from : http://blog.csdn.net/shenlan211314/article/details/6439573
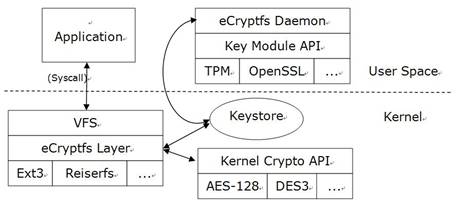
ecryptfs加密文件系统架构:
1 安装ecryptfs
在终端下输入:
sudo apt-get install ecryptfs-utils
如下图所示:

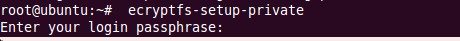
2 创建登录密码和挂载密码
ecryptfs-setup-private
如下图所示:
3 挂载私人文件
a) 创建文件夹 mkdir /root/tPrivate

b) 修改文件夹权限,使其他人无法访问这个文件夹 chmod 700 /root/tPrivate
c) 用ecrypt挂载文件夹(加密) mount -t ecryptfs /root/tPrivate /root/tPrivate
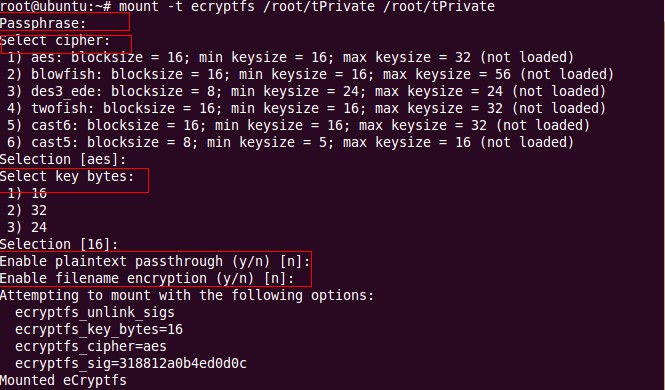
d) 在挂载过程中会遇到询问提示
首先需要输入挂载密码(不同于登录密码)
然后需要选择密钥计算方式(直接回车为默认)
接着需要输入加密长度(直接回车为默认)
接着需要选择是否允许将未加密文件放入此文件夹中(默认为不允许)
此时提示挂载成功
注:
from :http://manpages.ubuntu.com/manpages/jaunty/en/man7/ecryptfs.7.html
NAME
eCryptfs - an enterprise-class cryptographic filesystem for linux
SYNOPSIS
mount -t ecryptfs [SRC DIR] [DST DIR] -o [OPTIONS]
DESCRIPTION
eCryptfs is a POSIX-compliant enterprise-class stacked cryptographic
filesystem for Linux. It is derived from Erez Zadok’s Cryptfs,
implemented through the FiST framework for generating stacked
filesystems. eCryptfs extends Cryptfs to provide advanced key
management and policy features. eCryptfs stores cryptographic metadata
in the header of each file written, so that encrypted files can be
copied between hosts; the file will be decryptable with the proper key,
and there is no need to keep track of any additional information aside
from what is already in the encrypted file itself. Think of eCryptfs as
a sort of "gnupgfs."
OPTIONS
KERNEL OPTIONS
Parameters that apply to the eCryptfs kernel module.
ecryptfs_sig=(fekek_sig)
Specify the signature of the mount wide authentication token.
The authentication token must be in the kernel keyring before
the mount is performed. ecryptfs-manager or the eCryptfs mount
helper can be used to construct the authentication token and add
it to the keyring prior to mounting.
ecryptfs_fnek_sig=(fnek_sig)
Specify the signature of the mount wide authentication token
used for filename crypto. The authentication must be in the
kernel keyring before mounting.
ecryptfs_cipher=(cipher)
Specify the symmetric cipher to be used on a per file basis
ecryptfs_key_bytes=(key_bytes)
Specify the keysize to be used with the selected cipher. If the
cipher only has one keysize the keysize does not need to be
specified.
ecryptfs_passthrough
Allows for non-eCryptfs files to be read and written from within
an eCryptfs mount. This option is turned off by default.
no_sig_cache
Do not check the mount key signature against the values in the
user’s ~/.ecryptfs/sig-cache.txt file. This is useful for such
things as non-interactive setup scripts, so that the mount
helper does not stop and prompt the user in the event that the
key sig is not in the cache.
ecryptfs_encrypted_view
This option, when set, will have eCryptfs return the encrypted
versions of the lower files, rather than decrypt encrypted files
and return the decrypted data from the lower files. This options
is useful for such things as backup utilities.
ecryptfs_xattr
Store the metadata in the extended attribute of the lower files
rather than the header region of the lower files.
MOUNT HELPER OPTIONS
Parameters that apply to the eCryptfs mount helper.
key=(keytype):[KEY MODULE OPTIONS]
Specify the type of key to be used when mounting eCryptfs.
ecryptfs_enable_filename_crypto=(y/N)
Specify whether filename encryption should be enabled. If not,
the mount helper will not prompt the user for the filename
encryption key signature.
KEY MODULE OPTIONS
Parameters that apply to individual key modules have the alias
for the key module in the prefix of the parameter name. Key
modules are pluggable, and which key modules are available on
any given system is dependent upon whatever happens to be
installed in /usr/lib*/ecryptfs/. By default, this includes, at
a minimum, "passphrase" and "openssl."
passphrase_passwd=(passphrase)
The actual password is password. Since the password is visible
to utilities (like ps under Unix) this form should only be used
where security is not important.
passphrase_passwd_file=(filename)
The password should be specified in a file with
passwd=(passphrase). It is highly reccomended that the file be
stored on a secure medium such as a personal usb key.
passphrase_passwd_fd=(file descriptor)
The password is specified through the specified file descriptor.
passphrase_salt=(hex value)
The salt should be specified as a 16 digit hex value.
openssl_keyfile=(filename)
The filename should be the filename of a file containing an RSA
SSL key.
openssl_passwd_file=(filename)
The password should be specified in a file with passwd=(openssl-
password). It is highly reccomended that the file be stored on a
secure medium such as a personal usb key.
openssl_passwd_fd=(file descriptor)
The password is specified through the specified file descriptor.
openssl_passwd=(password)
The password can be specified on the command line. Since the
password is visible in the process list, it is highly
recommended to use this option only for testing purposes.
EXAMPLE
The following command will layover mount eCryptfs on /secret with a
passphrase contained in a file stored on secure media mounted at
/mnt/secureusb/.
mount -t ecryptfs -o
key=passphrase:passphrase_passwd_file=/mnt/secureusb/passwd_file.txt
/secret /secret
Where passwd_file.txt contains the contents
"passphrase_passwd=[passphrase]".
4)测试
a)创建文件,并输入内容,例如:gedit /root/private/test 输入内容“this is a test file content”。
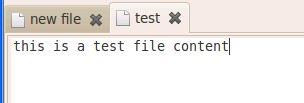
b)查看文件,输入 cat /root/private/test 会看到 this is a test file content 字样
c)卸载文件,输入"umount /root/private"
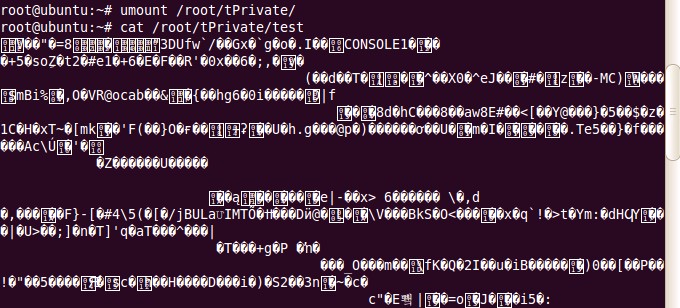
d)再次查看文件内容,输入cat /root/private/test,会看到乱码。
e)再次挂载,发现又可以看到之前输入的文字了。
成功!
=====
问题
signature的作用~
signature应该可以再某些情况下用于数据恢复的。这方面还没有进行尝试
相关文章:http://www.zeuux.org/blog/content/3610/


























 5327
5327

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








