本次参考:https://segmentfault.com/a/1190000020262431
安装
yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel migrationtools pam_ldap
版本
[root@monitor ~]# slapd -VVV
@(#) $OpenLDAP: slapd 2.4.44 (Feb 23 2022 17:11:27) $
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
Included static backends:
config
ldif
monitor
bdb
hdb
mdb
[root@monitor ~]# slapd -V
@(#) $OpenLDAP: slapd 2.4.44 (Feb 23 2022 17:11:27) $
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
[root@monitor ~]# slapd -VV
@(#) $OpenLDAP: slapd 2.4.44 (Feb 23 2022 17:11:27) $
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
配置
密码备用
[root@monitor ~]# slappasswd -s 156
{SSHA}j5IjUeZPrECXmz295Elg6zRYcpX27zTz
删掉配置
rm -rf /etc/openldap/slapd.d
复制ldif过来
cp -rp /usr/share/openldap-servers/slapd.ldif /etc/openldap/
- 用户信息,修改3行增加1行密码(在145行)
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=Manager,dc=joyhour,dc=fun" read by * none
olcSuffix: dc=joyhour,dc=fun
olcRootDN: cn=Manager,dc=joyhour,dc=fun
olcRootPW: {SSHA}j5IjUeZPrECXmz295Elg6zRYcpX27zTz
- 加载所有的置的属性类, core.ldif 必须放在第一行
include: file:///etc/openldap/schema/core.ldif
include: file:///etc/openldap/schema/collective.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
生成配置文件
cp -rp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@monitor openldap]# slapadd -n 0 -F /etc/openldap/slapd.d -l slapd.ldif
_#################### 100.00% eta none elapsed none fast!
Closing DB...
- 配置目录内生成了新的文件
[root@monitor slapd.d]# pwd
/etc/openldap/slapd.d
[root@monitor slapd.d]# ls
cn=config cn=config.ldif
[root@monitor slapd.d]# cat "cn=config.ldif"
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 abb60c5d
dn: cn=config
objectClass: olcGlobal
cn: config
olcArgsFile: /var/run/openldap/slapd.args
olcPidFile: /var/run/openldap/slapd.pid
olcTLSCACertificatePath: /etc/openldap/certs
olcTLSCertificateFile: "OpenLDAP Server"
olcTLSCertificateKeyFile: /etc/openldap/certs/password
structuralObjectClass: olcGlobal
entryUUID: 42fd91c8-89f7-103e-9b54-bfa73ed6921e
creatorsName: cn=config
createTimestamp: 20240408132550Z
entryCSN: 20240408132550.490161Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20240408132550Z
- 授权
chown -R ldap:ldap /etc/openldap/ /var/lib/ldap
- 检查
slaptest -u
[root@monitor openldap]# slaptest -u
config file testing succeeded
- 启动
systemctl start slapd
[root@monitor ldap]# pwd
/var/lib/ldap
[root@monitor ldap]# ls -l
总用量 19232
-rw-r--r-- 1 ldap ldap 2048 4月 8 21:38 alock
-rw------- 1 ldap ldap 2416640 4月 8 21:38 __db.001
-rw------- 1 ldap ldap 17465344 4月 8 21:38 __db.002
-rw------- 1 ldap ldap 1884160 4月 8 21:38 __db.003
-rw-r--r-- 1 ldap ldap 845 2月 24 2022 DB_CONFIG
-rw------- 1 ldap ldap 8192 4月 8 21:38 dn2id.bdb
-rw------- 1 ldap ldap 32768 4月 8 21:38 id2entry.bdb
-rw------- 1 ldap ldap 10485760 4月 8 21:38 log.0000000001
登陆
刚创建完这个目录除了管理员之外,是没有其他用户端
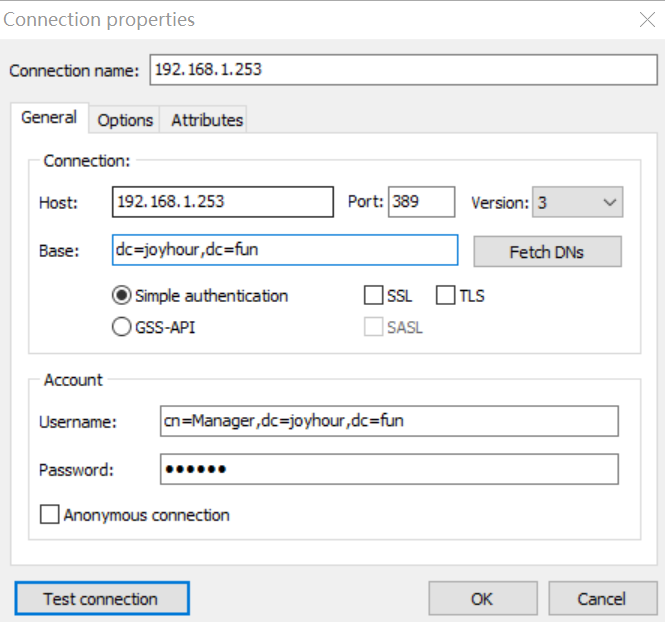
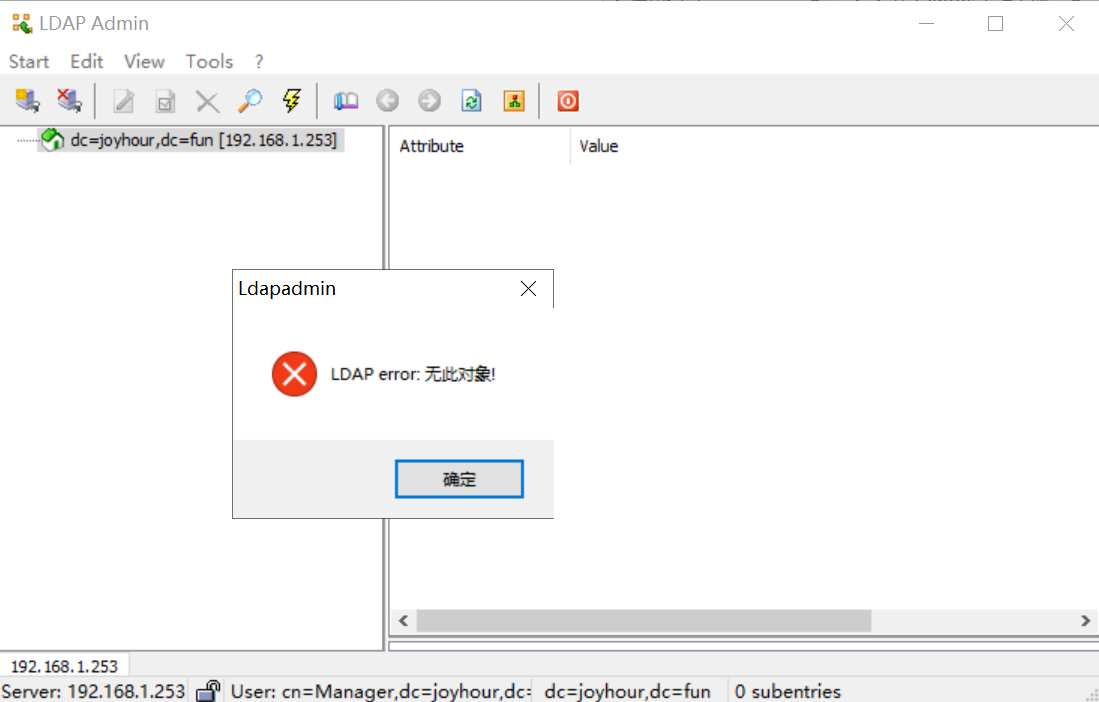
创建用户
创建linux用户
groupadd ldapgroup1
groupadd ldapgroup2
useradd -g ldapgroup1 ldapuser1
useradd -g ldapgroup2 ldapuser2
echo '123456' | passwd --stdin ldapuser1
echo '123456' | passwd --stdin ldapuser2
提取用户和组
grep ":10[0-9][0-9]" /etc/passwd > /root/users
grep ":10[0-9][0-9]" /etc/group > /root/groups
[root@monitor ~]# cat /root/users
appadm:x:1000:1000:appadm:/home/appadm:/bin/bash
ldapuser1:x:1001:1001::/home/ldapuser1:/bin/bash
ldapuser2:x:1002:1002::/home/ldapuser2:/bin/bash
[root@monitor ~]# cat /root/groups
appadm:x:1000:
ldapgroup1:x:1001:
ldapgroup2:x:1002:
配置导入工具 migrationtools
vim /usr/share/migrationtools/migrate_common.ph
# Default DNS domain
$DEFAULT_MAIL_DOMAIN = "joyhour.fun";
# Default base
$DEFAULT_BASE = "dc=joyhour,dc=fun";
$EXTENDED_SCHEMA = 1;
生成ldif文件
/usr/share/migrationtools/migrate_passwd.pl /root/users > /root/users.ldif
/usr/share/migrationtools/migrate_group.pl /root/groups > /root/groups.ldif
cat users.ldif
cat groups.ldif
[root@monitor ~]# cat /root/users.ldif
dn: uid=appadm,ou=People,dc=joyhour,dc=fun
uid: appadm
cn: appadm
sn: appadm
mail: appadm@joyhour.fun
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$5$Ryqqxjzb7e31owCk$UXpqhs/0nsPxZT9Fe53jDlIGAj.xvUh2rVixGUkj3Q6
shadowLastChange: 19647
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1000
gidNumber: 1000
homeDirectory: /home/appadm
gecos: appadm
dn: uid=ldapuser1,ou=People,dc=joyhour,dc=fun
uid: ldapuser1
cn: ldapuser1
sn: ldapuser1
mail: ldapuser1@joyhour.fun
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$1$ZsMVUX.0$7GyHAZEmC4P/wQc6pC.HX/
shadowLastChange: 19821
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1001
gidNumber: 1001
homeDirectory: /home/ldapuser1
dn: uid=ldapuser2,ou=People,dc=joyhour,dc=fun
uid: ldapuser2
cn: ldapuser2
sn: ldapuser2
mail: ldapuser2@joyhour.fun
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$1$Ue59drWz$Tqk9ZM3bEHDH6Gp8MqWXJ0
shadowLastChange: 19821
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1002
gidNumber: 1002
homeDirectory: /home/ldapuser2
[root@monitor ~]# cat /root/groups.ldif
dn: cn=appadm,ou=Group,dc=joyhour,dc=fun
objectClass: posixGroup
objectClass: top
cn: appadm
userPassword: {crypt}x
gidNumber: 1000
dn: cn=ldapgroup1,ou=Group,dc=joyhour,dc=fun
objectClass: posixGroup
objectClass: top
cn: ldapgroup1
userPassword: {crypt}x
gidNumber: 1001
dn: cn=ldapgroup2,ou=Group,dc=joyhour,dc=fun
objectClass: posixGroup
objectClass: top
cn: ldapgroup2
userPassword: {crypt}x
gidNumber: 1002
- 配置基础数据库 base.ldif
dn: dc=joyhour,dc=fun
dc: joyhour
objectClass: top
objectClass: domain
dn: cn=Manager,dc=joyhour,dc=fun
cn: Manager
objectClass: organizationalRole
description: Directory Manager
dn: ou=People,dc=joyhour,dc=fun
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=joyhour,dc=fun
ou: Group
objectClass: top
objectClass: organizationalUnit
导入数据
[root@monitor ~]# ldapadd -x -w "123456" -D "cn=Manager,dc=joyhour,dc=fun" -f /root/base.ldif
adding new entry "dc=joyhour,dc=fun"
adding new entry "cn=Manager,dc=joyhour,dc=fun"
adding new entry "ou=People,dc=joyhour,dc=fun"
adding new entry "ou=Group,dc=joyhour,dc=fun"
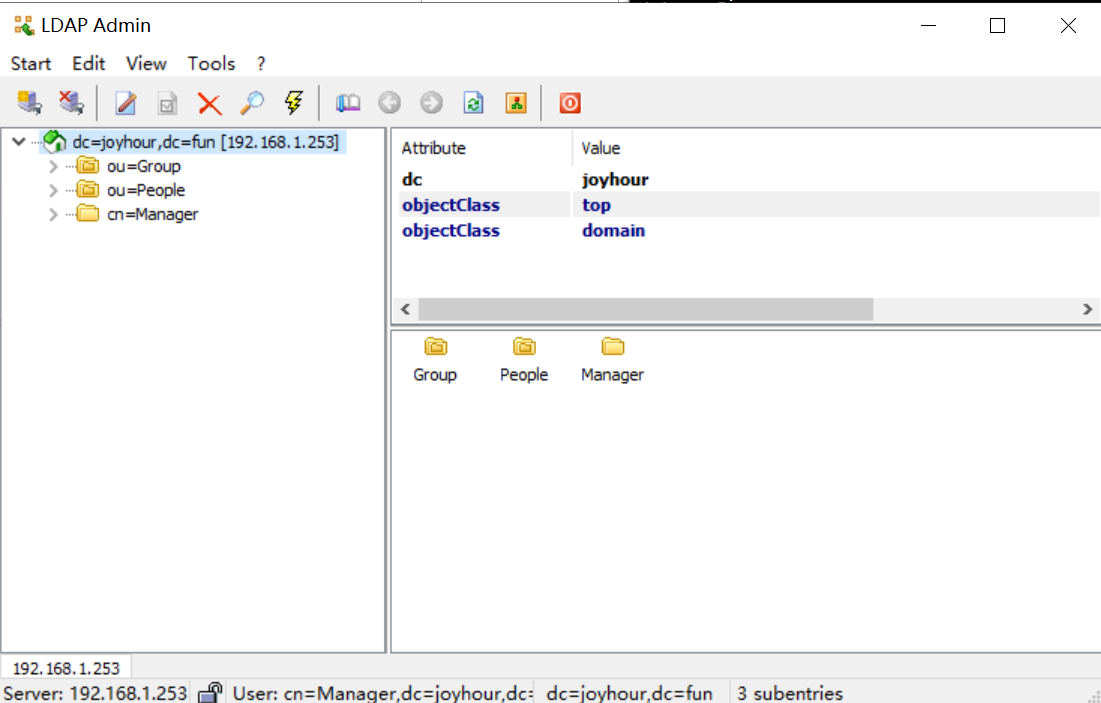
[root@monitor ~]# ldapadd -x -w "123456" -D "cn=Manager,dc=joyhour,dc=fun" -f /root/users.ldif
adding new entry "uid=appadm,ou=People,dc=joyhour,dc=fun"
adding new entry "uid=ldapuser1,ou=People,dc=joyhour,dc=fun"
adding new entry "uid=ldapuser2,ou=People,dc=joyhour,dc=fun"
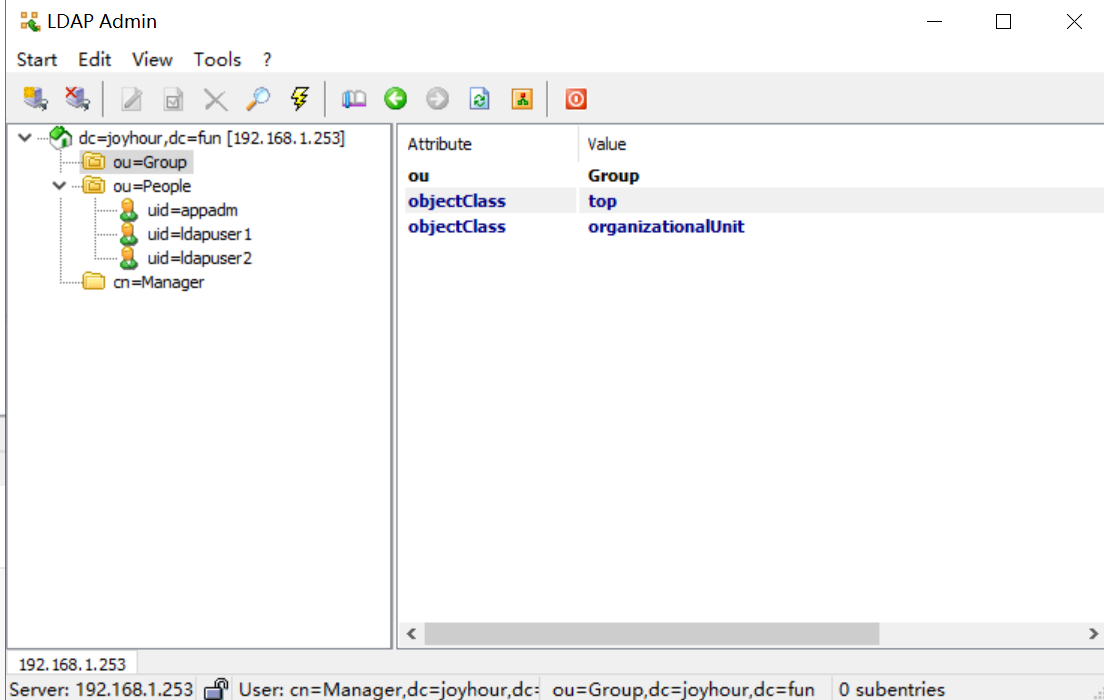
[root@monitor ~]# ldapadd -x -w "123456" -D "cn=Manager,dc=joyhour,dc=fun" -f /root/groups.ldif
adding new entry "cn=appadm,ou=Group,dc=joyhour,dc=fun"
adding new entry "cn=ldapgroup1,ou=Group,dc=joyhour,dc=fun"
adding new entry "cn=ldapgroup2,ou=Group,dc=joyhour,dc=fun"

关联用户到用户组,否则用户和组之间没有关系
把 ldapuser1 用户加入到 ldapgroup1 用户组,需要新建添加用户到用户组的ldif文件,如下:
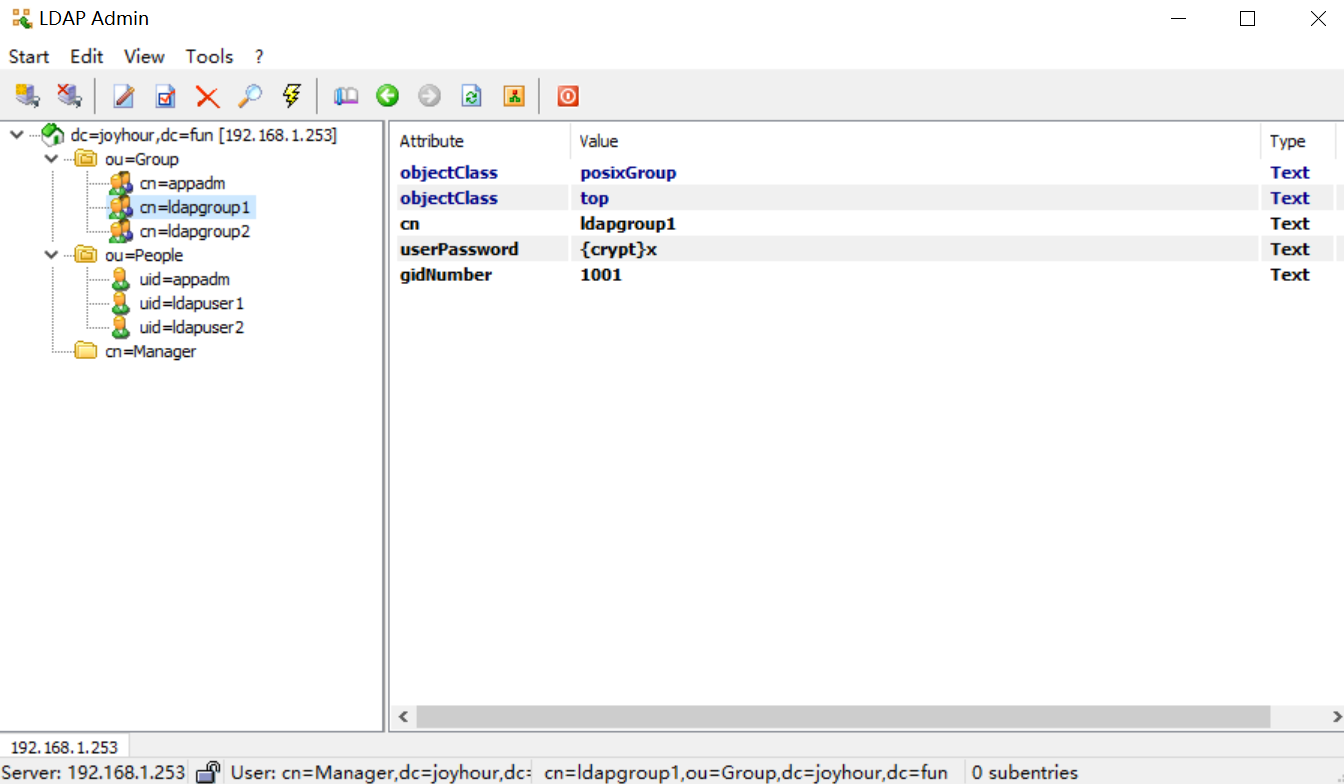
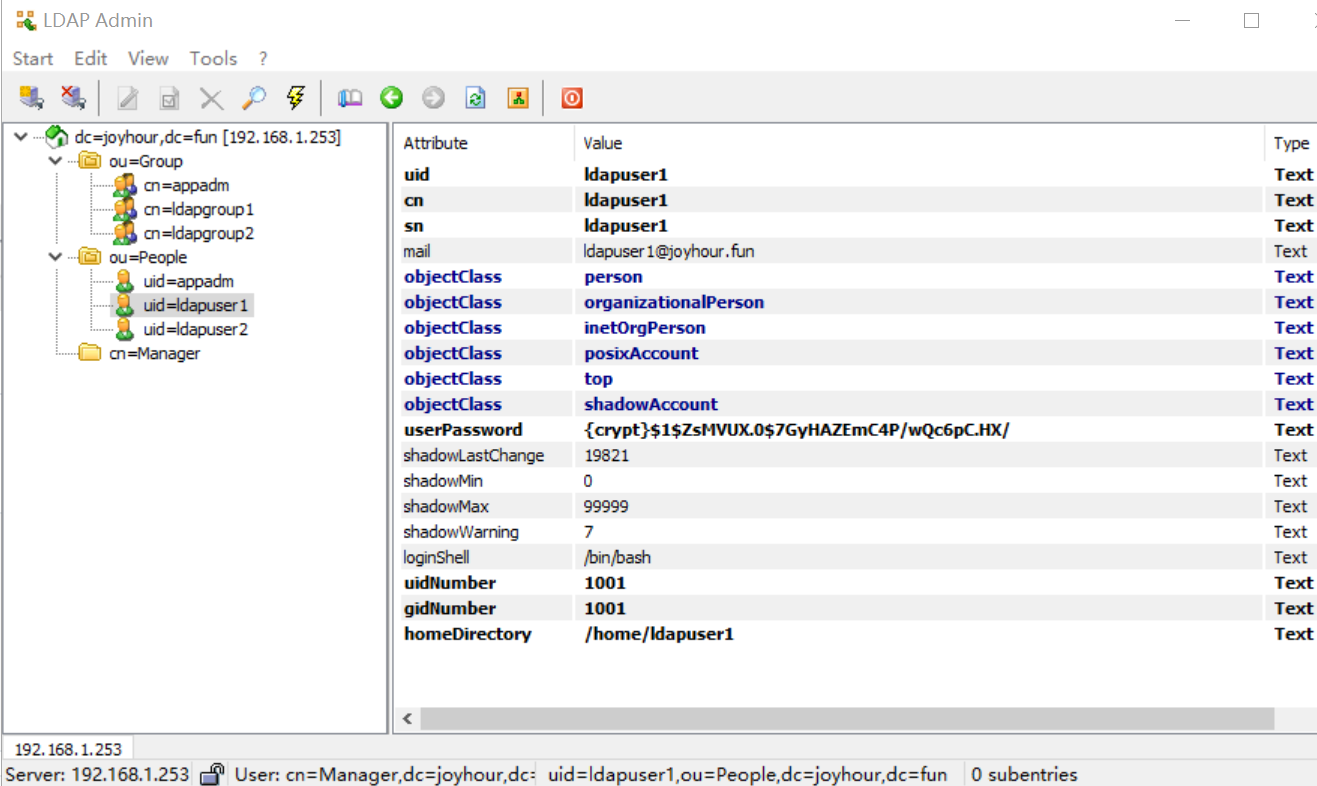
- 定义member和group的关系
cat > /root/users_to_groups.ldif << EOF
dn: cn=ldapgroup1,ou=Group,dc=joyhour,dc=fun
changetype: modify
add: memberuid
memberuid: ldapuser1
EOF
- 执行
[root@monitor ~]# ldapadd -x -w "123456" -D "cn=Manager,dc=joyhour,dc=fun" -f /root/users_to_groups.ldif
modifying entry "cn=ldapgroup1,ou=Group,dc=joyhour,dc=fun"
- 执行完后,可以发现组内已经增加了一个用户
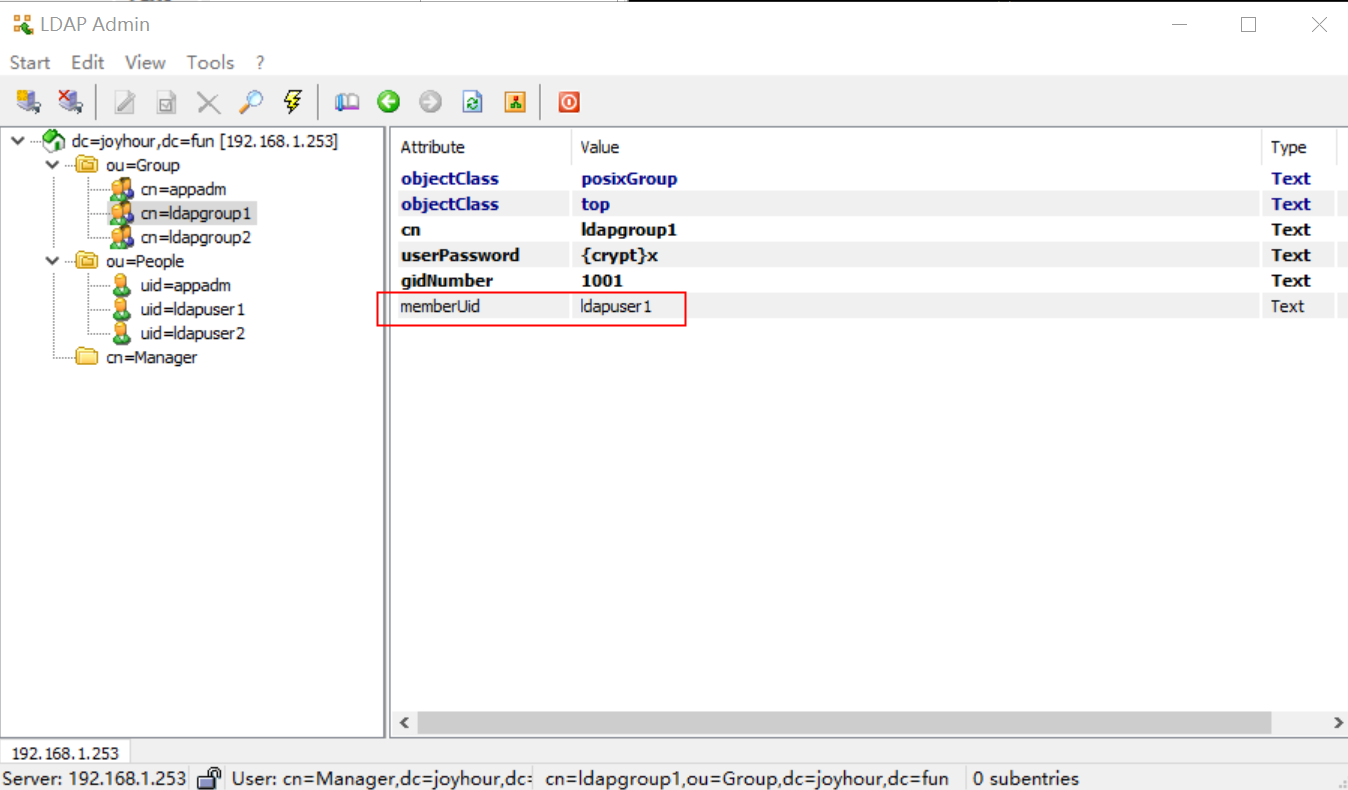
- 命令行查看结果
ldapsearch -LLL -x -D 'cn=Manager,dc=joyhour,dc=fun' -w "123456" -b 'dc=joyhour,dc=fun' 'cn=ldapgroup1'
[root@monitor ~]# ldapsearch -LLL -x -D 'cn=Manager,dc=joyhour,dc=fun' -w "123456" -b 'dc=joyhour,dc=fun' 'cn=ldapgroup1'
dn: cn=ldapgroup1,ou=Group,dc=joyhour,dc=fun
objectClass: posixGroup
objectClass: top
cn: ldapgroup1
userPassword:: e2NyeXB0fXg=
gidNumber: 1001
memberUid: ldapuser1
开启openldap日志访问功能
cat > loglevel.ldif <<EOF
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
EOF
ldapmodify -Y EXTERNAL -H ldapi:/// -f /root/loglevel.ldif
[root@monitor openldap]# ldapmodify -Y EXTERNAL -H ldapi:/// -f /root/loglevel.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=config"
systemctl restart slapd
- 修改 syslog并重启
vim /etc/rsyslog.conf
local4.* /var/log/slapd.log
systemctl restart rsyslog























 508
508











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










