题目虽然没做出来,但是还是要复盘的。
not_wiener
from Crypto.Util.number import *
from gmpy2 import *
import random, os
from hashlib import sha1
from random import randrange
flag=b''
x = bytes_to_long(flag)
def gen_key():
while True:
q = getPrime(160)
p = 2 * getPrime(1024-160) * q+1
if isPrime(p):
break
h = random.randint(1, p - 1)
g = powmod(h,(p-1)//q, p)
y=pow(g,x,p)
return p,q,g,y
def cry():
a =
p = getPrime(512)
q = getPrime(512)
d = getPrime(280)
n = p * q
e = inverse(d, (p - 1) * (q - 1))
c = pow(a, e, n)
return n,e,c
p,q,g,y=gen_key()
k1 = random.randint(1, q-1)
h1 = bytes_to_long(sha1(os.urandom(20)).digest())
r1 = pow(g, k1, p) % q
s1 = ((h1 + x*r1) * invert(k1, q))% q
n,e,c= cry()
a=
b= 17474742587088593627
k2 = a*k1 + b
h2 = bytes_to_long(sha1(os.urandom(20)).digest())
r2 = pow(g, k2, p) % q
s2 = ((h2 + x*r2) * invert(k2, q)) % q
print(n,e,c)
print(p,q,g,y)
print("h1:%s r1:%s s1:%s"%(h1,r1,s1))
print("h2:%s r2:%s s2:%s"%(h2,r2,s2))
n = 98871082998654651904594468693622517613869880791884929588100914778964766348914919202255397776583412976785216592924335179128220634848871563960167726280836726035489482233158897362166942091133366827965811201438682117312550600943385153640907629347663140487841016782054145413246763816202055243693289693996466579973
e = 76794907644383980853714814867502708655721653834095293468287239735547303515225813724998992623067007382800348003887194379223500764768679311862929538017193078946067634221782978912767213553254272722105803768005680182504500278005295062173004098796746439445343896868825218704046110925243884449608326413259156482881
c = 13847199761503953970544410090850216804358289955503229676987212195445226107828814170983735135692611175621170777484117542057117607579344112008580933900051471041224296342157618857321522682033260246480258856376097987259016643294843196752685340912823459403703609796624411954082410762846356541101561523204985391564p= 161310487790785086482919800040790794252181955976860261806376528825054571226885460699399582301663712128659872558133023114896223014064381772944582265101778076462675402208451386747128794418362648706087358197370036248544508513485401475977401111270352593919906650855268709958151310928767086591887892397722958234379
q= 1115861146902610160756777713087325311747309309771
g= 61073566757714587321114447684333928353300944355112378054603585955730395524359123615359185275743626350773632555967063692889668342544616165017003197599818881844811647270423070958521148291118914198811187731689123176313367399492561288350530256722898205674043032421874788802819858438796795768177550638273020791962
y= 23678147495254433946472657196764372220306841739888385605070426528738230369489739339976134564575544246606937803367113623097260181789372915552172469427842482448570540429192377881186772226796452797182435452490307834205012154495575570994963829345053331967442452842152258650027916313982835119514473311305158299360
(h1, r1, s1) = 535874494834828755542711401117152397489711233142, 117859946800380767356190121030392492081340616512, 26966646740134065096660259687229179143947213779
(h2, r2, s2) = 236574518096866758760287021848258048065293279716, 863199000523521111517835459866422731857447792677, 517924607931342012033031470185302567344725962419
这里涉及到了rsa和签名算法
常见的签名算法有
Rsa数字签名,ElGamal和Dsa
这里考查的是DSA
相关信息查阅DSA - CTF Wiki
然后e是非常大的,题目提示不能用维纳攻击,那么该怎么求呢?
这里是需要用到 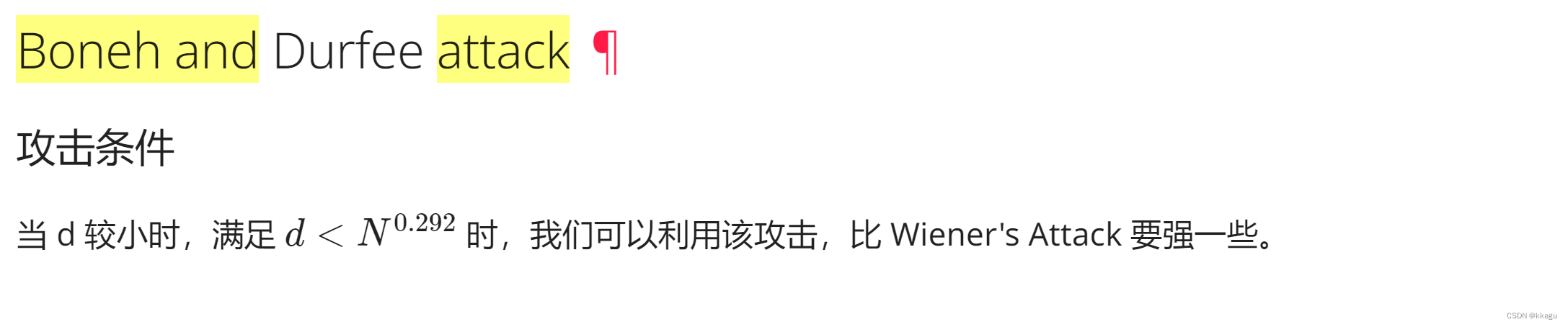
d = getPrime(280),这里刚好满足,然后风大的脚本
#sage
import time
"""
Setting debug to true will display more informations
about the lattice, the bounds, the vectors...
"""
debug = True
"""
Setting strict to true will stop the algorithm (and
return (-1, -1)) if we don't have a correct
upperbound on the determinant. Note that this
doesn't necesseraly mean that no solutions
will be found since the theoretical upperbound is
usualy far away from actual results. That is why
you should probably use `strict = False`
"""
strict = False
"""
This is experimental, but has provided remarkable results
so far. It tries to reduce the lattice as much as it can
while keeping its efficiency. I see no reason not to use
this option, but if things don't work, you should try
disabling it
"""
helpful_only = True
dimension_min = 7 # stop removing if lattice reaches that dimension
############################################
# Functions
##########################################
# display stats on helpful vectors
def helpful_vectors(BB, modulus):
nothelpful = 0
for ii in range(BB.dimensions()[0]):
if BB[ii,ii] >= modulus:
nothelpful += 1
print (nothelpful, "/", BB.dimensions()[0], " vectors are not helpful")
# display matrix picture with 0 and X
def matrix_overview(BB, bound):
for ii in range(BB.dimensions()[0]):
a = ('%02d ' % ii)
for jj in range(BB.dimensions()[1]):
a += '0' if BB[ii,jj] == 0 else 'X'
if BB.dimensions()[0] < 60:
a += ' '
if BB[ii, ii] >= bound:
a += '~'
print (a)
# tries to remove unhelpful vectors
# we start at current = n-1 (last vector)
def remove_unhelpful(BB, monomials, bound, current):
# end of our recursive function
if current == -1 or BB.dimensions()[0] <= dimension_min:
return BB
# we start by checking from the end
for ii in range(current, -1, -1):
# if it is unhelpful:
if BB[ii, ii] >= bound:
affected_vectors = 0
affected_vector_index = 0
# let's check if it affects other vectors
for jj in range(ii + 1, BB.dimensions()[0]):
# if another vector is affected:
# we increase the count
if BB[jj, ii] != 0:
affected_vectors += 1
affected_vector_index = jj
# level:0
# if no other vectors end up affected
# we remove it
if affected_vectors == 0:
print ("* removing unhelpful vector", ii)
BB = BB.delete_columns([ii])
BB = BB.delete_rows([ii])
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii-1)
return BB
# level:1
# if just one was affected we check
# if it is affecting someone else
elif affected_vectors == 1:
affected_deeper = True
for kk in range(affected_vector_index + 1, BB.dimensions()[0]):
# if it is affecting even one vector
# we give up on this one
if BB[kk, affected_vector_index] != 0:
affected_deeper = False
# remove both it if no other vector was affected and
# this helpful vector is not helpful enough
# compared to our unhelpful one
if affected_deeper and abs(bound - BB[affected_vector_index, affected_vector_index]) < abs(bound - BB[ii, ii]):
print ("* removing unhelpful vectors", ii, "and", affected_vector_index)
BB = BB.delete_columns([affected_vector_index, ii])
BB = BB.delete_rows([affected_vector_index, ii])
monomials.pop(affected_vector_index)
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii-1)
return BB
# nothing happened
return BB
"""
Returns:
* 0,0 if it fails
* -1,-1 if `strict=true`, and determinant doesn't bound
* x0,y0 the solutions of `pol`
"""
def boneh_durfee(pol, modulus, mm, tt, XX, YY):
"""
Boneh and Durfee revisited by Herrmann and May
finds a solution if:
* d < N^delta
* |x| < e^delta
* |y| < e^0.5
whenever delta < 1 - sqrt(2)/2 ~ 0.292
"""
# substitution (Herrman and May)
PR.<u, x, y> = PolynomialRing(ZZ)
Q = PR.quotient(x*y + 1 - u) # u = xy + 1
polZ = Q(pol).lift()
UU = XX*YY + 1
# x-shifts
gg = []
for kk in range(mm + 1):
for ii in range(mm - kk + 1):
xshift = x^ii * modulus^(mm - kk) * polZ(u, x, y)^kk
gg.append(xshift)
gg.sort()
# x-shifts list of monomials
monomials = []
for polynomial in gg:
for monomial in polynomial.monomials():
if monomial not in monomials:
monomials.append(monomial)
monomials.sort()
# y-shifts (selected by Herrman and May)
for jj in range(1, tt + 1):
for kk in range(floor(mm/tt) * jj, mm + 1):
yshift = y^jj * polZ(u, x, y)^kk * modulus^(mm - kk)
yshift = Q(yshift).lift()
gg.append(yshift) # substitution
# y-shifts list of monomials
for jj in range(1, tt + 1):
for kk in range(floor(mm/tt) * jj, mm + 1):
monomials.append(u^kk * y^jj)
# construct lattice B
nn = len(monomials)
BB = Matrix(ZZ, nn)
for ii in range(nn):
BB[ii, 0] = gg[ii](0, 0, 0)
for jj in range(1, ii + 1):
if monomials[jj] in gg[ii].monomials():
BB[ii, jj] = gg[ii].monomial_coefficient(monomials[jj]) * monomials[jj](UU,XX,YY)
# Prototype to reduce the lattice
if helpful_only:
# automatically remove
BB = remove_unhelpful(BB, monomials, modulus^mm, nn-1)
# reset dimension
nn = BB.dimensions()[0]
if nn == 0:
print ("failure")
return 0,0
# check if vectors are helpful
if debug:
helpful_vectors(BB, modulus^mm)
# check if determinant is correctly bounded
det = BB.det()
bound = modulus^(mm*nn)
if det >= bound:
print ("We do not have det < bound. Solutions might not be found.")
print ("Try with highers m and t.")
if debug:
diff = (log(det) - log(bound)) / log(2)
print ("size det(L) - size e^(m*n) = ", floor(diff))
if strict:
return -1, -1
else:
print ("det(L) < e^(m*n) (good! If a solution exists < N^delta, it will be found)")
# display the lattice basis
if debug:
matrix_overview(BB, modulus^mm)
# LLL
if debug:
print ("optimizing basis of the lattice via LLL, this can take a long time")
BB = BB.LLL()
if debug:
print ("LLL is done!")
# transform vector i & j -> polynomials 1 & 2
if debug:
print ("looking for independent vectors in the lattice")
found_polynomials = False
for pol1_idx in range(nn - 1):
for pol2_idx in range(pol1_idx + 1, nn):
# for i and j, create the two polynomials
PR.<w,z> = PolynomialRing(ZZ)
pol1 = pol2 = 0
for jj in range(nn):
pol1 += monomials[jj](w*z+1,w,z) * BB[pol1_idx, jj] / monomials[jj](UU,XX,YY)
pol2 += monomials[jj](w*z+1,w,z) * BB[pol2_idx, jj] / monomials[jj](UU,XX,YY)
# resultant
PR.<q> = PolynomialRing(ZZ)
rr = pol1.resultant(pol2)
# are these good polynomials?
if rr.is_zero() or rr.monomials() == [1]:
continue
else:
print ("found them, using vectors", pol1_idx, "and", pol2_idx)
found_polynomials = True
break
if found_polynomials:
break
if not found_polynomials:
print ("no independant vectors could be found. This should very rarely happen...")
return 0, 0
rr = rr(q, q)
# solutions
soly = rr.roots()
if len(soly) == 0:
print ("Your prediction (delta) is too small")
return 0, 0
soly = soly[0][0]
ss = pol1(q, soly)
solx = ss.roots()[0][0]
#
return solx, soly
def example():
############################################
# How To Use This Script
##########################################
#
# The problem to solve (edit the following values)
#
# the modulus
N = 98871082998654651904594468693622517613869880791884929588100914778964766348914919202255397776583412976785216592924335179128220634848871563960167726280836726035489482233158897362166942091133366827965811201438682117312550600943385153640907629347663140487841016782054145413246763816202055243693289693996466579973
# the public exponent
e = 76794907644383980853714814867502708655721653834095293468287239735547303515225813724998992623067007382800348003887194379223500764768679311862929538017193078946067634221782978912767213553254272722105803768005680182504500278005295062173004098796746439445343896868825218704046110925243884449608326413259156482881
# the hypothesis on the private exponent (the theoretical maximum is 0.292)
delta = 0.280 # this means that d < N^delta
#
# Lattice (tweak those values)
#
# you should tweak this (after a first run), (e.g. increment it until a solution is found)
m =10 # size of the lattice (bigger the better/slower)
# you need to be a lattice master to tweak these
t = int((1-2*delta) * m) # optimization from Herrmann and May
X = 2*floor(N^delta) # this _might_ be too much
Y = floor(N^(1/2)) # correct if p, q are ~ same size
#
# Don't touch anything below
#
# Problem put in equation
P.<x,y> = PolynomialRing(ZZ)
A = int((N+1)/2)
pol = 1 + x * (A + y)
#
# Find the solutions!
#
# Checking bounds
if debug:
print ("=== checking values ===")
print ("* delta:", delta)
print ("* delta < 0.292", delta < 0.292)
print ("* size of e:", int(log(e)/log(2)))
print ("* size of N:", int(log(N)/log(2)))
print ("* m:", m, ", t:", t)
# boneh_durfee
if debug:
print ("=== running algorithm ===")
start_time = time.time()
solx, soly = boneh_durfee(pol, e, m, t, X, Y)
# found a solution?
if solx > 0:
print ("=== solution found ===")
if False:
print ("x:", solx)
print ("y:", soly)
d = int(pol(solx, soly) / e)
print ("private key found:", d)
else:
print ("=== no solution was found ===")
if debug:
print("=== %s seconds ===" % (time.time() - start_time))
if __name__ == "__main__":
example() 原先代码m=4,这里需要调试到10,此外sagemath运作时间挺长才得到d
输出:
=== checking values ===
* delta: 0.280000000000000
* delta < 0.292 True
* size of e: 1022
* size of N: 1023
* m: 10 , t: 4
=== running algorithm ===
* removing unhelpful vector 88
* removing unhelpful vector 87
* removing unhelpful vector 82
* removing unhelpful vector 75
* removing unhelpful vector 66
* removing unhelpful vectors 1 and 2
* removing unhelpful vector 0
35 / 82 vectors are not helpful
We do not have det < bound. Solutions might not be found.
Try with highers m and t.
size det(L) - size e^(m*n) = 833
00 X000000000000000000000000000000000000000000000000000000000000000000000000000000000~
01 XX00000000000000000000000000000000000000000000000000000000000000000000000000000000~
02 XXX0000000000000000000000000000000000000000000000000000000000000000000000000000000
03 000X000000000000000000000000000000000000000000000000000000000000000000000000000000~
04 000XX00000000000000000000000000000000000000000000000000000000000000000000000000000~
05 000XXX0000000000000000000000000000000000000000000000000000000000000000000000000000
06 000XXXX000000000000000000000000000000000000000000000000000000000000000000000000000
07 0000000X00000000000000000000000000000000000000000000000000000000000000000000000000~
08 0000000XX0000000000000000000000000000000000000000000000000000000000000000000000000~
09 0000000XXX000000000000000000000000000000000000000000000000000000000000000000000000~
10 0000000XXXX00000000000000000000000000000000000000000000000000000000000000000000000
11 0000000XXXXX0000000000000000000000000000000000000000000000000000000000000000000000
12 000000000000X000000000000000000000000000000000000000000000000000000000000000000000~
13 000000000000XX00000000000000000000000000000000000000000000000000000000000000000000~
14 000000000000XXX0000000000000000000000000000000000000000000000000000000000000000000~
15 000000000000XXXX000000000000000000000000000000000000000000000000000000000000000000
16 000000000000XXXXX00000000000000000000000000000000000000000000000000000000000000000
17 000000000000XXXXXX0000000000000000000000000000000000000000000000000000000000000000
18 000000000000000000X000000000000000000000000000000000000000000000000000000000000000~
19 000000000000000000XX00000000000000000000000000000000000000000000000000000000000000~
20 000000000000000000XXX0000000000000000000000000000000000000000000000000000000000000~
21 000000000000000000XXXX000000000000000000000000000000000000000000000000000000000000~
22 000000000000000000XXXXX00000000000000000000000000000000000000000000000000000000000
23 000000000000000000XXXXXX0000000000000000000000000000000000000000000000000000000000
24 000000000000000000XXXXXXX000000000000000000000000000000000000000000000000000000000
25 0000000000000000000000000X00000000000000000000000000000000000000000000000000000000~
26 0000000000000000000000000XX0000000000000000000000000000000000000000000000000000000~
27 0000000000000000000000000XXX000000000000000000000000000000000000000000000000000000~
28 0000000000000000000000000XXXX00000000000000000000000000000000000000000000000000000~
29 0000000000000000000000000XXXXX0000000000000000000000000000000000000000000000000000
30 0000000000000000000000000XXXXXX000000000000000000000000000000000000000000000000000
31 0000000000000000000000000XXXXXXX00000000000000000000000000000000000000000000000000
32 0000000000000000000000000XXXXXXXX0000000000000000000000000000000000000000000000000
33 000000000000000000000000000000000X000000000000000000000000000000000000000000000000~
34 000000000000000000000000000000000XX00000000000000000000000000000000000000000000000~
35 000000000000000000000000000000000XXX0000000000000000000000000000000000000000000000~
36 000000000000000000000000000000000XXXX000000000000000000000000000000000000000000000~
37 000000000000000000000000000000000XXXXX00000000000000000000000000000000000000000000~
38 000000000000000000000000000000000XXXXXX0000000000000000000000000000000000000000000
39 000000000000000000000000000000000XXXXXXX000000000000000000000000000000000000000000
40 000000000000000000000000000000000XXXXXXXX00000000000000000000000000000000000000000
41 000000000000000000000000000000000XXXXXXXXX0000000000000000000000000000000000000000
42 000000000000000000000000000000000000000000X000000000000000000000000000000000000000~
43 000000000000000000000000000000000000000000XX00000000000000000000000000000000000000~
44 000000000000000000000000000000000000000000XXX0000000000000000000000000000000000000~
45 000000000000000000000000000000000000000000XXXX000000000000000000000000000000000000~
46 000000000000000000000000000000000000000000XXXXX00000000000000000000000000000000000~
47 000000000000000000000000000000000000000000XXXXXX0000000000000000000000000000000000~
48 000000000000000000000000000000000000000000XXXXXXX000000000000000000000000000000000
49 000000000000000000000000000000000000000000XXXXXXXX00000000000000000000000000000000
50 000000000000000000000000000000000000000000XXXXXXXXX0000000000000000000000000000000
51 000000000000000000000000000000000000000000XXXXXXXXXX000000000000000000000000000000
52 0000000000000000000000000000000000000000000000000000X00000000000000000000000000000~
53 0000000000000000000000000000000000000000000000000000XX0000000000000000000000000000~
54 0000000000000000000000000000000000000000000000000000XXX000000000000000000000000000~
55 0000000000000000000000000000000000000000000000000000XXXX00000000000000000000000000~
56 0000000000000000000000000000000000000000000000000000XXXXX0000000000000000000000000~
57 0000000000000000000000000000000000000000000000000000XXXXXX000000000000000000000000~
58 0000000000000000000000000000000000000000000000000000XXXXXXX00000000000000000000000
59 0000000000000000000000000000000000000000000000000000XXXXXXXX0000000000000000000000
60 0000000000000000000000000000000000000000000000000000XXXXXXXXX000000000000000000000
61 0000000000000000000000000000000000000000000000000000XXXXXXXXXX00000000000000000000
62 0000000000000000000000000000000000000000000000000000XXXXXXXXXXX0000000000000000000
63 XXX0XXX00000000000000000000000000000000000000000000000000000000X000000000000000000
64 000XXXX0XXXX0000000000000000000000000000000000000000000000000000X00000000000000000
65 0000000XXXXX0XXXXX00000000000000000000000000000000000000000000000X0000000000000000
66 000000000000XXXXXX0XXXXXX00000000000000000000000000000000000000000X000000000000000
67 000000000000000000XXXXXXX0XXXXXXX0000000000000000000000000000000000X00000000000000
68 0000000000000000000000000XXXXXXXX0XXXXXXXX00000000000000000000000000X0000000000000
69 000000000000000000000000000000000XXXXXXXXX0XXXXXXXXX00000000000000000X000000000000
70 000000000000000000000000000000000000000000XXXXXXXXXX0XXXXXXXXXX0000000X00000000000
71 000XXXX0XXXX00XXXX0000000000000000000000000000000000000000000000XX00000X0000000000
72 0000000XXXXX0XXXXX00XXXXX0000000000000000000000000000000000000000XX00000X000000000
73 000000000000XXXXXX0XXXXXX00XXXXXX000000000000000000000000000000000XX00000X00000000
74 000000000000000000XXXXXXX0XXXXXXX00XXXXXXX0000000000000000000000000XX00000X0000000
75 0000000000000000000000000XXXXXXXX0XXXXXXXX00XXXXXXXX0000000000000000XX00000X000000
76 000000000000000000000000000000000XXXXXXXXX0XXXXXXXXX00XXXXXXXXX000000XX00000X00000
77 0000000XXXXX0XXXXX00XXXXX000XXXXX00000000000000000000000000000000XXX0000XX000X0000
78 000000000000XXXXXX0XXXXXX00XXXXXX000XXXXXX000000000000000000000000XXX0000XX000X000
79 000000000000000000XXXXXXX0XXXXXXX00XXXXXXX000XXXXXXX000000000000000XXX0000XX000X00
80 0000000000000000000000000XXXXXXXX0XXXXXXXX00XXXXXXXX000XXXXXXXX00000XXX0000XX000X0
81 000000000000000000XXXXXXX0XXXXXXX00XXXXXXX000XXXXXXX0000XXXXXXX0000XXXX000XXX00XXX
optimizing basis of the lattice via LLL, this can take a long time
LLL is done!
looking for independent vectors in the lattice
found them, using vectors 0 and 1
=== solution found ===
private key found: 1493519932573300884636712093929290985070801830526216141153447882450934993737739146621
=== 120.1167061328888 seconds ===得到 d=1493519932573300884636712093929290985070801830526216141153447882450934993737739146621
所以可以求得a
d=1493519932573300884636712093929290985070801830526216141153447882450934993737739146621
a=pow(c,d,n)
print(a)
#a=24601959430759983424400804734518943158892550216065342062971649989571838687333接下来就是DSA的线性k攻击了,就是把两次签名的式子消元解出私钥x,也就是flag
s1*k1^-1 = (h1 + x*r1) % q
s2*(ak1+b)^-1 = (h2 + x*r2) )% q
乘以相对应的逆元
(h1 + xr1) = k1s1 (mod q)
(h2 + xr2) = (ak1 + b)s2 (mod q)
移项后分别乘以r2和r1
xr1r2 = (s1k1 - h1)r2 (mod q)
xr1r2 = ((ak1 + b)s2 - h2)r1 (mod q)两式消元得到
k1(s1r2 - s2ar1) = h1r2 - h2r1 + s2br1 (mod q)求得k1,代入任意式子可求x
import gmpy2
from Crypto.Util.number import *
a = 24601959430759983424400804734518943158892550216065342062971649989571838687333
b = 17474742587088593627
p= 161310487790785086482919800040790794252181955976860261806376528825054571226885460699399582301663712128659872558133023114896223014064381772944582265101778076462675402208451386747128794418362648706087358197370036248544508513485401475977401111270352593919906650855268709958151310928767086591887892397722958234379
q= 1115861146902610160756777713087325311747309309771
(h1, r1, s1) = 535874494834828755542711401117152397489711233142, 117859946800380767356190121030392492081340616512, 26966646740134065096660259687229179143947213779
(h2, r2, s2) = 236574518096866758760287021848258048065293279716, 863199000523521111517835459866422731857447792677, 517924607931342012033031470185302567344725962419
print(a)
k1 = (h1*r2 - h2*r1 + s2*b*r1) *gmpy2.invert(s1*r2-s2*a*r1,q)%q
print(k1)
x=(k1*s1-h1)*gmpy2.invert(r1,q) %q
print(long_to_bytes(x))#l1near_k1s_unsafe
CF is Crypto Faker
题目内容:学过AI的都知道,这题不是“纯密码”,密码假面人要披上AI的战衣,但他永远不会卸下密码的假面。
打开附件有挺多py文件,眼花缭乱了,这里的话写关键内容
task.py
from Crypto.Util.number import *
import initialize
import train
import valid
import test
import rec
from secret import message, flag_point
flag = b"flag{" + long_to_bytes(message) + long_to_bytes(flag_point) + b".}"
p = getPrime(512)
q = getPrime(512)
n = p * q
print("The significant parameter n: %s" % hex(n))
phi0 = (p - 1) * (q - 1)
r = rec.rec(p, q)
print("The unique parameter r: %s" % hex(r))
parameters = initialize.initialize(p, q)
wild_phi = parameters[0]
wild_e = parameters[1]
print("------")
print("Parameters are initialized to: \n phi:%s\n" % hex(wild_phi), " e:%s" % hex(wild_e))
print("But they are wild and crazy!")
print("We have to give them a lesson!")
print("------")
parameters = train.train(wild_phi, wild_e, n, r, phi0)
trained_phi = parameters[0]
trained_e = parameters[1]
print("Parameters are trained to: \n phi:%s\n" % hex(trained_phi), " e:%s" % hex(trained_e))
print("After training, the two naughty parameters are more and more normal.")
print("It's closer to your target!")
print("------")
parameters = valid.valid(trained_phi, trained_e, n)
y_valid = parameters[0]
print("The encrypted output in validation set is %s" % hex(y_valid))
print("After validation, the model is more and more stable.")
print("To test the real flag!")
print("------")
parameters = test.test(trained_phi, trained_e, n)
y_hat_cipher1 = parameters[0]
y_hat_cipher2 = parameters[1]
print("The final output is \n%s" % hex(y_hat_cipher1), "\n%s" % hex(y_hat_cipher2))
print("------")告诉我们flag有两部分
The significant parameter n: 0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709b3d2698476b6dd203811b6a2ec6a6e2a7e213ab719bcd3ab49bb864b10e9c78ea3f501c0e2213dfe431043bb6f0cc2e8d77bfb43869b843af1a99ae81b87811e101
The unique parameter r: 0x4f37fe985d13ffde9867fa0063f68dea79196408b1404eadf03ea59297d629c2183a4a6a6647b6c4c99dd43bae8c4fa4691a608d20170fd42b18aef7efb3ae01cd3
------
Parameters are initialized to:
phi:0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709648d78eb17edb46dda768a97d57e6bd1c48657393b7c0d9c574c38cc0a3545ce7d209ade33b8ac6b31a41fe9f4ed62b4ddd7b99859b74915f2031dd2f5f0499a2f8
e:0x2ebad696da6dda845bf03fdf34ee73d4849800de9267a5baa3c068e2d33a74727d00002fbfea775e5233087a9039d267130aa924a4f7fed3576f6ff7b8e1b2e8
But they are wild and crazy!
We have to give them a lesson!
------
The loss is -0x5144bdad7cc24f5348c5752dda0ff5fa7d72e36370d5af55eb6f590ac0764b843a06ee1a4651b8f3a6c878df56f1678454e58eaf0ede9a1eb0503dce6a1303b69e33bbaad112abb051a28d51a9fee629e89400a338bd02998568d044852f11e05572fc4a0ddacdf7342048295a4025394e77e973621a77ea5bbdb06af2cb72b2f8298e2cd16736454fd066d3d96a4f77cd094cd783ead17024de981df7ade84aa8c282b1ec6f8ec6ec4752727387ef637ba2a4eed8f83c77d5db14d297de8098
Parameters are trained to:
phi:0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709b3bb712fdcba325655f111918472d4353a66854ccda50b63a1047278c15a4b39cde898d054db87092958c7c05f8fa566dcd969b1ff4b7d1935c375a4af3bfc341b0
e:0x2c22193ad9abcca2f67552fc76dd07b3ef883f3d755c95119cdf82bb6a07c970fd37e582bb49250d8efaa29b8a59c82059165c654206a9d7261f6b45a90dc69
After training, the two naughty parameters are more and more normal.
It's closer to your target!
------
The encrypted output in validation set is 0x775cbee546e7579f0a69645b59f72f5c8ff0c538dd9a6e755969dee2ffb8748073c089557801dfb8bfae15baba9a909f3addac142ad928ac7cc453c72166dda235128de12965df4308997416e054ab1ab9af55c60533c7374096aa2d05339900b3e14f7148930bf083eb1eb9fa22b9a997f85b39501d3a9bdfa08e3389b8f2fe
After validation, the model is more and more stable.
To test the real flag!
------
The final output is
0x29289e3d9275147b885b5061637564cbee3e4d9f48e52694e594f020e49da9b24d9246b2437fb2221fa86ca1a277f3fdd7ab5cad4738a02b66d47703ef816844a84c6c209c8251e8961c9ba2c791649e022627f86932d9700c3b1dc086e8b2747d0a5604955387a935464d3866dd4100b2f3d57603c728761d1d8ef7fdbdcbee
0x2b0059f88454e0e36269c809b5d5b6b28e5bab3c87b20f9e55635239331100a0a582241e7a385034698b61ebf24b519e868617ff67974cc907cc61be38755737f9a6dbeb7890ff55550b1af1ecf635112fcaaa8b07a3972b3c6728cbcf2a3973a4d7bd92affec7e065e0ae83cd36858e6d983785a3668a8b82709d78a69796af
------
所以的都告诉我们了,基础解密,真非预期(泪目了)
import gmpy2
from Crypto.Util.number import long_to_bytes
n= 0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709b3d2698476b6dd203811b6a2ec6a6e2a7e213ab719bcd3ab49bb864b10e9c78ea3f501c0e2213dfe431043bb6f0cc2e8d77bfb43869b843af1a99ae81b87811e101
# r: 0x4f37fe985d13ffde9867fa0063f68dea79196408b1404eadf03ea59297d629c2183a4a6a6647b6c4c99dd43bae8c4fa4691a608d20170fd42b18aef7efb3ae01cd3
phi:0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709648d78eb17edb46dda768a97d57e6bd1c48657393b7c0d9c574c38cc0a3545ce7d209ade33b8ac6b31a41fe9f4ed62b4ddd7b99859b74915f2031dd2f5f0499a2f8
e:0x2ebad696da6dda845bf03fdf34ee73d4849800de9267a5baa3c068e2d33a74727d00002fbfea775e5233087a9039d267130aa924a4f7fed3576f6ff7b8e1b2e8
# The loss is -0x5144bdad7cc24f5348c5752dda0ff5fa7d72e36370d5af55eb6f590ac0764b843a06ee1a4651b8f3a6c878df56f1678454e58eaf0ede9a1eb0503dce6a1303b69e33bbaad112abb051a28d51a9fee629e89400a338bd02998568d044852f11e05572fc4a0ddacdf7342048295a4025394e77e973621a77ea5bbdb06af2cb72b2f8298e2cd16736454fd066d3d96a4f77cd094cd783ead17024de981df7ade84aa8c282b1ec6f8ec6ec4752727387ef637ba2a4eed8f83c77d5db14d297de8098
phi=0x81c5f040bfaea676120cd62c36ba7afb303561504bbf8609afa3da60fb6202ca875b0bd2a06143ebcd16fa615557ff159d97909160d68e1938b3ecaf57709b3bb712fdcba325655f111918472d4353a66854ccda50b63a1047278c15a4b39cde898d054db87092958c7c05f8fa566dcd969b1ff4b7d1935c375a4af3bfc341b0
e=0x2c22193ad9abcca2f67552fc76dd07b3ef883f3d755c95119cdf82bb6a07c970fd37e582bb49250d8efaa29b8a59c82059165c654206a9d7261f6b45a90dc69
# 0x775cbee546e7579f0a69645b59f72f5c8ff0c538dd9a6e755969dee2ffb8748073c089557801dfb8bfae15baba9a909f3addac142ad928ac7cc453c72166dda235128de12965df4308997416e054ab1ab9af55c60533c7374096aa2d05339900b3e14f7148930bf083eb1eb9fa22b9a997f85b39501d3a9bdfa08e3389b8f2fe
c1=0x29289e3d9275147b885b5061637564cbee3e4d9f48e52694e594f020e49da9b24d9246b2437fb2221fa86ca1a277f3fdd7ab5cad4738a02b66d47703ef816844a84c6c209c8251e8961c9ba2c791649e022627f86932d9700c3b1dc086e8b2747d0a5604955387a935464d3866dd4100b2f3d57603c728761d1d8ef7fdbdcbee
c2=0x2b0059f88454e0e36269c809b5d5b6b28e5bab3c87b20f9e55635239331100a0a582241e7a385034698b61ebf24b519e868617ff67974cc907cc61be38755737f9a6dbeb7890ff55550b1af1ecf635112fcaaa8b07a3972b3c6728cbcf2a3973a4d7bd92affec7e065e0ae83cd36858e6d983785a3668a8b82709d78a69796af
d=gmpy2.invert(e,phi)
m1=pow(c1,d,n)
m2=pow(c2,d,n)
print(long_to_bytes(m1)+long_to_bytes(m2))
#b"With the method of machine learning, it is available for Crypto-er to develop the modern cryptography.Don't give up learning crypto"
ez_ECC太难了,日后补






















 5263
5263











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








