用户名+序列号 破解
查壳:Borland Delphi 3.0
Sorry , The serial is incorect !
提取关键字 下断点,搜索字符串发现两处 都下断
运行 停在了这一行
0042FB26 |. BA 80FB4200 mov edx,Acid_bur.0042FB80 ; Sorry , The serial is incorect !
查看附近的代码
0042FAF8 |. 8B55 F0 mov edx,[local.4]
0042FAFB |. 8B45 F4 mov eax,[local.3]
0042FAFE |. E8 F93EFDFF call Acid-bur.004039FC ; 判断 序列号是否正确
0042FB03 |. 75 1A jnz short Acid-bur.0042FB1F ; 关键跳
0042FB05 |. 6A 00 push 0x0
0042FB07 |. B9 CCFB4200 mov ecx,Acid-bur.0042FBCC ; Congratz !!
0042FB0C |. BA D8FB4200 mov edx,Acid-bur.0042FBD8 ; Good job dude =)
0042FB11 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB18 |. E8 53A6FFFF call Acid-bur.0042A170
0042FB1D |. EB 18 jmp short Acid-bur.0042FB37
0042FB1F |> 6A 00 push 0x0
0042FB21 |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FB26 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB32 |. E8 39A6FFFF call Acid-bur.0042A170
0042FB37 |> 33C0 xor eax,eax ; kernel32.BaseThreadInitThunk
0042FB39 |. 5A pop edx ; kernel32.77371174
0042FB3A |. 59 pop ecx ; kernel32.77371174
0042FB3B |. 59 pop ecx ; kernel32.77371174找到了关键跳0042FB03 |. 75 1A jnz short Acid-bur.0042FB1F
前面的call是用来判断序列号和验证码是否相同。
猜想序列号是又最近的call 1产生的
0042FAE5 |. E8 C23EFDFF call Acid-bur.004039AC ; 最近的call 2
0042FAEA |. 8D55 F0 lea edx,[local.4]
0042FAED |. 8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. E8 60AFFEFF call Acid-bur.0041AA58 ; 最近的call 1
0042FAF8 |. 8B55 F0 mov edx,[local.4]
0042FAFB |. 8B45 F4 mov eax,[local.3]
0042FAFE |. E8 F93EFDFF call Acid-bur.004039FC ; 判断 序列号是否正确
0042FB03 |. 75 1A jnz short Acid-bur.0042FB1F ; 关键跳
0042FB05 |. 6A 00 push 0x0
0042FB07 |. B9 CCFB4200 mov ecx,Acid-bur.0042FBCC ; Congratz !!
0042FB0C |. BA D8FB4200 mov edx,Acid-bur.0042FBD8 ; Good job dude =)
0042FB11 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB18 |. E8 53A6FFFF call Acid-bur.0042A170
0042FB1D |. EB 18 jmp short Acid-bur.0042FB37
0042FB1F |> 6A 00 push 0x0
0042FB21 |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FB26 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB32 |. E8 39A6FFFF call Acid-bur.0042A170
0042FB37 |> 33C0 xor eax,eax ; kernel32.BaseThreadInitThunk
0042FB39 |. 5A pop edx ; kernel32.77371174
0042FB3A |. 59 pop ecx ; kernel32.77371174
0042FB3B |. 59 pop ecx ; kernel32.77371174在call 1处下断,F7跟进
0041AA58 /$ 53 push ebx
0041AA59 |. 56 push esi
0041AA5A |. 57 push edi
0041AA5B |. 8BFA mov edi,edx
0041AA5D |. 8BF0 mov esi,eax
0041AA5F |. 8BC6 mov eax,esi
0041AA61 |. E8 A2FFFFFF call Acid-bur.0041AA08
0041AA66 |. 8BD8 mov ebx,eax
0041AA68 |. 8BC7 mov eax,edi
0041AA6A |. 8BCB mov ecx,ebx
0041AA6C |. 33D2 xor edx,edx
0041AA6E |. E8 E18CFEFF call Acid-bur.00403754
0041AA73 |. 85DB test ebx,ebx
0041AA75 |. 74 0C je short Acid-bur.0041AA83
0041AA77 |. 8D4B 01 lea ecx,dword ptr ds:[ebx+0x1]
0041AA7A |. 8B17 mov edx,dword ptr ds:[edi] ; Acid-bur.0042D67C
0041AA7C |. 8BC6 mov eax,esi
0041AA7E |. E8 95FFFFFF call Acid-bur.0041AA18
0041AA83 |> 5F pop edi ; Acid-bur.0042FAF8
0041AA84 |. 5E pop esi ; Acid-bur.0042FAF8
0041AA85 |. 5B pop ebx ; Acid-bur.0042FAF8
0041AA86 \. C3 retn
在 0041AA6E |. E8 E18CFEFF call处继续跟进
0041AA08 /$ 6A 00 push 0x0
0041AA0A |. 33C9 xor ecx,ecx
0041AA0C |. BA 0E000000 mov edx,0xE
0041AA11 |. E8 F6070000 call Acid-bur.0041B20C
0041AA16 \. C3 retn
在0041AA11处继续跟进
0041B20C /$ 55 push ebp
0041B20D |. 8BEC mov ebp,esp
0041B20F |. 83C4 F0 add esp,-0x10
0041B212 |. 53 push ebx
0041B213 |. 8955 F0 mov [local.4],edx
0041B216 |. 894D F4 mov [local.3],ecx
0041B219 |. 8B55 08 mov edx,[arg.1]
0041B21C |. 8955 F8 mov [local.2],edx
0041B21F |. 33D2 xor edx,edx
0041B221 |. 8955 FC mov [local.1],edx
0041B224 |. 85C0 test eax,eax
0041B226 |. 74 0B je short Acid-bur.0041B233
0041B228 |. 8D55 F0 lea edx,[local.4]
0041B22B |. 8BD8 mov ebx,eax
0041B22D |. 8B43 2C mov eax,dword ptr ds:[ebx+0x2C]
0041B230 |. FF53 28 call dword ptr ds:[ebx+0x28] ; Acid-bur.004260E8
0041B233 |> 8B45 FC mov eax,[local.1] ; Acid-bur.0042FBAC
0041B236 |. 5B pop ebx ; Acid-bur.0041AA16
0041B237 |. 8BE5 mov esp,ebp
0041B239 |. 5D pop ebp ; Acid-bur.0041AA16
0041B23A \. C2 0400 retn 0x4
跟了这么多层 发现竟然还有call
仔细观察栈
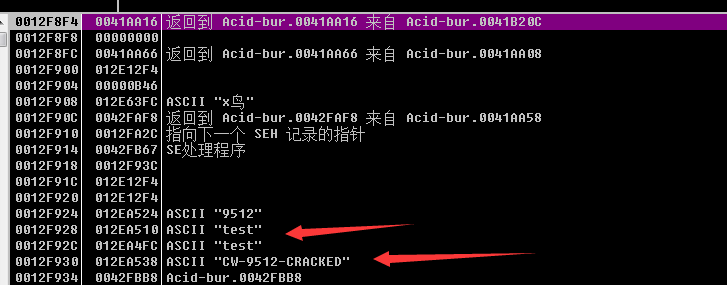
发现栈中已经存在了正确的序列号了。
我们认为 序列号产生于最后一个call中的假设不成立。
那么就往前看着一片代码。
0042F998 /. 55 push ebp
0042F999 |. 8BEC mov ebp,esp
0042F99B |. 33C9 xor ecx,ecx
0042F99D |. 51 push ecx
0042F99E |. 51 push ecx
0042F99F |. 51 push ecx
0042F9A0 |. 51 push ecx
0042F9A1 |. 51 push ecx
0042F9A2 |. 51 push ecx
0042F9A3 |. 53 push ebx
0042F9A4 |. 56 push esi
0042F9A5 |. 8BD8 mov ebx,eax
0042F9A7 |. 33C0 xor eax,eax
0042F9A9 |. 55 push ebp
0042F9AA |. 68 67FB4200 push Acid-bur.0042FB67
0042F9AF |. 64:FF30 push dword ptr fs:[eax]
0042F9B2 |. 64:8920 mov dword ptr fs:[eax],esp
0042F9B5 |. C705 50174300>mov dword ptr ds:[0x431750],0x29
0042F9BF |. 8D55 F0 lea edx,[local.4]
0042F9C2 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9C8 |. E8 8BB0FEFF call Acid-bur.0041AA58
0042F9CD |. 8B45 F0 mov eax,[local.4]
0042F9D0 |. E8 DB40FDFF call Acid-bur.00403AB0
0042F9D5 |. A3 6C174300 mov dword ptr ds:[0x43176C],eax
0042F9DA |. 8D55 F0 lea edx,[local.4]
0042F9DD |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9E3 |. E8 70B0FEFF call Acid-bur.0041AA58
0042F9E8 |. 8B45 F0 mov eax,[local.4]
0042F9EB |. 0FB600 movzx eax,byte ptr ds:[eax]
0042F9EE |. 8BF0 mov esi,eax
0042F9F0 |. C1E6 03 shl esi,0x3
0042F9F3 |. 2BF0 sub esi,eax
0042F9F5 |. 8D55 EC lea edx,[local.5]
0042F9F8 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9FE |. E8 55B0FEFF call Acid-bur.0041AA58
0042FA03 |. 8B45 EC mov eax,[local.5]
0042FA06 |. 0FB640 01 movzx eax,byte ptr ds:[eax+0x1]
0042FA0A |. C1E0 04 shl eax,0x4
0042FA0D |. 03F0 add esi,eax
0042FA0F |. 8935 54174300 mov dword ptr ds:[0x431754],esi
0042FA15 |. 8D55 F0 lea edx,[local.4]
0042FA18 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA1E |. E8 35B0FEFF call Acid-bur.0041AA58
0042FA23 |. 8B45 F0 mov eax,[local.4]
0042FA26 |. 0FB640 03 movzx eax,byte ptr ds:[eax+0x3]
0042FA2A |. 6BF0 0B imul esi,eax,0xB
0042FA2D |. 8D55 EC lea edx,[local.5]
0042FA30 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA36 |. E8 1DB0FEFF call Acid-bur.0041AA58
0042FA3B |. 8B45 EC mov eax,[local.5]
0042FA3E |. 0FB640 02 movzx eax,byte ptr ds:[eax+0x2]
0042FA42 |. 6BC0 0E imul eax,eax,0xE
0042FA45 |. 03F0 add esi,eax
0042FA47 |. 8935 58174300 mov dword ptr ds:[0x431758],esi
0042FA4D |. A1 6C174300 mov eax,dword ptr ds:[0x43176C]
0042FA52 |. E8 D96EFDFF call Acid-bur.00406930
0042FA57 |. 83F8 04 cmp eax,0x4
0042FA5A |. 7D 1D jge short Acid-bur.0042FA79
0042FA5C |. 6A 00 push 0x0
0042FA5E |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FA63 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FA68 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FA6D |. 8B00 mov eax,dword ptr ds:[eax] ; Acid-bur.0042B05C
0042FA6F |. E8 FCA6FFFF call Acid-bur.0042A170
0042FA74 |. E9 BE000000 jmp Acid-bur.0042FB37
0042FA79 |> 8D55 F0 lea edx,[local.4]
0042FA7C |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA82 |. E8 D1AFFEFF call Acid-bur.0041AA58
0042FA87 |. 8B45 F0 mov eax,[local.4]
0042FA8A |. 0FB600 movzx eax,byte ptr ds:[eax]
0042FA8D |. F72D 50174300 imul dword ptr ds:[0x431750]
0042FA93 |. A3 50174300 mov dword ptr ds:[0x431750],eax
0042FA98 |. A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FA9D |. 0105 50174300 add dword ptr ds:[0x431750],eax
0042FAA3 |. 8D45 FC lea eax,[local.1]
0042FAA6 |. BA ACFB4200 mov edx,Acid-bur.0042FBAC ; CW
0042FAAB |. E8 583CFDFF call Acid-bur.00403708
0042FAB0 |. 8D45 F8 lea eax,[local.2]
0042FAB3 |. BA B8FB4200 mov edx,Acid-bur.0042FBB8 ; CRACKED
0042FAB8 |. E8 4B3CFDFF call Acid-bur.00403708
0042FABD |. FF75 FC push [local.1] ; Acid-bur.0042FBAC
0042FAC0 |. 68 C8FB4200 push Acid-bur.0042FBC8 ; -
0042FAC5 |. 8D55 E8 lea edx,[local.6]
0042FAC8 |. A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FACD |. E8 466CFDFF call Acid-bur.00406718 ; 最近的call 3
0042FAD2 |. FF75 E8 push [local.6]
0042FAD5 |. 68 C8FB4200 push Acid-bur.0042FBC8 ; -
0042FADA |. FF75 F8 push [local.2] ; Acid-bur.0042FBB8
0042FADD |. 8D45 F4 lea eax,[local.3]
0042FAE0 |. BA 05000000 mov edx,0x5
0042FAE5 |. E8 C23EFDFF call Acid-bur.004039AC ; 最近的call 2
0042FAEA |. 8D55 F0 lea edx,[local.4]
0042FAED |. 8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. E8 60AFFEFF call Acid-bur.0041AA58 ; 最近的call 1
0042FAF8 |. 8B55 F0 mov edx,[local.4]
0042FAFB |. 8B45 F4 mov eax,[local.3]
0042FAFE |. E8 F93EFDFF call Acid-bur.004039FC ; 判断 序列号是否正确
0042FB03 |. 75 1A jnz short Acid-bur.0042FB1F ; 关键跳
0042FB05 |. 6A 00 push 0x0
0042FB07 |. B9 CCFB4200 mov ecx,Acid-bur.0042FBCC ; Congratz !!
0042FB0C |. BA D8FB4200 mov edx,Acid-bur.0042FBD8 ; Good job dude =)
0042FB11 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. 8B00 mov eax,dword ptr ds:[eax] ; Acid-bur.0042B05C
0042FB18 |. E8 53A6FFFF call Acid-bur.0042A170
0042FB1D |. EB 18 jmp short Acid-bur.0042FB37
0042FB1F |> 6A 00 push 0x0
0042FB21 |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FB26 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. 8B00 mov eax,dword ptr ds:[eax] ; Acid-bur.0042B05C
0042FB32 |. E8 39A6FFFF call Acid-bur.0042A170
0042FB37 |> 33C0 xor eax,eax
0042FB39 |. 5A pop edx ; 0012FA2C
0042FB3A |. 59 pop ecx ; 0012FA2C
0042FB3B |. 59 pop ecx ; 0012FA2C
分析这一片代码,F8步过分析
一定要记得观察栈中的值
0042F998 /. 55 push ebp
0042F999 |. 8BEC mov ebp,esp
0042F99B |. 33C9 xor ecx,ecx ; Acid-bur.0042FB74
0042F99D |. 51 push ecx ; Acid-bur.0042FB74
0042F99E |. 51 push ecx ; Acid-bur.0042FB74
0042F99F |. 51 push ecx ; Acid-bur.0042FB74
0042F9A0 |. 51 push ecx ; Acid-bur.0042FB74
0042F9A1 |. 51 push ecx ; Acid-bur.0042FB74
0042F9A2 |. 51 push ecx ; Acid-bur.0042FB74
0042F9A3 |. 53 push ebx
0042F9A4 |. 56 push esi
0042F9A5 |. 8BD8 mov ebx,eax
0042F9A7 |. 33C0 xor eax,eax
0042F9A9 |. 55 push ebp
0042F9AA |. 68 67FB4200 push Acid-bur.0042FB67
0042F9AF |. 64:FF30 push dword ptr fs:[eax]
0042F9B2 |. 64:8920 mov dword ptr fs:[eax],esp
0042F9B5 |. C705 50174300>mov dword ptr ds:[0x431750],0x29 ; 0x29 赋值给 地址0x431750处
0042F9BF |. 8D55 F0 lea edx,[local.4]
0042F9C2 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9C8 |. E8 8BB0FEFF call Acid-bur.0041AA58
0042F9CD |. 8B45 F0 mov eax,[local.4]
0042F9D0 |. E8 DB40FDFF call Acid-bur.00403AB0
0042F9D5 |. A3 6C174300 mov dword ptr ds:[0x43176C],eax ; eax=用户名test的地址
0042F9DA |. 8D55 F0 lea edx,[local.4]
0042F9DD |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9E3 |. E8 70B0FEFF call Acid-bur.0041AA58
0042F9E8 |. 8B45 F0 mov eax,[local.4]
0042F9EB |. 0FB600 movzx eax,byte ptr ds:[eax]
0042F9EE |. 8BF0 mov esi,eax
0042F9F0 |. C1E6 03 shl esi,0x3
0042F9F3 |. 2BF0 sub esi,eax
0042F9F5 |. 8D55 EC lea edx,[local.5]
0042F9F8 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042F9FE |. E8 55B0FEFF call Acid-bur.0041AA58
0042FA03 |. 8B45 EC mov eax,[local.5]
0042FA06 |. 0FB640 01 movzx eax,byte ptr ds:[eax+0x1]
0042FA0A |. C1E0 04 shl eax,0x4
0042FA0D |. 03F0 add esi,eax
0042FA0F |. 8935 54174300 mov dword ptr ds:[0x431754],esi
0042FA15 |. 8D55 F0 lea edx,[local.4]
0042FA18 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA1E |. E8 35B0FEFF call Acid-bur.0041AA58
0042FA23 |. 8B45 F0 mov eax,[local.4]
0042FA26 |. 0FB640 03 movzx eax,byte ptr ds:[eax+0x3] ; 取第四个字母t test
0042FA2A |. 6BF0 0B imul esi,eax,0xB
0042FA2D |. 8D55 EC lea edx,[local.5]
0042FA30 |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA36 |. E8 1DB0FEFF call Acid-bur.0041AA58
0042FA3B |. 8B45 EC mov eax,[local.5]
0042FA3E |. 0FB640 02 movzx eax,byte ptr ds:[eax+0x2]
0042FA42 |. 6BC0 0E imul eax,eax,0xE
0042FA45 |. 03F0 add esi,eax
0042FA47 |. 8935 58174300 mov dword ptr ds:[0x431758],esi
0042FA4D |. A1 6C174300 mov eax,dword ptr ds:[0x43176C]
0042FA52 |. E8 D96EFDFF call Acid-bur.00406930
0042FA57 |. 83F8 04 cmp eax,0x4
0042FA5A |. 7D 1D jge short Acid-bur.0042FA79
0042FA5C |. 6A 00 push 0x0
0042FA5E |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FA63 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FA68 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FA6D |. 8B00 mov eax,dword ptr ds:[eax]
0042FA6F |. E8 FCA6FFFF call Acid-bur.0042A170
0042FA74 |. E9 BE000000 jmp Acid-bur.0042FB37
0042FA79 |> 8D55 F0 lea edx,[local.4]
0042FA7C |. 8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA82 |. E8 D1AFFEFF call Acid-bur.0041AA58
0042FA87 |. 8B45 F0 mov eax,[local.4]
0042FA8A |. 0FB600 movzx eax,byte ptr ds:[eax] ; 取第一个字母t
0042FA8D |. F72D 50174300 imul dword ptr ds:[0x431750] ; 乘以0x29
0042FA93 |. A3 50174300 mov dword ptr ds:[0x431750],eax ; 将结果写回内存
0042FA98 |. A1 50174300 mov eax,dword ptr ds:[0x431750] ; 取结果
0042FA9D |. 0105 50174300 add dword ptr ds:[0x431750],eax ; 乘2写回内存
0042FAA3 |. 8D45 FC lea eax,[local.1] ; 取该函数内的第一个局部变量 0012F938
0042FAA6 |. BA ACFB4200 mov edx,Acid-bur.0042FBAC ; CW
0042FAAB |. E8 583CFDFF call Acid-bur.00403708 ; 变量1变成了CW
0042FAB0 |. 8D45 F8 lea eax,[local.2] ; 取局部变量2 0012F934
0042FAB3 |. BA B8FB4200 mov edx,Acid-bur.0042FBB8 ; CRACKED
0042FAB8 |. E8 4B3CFDFF call Acid-bur.00403708 ; 变量2变成了CRACKED
0042FABD |. FF75 FC push [local.1] ; Acid-bur.0042FBAC
0042FAC0 |. 68 C8FB4200 push Acid-bur.0042FBC8 ; -
0042FAC5 |. 8D55 E8 lea edx,[local.6] ; EDX=0012F924
0042FAC8 |. A1 50174300 mov eax,dword ptr ds:[0x431750] ; EAX=0X2528
0042FACD |. E8 466CFDFF call Acid-bur.00406718 ; 最近的call 3 EDX所指寄存器变成了 9515也就是 0x2528的十进制
0042FAD2 |. FF75 E8 push [local.6]
0042FAD5 |. 68 C8FB4200 push Acid-bur.0042FBC8 ; -
0042FADA |. FF75 F8 push [local.2] ; Acid-bur.0042FBB8
0042FADD |. 8D45 F4 lea eax,[local.3] ; eax=0xf930
0042FAE0 |. BA 05000000 mov edx,0x5 ; edx=5
0042FAE5 |. E8 C23EFDFF call Acid-bur.004039AC ; 最近的call 2 0012F930处出现了正确的序列号
0042FAEA |. 8D55 F0 lea edx,[local.4] ; edx=0012F92C
0042FAED |. 8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. E8 60AFFEFF call Acid-bur.0041AA58 ; 最近的call 1 0012F92C出现了我们输入的序列号
0042FAF8 |. 8B55 F0 mov edx,[local.4]
0042FAFB |. 8B45 F4 mov eax,[local.3]
0042FAFE |. E8 F93EFDFF call Acid-bur.004039FC ; 判断 序列号是否正确
0042FB03 |. 75 1A jnz short Acid-bur.0042FB1F ; 关键跳
0042FB05 |. 6A 00 push 0x0
0042FB07 |. B9 CCFB4200 mov ecx,Acid-bur.0042FBCC ; Congratz !!
0042FB0C |. BA D8FB4200 mov edx,Acid-bur.0042FBD8 ; Good job dude =)
0042FB11 |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB18 |. E8 53A6FFFF call Acid-bur.0042A170
0042FB1D |. EB 18 jmp short Acid-bur.0042FB37
0042FB1F |> 6A 00 push 0x0
0042FB21 |. B9 74FB4200 mov ecx,Acid-bur.0042FB74 ; Try Again!
0042FB26 |. BA 80FB4200 mov edx,Acid-bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. 8B00 mov eax,dword ptr ds:[eax]
0042FB32 |. E8 39A6FFFF call Acid-bur.0042A170
0042FB37 |> 33C0 xor eax,eax
0042FB39 |. 5A pop edx ; Acid-bur.0042FB80
0042FB3A |. 59 pop ecx ; Acid-bur.0042FB74
0042FB3B |. 59 pop ecx ; Acid-bur.0042FB74
由此得出算法如下
取用户名的第四个字符乘以0x29再乘2 换算成10进制前面加CW-后面加-CRACKED
就是正确的序列号.
注册机
#include<stdio.h>
#include<stdlib.h>
int main()
{
int t;
printf("please input the username:");
char *s=(char *)malloc(1000);
gets(s);
printf("first character:%c\n",*s);
t=*s;
t=t*0x29*2;
printf("result:CW-%4d-CRACKED\n",t);
}希望自己能够多练习,多努力。以此自勉。






















 3671
3671

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








