
尽管蓝牙已成为我们日常生活中无处不在的一部分,但大多数人仍然不知道其内部工作原理,更重要的是,它容易受到黑客攻击。深入研究蓝牙黑客领域可以直接了解目标的世界。鉴于几乎所有设备都配备了蓝牙功能,利用这种无线技术可能会允许访问手机和平板电脑上存储的大量个人信息。
尽管蓝牙和 Wi-Fi 共享相同的 2.4 GHz 频率,但它们不同的协议使它们在安全性方面具有不同的实体。蓝牙增强的安全措施使得传统的 Wi-Fi 黑客工具对其无效。
蓝牙设备采用的连续跳频是一项显着特征。当两个设备通过蓝牙进行通信时,它们利用一种每秒动态多次改变频率的算法。这种恒定的跳频对试图窃听通信的潜在攻击者构成了重大挑战。
此外,蓝牙与 Wi-Fi 的不同之处在于处理密钥协商的方式。Wi-Fi 会在每次连接时协商密钥,而蓝牙在初始连接期间仅建立一次密钥。随后,该秘密密钥被存储并被引用以用于与同一设备的后续通信。与 Wi-Fi 不同,这种方法使攻击者几乎不可能被动地嗅探密钥,因为他们需要在初始通信期间在场。
然而,这并不意味着蓝牙是不可渗透的。它仍然容易跟踪附近的设备、从中提取信息,甚至操纵特定的特征。进行侦察变得至关重要,因为它可能会发现夺取控制权、识别漏洞或发现与附近设备相关的潜在漏洞的机会。
了解蓝牙技术的细微差别不仅对于用户至关重要,对于那些负责在不断发展的数字环境中保护这些无线连接的人员也至关重要。
准备蓝牙侦察:快速指南
开始蓝牙监控需要装备精良的设置。确保您安装了最新的 Kali Linux,因为我们将利用其内置的蓝牙工具来实现这一目标。为了保持精简,我们不会添加任何额外的工具;Kali Linux 中默认的蓝牙工具包就足够了。
BlueZ(大多数 Linux 版本中的默认蓝牙协议栈)中包含的关键工具构成了我们探索的基础。其中,我们将深入研究 hciconfig、hcitool、sdptool、l2ping 和 btscanner。此外,还将推出为 Kali Linux 中的蓝牙侦察量身定制的专用工具。
邻近度是蓝牙黑客攻击的一个关键因素。配备可靠的蓝牙适配器,您可以在各种环境中定位设备 - 无论是咖啡店、学校教室、办公室,甚至是邻居家附近的设备。确保您的蓝牙适配器具有高品质,以最大限度地扩大蓝牙侦察范围。
激活蓝牙适配器:hciconfig 入门
就像 ifconfig 用于 Wi-Fi 一样,蓝牙设备的对应项是 hciconfig。该工具有助于激活您的蓝牙适配器,作为我们侦察之旅的第一步。熟悉 hciconfig,为高效的蓝牙黑客攻击奠定基础。
~\# hciconfig
hci0 Type: Primary Bus: USBType: Primary Bus: USB
BD Address: ██:██:██:██:██:██ ACL MTU: 1022:8 SCO MTU: 183.5
DOWN
RX bytes:574 acl:0 sco:0 events:30 errors:0
TX bytes:368 acl:0 sco:0 commands:30 errors:0
正如 ifconfig 是 Wi-Fi 的代名词一样,hciconfig 是蓝牙设备的领先者。在本指南中,我们将介绍蓝牙接口的设置,这是高效蓝牙黑客攻击的重要前提。观察我们的示例,其中蓝牙接口当前处于非活动状态(关闭)。请按照以下步骤将其激活并启动蓝牙操作。假设您非常熟悉 ifconfig 命令。在这种情况下,适应 hciconfig 将是无缝的,因为它们具有结构相似性。例如,如果您需要激活 Wi-Fi 接口,则命令为“ifconfig [interface_name] up”。在蓝牙领域,使用 hciconfig 反映了这个过程。浏览 hciconfig 手册页以获取兼容命令的完整列表。
~\# man hciconfig
HCICONFIG(1) Linux System Administration HCICONFIG(1)1) Linux System Administration HCICONFIG(1)
NAME
hciconfig \- configure Bluetooth devices
SYNOPSIS
hciconfig \-h
hciconfig \[\-a\]
hciconfig \[\-a\] hciX \[command \[command parameters\]\]
DESCRIPTION
hciconfig is used to configure Bluetooth devices. hciX is the name of
a Bluetooth device installed in the system. If hciX is not given, hci‐
config prints name and basic information about all the Bluetooth de‐
vices installed in the system. If hciX is given but no command is
given, it prints basic information on device hciX only. Basic informa‐
tion is interface type, BD address, ACL MTU, SCO MTU, flags (up, init,
running, raw, page scan enabled, inquiry scan enabled, inquiry, authen‐
tication enabled, encryption enabled).
OPTIONS
\-h, \--help
Gives a list of possible commands.
\-a, \--all
Other than the basic info, print features, packet type, link
policy, link mode, name, class, version.
COMMANDS
up Open and initialize HCI device.
down Close HCI device.
reset Reset HCI device.
rstat Reset statistic counters.
auth Enable authentication (sets device to security mode 3).
noauth Disable authentication.
encrypt Enable encryption (sets device to security mode 3).
noencrypt Disable encryption.
secmgr Enable security manager (current kernel support is limited).
nosecmgr Disable security manager.
piscan Enable page and inquiry scan.
noscan Disable page and inquiry scan.
iscan Enable inquiry scan, disable page scan.
pscan Enable page scan, disable inquiry scan.
ptype \[type\] With no type , displays the current packet types. Otherwise, all the packet types specified by type are set. type is a comma\-separated list of packet types, where the possible packet types are DM1, DM3, DM5, DH1, DH3, DH5, HV1, HV2, HV3.
name \[name\] With no name, prints local name. Otherwise, sets local name to name.
class \[class\] With no class, prints class of device. Otherwise, sets class of device to class. class is a 24\-bit hex number describing the class of device, as specified in section 1.2 of the Bluetooth Assigned Numers document.
voice \[voice\] With no voice, prints voice setting. Otherwise, sets voice setting to voice. voice is a 16\-bit hex number describing the voice setting.
iac \[iac\] With no iac, prints the current IAC setting. Otherwise, sets the IAC to iac.
inqtpl \[level\] With no level, prints out the current inquiry transmit power level. Otherwise, sets inquiry transmit power level to level.
inqmode \[mode\] With no mode, prints out the current inquiry mode. Otherwise, sets inquiry mode to mode.
inqdata \[data\] With no name, prints out the current inquiry data. Otherwise, sets inquiry data to data.
inqtype \[type\] With no type, prints out the current inquiry scan type. Otherwise, sets inquiry scan type to type.
inqparams \[win:int\] With no win:int, prints inquiry scan window and interval. Otherwise, sets inquiry scan window to win slots and inquiry scan interval to int slots.
pageparms \[win:int\] With no win:int, prints page scan window and interval. Otherwise, sets page scan window to win slots and page scan interval to int slots.
pageto \[to\] With no to, prints page timeout. Otherwise, sets page timeout to .I to slots.
afhmode \[mode\] With no mode, prints out the current AFH mode. Otherwise, sets AFH mode to mode.
sspmode \[mode\] With no mode, prints out the current Simple Pairing mode. Otherwise, sets Simple Pairing mode to mode.
aclmtu mtu:pkt Sets ACL MTU to to mtu bytes and ACL buffer size to pkt packets.
scomtu mtu:pkt Sets SCO MTU to mtu bytes and SCO buffer size to pkt packets.
delkey This command deletes the stored link key for bdaddr from the device.
oobdata Get local OOB data (invalidates previously read data).
commands Display supported commands.
features Display device features.
version Display version information.
revision Display revision information.
lm \[mode\] With no mode , prints link mode. MASTER or SLAVE mean, respectively, to ask to become master or to remain slave when a connection request comes in. The additional keyword ACCEPT means that baseband connections will be accepted even if there are no listening AF\_BLUETOOTH sockets. mode is NONE or a comma\-separated list of keywords, where possible keywords are MASTER and ACCEPT . NONE sets link policy to the default behaviour of remaining slave and not accepting baseband connections when there are no listening AF\_BLUETOOTH sockets. If MASTER is present, the device will ask to become master if a connection request comes in. If ACCEPT is present, the device will accept baseband connections even when there are no listening AF\_BLUETOOTH sockets.
AUTHORS
Written by Maxim Krasnyansky and Marcel Holtmann
man page by Fabrizio Gennari
BlueZ Nov 11 2002 HCICONFIG(1)
Manual page hciconfig(1) line 147/169 (END) (press h for help or q to quit)
hciconfig 的多功能性不仅仅限于接口激活;它是配置蓝牙设备的强大工具。无论您是否连接了外部蓝牙设备,其应用程序都包含设备发现和配置。熟悉这方面后,按 Q 退出 hciconfig 手册页。要将发现的蓝牙设备联机,请执行命令“hciconfig [device_name] up”。此步骤对于为后续操作准备已识别的蓝牙设备至关重要。
~ \# hciconfig hci0 up
要查看它是否有效,请再次运行 hciconfig 命令:
〜#hciconfig
hci0 Type: Primary Bus: USBType: Primary Bus: USB
BD Address: ██:██:██:██:██:██ ACL MTU: 1022:8 SCO MTU: 183.5
UP RUNNING
RX bytes:1148 acl:0 sco:0 events:60 errors:0
TX bytes:736 acl:0 sco:0 commands:60 errors:0
步骤 2:使用 hcitool 扫描蓝牙设备
现在,让我们使用 hcitool 来查找正在发送发现信标(在发现模式下)的蓝牙设备。首先,让我们看看它的手册页:
~# man hciconfig
HCITOOL(1) Linux System Administration HCITOOL(1)1) Linux System Administration HCITOOL(1)
NAME
hcitool - configure Bluetooth connections
SYNOPSIS
hcitool [-h]
hcitool [-i ] [command [command parameters]]
DESCRIPTION
hcitool is used to configure Bluetooth connections and send some spe‐
cial command to Bluetooth devices. If no command is given, or if the
option -h is used, hcitool prints some usage information and exits.
OPTIONS
-h Gives a list of possible commands
-i
The command is applied to device hciX , which must be the name
of an installed Bluetooth device. If not specified, the command
will be sent to the first available Bluetooth device.
COMMANDS
dev Display local devices
inq Inquire remote devices. For each discovered device, Bluetooth device address, clock offset and class are printed.
scan Inquire remote devices. For each discovered device, device name are printed.
name Print device name of remote device with Bluetooth address bdaddr.
info Print device name, version and supported features of remote device with Bluetooth address bdaddr.
spinq Start periodic inquiry process. No inquiry results are printed.
epinq Exit periodic inquiry process.
cmd [parameters]
Submit an arbitrary HCI command to local device. ogf, ocf and parameters are hexadecimal bytes.
con Display active baseband connections
cc [–role=m|s] [–pkt-type=]
Create baseband connection to remote device with Bluetooth address bdaddr. Option --pkt-type specifies a list of allowed packet types. is a comma-separated list of packet types, where the possible packet types are DM1, DM3, DM5, DH1, DH3, DH5, HV1, HV2, HV3. Default is to allow all packet types. Option --role can have value m (do not allow role switch, stay master) or s (allow role switch, become slave if the peer asks to become master). Default is m.
dc [reason]
Delete baseband connection from remote device with Bluetooth address bdaddr. The reason can be one of the Bluetooth HCI error codes. Default is 19 for user ended connections. The value must be given in decimal.
sr Switch role for the baseband connection from the remote device to master or slave.
cpt
Change packet types for baseband connection to device with Bluetooth address bdaddr. packet types is a comma-separated list of packet types, where the possible packet types are DM1, DM3, DM5, DH1, DH3, DH5, HV1, HV2, HV3.
rssi Display received signal strength information for the connection to the device with Bluetooth address bdaddr.
lq Display link quality for the connection to the device with Bluetooth address bdaddr.
tpl [type] Display transmit power level for the connection to the device with Bluetooth address bdaddr. The type can be 0 for the current transmit power level (which is default) or 1 for the maximum transmit power level.
afh Display AFH channel map for the connection to the device with Bluetooth address bdaddr.
lp [value] With no value, displays link policy settings for the connection to the device with Bluetooth address bdaddr. If value is given, sets the link policy settings for that connection to value. Possible values are RSWITCH, HOLD, SNIFF and PARK.
lst [value] With no value, displays link supervision timeout for the connection to the device with Bluetooth address bdaddr. If value is given, sets the link supervision timeout for that connection to value slots, or to infinite if value is 0.
auth Request authentication for the device with Bluetooth address bdaddr.
enc [encrypt enable]
Enable or disable the encryption for the device with Bluetooth address bdaddr.
key Change the connection link key for the device with Bluetooth address bdaddr.
clkoff Read the clock offset for the device with Bluetooth address bdaddr.
clock [bdaddr] [which clock]
Read the clock for the device with Bluetooth address bdaddr. The clock can be 0 for the local clock or 1 for the piconet clock (which is default).
lescan [–privacy] [–passive] [–whitelist] [–discovery=g|l] [–duplicates]
Start LE scan
leinfo [–static] [–random]
Get LE remote information
lewladd [–random]
Add device to LE White List
lewlrm Remove device from LE White List
lewlsz Read size of LE White List
lewlclr Clear LE White List
lerladd [–local irk] [–peer irk] [–random]
Add device to LE Resolving List
lerlrm Remove device from LE Resolving List
lerlclr Clear LE Resolving List
lerlsz Read size of LE Resolving List
lerlon Enable LE Address Resolution
lerloff Disable LE Address Resolution
lecc [–static] [–random] | [–whitelist]
Create a LE Connection
ledc [reason]
Disconnect a LE Connection
lecup
LE Connection Update
AUTHORS
Written by Maxim Krasnyansky and Marcel Holtmann
man page by Fabrizio Gennari
BlueZ Nov 12 2002 HCITOOL(1)
Manual page hcitool(1) line 154/176 (END) (press h for help or q to quit)
事实证明,Hcitool 在配置和执行扫描、查询和名称检索等各种任务方面具有无价的价值。然而,某些命令需要使用 MAC 地址。基本操作是扫描附近的蓝牙设备,提供 MAC 地址以供进一步查询或尝试提取设备名称。使用 hcitool scan 命令启动扫描。它利用蓝牙接口来识别附近的设备,揭示它们的 MAC 地址。此信息可作为后续扫描、查询或努力揭示设备名称的网关。
~\# hcitool scan
Scanning ...
00:1D:A5:00:09:1D OBDII
在上面,我们看到一个连接到车辆的OBD2 连接器。这很有趣。有了 MAC 地址,我们现在可以执行另一个要求我们首先拥有 MAC 地址的命令。让我们尝试获取设备的名称:
~# hcitool name 00:1D:A5:00:09:1D
OBDII
这应该允许我们获取设备的名称,但我们已经从第一次扫描中知道了它。然而,如果我们不知道它,它将使我们能够了解更多信息。要了解更多信息,我们可以使用 inq 命令:
~\# hcitool inq 00:1D:A5:00:09:1D
Scanning ...
00:1D:A5:00:09:1D clock offset: 0x21c0 class: ox5a020c00:1D:A5:00:09:1D clock offset: 0x21c0 class: ox5a020c
请注意,它还显示时钟偏移和类别。该类表明了它是什么类型的蓝牙设备,我们可以通过蓝牙站点查找代码。或者,正如我们稍后将看到的,一些工具可以为我们做到这一点。
步骤 3:使用 sdptool 扫描服务
探索蓝牙设备领域需要对其服务进行仔细检查。来认识一下“sdptool”,它是一个专门为此目的而设计的多功能伴侣。该工具使用户能够深入研究设备服务的复杂性,深入了解其功能、广泛的可能性和固有的限制。在开始使用“sdptool”的探索之旅之前,有必要熟悉它的命令选项和各种功能。对可用命令的充分掌握可确保更细致、更有效的探索体验。掌握了这些知识,就可以无缝地利用“sdptool”来解析蓝牙设备扩展的一系列服务。这种全面的探索不仅揭示了该设备的特性,还提供了细致入微的理解,从而实现明智的侦察和战略互动。
# man sdptool
sdptool(1) General Commands Manual sdptool(1)
NAME
sdptool — control and interrogate SDP servers
SYNOPSIS
sdptool [options] {command} [command parameters …]
DESCRIPTION
sdptool provides the interface for performing SDP queries on Bluetooth
devices, and administering a local SDP database.
COMMANDS
The following commands are available. In all cases bdaddr specifies
the device to search or browse. If local is used for bdaddr, then the
local SDP database is searched.
Services are identified and manipulated with a 4-byte record_handle
(NOT the service name). To find a service’s record_handle, look for
the “Service RecHandle” line in the search or browse results
search [–bdaddr bdaddr] [–tree] [–raw] [–xml] service_name
Search for services… Known service names are DID, SP, DUN, LAN, FAX, OPUSH, FTP, HS, HF, HFAG, SAP, NAP, GN, PANU, HCRP, HID, CIP, A2SRC, A2SNK, AVRCT, AVRTG, UDIUE, UDITE and SYNCML.
browse [–tree] [–raw] [–xml] [bdaddr]
Browse all available services on the device specified by a Bluetooth address as a parameter.
records [–tree] [–raw] [–xml] bdaddr
Retrieve all possible service records.
add [ --handle=N --channel=N ]
Add a service to the local SDP database. You can specify a handle for this record using the --handle option. You can specify a channel to add the service on using the --channel option. NOTE: Local adapters configuration will not be updated and this command should be used only for SDP testing.
del record_handle
Remove a service from the local SDP database. NOTE: Local adapters configuration will not be updated and this command should be used only for SDP testing.
get [–tree] [–raw] [–xml] [–bdaddr bdaddr] record_handle
Retrieve a service from the local SDP database.
setattr record_handle attrib_id attrib_value
Set or add an attribute to an SDP record.
setseq record_handle attrib_id attrib_values
Set or add an attribute sequence to an SDP record.
OPTIONS
–help Displays help on using sdptool.
EXAMPLES
sdptool browse 00:80:98:24:15:6D
sdptool browse local
sdptool add DUN
sdptool del 0x10000
BUGS
Documentation needs improving.
AUTHOR
Maxim Krasnyansky . Man page written by Edd Dumbill .
sdptool(1)
Manual page sdptool(1) line 60/82 (END) (press h for help or q to quit)
现在,对“sdptool”有了基本的了解,让我们利用其功能来深入研究蓝牙设备上服务发现的复杂性。`sdptool` 是一个用于配置、控制和询问 SDP(服务发现协议)服务器的多功能工具。此功能使我们能够对蓝牙设备进行详细查询,揭示有关权限的关键信息,并深入了解这些服务中的潜在操作。要开始此探索,请输入“sdptool browser”,然后输入我们之前捕获的 MAC 地址来启动命令。该命令充当全面了解设备服务环境的门户,揭示等待发现的权限、约束和可能性。
~\# sdptool browse 00:1D:A5:00:09:1D
Browsing 00:1D:A5:00:09:1D ...
Service Name: SPP
Service RecHandle: 0x10001
Service Class ID List:
"Serial Port" (ox1101)
Protocol Descriptor List:
"L2CAP" (0x0100)
"RFCOMM" (0x0003)
Channel: 1
在这种情况下,输出提供了对通信领域的更多见解,揭示了设备所使用的协议的复杂性。当我们探索设备内的潜在漏洞时,这些新发现的知识变得至关重要。通过仔细检查细节,我们可能会发现漏洞,确定直接通信的可行性,甚至辨别设备是否采用了 MAC 地址随机化等安全措施。这种多方面的探索为我们提供了在蓝牙侦察工作中做出明智决策和战略行动所需的信息。
第 4 步:使用 l2ping 对蓝牙设备执行 Ping 操作
现在我们已经获取了附近设备的 MAC 地址,我们可以利用 l2ping 对它们进行 ping 操作,无论它们是否处于发现模式,以评估它们的可达性。就我而言,只有一台设备。在继续之前,让我们浏览一下该工具的手册页以了解所有可用选项。
~\# man l2ping
L2PING(1) Linux System Administration L2PING(1)NAME
l2ping - Send L2CAP echo request and receive answerSYNOPSIS
l2ping \[-i \] \[-s size\] \[-c count\] \[-t timeout\] \[-d delay\] \[-f\]
\[-r\] \[-v\] bd\_addrDESCRIPTION
L2ping sends a L2CAP echo request to the Bluetooth MAC address bd\_addr
given in dotted hex notation.OPTIONS
-i The command is applied to device hciX , which must be the name of an installed Bluetooth device (X = 0, 1, 2, ...) If not specified, the command will be sent to the first available Bluetooth device.
-s size The size of the data packets to be sent.
-c count Send count number of packets then exit.
-t timeout Wait timeout seconds for the response.
-d delay Wait delay seconds between pings.
-f Kind of flood ping. Use with care! It reduces the delay time between packets to 0.
-r Reverse ping (gnip?). Send echo response instead of echo request.
-v Verify response payload is identical to request payload. It is not required for remote stacks to return the request payload, but most stacks do (including Bluez).
bd\_addr The Bluetooth MAC address to be pinged in dotted hex notation like 01:02:03:ab:cd:ef or 01:EF:cd:aB:02:03AUTHORS
Written by Maxim Krasnyansky and Marcel Holtmann man page by Nils Faerber , Adam Laurie .BlueZ Jan 22 2002 L2PING(1)Manual page l2ping(1) line 32/54 (END) (press h for help or q to quit)
NAME
l2ping - Send L2CAP echo request and receive answerand receive answer
SYNOPSIS
l2ping \[-i \] \[-s size\] \[-c count\] \[-t timeout\] \[-d delay\] \[-f\]
\[-r\] \[-v\] bd\_addr
DESCRIPTION
L2ping sends a L2CAP echo request to the Bluetooth MAC address bd\_addr
given in dotted hex notation.
OPTIONS
-i The command is applied to device hciX , which must be the name of an installed Bluetooth device (X = 0, 1, 2, ...) If not specified, the command will be sent to the first available Bluetooth device.
-s size The size of the data packets to be sent.
-c count Send count number of packets then exit.
-t timeout Wait timeout seconds for the response.
-d delay Wait delay seconds between pings.
-f Kind of flood ping. Use with care! It reduces the delay time between packets to 0.
-r Reverse ping (gnip?). Send echo response instead of echo request.
-v Verify response payload is identical to request payload. It is not required for remote stacks to return the request payload, but most stacks do (including Bluez).
bd\_addr The Bluetooth MAC address to be pinged in dotted hex notation like 01:02:03:ab:cd:ef or 01:EF:cd:aB:02:03
AUTHORS
Written by Maxim Krasnyansky and Marcel Holtmann
man page by Nils Faerber , Adam Laurie .
BlueZ Jan 22 2002 L2PING(1)
Manual page l2ping(1) line 32/54 (END) (press h for help or q to quit)
我们不需要在这里做任何花哨的事情,只需像这样 ping 蓝牙设备即可:
~\# l2ping 00:1D:A5:00:09:1D
Ping: 00:1D:A5:00:09:1D from ██:██:██:██:██:██ (data size 44) ...
44 bytes from 00:1D:A5:00:09:1D id 0 time 37.57ms
44 bytes from 00:1D:A5:00:09:1D id 1 time 27.23ms
44 bytes from 00:1D:A5:00:09:1D id 2 time 27.59ms
44 bytes from 00:1D:A5:00:09:1D id 3 time 27.31ms
44 bytes from 00:1D:A5:00:09:1D id 4 time 40.99ms
44 bytes from 00:1D:A5:00:09:1D id 5 time 48.77ms
44 bytes from 00:1D:A5:00:09:1D id 6 time 59.93ms
44 bytes from 00:1D:A5:00:09:1D id 7 time 48.84ms
44 bytes from 00:1D:A5:00:09:1D id 8 time 67.59ms
这表明该设备在范围内并且可以访问。
第5步:使用btscanner扫描蓝牙设备
现在,让我们将注意力转向我们武器库中的最后一个工具 - 专为蓝牙设备发现而设计的成熟图形用户界面。它的名称是 btscanner。要启动它,只需输入 btscanner。在继续之前,让我们快速回顾一下该工具的手册页。
~\# man btscanner
BTSCANNER(1) General Commands Manual BTSCANNER(1)NAME
btscanner - ncurses-based scanner for Bluetooth devicesSYNOPSIS
btscanner \[--help\] \[--cfg \] \[--no-reset\]DESCRIPTION
This manual page was written for the Debian GNU/Linux distribution be‐
cause the original program does not have a manual page. btscanner is a tool designed specifically to extract as much informa‐
tion as possible from a Bluetooth device without the requirement to
pair. A detailed information screen extracts HCI and SDP information,
and maintains an open connection to monitor the RSSI and link quality.
btscanner is based on the BlueZ Bluetooth stack, which is included with
recent Linux kernels, and the BlueZ toolset. btscanner also contains a
complete listing of the IEEE OUI numbers and class lookup tables. Using
the information gathered from these sources it is possible to make edu‐
cated guesses as to the host device type.OPTIONS
--help Show a help text and exit.
--cfg Use as the config file.
--no-reset Do not reset the Bluetooth adapter before scanning.BUGS
Please report any bugs to Tim Hurman .LICENCE
btscanner is covered by the GNU General Public License (GPL).SEE ALSO
kismet(1).AUTHORS
Tim Hurman This manual page was written by Uwe Hermann , for
the Debian GNU/Linux system (but may be used by others). April 22, 2006 BTSCANNER(1) Manual page btscanner(1) line 23/45 (END) (press h for help or q to quit)
正如您所观察到的,btscanner 的命令行参数并不多。这是因为 btscanner 是一个图形用户界面 (GUI) 工具,一旦执行该工具,其功能就会变得显而易见。让我们继续运行 btscanner 来揭示它的功能。
~\# btscanner
尽管许多人每天都使用蓝牙,但其工作原理和漏洞往往仍然未知。破解蓝牙可以访问手机和平板电脑上存储的大量个人数据。与 Wi-Fi 不同,蓝牙设备会跳频,使攻击者难以拦截通信。此外,蓝牙会协商一次密钥,从而增强安全性。借助 Kali Linux 上的内置工具,可以进行蓝牙侦察。hciconfig、hcitool、sdptool、l2ping 和 btscanner 等工具可实现设备发现、服务探索和 ping 测试。蓝牙黑客攻击需要近距离,而兼容的适配器可以增强覆盖范围。负责任地执行这些步骤,尊重法律和道德界限。
黑客&网络安全如何学习
今天只要你给我的文章点赞,我私藏的网安学习资料一样免费共享给你们,来看看有哪些东西。
1.学习路线图
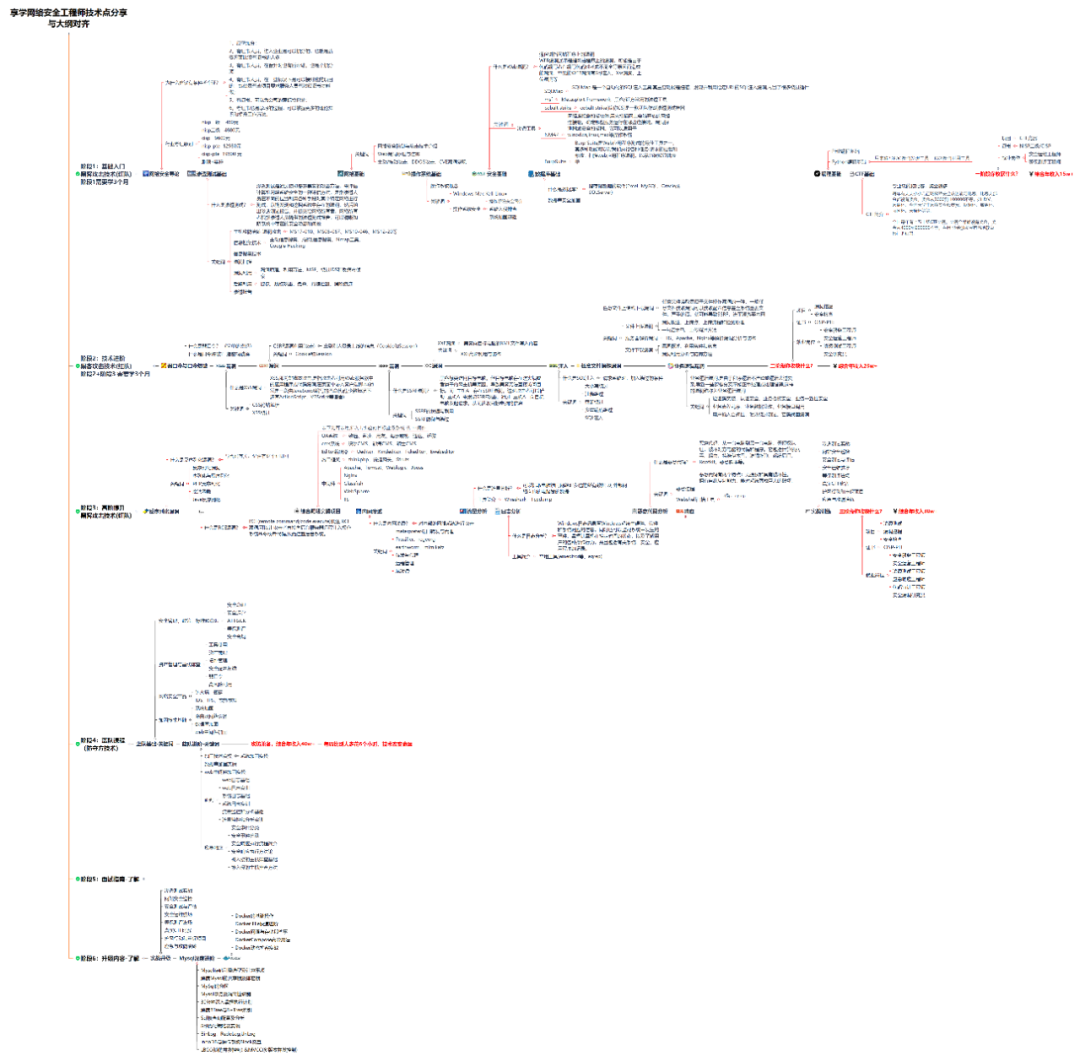
攻击和防守要学的东西也不少,具体要学的东西我都写在了上面的路线图,如果你能学完它们,你去就业和接私活完全没有问题。
2.视频教程
网上虽然也有很多的学习资源,但基本上都残缺不全的,这是我自己录的网安视频教程,上面路线图的每一个知识点,我都有配套的视频讲解。
内容涵盖了网络安全法学习、网络安全运营等保测评、渗透测试基础、漏洞详解、计算机基础知识等,都是网络安全入门必知必会的学习内容。

(都打包成一块的了,不能一一展开,总共300多集)
因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
3.技术文档和电子书
技术文档也是我自己整理的,包括我参加大型网安行动、CTF和挖SRC漏洞的经验和技术要点,电子书也有200多本,由于内容的敏感性,我就不一一展示了。

因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
4.工具包、面试题和源码
“工欲善其事必先利其器”我为大家总结出了最受欢迎的几十款款黑客工具。涉及范围主要集中在 信息收集、Android黑客工具、自动化工具、网络钓鱼等,感兴趣的同学不容错过。
还有我视频里讲的案例源码和对应的工具包,需要的话也可以拿走。

因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
最后就是我这几年整理的网安方面的面试题,如果你是要找网安方面的工作,它们绝对能帮你大忙。
这些题目都是大家在面试深信服、奇安信、腾讯或者其它大厂面试时经常遇到的,如果大家有好的题目或者好的见解欢迎分享。
参考解析:深信服官网、奇安信官网、Freebuf、csdn等
内容特点:条理清晰,含图像化表示更加易懂。
内容概要:包括 内网、操作系统、协议、渗透测试、安服、漏洞、注入、XSS、CSRF、SSRF、文件上传、文件下载、文件包含、XXE、逻辑漏洞、工具、SQLmap、NMAP、BP、MSF…

因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取




























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








