@ WK01: Crypto Building Blocks
Public key and Prviate key
公钥私钥是不对称的
不对称指的是用一把钥匙锁住必须用另一把钥匙打开
Alic拥有Bob的公钥,利用Bob的公钥加密plaintext m,再将m发送给Bob,只有用Bob的私钥才能重新获得明文m.(用Bob的公钥解密是解不开的)
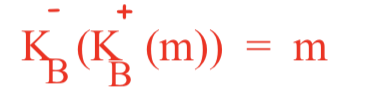
-为私钥 +为公钥
disadvantage: the speed is slower than symmetry cryptography method as may require exponential computation.
advantage: safe
Symmetric Key Cryptography
有一个钥匙的加密方式为对称加密(通过一个众所周知的加密算法)
但这样就不能随意在公网上传递秘钥
若有人截取就可以随意破解加密信息
RSA
RSA (Rivest–Shamir–Adleman) is one of the first public-key cryptosystems
即使用公钥私钥加密方式的加密系统
Hash Function
用来确定报文的完整性
1)报文来自Alice
2)该报文在到Bob的图中没有被篡改
SHA:Secure Hash Algorithms
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS), including:
SHA-0: A retronym applied to the original version of the 160-bit hash function published in 1993 under the name “SHA”. It was withdrawn shortly after publication due to an undisclosed “significant flaw” and replaced by the slightly revised version SHA-1.
SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010.
SHA-2: A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size; SHA-256 uses 32-bit words where SHA-512 uses 64-bit words. There are also truncated versions of each standard, known as SHA-224, SHA-384, SHA-512/224 and SHA-512/256. These were also designed by the NSA.
SHA-3: A hash function formerly called Keccak, chosen in 2012 after a public competition among non-NSA designers. It supports the same hash lengths as SHA-2, and its internal structure differs significantly from the rest of the SHA family.
通过比对(m,H(m)),if H’(m) == H(m) 完整 else 不完整
HMAC : sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code
It may be used to simultaneously verify both the data integrity and the authentication of a message, as with any MAC.
MAC:message authentication code
报文鉴别码:改变计算散列的方法,在原来计算的基础上加一个报文鉴别码MAC,即H(m+s),alice 和bob都知道这个MAC,Bob通过再次计算H(m+s)来比对Alice发过来的H(m+s),来确定报文的完整性
DIgital signatures
Bob用自己的私钥加密发送给Bob
若Alice可以用Bob的公钥打开,则可以证明:
• Bob signed m
• no one else signed m
• Bob signed m and not m‘
workflow:
若Alice能够用Bob的公钥获得散列值k,且H(m) = k,即可证明:
• Bob signed m
• no one else signed m
• Bob signed m and not m‘
Cipher Block Chaining
CBC: Sender
有两种加密方法
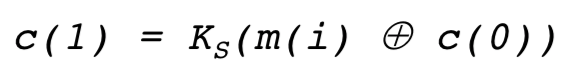
每个块和第一个块进行异或运算然后在用加密算法加密
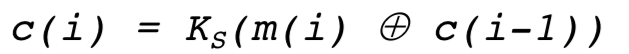
每个块和这个块的前一块进行异或运算然后在用加密算法加密
CBC: Receiver
























 3787
3787











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








