
互联网安全协议(Internet Protocol Security,IPSec)是一个应用在OSI网络层保护基于TCP或UDP的协议簇(主要有AH、ESP、SA、IKE),通过对IP协议的分组进行加密和认证来保护IP协议的网络传输安全。

一、IPSec体系结构
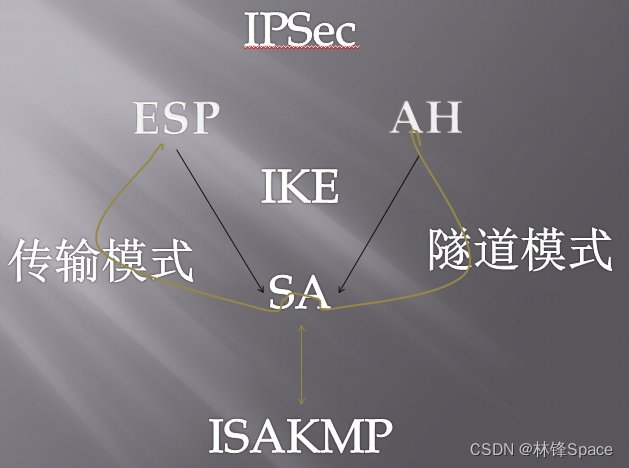
1、安全协议
(1)AH协议
Authentication Header
认证头,保证被传输分组的完整性和可靠性。此外,AH还保护不受重放攻击。
在服务两端根据算法独立交换秘钥,根据秘钥和数据包产生一个校验项,收据在对端被接收后进行校验。从而保证数据包来源的确认以及数据包不被非法修改。
(2)ESP协议
Encapsulating Security Payload
封装安全载荷,保证分组源可靠性、完整性和保密性,与AH不同的是,ESP不对IP分组的头部进行安全保护,只保护Payload,即负载数据。
同时,AH虽然可以保护通信免受篡改,但并不进行加密,数据对于黑客而言是可见的,为了进一步保证数据传输安全,ESP,提供了加密。
2、安全联盟SA
安全联盟(Security Association)SA,也叫安全关联,是IPSec的基础。记录每条IP安全通路的策略和策略参数,是通信双方建立的一种协议,决定了用来保护数据包的协议、转码方式、秘钥以及秘钥有效期等。AH和ESP都要用到安全联盟,IKE的一个主要功能就是建立和维护安全联盟SA。
SA可以定义两种模式
(1)传输模式
传输模式保护IP包内的数据载荷
(2)隧道模式
隧道模式保护整个IP数据包,只要安全联盟的任意一端是安全网关,SA就必须是隧道模式
3、秘钥管理协议
秘钥管理协议ISAKMP(Internet Security Association and Key Management Protocol),提供共享安全信息,实现IPSec的秘钥管理,为身份认证的SA设置以及秘钥交换技术。
二、IPSec应用实验设计
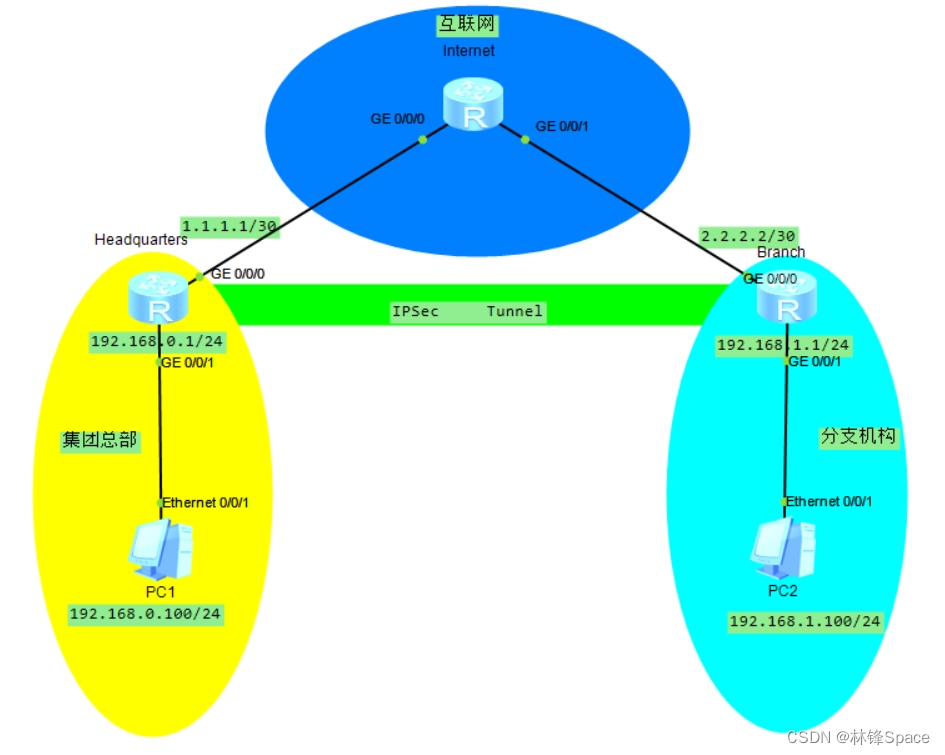
1、网络拓扑
配置总部与分支之间通过IKE动态协商方式建立IPSec隧道
2、配置项
| 配置项 | Headquarters | Branch | |
| IPSec安全提议 | 封装模式 | 隧道模式 | 隧道模式 |
| 安全协议 | ESP | ESP | |
| ESP协议验证算法 | SHA2-256 | SHA2-256 | |
| ESP协议加密算法 | AES-128 | AES-128 | |
| IKE对等体 | 协商模式 | 主模式 | 主模式 |
| 加密算法 | AES-cbc-128 | AES-cbc-128 | |
| 认证算法 | SHA1 | SHA1 | |
| DH Group | GROUP2 | GROUP2 | |
| 预共享密钥 | Key123 | Key123 | |
| 身份类型 | IP地址 | IP地址 | |
| 版本 | V1 | V1 | |
3、组网需求
(1)Headquarters和Branch之间建立IPSec安全隧道,对PC 1与PC 2之间的数据流进行安全保护。
(2)Headquarters和Branch建立IPSec连接,Headquarters和Branch都配置DPD。通过配置DPD技术来监测Headquarters与Branch间IPSec对等体的存活情况。
4、实验步骤
(1)连通性
(2)ACL识别兴趣流
(3)安全协议
(4)安全策略
(5)应用安全策略
(6)测试及抓包分析
三、IPSec实验配置
1、连通性
(1)接口配置
Headquarters
Headquarters
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sysn Headquarters
[Headquarters]int gi 0/0/0
[Headquarters-GigabitEthernet0/0/0]ip add 1.1.1.1 30
[Headquarters-GigabitEthernet0/0/0]q
[Headquarters]int gi 0/0/1
[Headquarters-GigabitEthernet0/0/1]ip add 192.168.0.1 24
[Headquarters-GigabitEthernet0/0/1]q
Branch
Branch
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sysn Branch
[Branch]int gi 0/0/0
[Branch-GigabitEthernet0/0/0]ip add 2.2.2.2 30
[Branch-GigabitEthernet0/0/0]q
[Branch]int gi 0/0/1
[Branch-GigabitEthernet0/0/1]ip add 192.168.1.1 24
[Branch-GigabitEthernet0/0/1]qInternet
Internet
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sysn Internet
[Internet]int gi 0/0/0
[Internet-GigabitEthernet0/0/0]ip add 1.1.1.2 30
[Internet-GigabitEthernet0/0/0]q
[Internet]int gi 0/0/1
[Internet-GigabitEthernet0/0/1]ip add 2.2.2.1 30
[Internet-GigabitEthernet0/0/1]q(2)模拟互联网,通过ospf配置路由器之间外网互通
Headquarters
Headquarters
[Headquarters]ospf
[Headquarters-ospf-1]area 0
[Headquarters-ospf-1-area-0.0.0.0]net 1.1.1.1 0.0.0.0
[Headquarters-ospf-1-area-0.0.0.0]q
[Headquarters-ospf-1]qBranch
Branch
[Branch]ospf
[Branch-ospf-1]area 0
[Branch-ospf-1-area-0.0.0.0]net 2.2.2.2 0.0.0.0
[Branch-ospf-1-area-0.0.0.0]q
[Branch-ospf-1]qInternet
Internet
[Internet]ospf
[Internet-ospf-1]area 0
[Internet-ospf-1-area-0.0.0.0]net 1.1.1.2 0.0.0.0
[Internet-ospf-1-area-0.0.0.0]net 2.2.2.1 0.0.0.0
[Internet-ospf-1-area-0.0.0.0]q
[Internet-ospf-1]q
[Internet]q
<Internet>dis ospf peer
OSPF Process 1 with Router ID 1.1.1.2
Neighbors
Area 0.0.0.0 interface 1.1.1.2(GigabitEthernet0/0/0)'s neighbors
Router ID: 1.1.1.1 Address: 1.1.1.1
State: Full Mode:Nbr is Slave Priority: 1
DR: 1.1.1.2 BDR: 1.1.1.1 MTU: 0
Dead timer due in 34 sec
Retrans timer interval: 5
Neighbor is up for 00:00:52
Authentication Sequence: [ 0 ]
Neighbors
Area 0.0.0.0 interface 2.2.2.1(GigabitEthernet0/0/1)'s neighbors
Router ID: 2.2.2.2 Address: 2.2.2.2
State: Full Mode:Nbr is Master Priority: 1
DR: 2.2.2.1 BDR: 2.2.2.2 MTU: 0
Dead timer due in 39 sec
Retrans timer interval: 5
Neighbor is up for 00:00:05
Authentication Sequence: [ 0 ]
<Internet>dis ospf rout
<Internet>dis ospf routing
OSPF Process 1 with Router ID 1.1.1.2
Routing Tables
Routing for Network
Destination Cost Type NextHop AdvRouter Area
1.1.1.0/30 1 Transit 1.1.1.2 1.1.1.2 0.0.0.0
2.2.2.0/30 1 Transit 2.2.2.1 1.1.1.2 0.0.0.0
Total Nets: 2
Intra Area: 2 Inter Area: 0 ASE: 0 NSSA: 0
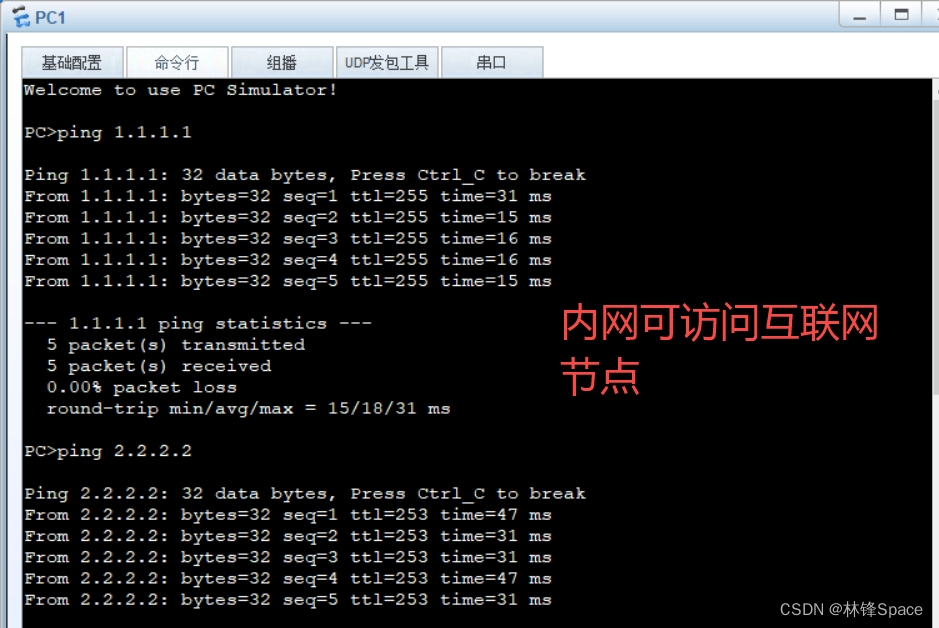
这个时候完全模拟互联网环境,外网之间互联互通。
(3)NAT配置,模拟内网访问互联网模式
Headquarters
Headquarters
[Headquarters]acl 2000
[Headquarters-acl-basic-2000]rule pe so 192.168.0.0 0.0.0.255 //配置允许进行NAT转换的内网地址段
[Headquarters-acl-basic-2000]q
[Headquarters]int gi 0/0/0
[Headquarters-GigabitEthernet0/0/0]nat ou
[Headquarters-GigabitEthernet0/0/0]nat outbound 2000 //在出接口上配置Easy IP方式的NAT
[Headquarters-GigabitEthernet0/0/0]q
[Headquarters]ip rou
[Headquarters]ip route
[Headquarters]ip route-static 0.0.0.0 0.0.0.0 1.1.1.2 //配置默认路由,保证出接口到对端路由可达
[Headquarters]dis nat outbound
NAT Outbound Information:
--------------------------------------------------------------------------
Interface Acl Address-group/IP/Interface Type
--------------------------------------------------------------------------
GigabitEthernet0/0/0 2000 1.1.1.1 easyip
--------------------------------------------------------------------------
Total : 1
Branch
Branch
[Branch]acl 2000
[Branch-acl-basic-2000]ru per so 192.168.1.0 0.0.0.255
[Branch-acl-basic-2000]q
[Branch]int gi 0/0/0
[Branch-GigabitEthernet0/0/0]nat outbound 2000
[Branch-GigabitEthernet0/0/0]q
[Branch]ip route-static 0.0.0.0 0.0.0.0 2.2.2.1
[Branch]dis nat outbound
NAT Outbound Information:
--------------------------------------------------------------------------
Interface Acl Address-group/IP/Interface Type
--------------------------------------------------------------------------
GigabitEthernet0/0/0 2000 2.2.2.2 easyip
--------------------------------------------------------------------------
Total : 1
此时,已完全模拟出企业内外网互联互通情况。
2、配置ACL感兴趣流
Headquarters
配置ACL 3000,匹配从总部子网到分支子网的流量
[Headquarters]acl 3000
[Headquarters-acl-adv-3000]ru pe ip so 192.168.0.0 0.0.0.255 de 192.168.1.0 0.0.
0.255
[Headquarters-acl-adv-3000]qBranch
配置ACL 3000,匹配从分支子网到总部子网的流量
[Branch]acl 3000
[Branch-acl-adv-3000]ru per ip so 192.168.1.0 0.0.0.255 de 192.168.0.0 0.0.0.255
[Branch-acl-adv-3000]q3、配置安全协议
(1)配置IPSec提议
Headquarters
[Headquarters]ipsec proposal def
[Headquarters-ipsec-proposal-def]esp authentication-algorithm sha2-256 //认证算法
[Headquarters-ipsec-proposal-def]esp encryption-algorithm aes-128 //加密算法
[Headquarters-ipsec-proposal-def]q
Branch配置IPSec提议配置同Headquarters
(2)配置IKE提议
Headquarters
[Headquarters]ike proposal 5
[Headquarters-ike-proposal-5]encryption-algorithm ? //加密算法
3des-cbc 168 bits 3DES-CBC
aes-cbc-128 Use AES-128
aes-cbc-192 Use AES-192
aes-cbc-256 Use AES-256
des-cbc 56 bits DES-CBC
[Headquarters-ike-proposal-5]encryption-algorithm aes-cbc-128
[Headquarters-ike-proposal-5]authentication-algorithm ? //认证算法
aes-xcbc-mac-96 Select aes-xcbc-mac-96 as the hash algorithm
md5 Select MD5 as the hash algorithm
sha1 Select SHA as the hash algorithm
sm3 Select sm3 as the hash algorithm
[Headquarters-ike-proposal-5]authentication-algorithm sha1
[Headquarters-ike-proposal-5]dh ?
group1 768 bits Diffie-Hellman group
group14 2048 bits Diffie-Hellman group
group2 1024 bits Diffie-Hellman group
group5 1536 bits Diffie-Hellman group
[Headquarters-ike-proposal-5]dh group2
[Headquarters-ike-proposal-5]qBranch配置IKE提议配置同Headquarters
(3)配置IKE对等体
Headquarters
[Headquarters]ike peer Center v1 //创建版本为1名称为Center的IKE对等体
[Headquarters-ike-peer-Center]pre-shared-key cipher Key123 //配置预共享秘钥
[Headquarters-ike-peer-Center]remote-address 2.2.2.2 //配置对端IP地址
[Headquarters-ike-peer-Center]dpd type ? //配置DPD检测模式为根据需要进行检测
on-demand Enable the DPD and set the mode to On-Demand
periodic Enable the DPD and set the mode to periodic
[Headquarters-ike-peer-Center]dpd type on-demand
[Headquarters-ike-peer-Center]ike-proposal 5 //引入ike提议
[Headquarters-ike-peer-Center]qBranch
[Branch]ike peer Branch v1
[Branch-ike-peer-Branch]pre-shared-key cipher Key123
[Branch-ike-peer-Branch]remote-address 1.1.1.1
[Branch-ike-peer-Branch]dpd type on-demand
[Branch-ike-peer-Branch]ike-proposal 5
[Branch-ike-peer-Branch]q4、配置安全策略
Headquarters
[Headquarters]ipsec policy center 1 isakmp
[Headquarters-ipsec-policy-isakmp-center-1]security acl 3000
[Headquarters-ipsec-policy-isakmp-center-1]ike-peer Center
[Headquarters-ipsec-policy-isakmp-center-1]proposal def
[Headquarters-ipsec-policy-isakmp-center-1]q
Branch
[Branch]ipsec policy branch 1 isakmp
[Branch-ipsec-policy-isakmp-branch-1]sec
[Branch-ipsec-policy-isakmp-branch-1]security acl 3000
[Branch-ipsec-policy-isakmp-branch-1]ike-peer Branch
[Branch-ipsec-policy-isakmp-branch-1]proposal def
[Branch-ipsec-policy-isakmp-branch-1]q
5、应用安全策略
Headquarters
#出接口下应用IPSec安全策略
[Headquarters]int gi 0/0/0
[Headquarters-GigabitEthernet0/0/0]ipsec policy center
[Headquarters-GigabitEthernet0/0/0]q
#配置一条目的地址为Branch内网的静态路由
[Headquarters]ip route-static 192.168.1.0 255.255.255.0 2.2.2.2
[Headquarters]Branch
[Branch]int gi 0/0/0
[Branch-GigabitEthernet0/0/0]ipsec policy branch
[Branch-GigabitEthernet0/0/0]q
[Branch]ip route-static 192.168.0.0 255.255.255.0 1.1.1.1
[Branch]四、故障解决
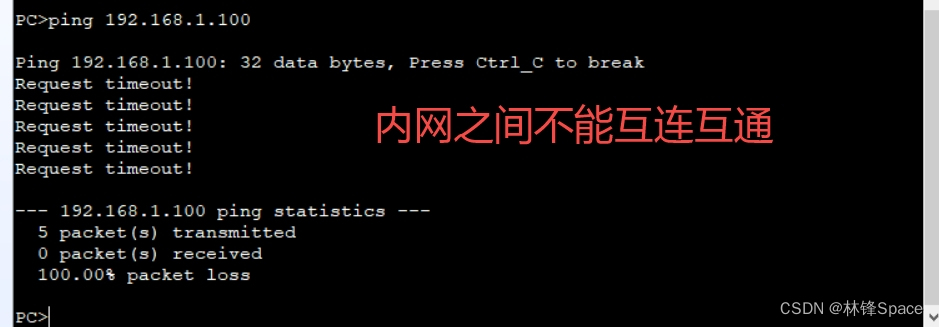
1、故障处理—内网连通性
(1)验证

(2)抓包
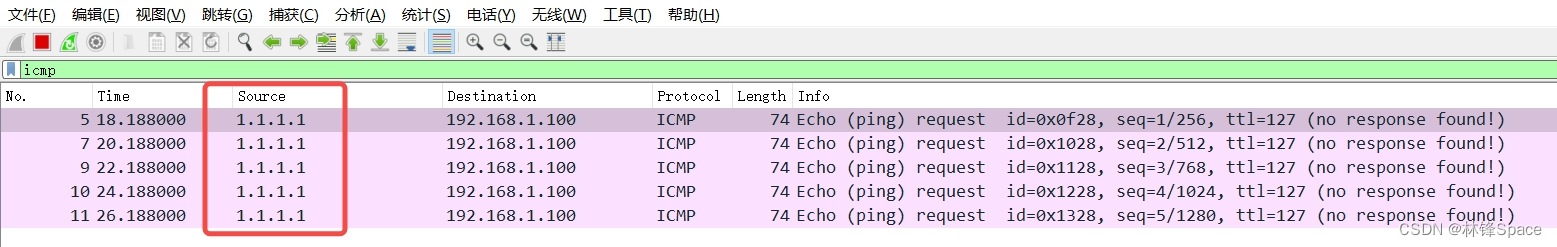
发现从PC1上pingPC2,源地址不是PC1的地址,而是PC1的互联网地址
说明NAT对PC1进行了转换。
(3)问题解决
需要配置NAT对应的ACL,对两个内网之间互访不进行NAT地址转换。
#基础ACL不能实现源目地址控制
#删除原来的NAT相关配置
<Headquarters>sys
Enter system view, return user view with Ctrl+Z.
[Headquarters]acl 2000
[Headquarters-acl-basic-2000]dis th
[V200R003C00]
#
acl number 2000
rule 5 permit source 192.168.0.0 0.0.0.255
#
return
[Headquarters-acl-basic-2000]q
[Headquarters]int gi 0/0/0
[Headquarters-GigabitEthernet0/0/0]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 1.1.1.1 255.255.255.252
ipsec policy center
nat outbound 2000
#
return
[Headquarters-GigabitEthernet0/0/0]undo nat outbound 2000
[Headquarters-GigabitEthernet0/0/0]q
[Headquarters]undo acl 2000
#配置高级ACL
[Headquarters]acl 3003
[Headquarters-acl-adv-3003]ru de ip so 192.168.0.0 0.0.0.255 de 192.168.1.0 0.0.
0.255 //不对源目地址为两地内网的进行NAT转换
[Headquarters-acl-adv-3003]ru pe ip so 192.168.0.0 0.0.0.255
[Headquarters-acl-adv-3003]q
[Headquarters]int gi 0/0/0
[Headquarters-GigabitEthernet0/0/0]nat outbound 3003
[Headquarters-GigabitEthernet0/0/0]q
[Headquarters]
Branch配置与Headquarter类似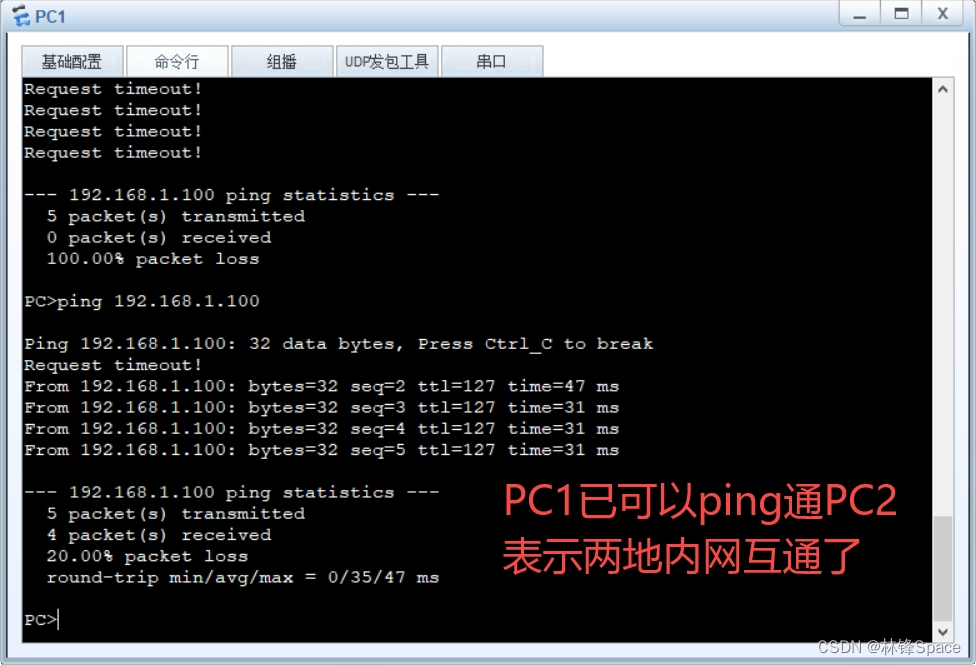

























 738
738











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










