEB (0 references) //完成添加
num pkts bytes target prot opt in out source destination
[root@rocky8 ~]#iptables -S //查看当前iptables已添加的规则;
-P INPUT ACCEPT
-P FORWARD ACCEPT
-P OUTPUT ACCEPT
-N WEB
-A INPUT -s 10.0.0.1/32 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type 0 -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j REJECT --reject-with icmp-port-unreachable
[root@rocky8 ~]#iptables -A WEB -p tcp -m multiport --dports 80,443 -j ACCEPT //将相关规则添加到自定义链中
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 1623 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 3596 226K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 10 904 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 28 2192 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3335 packets, 325K bytes)
num pkts bytes target prot opt in out source destination
Chain WEB (0 references)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
[root@rocky8 ~]#
[root@rocky8 ~]#iptables -I INPUT 3 -j WEB //使用时将自定义链进行调用
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 1624 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 3811 239K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 0 0 WEB all -- * * 0.0.0.0/0 0.0.0.0/0 //完成在哪里进行调用
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 28 2192 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3464 packets, 338K bytes)
num pkts bytes target prot opt in out source destination
Chain WEB (1 references)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
[root@rocky8 ~]#
[root@rocky8 ~]#iptables -A WEB -p udp --dport 53 -j ACCEPT //追加规则
[root@rocky8 ~]#iptables -vnL --line-numbers
Chain INPUT (policy ACCEPT 1624 packets, 2089K bytes)
num pkts bytes target prot opt in out source destination
1 3943 247K ACCEPT all -- * * 10.0.0.1 0.0.0.0/0
2 75 16857 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
3 0 0 WEB all -- * * 0.0.0.0/0 0.0.0.0/0
4 2 168 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
5 28 2192 REJECT all -- * * 10.0.0.0/24 0.0.0.0/0 reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3538 packets, 345K bytes)
num pkts bytes target prot opt in out source destination
Chain WEB (1 references)
num pkts bytes target prot opt in out source destination
1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
2 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53
1、删除自定义链时,先取消调用
iptables -D INPUT 3
2、清除自定义链中的规则后,进行删除自定义链;
iptables -F WEB
3、删除自定义链
iptables -X WEB //即可完成删除
// 实现HTTP与HTTPS访问
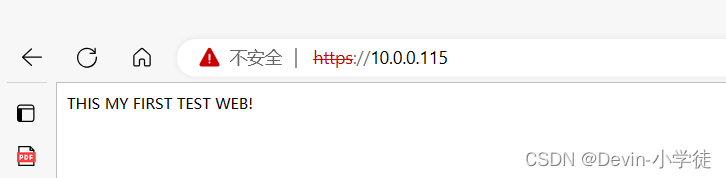
[root@localhost ~]#curl -k https://10.0.0.115
THIS MY FIRST TEST WEB!
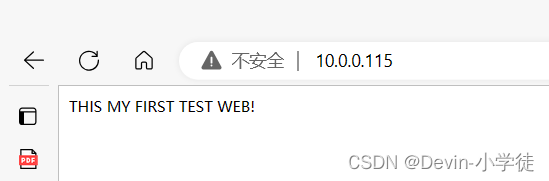
[root@localhost ~]#curl -k http://10.0.0.115
THIS MY FIRST TEST WEB!




















 1511
1511











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








