我们每一个人的一生中都会难免有缺憾和不如意,也许我们无力改变这个事实,而我们可以改变的只是看待这些事情的态度。用平和的态度去对待生活中的缺憾和苦难。
public partial class Form1 : Form
{
private const int RsaKeySize = 2048;
private const string publicKeyFileName = "RSA.Pub";
private const string privateKeyFileName = "RSA.Private";
private string basePathToStoreKeys;
public Form1()
{
InitializeComponent();
basePathToStoreKeys = Directory.GetCurrentDirectory();
}
private void button1_Click(object sender, EventArgs e)
{
GenerateKeys(basePathToStoreKeys);
}
private void button2_Click(object sender, EventArgs e)
{
var encryptedString = Encrypt(textBox1.Text, Path.Combine(basePathToStoreKeys, publicKeyFileName));
textBox2.Text = encryptedString;
}
private void button3_Click(object sender, EventArgs e)
{
var decryptedString = Decrypt(textBox2.Text, Path.Combine(basePathToStoreKeys, privateKeyFileName));
textBox2.Text = decryptedString;
}
public void GenerateKeys(string path)
{
using (var rsa = new RSACryptoServiceProvider(RsaKeySize))
{
try
{
var publicKey = rsa.ToXmlString(false);
var privateKey = rsa.ToXmlString(true);
File.WriteAllText(Path.Combine(path, publicKeyFileName), publicKey);
File.WriteAllText(Path.Combine(path, privateKeyFileName), privateKey);
MessageBox.Show(string.Format("生成的RSA密钥的路径: {0}\\ [{1}, {2}]", path, publicKeyFileName, privateKeyFileName));
}
finally
{
rsa.PersistKeyInCsp = false;
}
}
}
public string Encrypt(string plainText, string pathToPublicKey)
{
using (var rsa = new RSACryptoServiceProvider(RsaKeySize))
{
try
{
var publicXmlKey = File.ReadAllText(pathToPublicKey);
rsa.FromXmlString(publicXmlKey);
var bytesToEncrypt = System.Text.Encoding.Unicode.GetBytes(plainText);
var bytesEncrypted = rsa.Encrypt(bytesToEncrypt, false);
return Convert.ToBase64String(bytesEncrypted);
}
finally
{
rsa.PersistKeyInCsp = false;
}
}
}
public string Decrypt(string encryptedText, string pathToPrivateKey)
{
using (var rsa = new RSACryptoServiceProvider(RsaKeySize))
{
try
{
var privateXmlKey = File.ReadAllText(pathToPrivateKey);
rsa.FromXmlString(privateXmlKey);
var bytesEncrypted = Convert.FromBase64String(encryptedText);
var bytesPlainText = rsa.Decrypt(bytesEncrypted, false);
return System.Text.Encoding.Unicode.GetString(bytesPlainText);
}
finally
{
rsa.PersistKeyInCsp = false;
}
}
}
}
生成的RSA.Private的内容:
<?xml version="1.0" encoding="utf-8"?>
<RSAKeyValue>
<Modulus>veJTjzABfYl9/9YbOOw+EcfIZ1jajWiGPAXW+G/2uIUYh9L9WSyLPghl3oMZM2GDxp9f+chdc0k9lrNbJwsIaereleTiOcl2u/rq+jS8r2WhTfk8bIMWeAO/B5S0IjIbmKXdymRNZFw/KjuY99HdYk6nB1MZ1AJ/e3xJKwWJrXp55Y4DlX9sGTORS9kcy1q4fuxjJHUFAYsasV/vnsjlaau4sp6xBcDIfT1tRkxMZriDPW3J7qH7/qI2X4+iQZQIfAyFpSlqi+4GI9FajogEareCS7d1vc+OYdGc+jX1h0erHsRtlvFHzLcqBmZQ0Gz0XdZxOwJf5vhxUvvoK9BmBw==</Modulus>
<Exponent>AQAB</Exponent>
<P>9Dq9A5cVGeBKib4WNSUBQqp25J4p0IUX1foc+zrX6/ZuSgDeXxIKiFmQPcl9R2RTwXQxFYWSkGW4gQis+AMnQJL98kHJXnG2FAiEsEhYUDUEKx29OA+/y/hNoyEbztcggru8Ebn8v4Aq6BMBvM9Q+Q5lIl2I8SRQnDfVnuwdaSc=</P>
<Q>xwkVjnwN0m9K6EyHT5vrOJbw/0cTdcCtoFU7wDawOHJeDj872dR3vs3rf+YinnMNOo47VgH5CQaFEbhgmiAjYlaz+tPFqD/TiiHp0ceqfN3XjUqDx+TkPYq+gGreeh+XE43lP/Z2YUscLq0x/uHPky2EWIxvqqphvW1Xh7ECaCE=</Q>
<DP>cH6Zz4yIyKl6S+YFvqbz5Kw2JWoA4q5bY1FYhhP9nw+cj3PE+c+KkHGIsh0cGoVI2wPVFA+5ic+A49aGLZruOp06YZsR0PHZp3KhA73fB9rTt7R0Et2WP7J4uFoov+ZxcCZfI18i32Z+3PTcSQbJSl7qEKE60bAjfUFuoUwq4+M=</DP>
<DQ>D5hPnxVrQ9TCiscMRxmRaaKyCV55UN2i/RAQmXPvhMy5P+aGev/hzgp2bFQM3FtpavAgCBIpgCKJpKTMtObVvuvKOFoFf7RYj9cuaeh6HESJkiGHh88Qbx4C5S76dZkqDjctAkD+b4siDyo046Kvz/leCE4gpb+p3tzFYfVlmeE=</DQ>
<InverseQ>ux0qhR3AqWMzOsSnwLtj7OGZR7p8hrga6TEr9V5nuvCovHLUcMcwAjXHm/+ZEWXCuQBnoQC82yQbyICuIUbLkYUSfPE59mxAgxrInqHY3j3IDQ09APyJJ1sIelyB0DZOpFa2ERydH0PcthPcS9/d42vADIuE3Z5k6Y9JVyGqmKQ=</InverseQ>
<D>kbp2OKk2K5tu2P8AC3K7vDegpTg7G1XB16T/s9Fx/3EeP3d9OogGIUierePdXmKTmMdOCExu9ACcxODHrzI3ddpsk4uC16i3eFN9LSN2QAJ2hnomln0QrHDrlizZBnmAVmnNyvuprcFiNM5ieqdVCZKle+iaJOz529Kp8NuiK0FExKkv10WYSSsSf6T17eNnGqRqaCEnP8LSgu1WbPiKZ1oIEjt6WThGWIN6d9++InqhbXaCdglnA0U7kXXuWuAnlOf0uBlcUwrGBU6IKqmgrMwgqHKMuSSuJ65UoHYp3RTG+ECmtAHTe7YBBNnjOo8QSCEtdUpSdfKtT5YjVJhOwQ==</D>
</RSAKeyValue>
生成的RSA.Pub的内容:
<?xml version="1.0" encoding="utf-8"?>
<RSAKeyValue>
<Modulus>veJTjzABfYl9/9YbOOw+EcfIZ1jajWiGPAXW+G/2uIUYh9L9WSyLPghl3oMZM2GDxp9f+chdc0k9lrNbJwsIaereleTiOcl2u/rq+jS8r2WhTfk8bIMWeAO/B5S0IjIbmKXdymRNZFw/KjuY99HdYk6nB1MZ1AJ/e3xJKwWJrXp55Y4DlX9sGTORS9kcy1q4fuxjJHUFAYsasV/vnsjlaau4sp6xBcDIfT1tRkxMZriDPW3J7qH7/qI2X4+iQZQIfAyFpSlqi+4GI9FajogEareCS7d1vc+OYdGc+jX1h0erHsRtlvFHzLcqBmZQ0Gz0XdZxOwJf5vhxUvvoK9BmBw==</Modulus>
<Exponent>AQAB</Exponent>
</RSAKeyValue>
运行结果如图:
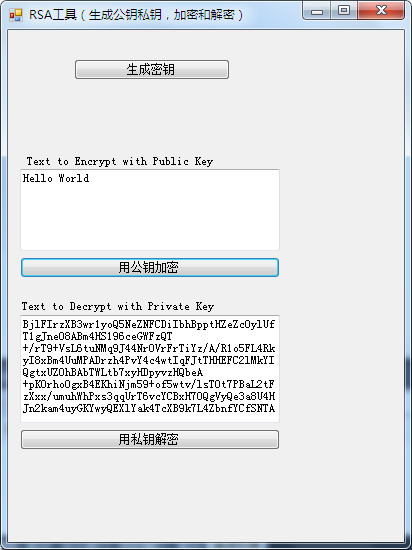
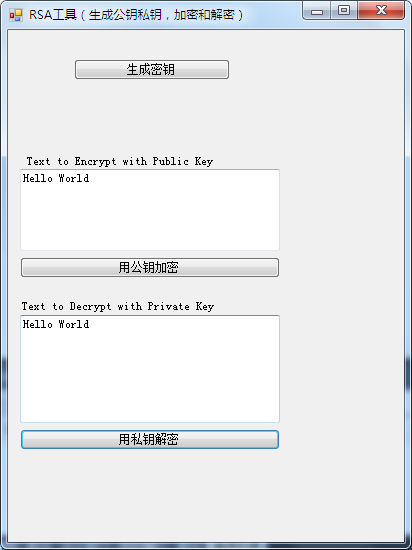


























 434
434

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








